AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Information Security Ppt
Information Security Ppt
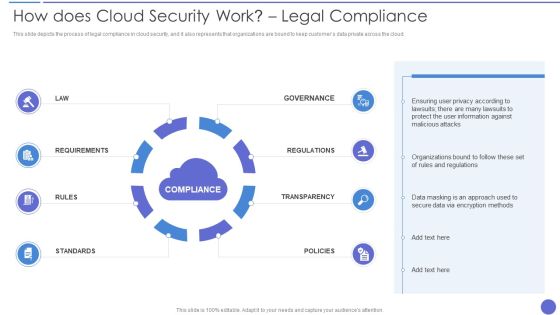
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Standard Compliances For Online Security Pictures PDF
This slide shows various standards that are established for digital safety and followed by organization to meet compliance regulations. It provides information for PCI DSS, SOC 2, NYDFS, NIST AND CCPA. Persuade your audience using this Major Standard Compliances For Online Security Pictures PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Digital Safety, Requirements For Financial, Regulate Risk Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
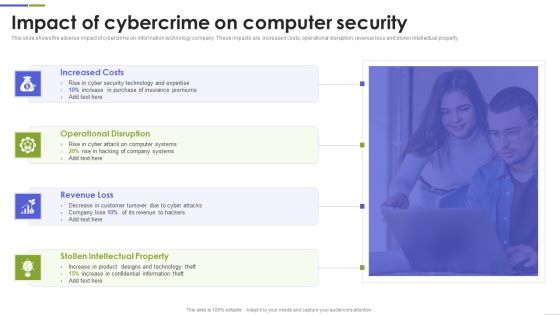
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Desktop Security Management Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting desktop security management assessment matrix of cyber risks infographics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like retail, systems, systems, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study 2 Banks Cyber Security Infrastructure Topics PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Presenting case study 2 banks cyber security infrastructure topics pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like implemented, integrated, our approach. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
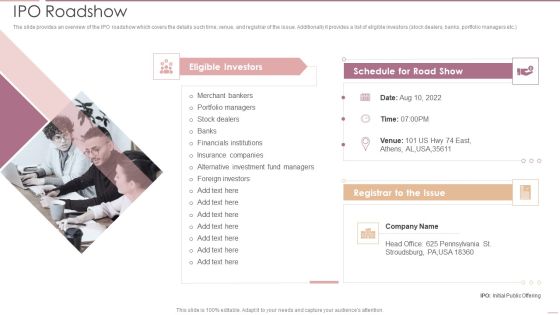
Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF
The slide provides an overview of the IPO roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc.Presenting Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Eligible Investors, Portfolio Managers, Alternative Investment In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Strategies To Manage Cyber Risks Rules PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting desktop security management strategies to manage cyber risks rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strategic, risk, implementation, awareness, invest. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Investment Banking Security Underwriting Pitchbook Post IPO Plan Microsoft PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and selling, general, and administration expenses, operating income, and net income.Presenting Investment Banking Security Underwriting Pitchbook Post IPO Plan Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Market Capitalization, Fund Allocation, Business Expansion In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
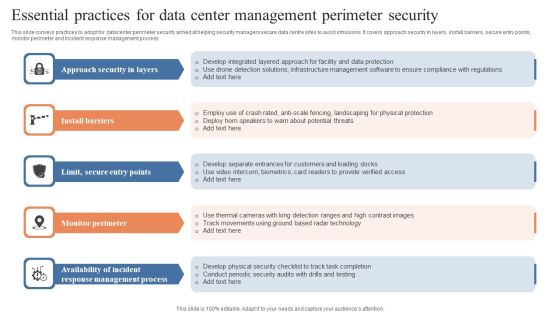
Essential Practices For Data Center Management Perimeter Security Guidelines PDF
This slide conveys practices to adopt for datacenter perimeter security aimed at helping security managers secure data centre sites to avoid intrusions. It covers approach security in layers, install barriers, secure entry points, monitor perimeter and incident response management process. Persuade your audience using this Essential Practices For Data Center Management Perimeter Security Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Approach Security Layers, Install Barriers, Monitor Perimeter. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Techniques For Digital Terrorism Icon Elements PDF
Persuade your audience using this Security Techniques For Digital Terrorism Icon Elements PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Digital Terrorism Icon, Security Techniques. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Awareness Trends In 2022 Diagrams PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Presenting Cyber Security Awareness Trends In 2022 Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Malware Ransomware, Advanced Challenging, Malware Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
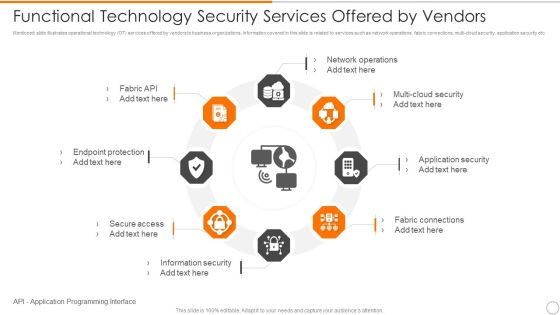
Functional Technology Security Services Offered By Vendors Microsoft PDF
Persuade your audience using this functional technology security services offered by vendors microsoft pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including network operations, security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Security Management Technology Framework Elements PDF
This slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Persuade your audience using this Cloud Computing Security Management Technology Framework Elements PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including User Access Management, Data Security, Hardware And Software, Network Security, Monitoring, Governance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
