AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Information Security Ppt
Information Security Ppt
Organizational Network Security Awareness Staff Learning Post It Icons PDF
This is a organizational network security awareness staff learning post it icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Network Security Awareness Staff Learning Idea Generation Designs PDF
This is a organizational network security awareness staff learning idea generation designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like idea generation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Post It Notes Portrait PDF
This is a project security administration it post it notes portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Info Security Wd Ppt PowerPoint Presentation Gallery Maker PDF
Presenting table of contents for info security wd ppt powerpoint presentation gallery maker pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like cyber risk assessment, steps for mitigation, cyber risk identification, key elements of information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
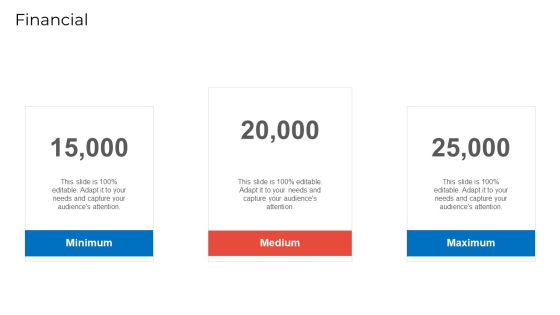
Implementing Security Management Strategy To Mitigate Risk Financial Summary PDF
This is a implementing security management strategy to mitigate risk financial summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

E Business And Cyber Risk Management Security Lifecycle Infographics PDF
Presenting e business and cyber risk management security lifecycle infographics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like implement, information system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
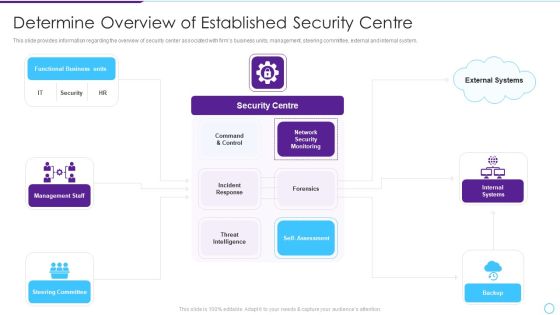
Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functional Business Units, Security Centre, Internal Systems, Self Assessment, Steering Committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Cyber Safety Incident Management Security Microsoft PDF
This is a table of contents cyber safety incident management security microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current scenario assessment, handling cyber threats to secure digital assets, ensuring physical security, securing firm from natural calamity threats . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. This is a Pricing Plan Of Security Awareness Packages Elements PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Pricing Plan, Security Awareness, Packages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Google Cloud Services Identity And Security Graphics PDF
This slide describes the identity and security service of google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a Google Cloud Services Identity And Security Graphics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Resource Manager, Cloud Security Scanner, Cloud Platform Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Domains That Will Be Addressed By ISMS Diagrams PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.This is a Security Domains That Will Be Addressed By ISMS Diagrams PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Support, Resources Security, Prevention Of Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
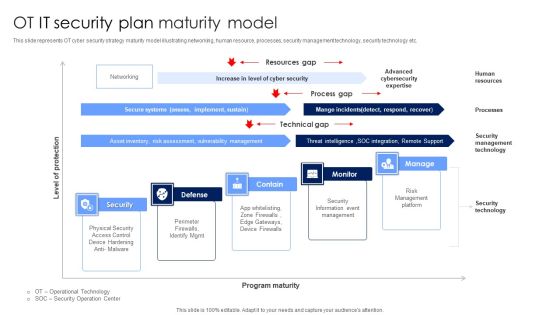
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Technology Guide For Serverless Computing Cloud Computing Security Designs PDF
Presenting technology guide for serverless computing cloud computing security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security categories, security domains, security risks, security threats, security dimensions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Breach Prevention Recognition Security Awareness Program Checklist Template PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a data breach prevention recognition security awareness program checklist template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, sustaining security awareness, document security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Infrastructure Building Administration Interdependence Resiliency And Security Microsoft PDF
This is a infrastructure building administration interdependence resiliency and security microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Developing Firm Security Strategy Plan Clipart PDF
This is a agenda for developing firm security strategy plan clipart pdf template with various stages. Focus and dispense information on fours stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security risks, develop effective, strategy, dynamic and flexible. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Security Solutions Analyzing Different SOC Deployment Models Themes PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a organizational security solutions analyzing different soc deployment models themes pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats End User Control Themes PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Security Threats End User Control Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Centralized Data, Customer, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
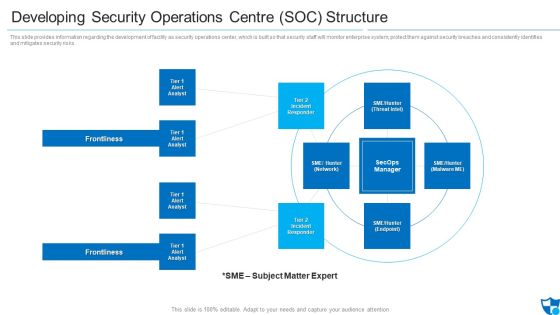
Developing Security Operations Centre SOC Structure Microsoft PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting developing security operations centre soc structure microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident responder, tier 2 incident responder, frontlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Running Cyber Security Awareness Campaign For Employees Clipart PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered.Presenting Running Cyber Security Awareness Campaign For Employees Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Campaign Objectives, Security Awareness, Security Awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
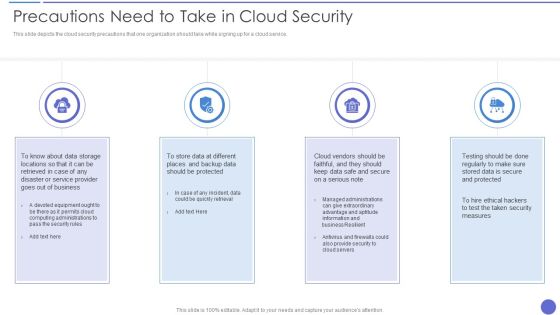
