AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Information Security Ppt
Information Security Ppt

Shared Responsibility For Cloud Network Security Microsoft PDF
The slide represents shared responsibilities that dictate security obligations ensuring accountability of both the cloud computing provider and its users. The elements are responsibilities such a data classification, client and end point protection, identity and access management etc. Showcasing this set of slides titled Shared Responsibility For Cloud Network Security Microsoft PDF. The topics addressed in these templates are Cloud Companion Guide, Foundation Benchmark, On Premises. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Critical Violations Security Dashboard With KPI Metrics Graphics PDF
This slide shows dashboard of security to mitigate violation by prioritizing KPIs. It includes application control, operating systems, restrict admin privileges, multi factor authentication and backup of important data. Showcasing this set of slides titled Critical Violations Security Dashboard With KPI Metrics Graphics PDF. The topics addressed in these templates are Risk Model, Application Components, Technologies Overview. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Dashboard For Technological Smart Homes Security System Management Designs PDF
This side showcase the dashboard of security system management for tracking and forecasting matrices for better functioning of devices. It include the statistic data such as temperature, power consumed, devices working, and list of devices connected. Showcasing this set of slides titled Dashboard For Technological Smart Homes Security System Management Designs PDF. The topics addressed in these templates are Smart Light, Smart Heating, Smart Cooling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Scan Principle For Smart Phone Security Model Clipart PDF
This slide shows SCAN framework for securing phone against possible threats to prevent loss of business data. It include components such as system, configuration, application and network, etc. Persuade your audience using this Scan Principle For Smart Phone Security Model Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including System, Configuration, App. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

User Authentication And Authorization Security Management Technology Summary PDF
This slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Persuade your audience using this User Authentication And Authorization Security Management Technology Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Based, Multi Factor, Certificate Based, Biometrics, Token Based. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risk Intelligence Services For Enterprise Security Icons PDF
Persuade your audience using this cyber risk intelligence services for enterprise security icons pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including incident resolution, threat protection, it services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Access Regulations Technology Six Months Roadmap With Security Solution Brochure
Introducing our access regulations technology six months roadmap with security solution brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
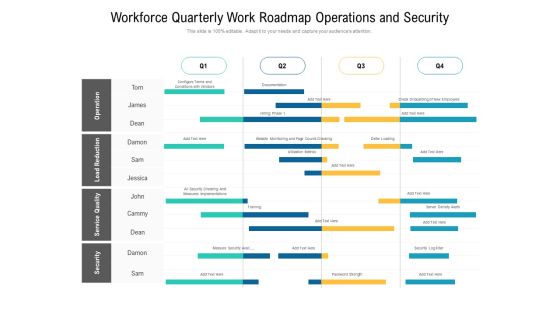
Workforce Quarterly Work Roadmap Operations And Security Demonstration
Introducing our workforce quarterly work roadmap operations and security demonstration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Disaster Recuperation Quarterly Roadmap To Eradicate Intrusion Icons
Introducing our cyber security disaster recuperation quarterly roadmap to eradicate intrusion icons. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Computing Security Quarterly Roadmap With Deployment Plan Themes
Introducing our cloud computing security quarterly roadmap with deployment plan themes. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Five Years Roadmap For Employee Security Recognition Clipart