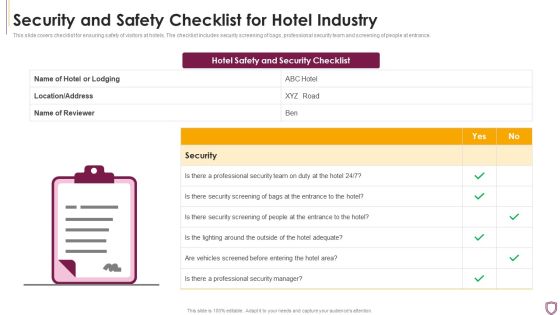
Security And Safety Checklist For Hotel Industry Summary PDF
This slide covers checklist for ensuring safety of visitors at hotels. The checklist includes security screening of bags, professional security team and screening of people at entrance.Showcasing this set of slides titled Security And Safety Checklist For Hotel Industry Summary PDF The topics addressed in these templates are Professional Security, Security Screening, Vehicles Screened All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Program Icon For Protecting Client Data Ideas PDF
Persuade your audience using this IT Security Program Icon For Protecting Client Data Ideas PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including It Security, Program Icon, Protecting Client Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF
Showcasing this set of slides titled Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF. The topics addressed in these templates are Data Warehouse, Security Mechanism, Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
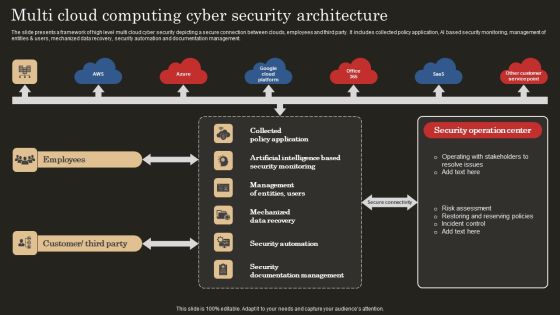
Multi Cloud Computing Cyber Security Architecture Microsoft PDF
The slide presents a framework of high level multi cloud cyber security depicting a secure connection between clouds, employees and third party. It includes collected policy application, AI based security monitoring, management of entities and users, mechanized data recovery, security automation and documentation management. Showcasing this set of slides titled Multi Cloud Computing Cyber Security Architecture Microsoft PDF. The topics addressed in these templates are Mechanized Data Recovery, Security Automation, Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security KPI Dashboard With Metrics Microsoft PDF
This slide showcases dashboard of security support cell based on complaints recorded from ABC company. It includes complaints, non complaints, open and close tickets and security incident by quarter. Showcasing this set of slides titled Cyber Security KPI Dashboard With Metrics Microsoft PDF. The topics addressed in these templates are Cyber Security, Kpi Dashboard With Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

AI Based Automation Of Cyber Risk Security Controls Summary PDF
The following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Showcasing this set of slides titled ai based automation of cyber risk security controls summary pdf. The topics addressed in these templates are controls management, cyber threat security controls, ai based cyber threat security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Network Cloud Network Security Analysis Icon Icons PDF
Persuade your audience using this Network Cloud Network Security Analysis Icon Icons PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Network Cloud, Network Security, Analysis Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon Showcasing Effective Online Security Policy Topics PDF
Persuade your audience using this Icon Showcasing Effective Online Security Policy Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showcasing Effective, Online Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Stakeholder Security Audit And Recognition Icon Demonstration PDF
Persuade your audience using this Stakeholder Security Audit And Recognition Icon Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholder Security Audit, Recognition Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

NIST Cybersecurity Framework For Cloud Security Icon Background PDF
Persuade your audience using this NIST Cybersecurity Framework For Cloud Security Icon Background PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including NIST Cybersecurity, Framework, Cloud Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Hazards Management Program Icon Slides PDF
Persuade your audience using this Cyber Security Hazards Management Program Icon Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
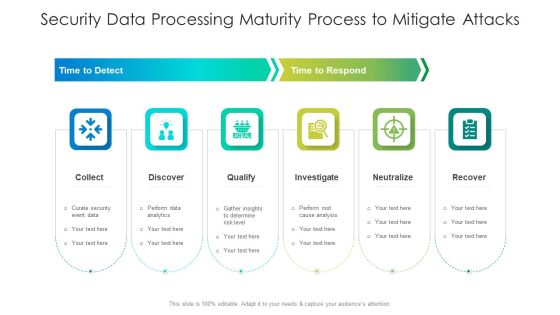
Security Data Processing Maturity Process To Mitigate Attacks Ideas PDF
Persuade your audience using this security data processing maturity process to mitigate attacks ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including qualify, analysis, determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Users Password IT Security Analysis Dashboard Elements PDF