Precautions Need To Take In Cloud Security Template PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. This is a Precautions Need To Take In Cloud Security Template PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Measures, Business Resilient, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Overview Of Cyber Security Awareness Course Clipart PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This is a Overview Of Cyber Security Awareness Course Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Learning Outcome, Attendees, Course Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roles And Responsibilities Of Cyber Security Team Designs PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide.This is a Roles And Responsibilities Of Cyber Security Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Operations Manager, Risk Manager . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Security Awareness Tracking Kpis Ideas PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a data breach prevention recognition security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Staff Learning Security Awareness Tracking Kpis Demonstration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a organizational network staff learning security awareness tracking kpis demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Current Security Management Challenges The Company Is Facing Elements PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.This is a Current security management challenges the company is facing elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, employee management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Our Expertise Pictures PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Security Camera System Company Profile Our Expertise Pictures PDF template with various stages. Focus and dispense information on Eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Internet Protocol, Physical Security, Communication Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Organization Chart Topics PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. This is a Security Agency Business Profile Organization Chart Topics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operations Supervisor, Security Personnel, Relief Security Personnel. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Email Security Encryption And Data Loss Prevention Roadmap Icons PDF
This is a email security encryption and data loss prevention roadmap icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap, 2017 to 2020. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Encryption And Data Loss Prevention Timeline Template PDF
This is a email security encryption and data loss prevention timeline template pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2013 to 2020. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Contract Breaches With Clients Download PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting Cloud Security Threats Contract Breaches With Clients Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Organization, Business Partners, Information Could. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Developing Firm Security Strategy Plan Post It Notes Download PDF
This is a developing firm security strategy plan post it notes download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Machine To Machine Communication What Is Iot Security Portrait PDF
The slide highlights IoT session layer protocol.This is a machine to machine communication what is iot security portrait pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, command and control center. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Security Assessment Ideas PDF
Presenting Table Of Contents For Cloud Security Assessment Ideas PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Cloud Security, Security Different, Security Is Important. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Security Solutions Timeframe For Incident Management Elements PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting organizational security solutions timeframe for incident management elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
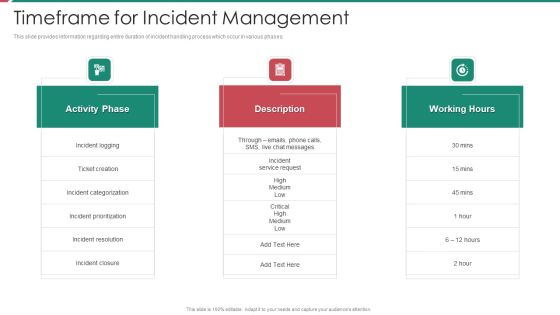
Security And Process Integration Timeframe For Incident Management Sample PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting security and process integration timeframe for incident management sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Need For Cyber Security Awareness Training Professional PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Presenting Need For Cyber Security Awareness Training Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organization Different, Technological Defenses, Awareness Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security In 5G Technology Architecture 5G Functional Architecture Formats PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.This is a Security In 5G Technology Architecture 5G Functional Architecture Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previous Generations, Distinguish Authentication, Transactions Adaptable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Security Solutions Facilities Offered By Successful Implementation Clipart PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a organizational security solutions facilities offered by successful implementation clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
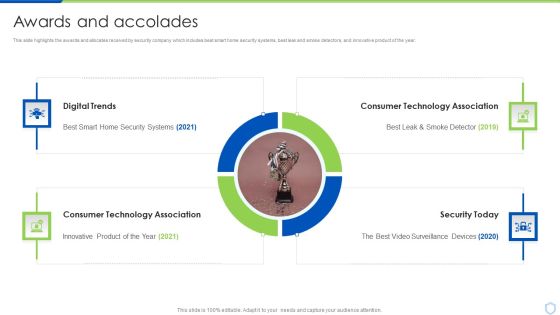
Security And Surveillance Company Profile Awards And Accolades Structure PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year.This is a Security And Surveillance Company Profile Awards And Accolades Structure PDF template with various stages. Focus and dispense information on Four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Digital Trends, Consumer Technology, Technology Association. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Client Testimonials And Reviews Inspiration PDF
This slide highlights the security guard company client testimonials and reviews which includes ratings from head of retail store, principal of school and manager of financial institution. This is a Security Agency Business Profile Client Testimonials And Reviews Inspiration PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Services, Financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Measures And Controls In Cloud Security Ideas PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. This is a Measures And Controls In Cloud Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Customer Testimonials Sample PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Security And Surveillance Company Profile Customer Testimonials Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Valuables Are Safe, Thousand Dollar, Security Devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Employees Rules And Regulations Mockup PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. This is a Security Agency Business Profile Employees Rules And Regulations Mockup PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees, Security Officer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Swot Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes 30 years experience as strengths, attacks on security personnel as weakness, high industry growth as opportunity and high attrition rate as threats. This is a Security Agency Business Profile Swot Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities, Threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
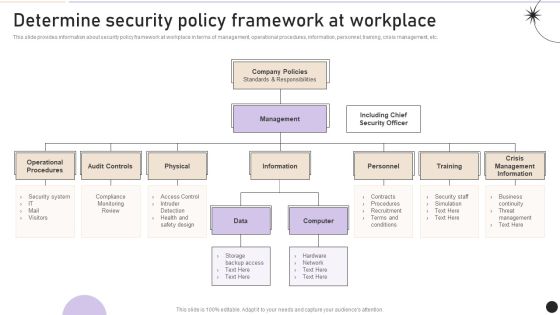