Introducing our five years roadmap for employee security recognition clipart. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Half Yearly Roadmap For Employee Security Recognition Formats
Introducing our half yearly roadmap for employee security recognition formats. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Six Months Roadmap For Employee Security Recognition Inspiration
Introducing our six months roadmap for employee security recognition inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
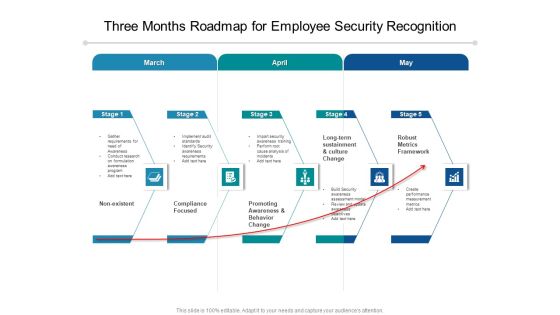
Three Months Roadmap For Employee Security Recognition Themes
Introducing our three months roadmap for employee security recognition themes. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Strategic Process Management Six Months Timeline Structure
Introducing our cyber security strategic process management six months timeline structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
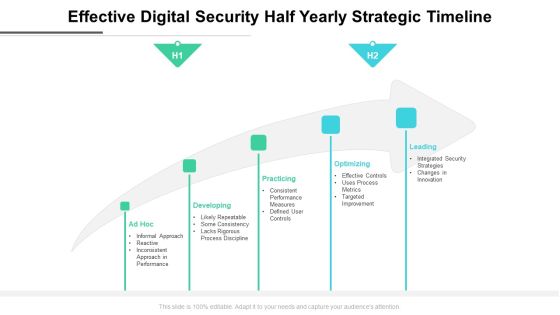
Effective Digital Security Half Yearly Strategic Timeline Download
Introducing our effective digital security half yearly strategic timeline download. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Security Operations Metrics For Detection And Response Effectiveness Structure PDF
Showcasing this set of slides titled Security Operations Metrics For Detection And Response Effectiveness Structure PDF. The topics addressed in these templates are Operations Metrics, Detection, Response Effectiveness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Business Automated Security Management Framework Professional PDF
This slide showcases a framework of automated security governance for an IT business to safeguard technology infrastructure from risks. It includes key components such as policies, constraints, business rules, analysis, diagnosis, trials, logs, etc. Showcasing this set of slides titled IT Business Automated Security Management Framework Professional PDF. The topics addressed in these templates are Monitor, Direct, Evaluator. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Blockchain Security Technology For Healthcare Industry Icons PDF
This slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification.Persuade your audience using this Blockchain Security Technology For Healthcare Industry Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authenticity Medicine, Electronic Health, Ensures Only Trusted. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Year Individual Data Security Career Roadmap Guidelines
Presenting the five year individual data security career roadmap guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
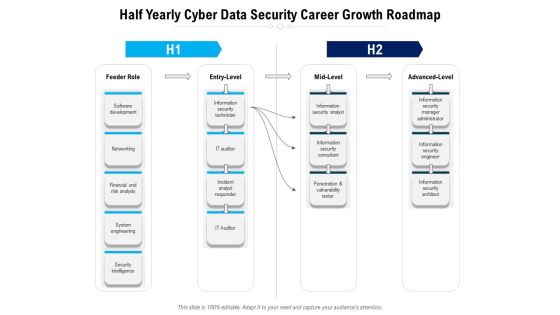
Half Yearly Cyber Data Security Career Growth Roadmap Topics
Presenting the half yearly cyber data security career growth roadmap topics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
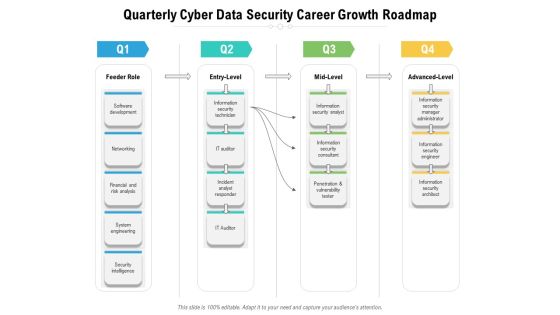
Quarterly Cyber Data Security Career Growth Roadmap Infographics
Presenting the quarterly cyber data security career growth roadmap infographics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Individual Data Security Career Roadmap Slides
Presenting the six months individual data security career roadmap slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Individual Data Security Career Roadmap Inspiration
Presenting the three months individual data security career roadmap inspiration. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
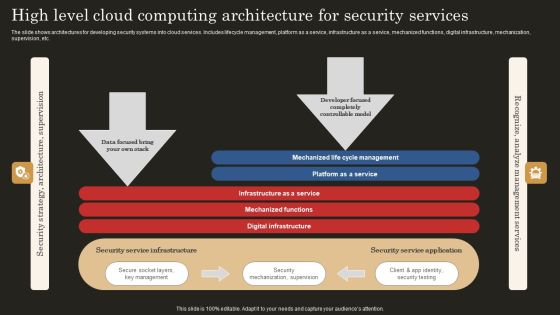
High Level Cloud Computing Architecture For Security Services Ideas PDF
The slide shows architectures for developing security systems into cloud services. Includes lifecycle management, platform as a service, infrastructure as a service, mechanized functions, digital infrastructure, mechanization, supervision, etc. Showcasing this set of slides titled High Level Cloud Computing Architecture For Security Services Ideas PDF. The topics addressed in these templates are Infrastructure Service, Mechanized Functions, Digital Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