This slide displays the analysis of the users password security in an organization to make sure that the users confidential details are safe. It includes security gains, password evaluation, active users data, activities of password, etc. Showcasing this set of slides titled Users Password IT Security Analysis Dashboard Elements PDF. The topics addressed in these templates are Password Evaluation Score, Security Gains. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Crime And War Security Strategic Vision Designs PDF
This slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team.Persuade your audience using this Cyber Crime And War Security Strategic Vision Designs PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Strategy, Protection Promotion, Secured Cyberspace Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Benchmark Analysis For Data Security Software Mockup PDF
This slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Showcasing this set of slides titled Benchmark Analysis For Data Security Software Mockup PDF. The topics addressed in these templates are Data Privacy, Data Integrity, Authentication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategies For Safety And Security In Hotel Industry Sample PDF
This slide outlines measures to ensure safety and security in hospitality sectors. It highlights four basic ways i.e. cyber security, add intelligence to video surveillance, internal theft and fraud and establish evergreen background screening protocol.Persuade your audience using this Strategies For Safety And Security In Hotel Industry Sample PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Internal Theft And Fraud, Establish Evergreen Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Security Management Tool Assessment Matrix Microsoft PDF
This slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Persuade your audience using this Data Security Management Tool Assessment Matrix Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Intelligence, Advanced Data Governance, Secure Score. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risk Security Market Growth With Current Trends Summary PDF
The following slide highlights the bar graph of cyber security market growth from 2017 to 2028 and pie chart of cyber security market share. Showcasing this set of slides titled cyber risk security market growth with current trends summary pdf. The topics addressed in these templates are cyber security market share, cyber security expected market growth, banking and finance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Business Driven Security Architecture Introduction PDF
The slide shows a security framework of business driven services. It highlight cloud computing services such as SaaS, PaaS and IaaS and security services such as data security management, software and service assertion, technical service control, risk management infrastructure management, etc. Showcasing this set of slides titled Cloud Computing Business Driven Security Architecture Introduction PDF. The topics addressed in these templates are Strategies, Delegation Authority, Service Goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Technology Skills Gap Analysis Priorities Clipart PDF
This slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Showcasing this set of slides titled cyber security technology skills gap analysis priorities clipart pdf. The topics addressed in these templates are cyber security technology skills gap analysis priorities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Plan Icon Depicting Biometric Identification Topics PDF
Showcasing this set of slides titled IT Security Plan Icon Depicting Biometric Identification Topics PDF. The topics addressed in these templates are IT Security Plan Icon, Depicting Biometric Identification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Attack Incident Communication Plan Icon Professional PDF
Showcasing this set of slides titled IT Security Attack Incident Communication Plan Icon Professional PDF. The topics addressed in these templates are IT Security Attack, Incident Communication, Plan Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Communication Plan Development Strategy Icon Professional PDF
