AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Information Security Ppt
Information Security Ppt

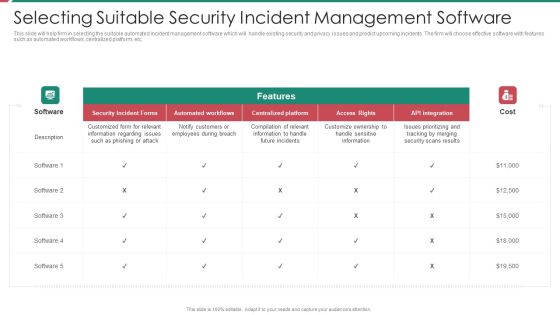
Organizational Security Solutions Selecting Suitable Security Incident Management Software Pictures PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative organizational security solutions selecting suitable security incident management software pictures pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security And Process Integration Selecting Suitable Security Incident Management Software Brochure PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security and process integration selecting suitable security incident management software brochure pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
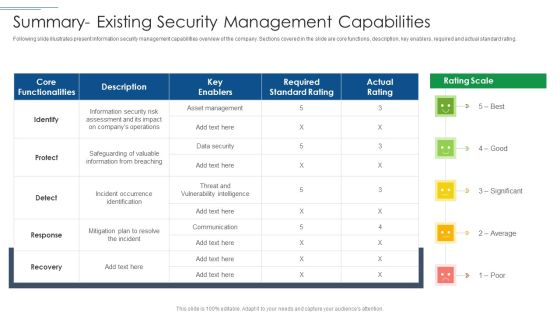
IT Security Risk Management Approach Introduction Summary Existing Security Management Capabilities Topics PDF
Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Required Standard Rating, Asset Management, Protect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Get a simple yet stunning designed CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit CYBER Security Breache Response Strategy Cyber Security Crisis Management Action Plan Timeline Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Automation Framework Criteria To Automate Security Analysis And Response Sample PDF
This slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Security Automation Framework Criteria To Automate Security Analysis And Response Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF.

Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF

Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF
This slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Explore a selection of the finest Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF today and make your presentation stand out from the rest.

CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.

Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Automation To Analyze And Mitigate Cyberthreats Criteria To Automate Security Brochure PDF
This slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats.Slidegeeks is here to make your presentations a breeze with Security Automation To Analyze And Mitigate Cyberthreats Criteria To Automate Security Brochure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software hardware installation, employee awareness sessions, etc.This is a IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking And Monitoring, Security Awareness, Installation Suggested. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment And Management Matrix Rules PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment And Management Matrix Rules PDF from Slidegeeks and deliver a wonderful presentation.

IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Security Functioning Centre Selecting Suitable Security Incident Management Software Introduction PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security functioning centre selecting suitable security incident management software introduction pdf bundle. Topics like prioritizing, customers, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Present Security Management Capabilities Of The Firm Template PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan present security management capabilities of the firm template pdf. Use them to share invaluable insights on actual standard rating, required standard rating, key enablers, description, core functions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CYBER Security Breache Response Strategy User Awareness Training Program Prevent Cyber Security Incidents Demonstration PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find a pre designed and impeccable CYBER Security Breache Response Strategy User Awareness Training Program Prevent Cyber Security Incidents Demonstration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
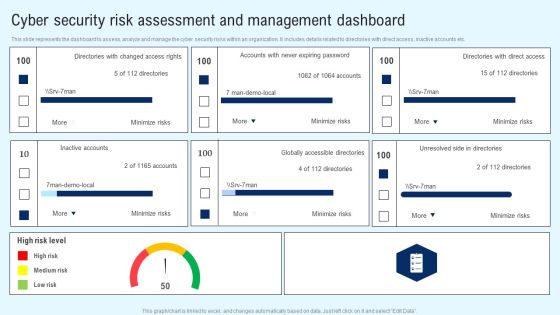
Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
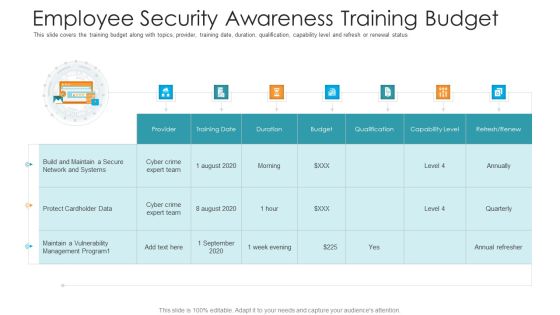
Employee Security Awareness Training Budget Hacking Prevention Awareness Training For IT Security Guidelines PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this employee security awareness training budget hacking prevention awareness training for it security guidelines pdf. Use them to share invaluable insights on training, maintain, management, budget, capability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
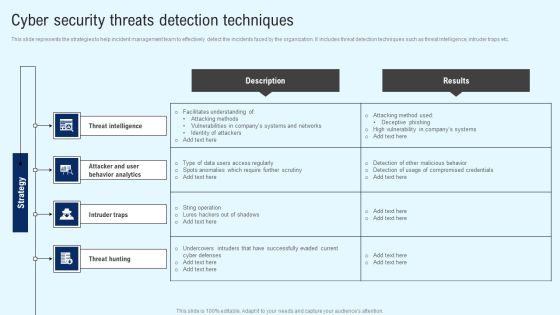
Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.
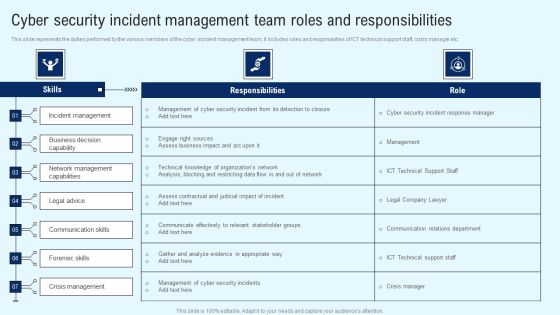
Implementing Cyber Security Incident Cyber Security Incident Team Roles Summary PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cyber Security Incident Cyber Security Incident Team Roles Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cyber Security Incident Cyber Security Incident Team Roles Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
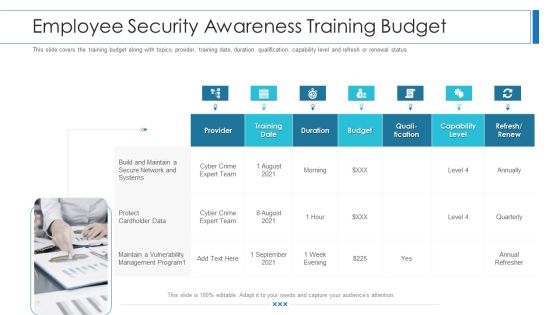
Workforce Security Realization Coaching Plan Employee Security Awareness Training Budget Summary PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan employee security awareness training budget summary pdf bundle. Topics like training date, duration, budget, capability level, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Cyber Threat Landscape In Computer Security Ideas PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this desktop security management cyber threat landscape in computer security ideas pdf. Use them to share invaluable insights on business disruption, strategic plans, financial, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Uniformed Security Next Steps In The Security Guard Services Proposal Rules PDF
Presenting uniformed security next steps in the security guard services proposal rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like next steps. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Are you searching for a Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF from Slidegeeks today.

Security Awareness Program Checklist Hacking Prevention Awareness Training For IT Security Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting security awareness program checklist hacking prevention awareness training for it security background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating the security awareness program, implementing security awareness, sustaining security awareness, documenting the security awareness program. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Want to ace your presentation in front of a live audience Our CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting workforce security realization coaching plan security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementing security awareness, sustaining security awareness, security awareness program. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
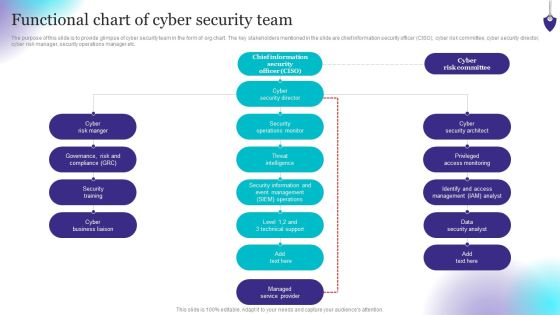
Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF today and make your presentation stand out from the rest.