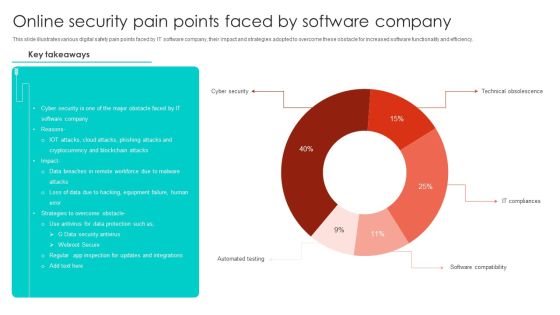
Online Security Pain Points Faced By Software Company Microsoft PDF
This slide illustrates various digital safety pain points faced by IT software company, their impact and strategies adopted to overcome these obstacle for increased software functionality and efficiency. Showcasing this set of slides titled Online Security Pain Points Faced By Software Company Microsoft PDF. The topics addressed in these templates are Cyber Security, Blockchain Attacks, Equipment Failure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Management Risk And Compliance Model Summary PDF
The following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Showcasing this set of slides titled Cloud Security Management Risk And Compliance Model Summary PDF. The topics addressed in these templates are Governance, Risk, Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparison Analysis Between Security Operations And Devops Inspiration PDF
This slide summarizes the difference between SecOps and DevOps methodologies that increase the efficiency and scalability of complex operations. It includes parameters such as goal, processing strategy, change implementation, focus on, team involved, etc. Showcasing this set of slides titled Comparison Analysis Between Security Operations And Devops Inspiration PDF. The topics addressed in these templates are Implementation, Processing Strategy, Security Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Risk Management And Incident Management Dashboard Icons PDF
This slide displays dashboard to help company in designing initiatives to mitigate cybersecurity risks. It includes kpis such as incident management, patches, compliance, vulnerabilities, etc. Showcasing this set of slides titled IT Security Risk Management And Incident Management Dashboard Icons PDF. The topics addressed in these templates are Compliance, Patches, Incident Management, Vulnerabilities Management, Cybersecurity Initiatives. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Risk Management Process For Organization Template PDF
This slide displays flow diagram to illustrate cybersecurity risk management process to ensure continuous monitoring. It includes components such as threats, vulnerabilities, impacts, intelligence, etc. Showcasing this set of slides titled IT Security Risk Management Process For Organization Template PDF. The topics addressed in these templates are Organization, Cyber Intelligence, Continuous Monitoring, Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Security Plan Quarterly Roadmap For IT Project Slides
Presenting our innovatively structured cloud computing security plan quarterly roadmap for it project slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
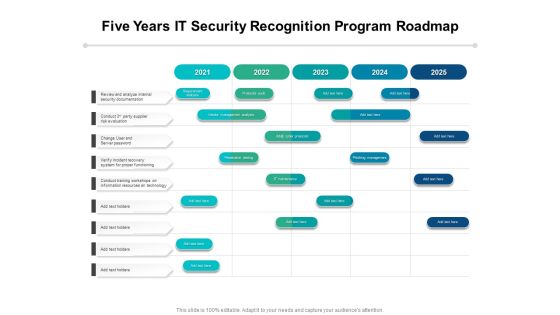
Five Years IT Security Recognition Program Roadmap Introduction
Presenting our innovatively-structured five years it security recognition program roadmap introduction Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Half Yearly IT Security Recognition Program Roadmap Designs
Presenting our innovatively-structured half yearly it security recognition program roadmap designs Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Six Months IT Security Recognition Program Roadmap Diagrams
Presenting our innovatively-structured six months it security recognition program roadmap diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
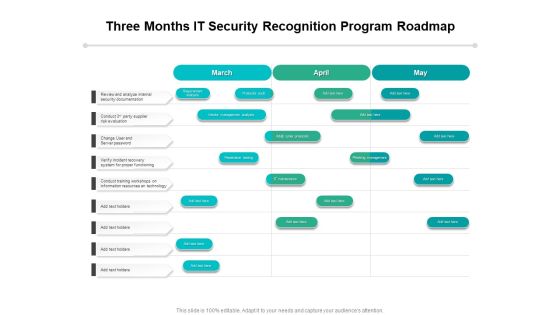
Three Months IT Security Recognition Program Roadmap Topics
Presenting our innovatively-structured three months it security recognition program roadmap topics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
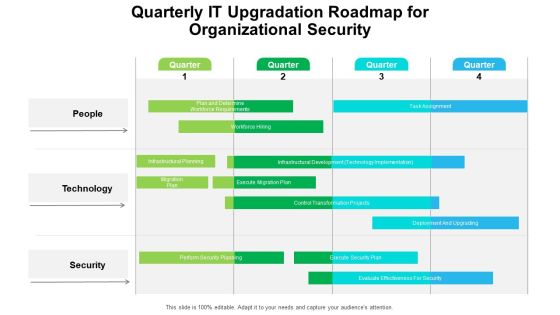
Quarterly IT Upgradation Roadmap For Organizational Security Professional
Presenting our innovatively structured quarterly it upgradation roadmap for organizational security professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