Determine Security Policy Framework At Workplace Pictures PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Get a simple yet stunning designed Determine Security Policy Framework At Workplace Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Security Policy Framework At Workplace Pictures PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Security Threats Loss Of Data Guidelines PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a Cloud Security Threats Loss Of Data Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategies, Service Provider, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Backup And Data Recovery Inspiration PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. This is a Cloud Security Checklist Backup And Data Recovery Inspiration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Plan, Cloud Service, Location Of Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps To Ensure Robotic Process Automated Security Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a Steps To Ensure Robotic Process Automated Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Protect Log Respectability, Empower Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Employee And Staff Welfare Professional PDF
This slide highlights the staff and employee welfare services which includes social security, insurance, medical, accommodation, pick and drop services. Presenting Security Agency Business Profile Employee And Staff Welfare Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Social Security, Insurance, Accommodation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Logging And Monitoring Download PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a Cloud Security Checklist Logging And Monitoring Download PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Potential, Observe Systems, Security Breaches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Benefits Of Cyber Security Awareness Training Background PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide.This is a Key Benefits Of Cyber Security Awareness Training Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drive Awareness, Reduce Threat, Amongst Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategy To Provide Layered Security Across Networks Elements PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Presenting Strategy To Provide Layered Security Across Networks Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Network, Applications, Device. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot Security Lock For Safe Fleet Management Mockup PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Mockup PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effect After Implementing Cyber Risk Security Awareness Program Professional PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments.This is a effect after implementing cyber risk security awareness program professional pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like lowest mobile malware infections, lowest computer malware infections. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Regaining Reputation Of Our Company Infographics PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies.This is a IT Security Hacker Regaining Reputation Of Our Company Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers And Clients, Appropriate Service, Database Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Iot Security Lock For Safe Fleet Management Sample PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Our Global Presence Inspiration PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. This is a Manpower Corporate Security Business Profile Our Global Presence Inspiration PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Our Global Presence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile SWOT Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. This is a Security And Surveillance Company Profile SWOT Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financials Position, Innovation Centers, Operations Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Home Security Solutions Company Profile Customer Testimonials Formats PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Smart Home Security Solutions Company Profile Customer Testimonials Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Testimonials. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Customer Testimonials Summary PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Security Camera System Company Profile Customer Testimonials Summary PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Testimonials. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile SWOT Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. This is a Security Camera System Company Profile SWOT Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Cyber Security Breach General Consequences Ideas PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. This is a Impact Of Cyber Security Breach General Consequences Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reputational Damage, Monetary Penalty, Operational Disruption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Our Business Approach Diagrams PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. This is a Security Agency Business Profile Our Business Approach Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Planning, Participatory Management, Productivity Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Case Study Mockup PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. This is a Manpower Corporate Security Business Profile Case Study Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Solution, Benefits, The Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Organization Chart Rules PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. This is a Manpower Corporate Security Business Profile Organization Chart Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Operations Supervisor, Audit Team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Circular Diagram Structure PDF
Presenting project security administration it circular diagram structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like circular diagram. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Organizational Network Security Awareness Staff Learning Financials Portrait PDF
Presenting organizational network security awareness staff learning financials portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Venn Summary PDF
Presenting organizational network security awareness staff learning venn summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like venn. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Developing Firm Security Strategy Plan Financial Template PDF
Presenting developing firm security strategy plan financial template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Stakeholders Of Cyber Security Awareness Training Mockup PDF