Showcasing this set of slides titled IT Security Communication Plan Development Strategy Icon Professional PDF. The topics addressed in these templates are IT Security Communication, Plan Development Strategy Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Plan Icon Depicting Computer Protection Icons PDF
Persuade your audience using this IT Security Plan Icon Depicting Computer Protection Icons PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Plan Icon, Depicting Computer Protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Firewall Data Network Security Management Technology Template PDF
The below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Persuade your audience using this Firewall Data Network Security Management Technology Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Packet Filtering, Proxy Service, Utm, Next Gen Firewall, Stateful Inspection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Building Data Analytics And Cyber Security Strategy Framework Icons PDF
This slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Persuade your audience using this Building Data Analytics And Cyber Security Strategy Framework Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Expansion, Standardize And Automate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Awareness Training Program For Employees Icon Mockup PDF
Persuade your audience using this IT Security Awareness Training Program For Employees Icon Mockup PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Employees Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Application Security Architecture Framework Elements PDF
The slide shows a framework describing security architecture to meet organizational unique requirements. It includes setting goals, determining process, constructing architecture and reviewing and revising security model. Showcasing this set of slides titled Cloud Computing Application Security Architecture Framework Elements PDF. The topics addressed in these templates are Set Goals, Determine Process, Construct Architecture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Service Company Revenue Allocation Background PDF
Showcasing this set of slides titled Cyber Security Service Company Revenue Allocation Background PDF. The topics addressed in these templates are Cyber Security, Service Company, Revenue Allocation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Certification Career Roadmap Icon Pictures PDF
Showcasing this set of slides titled Cyber Security Certification Career Roadmap Icon Pictures PDF. The topics addressed in these templates are Career Roadmap Icon, Cyber Security Certification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon Showcasing Online Security From Cyber Crime Clipart PDF
Showcasing this set of slides titled Icon Showcasing Online Security From Cyber Crime Clipart PDF. The topics addressed in these templates are Icon Showcasing Online, Security From Cyber Crime. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Compliance Traceability Matrix Icon Formats PDF
Showcasing this set of slides titled Cyber Security Compliance Traceability Matrix Icon Formats PDF. The topics addressed in these templates are Cyber Security, Compliance, Traceability Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Top Four Network IT Security Analysis Tools Guidelines PDF
This slide covers the tools used for the security analysis of the networks with their usage according to their needs on different occasions. It also includes the price or cost of these tools. Persuade your audience using this Top Four Network IT Security Analysis Tools Guidelines PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Network IT Security, Analysis Tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Wireless Network Security System Icon Depicting Router Connectivity Background PDF
Persuade your audience using this wireless network security system icon depicting router connectivity background pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon depicting router connectivity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Wireless Remote Control For Network Security System Themes PDF
Persuade your audience using this wireless remote control for network security system themes pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless remote control for network security system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Safety And Security Icon For Hotel Industry Formats PDF