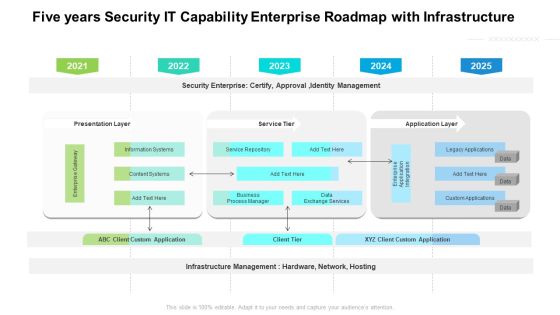
Five Years Security IT Capability Enterprise Roadmap With Infrastructure Guidelines
Presenting our jaw dropping five years security it capability enterprise roadmap with infrastructure guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Half Yearly Security IT Capability Enterprise Roadmap With Infrastructure Background
Presenting our jaw dropping half yearly security it capability enterprise roadmap with infrastructure background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Six Months Security IT Capability Enterprise Roadmap With Infrastructure Icons
Presenting our jaw dropping six months security it capability enterprise roadmap with infrastructure icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Three Months Security IT Capability Enterprise Roadmap With Infrastructure Clipart
Presenting our jaw dropping three months security it capability enterprise roadmap with infrastructure clipart. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Three Types Of Home Security Coverage Demonstration PDF
This slide shows types of coverage in home insurance. It includes dwelling, contents and personal liability. Showcasing this set of slides titled Three Types Of Home Security Coverage Demonstration PDF. The topics addressed in these templates are Contents Coverage, Dwelling Coverage, Personal Liability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Access Regulations Technology Five Years Roadmap With Security Solution Inspiration
Presenting our innovatively structured access regulations technology five years roadmap with security solution inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
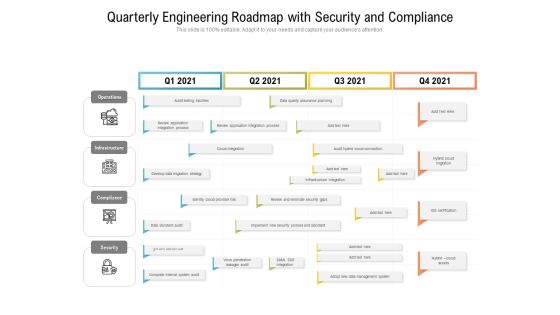
Quarterly Engineering Roadmap With Security And Compliance Template
Presenting our innovatively structured quarterly engineering roadmap with security and compliance template Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
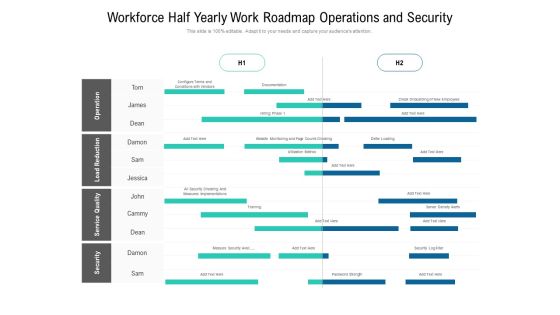
Workforce Half Yearly Work Roadmap Operations And Security Ideas
Presenting our innovatively structured workforce half yearly work roadmap operations and security ideas Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cloud Computing Security Half Yearly Roadmap With Deployment Plan Guidelines
Presenting our innovatively structured cloud computing security half yearly roadmap with deployment plan guidelines Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Strategic Process Management Half Yearly Timeline Rules
Presenting our innovatively structured cyber security strategic process management half yearly timeline rules Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
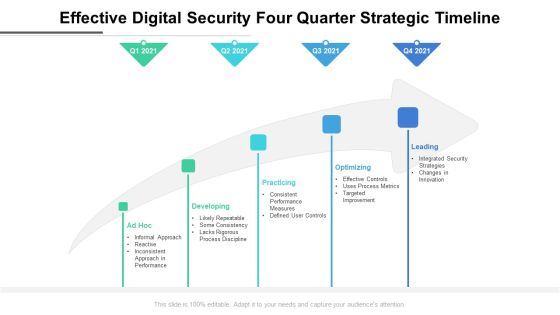
Effective Digital Security Four Quarter Strategic Timeline Elements
Presenting our innovatively structured effective digital security four quarter strategic timeline elements Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Blockchain Security Management Technology Working Flowchart Download PDF
This slide illustrates the working model of blockchain technology which is used to track and manage transaction in a business network. Process is divides into seven major steps. Persuade your audience using this Blockchain Security Management Technology Working Flowchart Download PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Completion, Cryptocurrency, Blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
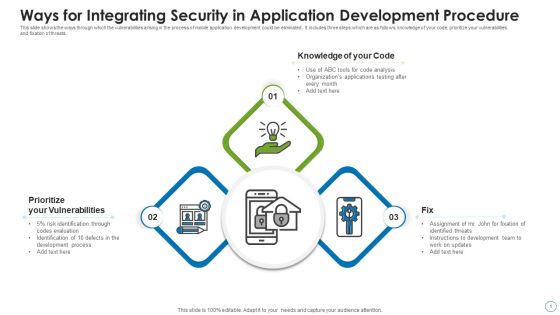
Ways For Integrating Security In Application Development Procedure Structure PDF