Presenting Key Stakeholders Of Cyber Security Awareness Training Mockup PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Senior Mangers, Line Managers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Web Development What Is The Cyber Security Designs PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Web Development What Is The Cyber Security Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Categories Of Cyber, Operational Security, Includes Network Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
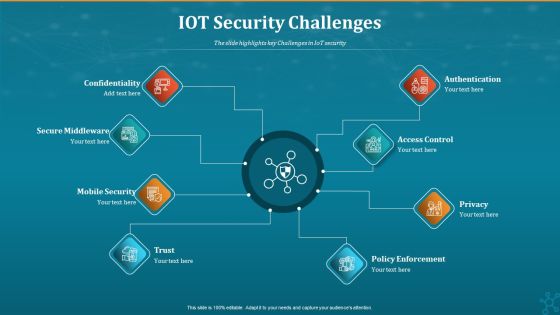
Machine To Machine Communication IOT Security Challenges Pictures PDF
The slide highlights key Challenges in IoT security.Presenting machine to machine communication iot security challenges pictures pdf. to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like confidentiality, secure middleware, policy enforcement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Transformation Trends In It And Cyber Security Designs PDF
This slide signifies digital transformation in Information technology and cyber security. It includes trends like securing assets, cloud computing, data analytics, security and automation. Persuade your audience using this digital transformation trends in it and cyber security designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including securing digital assets, cloud computing, data analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizational Network Staff Learning Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting organizational network staff learning security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security awareness program, implementing security awareness, sustaining security awareness. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Management Plan Table Of Contents Pictures PDF
Presenting cyber security risk management plan table of contents pictures pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like present scenario, roles and responsibilities, training and budget, dashboards, security infrastructure performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Web Application Firewall Infra Cyber Security Designs PDF
The following slide showcases web application firewalls hardware and software used to protect from security threats. It presents information related to legit traffic, visibility, compliance, etc. Showcasing this set of slides titled Web Application Firewall Infra Cyber Security Designs PDF. The topics addressed in these templates are Correlation Engines, AI Powered Traffic Pattern, Application Profiling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Current Security Management Challenges The Company Is Facing Download PDF
Presenting current security management challenges the company is facing download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like potential insider threats, external security breaches, rise of caas. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Advantages, Disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Types Of Disaster Recovery Plan Topics PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a desktop security management types of disaster recovery plan topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, locations, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Implementation Of Strong Password Policy Brochure PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a desktop security management implementation of strong password policy brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Introduction To Ethical Hacking Graphics PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network.This is a IT Security Hacker Introduction To Ethical Hacking Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Approved Effort, Data Is Referred, Ethical Hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Process Of Disaster Recovery Planning Professional PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a desktop security management process of disaster recovery planning professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plans, team, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Minimize Administrative And Staff Privileges Download PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a desktop security management minimize administrative and staff privileges download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategic Action Plan Of It Security Incident Ideas PDF
This slide covers the response plan of information security incident which shows sections and their description such as introduction, using incident response plan, event handling, incident topology, post-incident procedures, etc. Persuade your audience using this strategic action plan of it security incident ideas pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including strategic action plan of it security incident. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security And Surveillance Company Profile Our Expertise Professional PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. Presenting Security And Surveillance Company Profile Our Expertise Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Secure Environment, Communication Infrastructure, Physical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Workplace Employee Assistance Program Structure PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a project security administration it workplace employee assistance program structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pillars Of Cloud Security Visibility And Consistency Demonstration PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Presenting Pillars Of Cloud Security Visibility And Consistency Demonstration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Best Cloud Framework, Data Security, Asset Inventory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively.This is a IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disasters, Physical Location, Assessment Report. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement IPO Roadshow Topics PDF
The slide provides an overview of the IPO Roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc. This is a financing catalogue for security underwriting agreement ipo roadshow topics pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merchant bankers, portfolio managers, financials institutions, foreign investors, insurance companies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. This is a Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Case Undersubscription, Interested Investors, Normal Subscription You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operations Management Skills Software Security Skills Pictures PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Presenting operations management skills software security skills pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of IT Security End User Education Ppt Summary Portrait PDF