Workforce Security Realization Coaching Plan Security Awareness New Strategies For Learning Clipart PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Presenting workforce security realization coaching plan security awareness new strategies for learning clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security awareness new strategies for learning. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness New Strategies For Learning Hacking Prevention Awareness Training For IT Security Elements PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Presenting security awareness new strategies for learning hacking prevention awareness training for it security elements pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like targeted, training, continuous, management, methodologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. This is a Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Provide Safe Environment, Safeguard Environment, Campus Patrolling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Create an editable CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
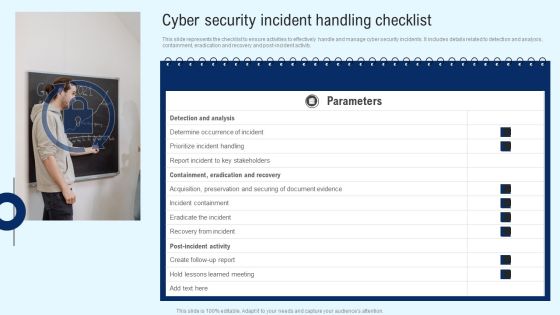
Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. This Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF.

IT Security Automation Systems Guide Determine Ideal Tasks For Security Automation Designs PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Want to ace your presentation in front of a live audience Our IT Security Automation Systems Guide Determine Ideal Tasks For Security Automation Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Organizing Security Awareness Strategies We Will Implement To Make Security Awareness Diagrams PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizing Security Awareness Strategies We Will Implement To Make Security Awareness Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizing Security Awareness Strategies We Will Implement To Make Security Awareness Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Deploying Cyber Security Incident Response Administration Strategies To Analyze Cyber Security Incidents Template PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Present like a pro with Deploying Cyber Security Incident Response Administration Strategies To Analyze Cyber Security Incidents Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
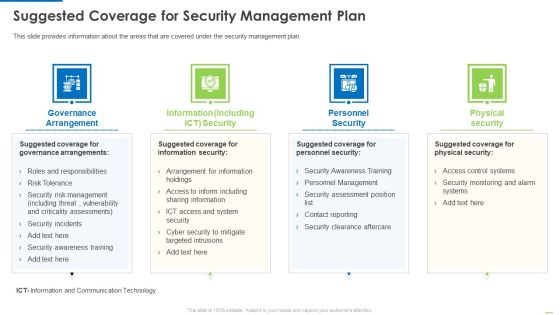
Suggested Coverage For Security Management Plan Background PDF
Presenting suggested coverage for security management plan background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like governance arrangement, information including, personnel security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Keyways To Secure Cloud Infrastructure From Security Threats Formats PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a keyways to secure cloud infrastructure from security threats formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encryption services, internet of things, security design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