This slide shows the ways through which the vulnerabilities arising in the process of mobile application development could be eliminated. It includes three steps which are as follows knowledge of your code, prioritize your vulnerabilities and fixation of threats. Persuade your audience using this ways for integrating security in application development procedure structure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including prioritize your vulnerabilities, knowledge of your code, fix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Security Management 4 Step Workflow Icons PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Persuade your audience using this Business Security Management 4 Step Workflow Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Treat, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Year IT Upgradation Roadmap For Organizational Security Rules
Presenting the five year it upgradation roadmap for organizational security rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
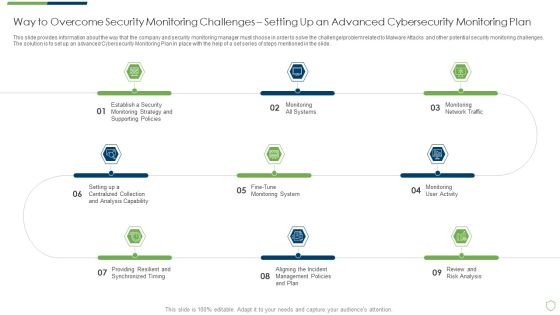
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
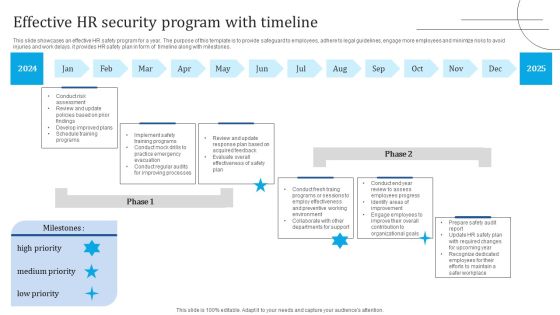
Effective HR Security Program With Timeline Portrait PDF
This slide showcases an effective HR safety program for a year. The purpose of this template is to provide safeguard to employees, adhere to legal guidelines, engage more employees and minimize risks to avoid injuries and work delays. it provides HR safety plan in form of timeline along with milestones. Showcasing this set of slides titled Effective HR Security Program With Timeline Portrait PDF. The topics addressed in these templates are Implement Safety Training Programs, Develop Improved Plans, Review Update. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

HR Security Training And Wellbeing KPI Dashboard Professional PDF
This slide showcases dashboard for HR safety training and wellbeing. This template aims to improve employee working efficiency and enhance working conditions to foster their working efficiency. It provides details regarding incidents reported, training programs implemented to reduce number of incidents, cost of providing training and level of employee satisfaction with training. Showcasing this set of slides titled HR Security Training And Wellbeing KPI Dashboard Professional PDF. The topics addressed in these templates are Severity, Injury Consequence, Employee Satisfaction Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Access Regulations Technology Half Yearly Roadmap With Security Solution Guidelines
Presenting the access regulations technology half yearly roadmap with security solution guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
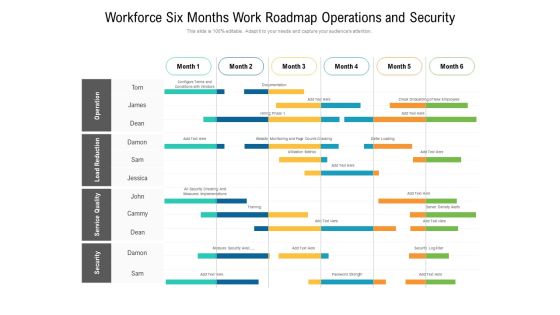
Workforce Six Months Work Roadmap Operations And Security Elements
Presenting the workforce six months work roadmap operations and security elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
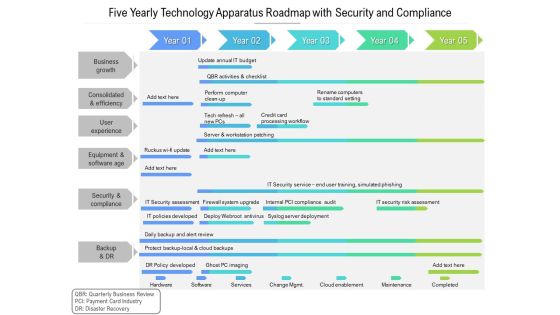
Five Yearly Technology Apparatus Roadmap With Security And Compliance Template
Presenting the five yearly technology apparatus roadmap with security and compliance template. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
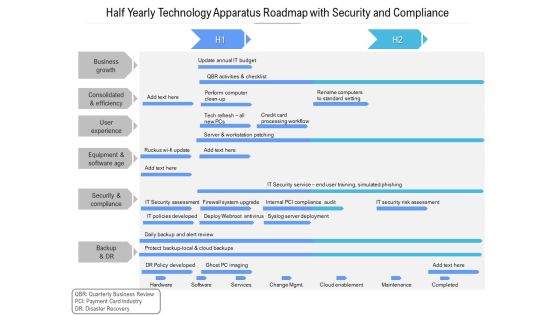
Half Yearly Technology Apparatus Roadmap With Security And Compliance Download
Presenting the half yearly technology apparatus roadmap with security and compliance download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Quarterly Technology Apparatus Roadmap With Security And Compliance Rules
Presenting the quarterly technology apparatus roadmap with security and compliance rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
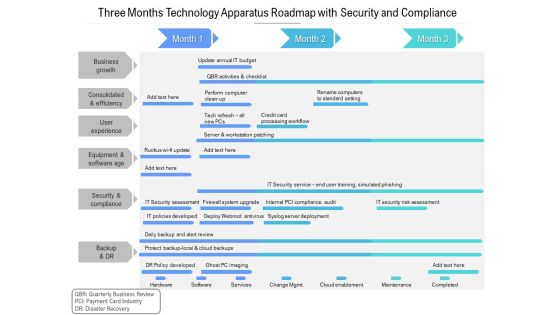
Three Months Technology Apparatus Roadmap With Security And Compliance Designs
Presenting the three months technology apparatus roadmap with security and compliance designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Plan Quarterly Roadmap With Multiple Phases Download
Presenting the cloud computing security plan quarterly roadmap with multiple phases download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Six Months Roadmap With Deployment Plan Themes
Presenting the cloud computing security six months roadmap with deployment plan themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
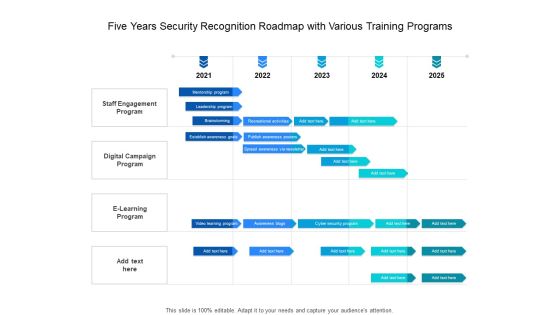