Persuade your audience using this Safety And Security Icon For Hotel Industry Formats PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Safety And Security, Icon Hotel, Industry Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Icon For Digital Cyber Safety And Security Report Pictures PDF
Persuade your audience using this Icon For Digital Cyber Safety And Security Report Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Report, Icon For Digital, Cyber Safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Blockchain Business Methodology For Business Security Icon Clipart PDF
Persuade your audience using this Blockchain Business Methodology For Business Security Icon Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Business Methodology, Business Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Face Scanning Smart Phone Security Technique Icon Brochure PDF
Persuade your audience using this Face Scanning Smart Phone Security Technique Icon Brochure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Face Scanning, Smart Phone, Security Technique Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Smart Phone Device Web Cam Security Icon Download PDF
Persuade your audience using this Smart Phone Device Web Cam Security Icon Download PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Smart Phone, Device Web, Cam Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Analysis Shield Software Icon Themes PDF
Persuade your audience using this Cyber Security Risk Analysis Shield Software Icon Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Risk Analysis, Shield Software Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Year Data Sharing Security Network Career Roadmap Clipart
Introducing our five year data sharing security network career roadmap clipart. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Six Months Data Sharing Security Network Career Roadmap Pictures
Introducing our six months data sharing security network career roadmap pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Three Months Data Sharing Security Network Career Roadmap Diagrams
Introducing our three months data sharing security network career roadmap diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Four Quarter Organizations Data Security Employee Career Roadmap Download
Introducing our four quarter organizations data security employee career roadmap download. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Half Yearly Organizations Data Security Employee Career Roadmap Introduction
Introducing our half yearly organizations data security employee career roadmap introduction. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Network Security Architecture And Boundaries Graphics PDF
The slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Showcasing this set of slides titled Cloud Network Security Architecture And Boundaries Graphics PDF. The topics addressed in these templates are Presentation Mobility, Presentation Platform, Applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Bar Chart Representing Security Incident Strategic Action Plan Themes PDF
This slide shows the graphical presentation of security incident response plan which covers the effectiveness of response plan strategies such as hiring skilled employees, engaging security service providers, improving governance practices, etc. Showcasing this set of slides titled bar chart representing security incident strategic action plan themes pdf. The topics addressed in these templates are bar chart representing security incident strategic action plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
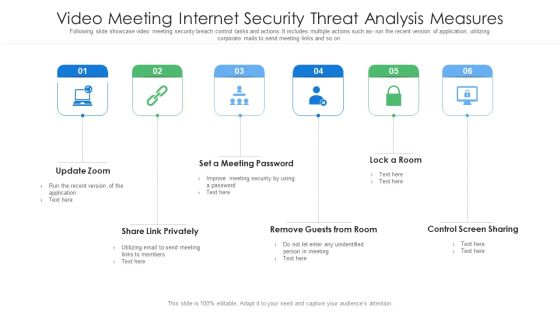
Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Security And Automation Control System Demonstration PDF
The purpose of this slide is to highlight the incorporation between business security and automation system which enables faster threat detection along with prominent control measures. The automated security system includes alarm systems, fire emergency buttons, control systems, and surveillance systems. Persuade your audience using this Business Security And Automation Control System Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Siren Alarm Systems, Fire Emergency Buttons, Surveillance Systems, Control System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organization Security Issues And Solution Assessment Ideas PDF