This slide shows the end-user education within the network security model. It also represents various factors that effective training plans should involve. Presenting elements of information technology security end user education ppt model graphics pictures pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like elements of information technology security end user education. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Awards And Accolades Download PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Manpower Corporate Security Business Profile Awards And Accolades Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Asis International, Gptw Institute, Sia Awards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Functioning Centre Facilities Offered By Successful Implementation Infographics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting security functioning centre facilities offered by successful implementation infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like risk mitigation, investigations, employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine New Roles Pivotal For Successful Devops Security Designs PDF
This slide provides information regarding the new roles considered as pivotal for successful DevOps in terms of DevOps evangelist, release manager, automation architect integration specialist. Presenting determine new roles pivotal for successful devops security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like manager, management, coordination. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Mobile Device Management Mobile Device Security Management Slides PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. Presenting Addressing Mobile Device Management Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Corporate Owned, Personally Enabled, Equipment Personal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Cloud Security Work Governance Professional PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting How Does Cloud Security Work Governance Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Access Management, Business Continuity Planning, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Evaluating IT System Security Using SWOT Analysis Portrait PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Presenting Evaluating IT System Security Using SWOT Analysis Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Services Security Architecture Assessment Infographics PDF
The slideshows an assessment model of CSP cloud service security. It includes identification of existing warrant, verification of certificates and reports, evidence review and additional information collection about third party warrant and certificates. Showcasing this set of slides titled Cloud Computing Services Security Architecture Assessment Infographics PDF. The topics addressed in these templates are Cloud Control Profile, Administrative Need, Safety Security Needs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Industries That Can Benefit From Cloud Security Brochure PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds. Presenting Industries That Can Benefit From Cloud Security Brochure PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Cloud Security, Production, Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Key Technological Trends In Online Security Clipart PDF
This slide highlights latest technological trends seen to build safe digitally safe infrastructure. It provides information regarding artificial intelligence, behavioral analytics, hardware authentication, blockchain cybersecurity and zero trust security model. Persuade your audience using this Key Technological Trends In Online Security Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Behavioral Analytics, Artificial Intelligence, Embedded Hardware Authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Smart Home Security Solutions Company Profile SWOT Analysis Rules PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. Presenting Smart Home Security Solutions Company Profile SWOT Analysis Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths Weaknesses Opportunities, Threats Market Technology, Home Security Devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Swot Analysis Introduction PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Swot Analysis Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weaknesses, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Use Of Security Programs Mockup PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Vulnerability Administration Plan And Security Services Topics PDF
This slide defines the vulnerability management program and security services based on risk. It includes information related to integrating, assessment planning, analysis and sustainability. Persuade your audience using this Vulnerability Administration Plan And Security Services Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Integrating, Assessment Planning, Analysis And Reporting, Sustainability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Data Security Software As A Service Saas Portrait PDF
This slide describes the software as a service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model. Presenting Cloud Data Security Software As A Service Saas Portrait PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Advantages, Disadvantages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

What Are The Downsides Of A Cloud Security Download PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting What Are The Downsides Of A Cloud Security Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Manage Security In Cloud Background PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting How To Manage Security In Cloud Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Firewalls, Access Controls, Data Recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organization Reinvention Need Of Cyber Security In Organization Graphics PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Reinvention Need Of Cyber Security In Organization Graphics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Security Confidential Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Our Global Presence Themes PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. Presenting Security Agency Business Profile Our Global Presence Themes PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Developed Markets, Customers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Dashboard With KPI Metrics Elements PDF
This slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Showcasing this set of slides titled Cyber Security Risk Dashboard With KPI Metrics Elements PDF. The topics addressed in these templates are Vulnerability Management Program, Reports And Metrics Elaboration, Critical Risk Identified. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