Five Years Security Recognition Roadmap With Various Training Programs Slides
Presenting the five years security recognition roadmap with various training programs slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
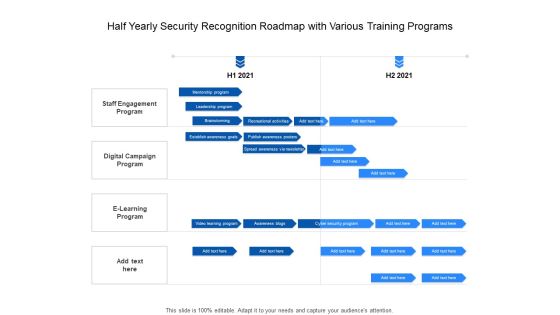
Half Yearly Security Recognition Roadmap With Various Training Programs Themes
Presenting the half yearly security recognition roadmap with various training programs themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
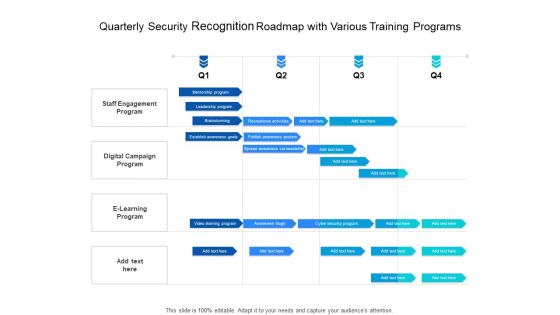
Quarterly Security Recognition Roadmap With Various Training Programs Download
Presenting the quarterly security recognition roadmap with various training programs download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Security Recognition Roadmap With Various Training Programs Summary
Presenting the six months security recognition roadmap with various training programs summary. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Security Recognition Roadmap With Various Training Programs Elements
Presenting the three months security recognition roadmap with various training programs elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Security Strategic Process Management Three Months Timeline Introduction
Presenting the cyber security strategic process management three months timeline introduction. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Agenda For Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Sample PDF
Presenting agenda for cyber security and phishing awareness training hacking prevention awareness training for it security sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like safeguard, integrity, cybersecurity, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Information Technology Management Ppt Images
This is a business information technology management ppt images. This is a five stage process. The stages in this process are bpms, applications, communications, information security, infrastructure and operations.

Cybersecurity Initiatives Ppt PowerPoint Presentation Outline Information
This is a cybersecurity initiatives ppt powerpoint presentation outline information. This is a nine stage process. The stages in this process are risk assessments, training and awareness, strategy, operationalizing cyber security, regulatory and legislative compliance.

Information Management Safety Illustration Ppt Slides
This is a information management safety illustration ppt slides. This is a three stage process. The stages in this process are identify, analyze, process.
Information Management Process Control Ppt Slides
This is a information management process control ppt slide. This is a four stage process. The stages in this process are process improvement, facilities and safety, customer service, documents and records.

Secure Internet Access Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Business PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Technology PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Use our Internet PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download and present our Computer PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges.Use these PowerPoint slides for presentations relating to The data is secure, security, business, technology, internet, computer. The prominent colors used in the PowerPoint template are Black, Gray, Yellow. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our internet PowerPoint templates and PPT Slides are designed by a team of presentation professionals. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. Customers tell us our business PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. People tell us our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses.

Information Mapping Process Ppt PowerPoint Presentation Summary Microsoft Cpb
This is a information mapping process ppt powerpoint presentation summary microsoft cpb. This is a four stage process. The stages in this process are information mapping process.