This slide showcases problems in firm related to security of crucial data important for organization. The issues include data breach, SPAM, phishing and insider threat. Persuade your audience using this Organization Security Issues And Solution Assessment Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breach, SPAM And Phishing, Insider Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Quarterly Data Sharing Security Network Career Roadmap Guidelines
Presenting our jaw-dropping quarterly data sharing security network career roadmap guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
Eight Steps Infographics To Improve Cyber Security Icons PDF
Persuade your audience using this eight steps infographics to improve cyber security icons pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including threats, knowledge, monitoring, authentication, protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
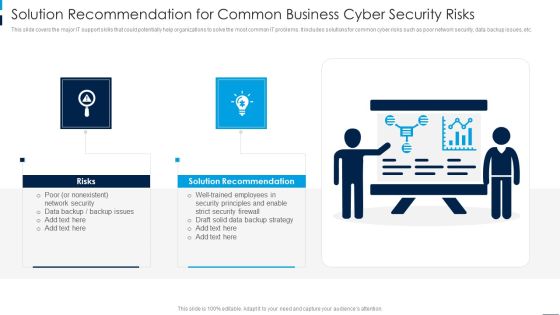
Solution Recommendation For Common Business Cyber Security Risks Rules PDF
This slide covers the major IT support skills that could potentially help organizations to solve the most common IT problems. It includes solutions for common cyber risks such as poor network security, data backup issues, etc. Persuade your audience using this Solution Recommendation For Common Business Cyber Security Risks Rules PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Solution Recommendation, Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Year Organizations Data Security Employee Career Roadmap Inspiration
Presenting our jaw-dropping five year organizations data security employee career roadmap inspiration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
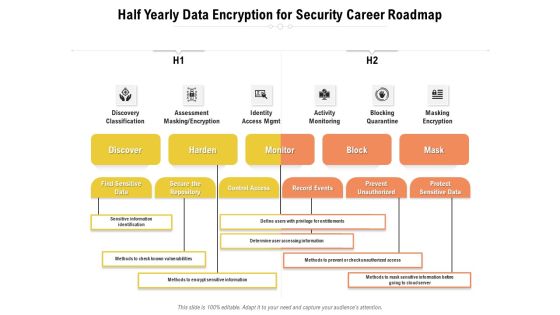
Half Yearly Data Encryption For Security Career Roadmap Structure
Presenting our jaw-dropping half yearly data encryption for security career roadmap structure. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Six Months Organizations Data Security Employee Career Roadmap Ideas
Presenting our jaw-dropping six months organizations data security employee career roadmap ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
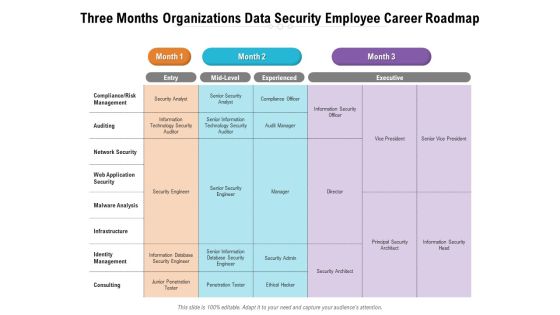
Three Months Organizations Data Security Employee Career Roadmap Background
Presenting our jaw-dropping three months organizations data security employee career roadmap background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
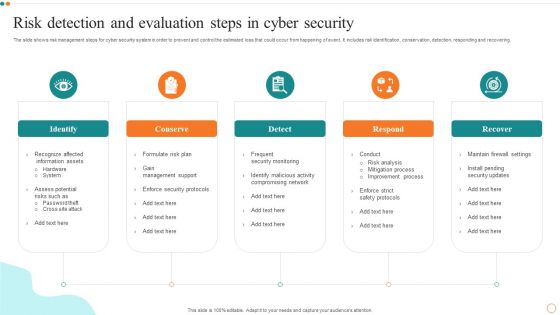
Risk Detection And Evaluation Steps In Cyber Security Designs PDF
Persuade your audience using this Risk Detection And Evaluation Steps In Cyber Security Designs PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Detection, Evaluation Steps. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Effective Online Security Risk Assessment Process Inspiration PDF
This slide showcases digital safety risk assessment process which helps identify potential cyber vulnerabilities. It provides steps such as asset prioritization, identify threat, analyze controls, assess impact and recommend controls. Persuade your audience using this Effective Online Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Card Data Security, Cross Border Transactions, Payment Methods. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Components Of People Centric Work Culture Security Ideas PDF
The following slide highlights the key elements of people centric security to prevent data breaches and IT damages. It includes activities such as personalized training, artificial intelligence AI and machine learning ML tools and prompt social engineering attacks etc. Persuade your audience using this Key Components Of People Centric Work Culture Security Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Personalized Training, Artificial Intelligence, Engineering Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risk Security Maturity Model With Protection Levels Mockup PDF
The following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Persuade your audience using this cyber risk security maturity model with protection levels mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including secure systems, vulnerability management, threat intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Potential Threats For Smart Phone Security Summary PDF