Elements Of IT Security Disaster Recovery Planning Ppt Icon Rules PDF
This slide depicts the disaster recovery plan in the network security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a elements of information technology security disaster recovery planning ppt outline background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business, security, operations, business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Assessment Matrix Of IT Risks Ppt Slides Visual Aids PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative information technology security assessment matrix of it risks ppt outline objects pdf bundle. Topics like assessment matrix of it risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
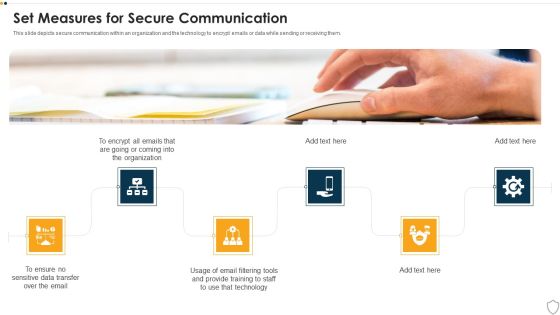
IT Security Set Measures For Secure Communication Ppt Infographic Template Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a it security set measures for secure communication ppt infographic template background designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, training, organization, data transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
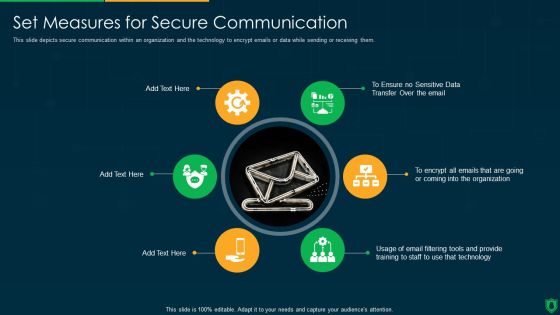
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
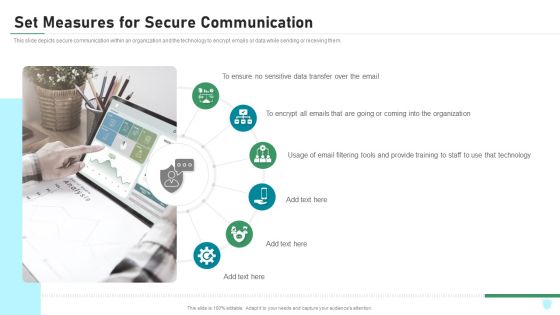
Set Measures For Secure Communication IT Security IT Ppt Styles Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting set measures for secure communication it security it ppt styles background designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data transfer, organization, technology, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Automation Icon To Improve Cyber Security Ppt Layouts Format Ideas PDF
Presenting Automation Icon To Improve Cyber Security Ppt Layouts Format Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Automation, Icon To Improve, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.
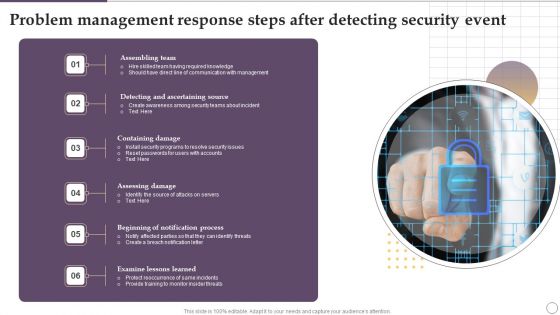
Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF
Presenting Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Assembling Team, Containing Damage, Assessing Damage, Examine Lessons Learned. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.
Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF.

Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
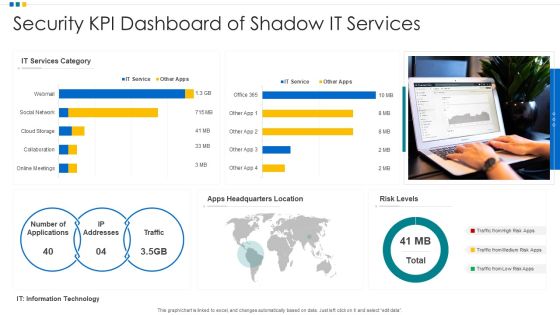
Security KPI Dashboard Of Shadow It Services Ppt Ideas Deck PDF
Pitch your topic with ease and precision using this Security KPI Dashboard Of Shadow It Services Ppt Ideas Deck PDF. This layout presents information on Security KPI Dashboard, Shadow It Services, Risk Levels. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

3 Stage Plan Icon To Improve Cyber Security Measures Ppt Gallery Diagrams PDF
Presenting 3 Stage Plan Icon To Improve Cyber Security Measures Ppt Gallery Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including 3 Stage Plan, Icon To Improve, Cyber Security Measures. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
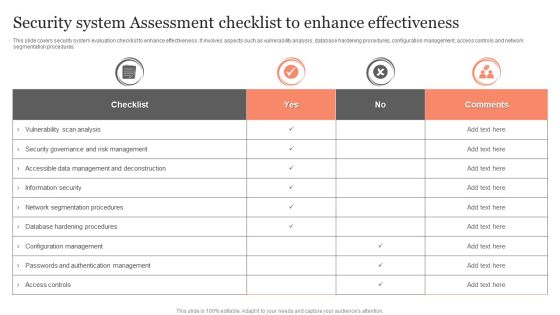
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Collaboration Plan Key Activities Information PDF
This slide presents a schedule timeline for tracking and monitoring key activities in order to successful completion of project. Its key tasks includes combined event action plan, short term security generation, competitive intelligence processes, branding, linking contacts in datasets, etc. Showcasing this set of slides titled Business Collaboration Plan Key Activities Information PDF. The topics addressed in these templates are Branding, Acquisition Positioning, Partners Communication, Short Term Security Generation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Person Using Smart Phone With Security Protection Ppt Portfolio Templates PDF
Presenting person using smart phone with security protection ppt portfolio templates pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including person using smart phone with security protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Dispose Data And Equipment Properly Ppt Icon Example PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information technology security dispose data and equipment properly ppt outline layouts pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF
This slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up. Presenting Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Problem Detection, Define, Investigate, Identify Resolutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF
This slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Determine Strategies, Risk Mitigation, Engagement Incident. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Management Matrix For IT Risk Control Strategies Security Ppt Professional Show PDF
This slide shows the risk management matrix for information technology security which covers the business workflow and technical systems with IT risks and threats such as software security, business controls, control risk modelling, penetration testing, attack modelling, etc. Pitch your topic with ease and precision using this Risk Management Matrix For IT Risk Control Strategies Security Ppt Professional Show PDF. This layout presents information on Corporate Workflow, Technical Systems, Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF
The following slide outlines the key dimensions of managed security service such as security information and event management, online staff augmentation, network security architecture and threat detection and alerts. Pitch your topic with ease and precision using this Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF. This layout presents information on Security Information, Event Management, Staff Augmentation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Administration In Organization Impact Analysis For Effective Threat Management Securing Rules PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative cyber security administration in organization impact analysis for effective threat management securing rules pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Information Protection Structural Framework Summary PDF
This slide covers business information security structural framework which includes chief information security officer with guidelines for control process.Showcasing this set of slides titled Business Information Protection Structural Framework Summary PDF. The topics addressed in these templates are Information Database, Classification Policy, Architecture Repository. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Privacy Vector Icon Ppt PowerPoint Presentation File Graphic Images
Presenting this set of slides with name information privacy vector icon ppt powerpoint presentation file graphic images. This is a one stage process. The stage in this process is information privacy vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Selecting Secured Threat Management Software Introduction PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management selecting secured threat management software introduction pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF
The following slide depicts some key trends in cyber threats happening across the globe. It includes some facts and figures related to the malware attack, data breach records, annual losses etc. Presenting Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Malware Attack, Business Fall, Data Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For IT Professional Data Certification Program Security Icons PDF
Presenting Table Of Contents For IT Professional Data Certification Program Security Icons PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Certified Information Systems, Security Professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
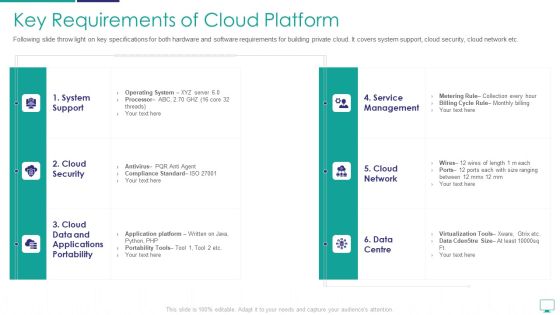
Key Requirements Of Cloud Platform Information PDF
Following slide throw light on key specifications for both hardware and software requirements for building private cloud. It covers system support, cloud security, cloud network etc. Deliver an awe inspiring pitch with this creative key requirements of cloud platform information pdf bundle. Topics like operating system, application platform, compliance standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Compliance Procedure Checklist Icons PDF
This slide presents information technology checklist, helpful in defining key tasks to be accomplished for successful completion of compliance process and management. It includes Access and identity control, incident response, disaster recovery, data loss prevention and protection against malware Showcasing this set of slides titled Information Technology Compliance Procedure Checklist Icons PDF. The topics addressed in these templates are Key Elements, Activities Accomplished, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizational Disaster Management Risk Checklist Information PDF
This slide depicts organizational disaster management response checklist that benefits organization in making preparations for employee safety illustrating safety checklist, employee management etc. Showcasing this set of slides titled organizational disaster management risk checklist information pdf. The topics addressed in these templates are prioritizing response checklist, employee management checklist, safety checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Accounting Actual Business Analysis Method Ppt Show Information PDF
Deliver an awe inspiring pitch with this creative accounting actual business analysis method ppt show information pdf bundle. Topics like inventory, investment, securities, sale, equipment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
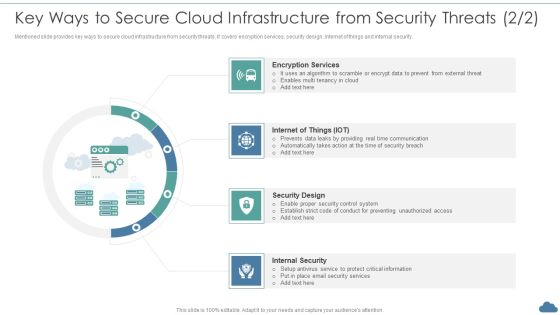
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Information Privacy It Diagrams PDF
This is a agenda for information privacy it diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for information privacy it. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Information Protection Management Icon Clipart PDF
Persuade your audience using this Organizational Information Protection Management Icon Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Organizational Information Protection, Management Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Cognitive Sensor Network Information PDF
Find a pre designed and impeccable Agenda For Cognitive Sensor Network Information PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