This slide show various categories of potential risks for phone security that can lead to various type of loss. It include potential risks such as surveillance threat, data theft and financial loss, etc. Persuade your audience using this Key Potential Threats For Smart Phone Security Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Botnet Activities, Impersonation Threats, Financial Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Safety And Security App Mapping Icon Slides PDF
This slide showcases comparative analysis various tools used for application mapping to help organization identify best available option. It further includes details about price, free trail and characteristics. Showcasing this set of slides titled Safety And Security App Mapping Icon Slides PDF. The topics addressed in these templates are Safety And Security, App Mapping Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
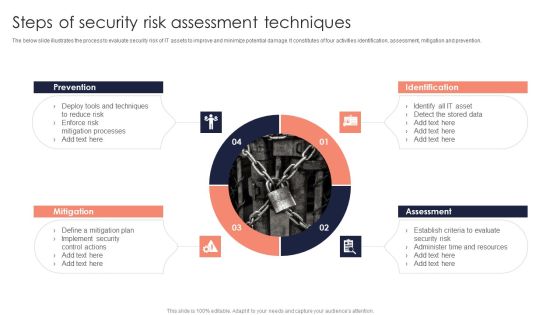
Steps Of Security Risk Assessment Techniques Introduction PDF
The below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Showcasing this set of slides titled Steps Of Security Risk Assessment Techniques Introduction PDF. The topics addressed in these templates are Prevention, Identification, Assessment, Mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
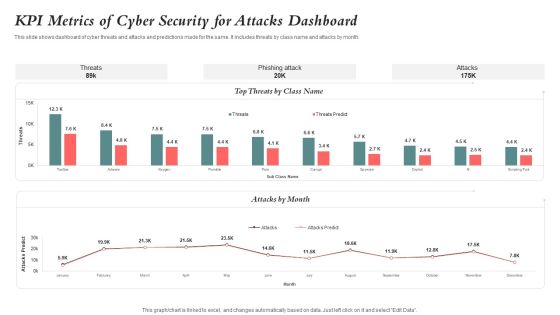
KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF
This slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Showcasing this set of slides titled KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF. The topics addressed in these templates are Kpi Metrics, Cyber Security, Attacks Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
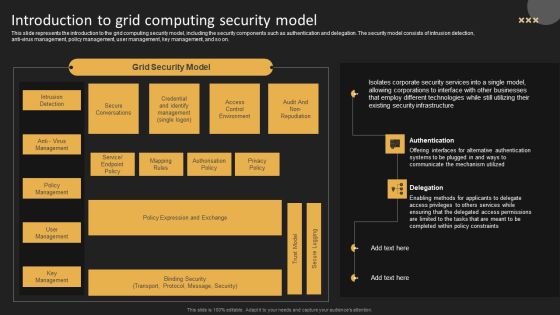
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Threat Dashboard With KPI Metrics Icons PDF
This slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Showcasing this set of slides titled Cyber Security Threat Dashboard With KPI Metrics Icons PDF. The topics addressed in these templates are Cyber Security Threat Dashboard, Kpi Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computer System Security PowerPoint Templates And PowerPoint Themes 1012
Computer System Security PowerPoint Templates And PowerPoint Themes 1012-Deliver amazing Presentations with our above template consists of laptop and lifesaver. This image represents the concept of computer help or assistance. This template also depicts the concept of computer security. Use this template for web services, technical support etc. It signifies assistance, nteworking, rescue and save. It is a useful captivating tool conceived to enable you to define your message in your Business PPT presentations. Deliver amazing presentations to mesmerize your audience.-Computer System Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Computer network , marketing, finance, internet, computer, technology
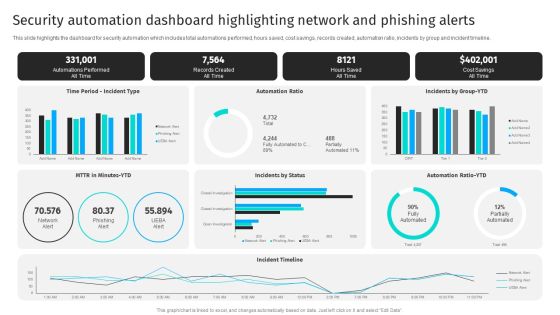
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Five Year Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured five year data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Four Quarter Individual Data Security Career Roadmap Sample
Presenting our innovatively-structured four quarter individual data security career roadmap sample Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
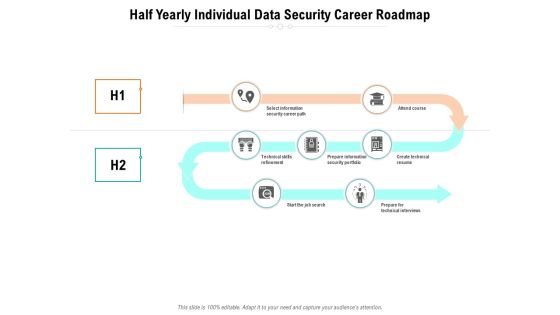
Half Yearly Individual Data Security Career Roadmap Slides
Presenting our innovatively-structured half yearly individual data security career roadmap slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Six Months Data Encryption For Security Career Roadmap Structure
Presenting our innovatively-structured six months data encryption for security career roadmap structure Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Three Months Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured three months data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps Included In Data Retention Security Mechanism Introduction PDF
This slide depicts the steps covered in data retention policy. The steps included are determine applicable regulations, catalogue data, decision making, policy documentation and implementation.Persuade your audience using this Steps Included In Data Retention Security Mechanism Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Catalogue Data, Decision Making, Document Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Incident Management Checklist Before An Incident Icons PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cyber Security Incident Management Checklist Before An Incident Icons PDF from Slidegeeks and deliver a wonderful presentation.

IT Security Employee Awareness Training Budget For FY2020 Ppt Pictures Example PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative information technology security employee awareness training budget for fy2020 ppt gallery information pdf bundle. Topics like employee awareness training budget for fy2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

AI Applications In Cyber Security To Enhance Safety Elements PDF
This slide covers use of artificial intelligence in cyber security to enhance safety. It involves uses such as detecting new threats, battling bots, breach risk prediction and better end point protection.Persuade your audience using this AI Applications In Cyber Security To Enhance Safety Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Prediction, Endpoint Protection, Countering Bots. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Safety And Security Incident Report Writing Tips Pictures PDF
This slide shows tips which can be used to prepare security incident report. These tips are include proof, observe and utilize software. Persuade your audience using this Safety And Security Incident Report Writing Tips Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Include Proof, Observe, Utilize Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Iot Smart Home Security Management Technology Demonstration PDF
This slide provides the use of smart security technology to get real time monitoring of home and obtain authenticity. Key features mentioned are smart cameras, biometric locks, smart cameras, connected switches and fire sensor. Persuade your audience using this Iot Smart Home Security Management Technology Demonstration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Smart Cameras, Biometric Locks, Smart Cameras, Connected Switches, Fire Sensor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Multistep Process Of Security Risk Management Slides PDF
This slide shows multistep process of security risk acceptance which contains identifying risk, summarizing risk and risk acceptance and action. This can assist businesses in understanding the cause and effect of risks. Persuade your audience using this Multistep Process Of Security Risk Management Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Identifying Risk, Summarizing Risk, Risk Acceptance And Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
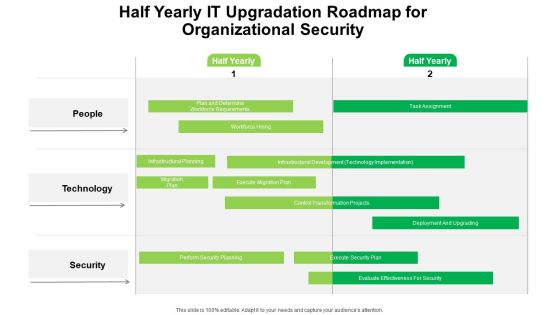
Half Yearly IT Upgradation Roadmap For Organizational Security Portrait
Introducing our half yearly it upgradation roadmap for organizational security portrait. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
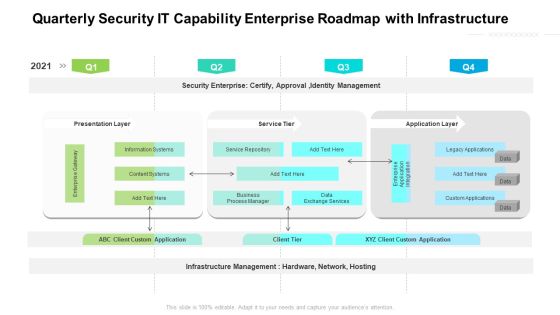
Quarterly Security IT Capability Enterprise Roadmap With Infrastructure Background
Presenting our jaw dropping quarterly security it capability enterprise roadmap with infrastructure background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Three Months IT Upgradation Roadmap For Organizational Security Brochure
Presenting our jaw dropping three months it upgradation roadmap for organizational security brochure. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