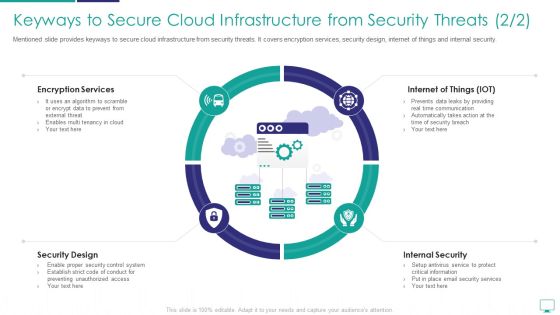
Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Retail And Shopping Complex Security Services Background PDF
This is a Security Agency Business Profile Retail And Shopping Complex Security Services Background PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Security, Shopping Complex Security, Theatre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Addressing Different Security Priorities At Organization Background PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of fraud or threat protection, physical security and business continuity. This is a developing firm security strategy plan addressing different security priorities at organization background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fraud or threat protection, physical security, business continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
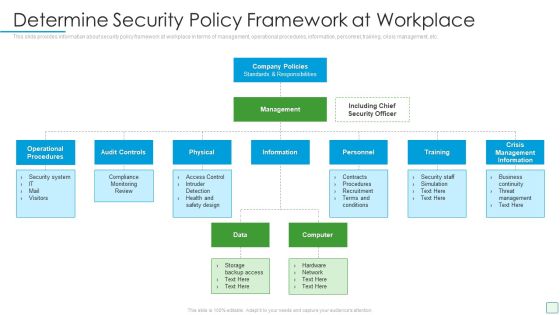
Developing Firm Security Strategy Plan Determine Security Policy Framework At Workplace Template PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Presenting developing firm security strategy plan determine security policy framework at workplace template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like operational procedures, audit controls, physical, training, crisis management information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.This is a Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Security, Internet Security, Endpoint Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. This is a IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Orchestrating Network Security, Integrating Network, Security Policy Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF
This slide highlights the security company services for retail outlets, mall and shopping complex and theatre security which includes the key role and responsibility of security guard. This is a Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Security, Shopping Complex Security, Theatre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. This is a IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, IDPS, SIEM, Privileged Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Introducing Security At Workplace To Ensure Assets Safety Introduction PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Presenting developing firm security strategy plan introducing security at workplace to ensure assets safety introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security policy, organizational strategy, security mission statement, strategic security objectives. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
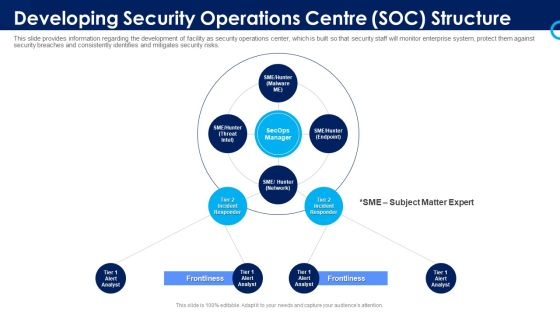
Organizational Security Solutions Developing Security Operations Centre SOC Structure Introduction PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting organizational security solutions developing security operations centre soc structure introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
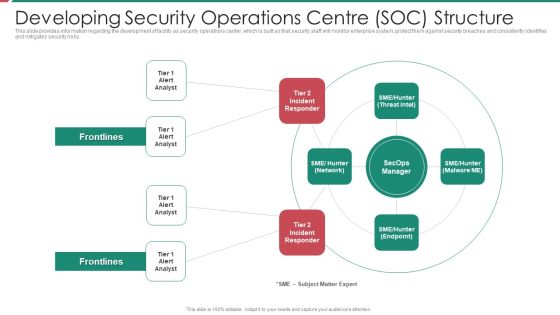
Security And Process Integration Developing Security Operations Centre SOC Structure Inspiration PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting security and process integration developing security operations centre soc structure inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Common Methods Used To Threaten Computer Security Template PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a desktop security management common methods used to threaten computer security template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, services, network, database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
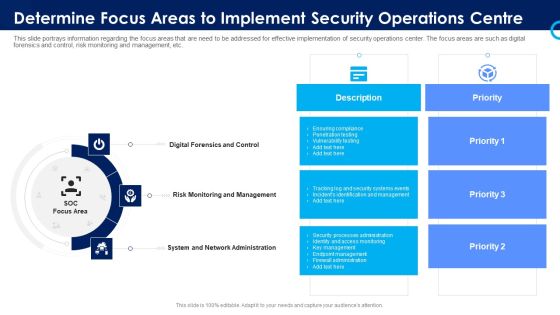
Organizational Security Solutions Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a organizational security solutions determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Risk Management Assessment Checklist Demonstration PDF
This slide shows a security risk management assessment checklist with multiple categories.Presenting techniques and strategies to reduce security management risks security risk management assessment checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, responding to security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Uniformed Security Proposal For Security Guard Services Table Of Content Inspiration PDF
This is a uniformed security proposal for security guard services table of content inspiration pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan, testimonials, investment, services, equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Uniformed Security 30 60 90 Days Plan For Security Guard Services Proposal Formats PDF
This is a uniformed security 30 60 90 days plan for security guard services proposal formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Uniformed Security Testimonials In The Security Guard Services Proposal Communication Formats PDF
This is a uniformed security testimonials in the security guard services proposal communication formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like testimonials. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
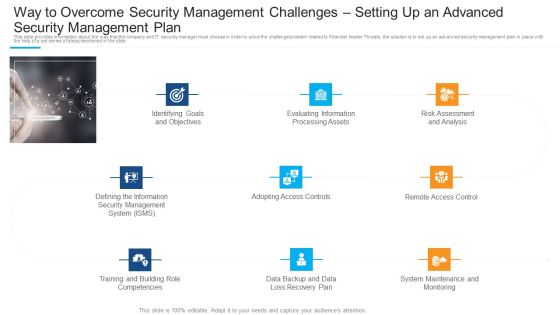
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Pictures PDF
Presenting way to overcome security management challenges setting up an advanced security management plan pictures pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. This is a IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Failed Human Insights, Right Time Automation, High Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Training Roadmap Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a security awareness training roadmap hacking prevention awareness training for it security template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, physical security, privacy threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance.This is a Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Access Control, Centre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Workforce Security Realization Coaching Plan Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a workforce security realization coaching plan security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps Portrait PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Adopting Access Controls. This is a techniques and strategies to reduce security management risks security management plan steps portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like suggested coverage, security risk management, estimated security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.This is a Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Business Continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. This is a IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Investigation, Findings, Remediation, Visualization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Addressing Physical Security At Workplace Ideas PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Presenting developing firm security strategy plan addressing physical security at workplace ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like workplace surveillance, employee monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security End User Education Background PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a desktop security management elements of computer security end user education background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, opportunities, security, organization, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting enhanced protection corporate event administration role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Uniformed Security Testimonials In The Security Guard Services Proposal Teamwork Clipart PDF
Presenting uniformed security testimonials in the security guard services proposal teamwork clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like testimonials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Enabling Data Security Risk Management Action Plan Download PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. This is a project security administration it enabling data security risk management action plan download pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential risk, risk level, action, responsible person, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Retail And Shopping Complex Security Services Icons PDF
This slide highlights the security company services for retail outlets, mall and shopping complex and theatre security which includes the key role and responsibility of security guard. Presenting Manpower Corporate Security Business Profile Retail And Shopping Complex Security Services Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Retail Security, Shopping Complex Security, Theatre Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Techniques And Strategies To Reduce Security Management Risks Security Detail System Maintenance And Monitoring Mockup PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. This is a techniques and strategies to reduce security management risks security detail system maintenance and monitoring mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perfective maintenance, corrective maintenance, perfective maintenance You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
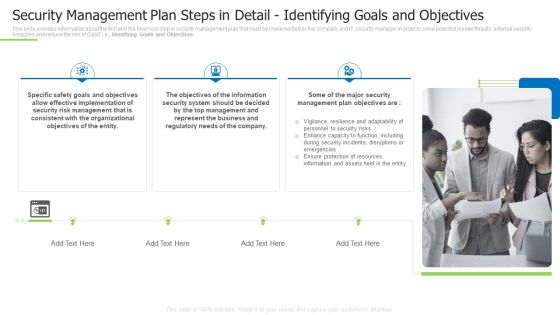
Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Inspiration PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a techniques and strategies to reduce security management risks security management plan steps in detail inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like effective implementation, consistent with the organizational, represent the business You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF
This slide highlights the security company services which includes CCTV, mobile app software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera.This is a Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking Solution, Display Solutions, Occupancy Sensor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment What Are The Downsides Of A Cloud Security Infographics PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches.This is a Cloud Security Assessment What Are The Downsides Of A Cloud Security Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Services Organizations, Company Employees, Monetary Losses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery.This is a Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, Access Controls, Data Masking You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Industries That Can Benefit From Cloud Security Topics PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds.This is a Cloud Security Assessment Industries That Can Benefit From Cloud Security Topics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automotive, Healthcare, Production You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. This is a IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Better Threat Detection, Faster Containment, Improve Productivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Where Is The Gap In Security Programs Hacking Prevention Awareness Training For IT Security Diagrams PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a where is the gap in security programs hacking prevention awareness training for it security diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Network Security Awareness Staff Learning Where Is The Gap In Security Programs Template PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a organizational network security awareness staff learning where is the gap in security programs template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, management, organizations, targeted training, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Facilities Rendered By Security Centre Implementation Clipart PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting project security administration it facilities rendered by security centre implementation clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Difference Between Cloud Security Solutions And Traditional IT Solutions Portrait PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses.Presenting Cloud Security Assessment Difference Between Cloud Security Solutions And Traditional IT Solutions Portrait PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Reduced Infrastructure, Resource Utilization, Diminished Opportunity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Precautions Need To Take In Cloud Security Elements PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service.This is a Cloud Security Assessment Precautions Need To Take In Cloud Security Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Computing Administrations, Service Provider, Managed Administrations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls.This is a Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security And Surveillance Company Profile Security Company Organization Chart Portrait PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. This is a Security And Surveillance Company Profile Security Company Organization Chart Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Raymond Michael, Executive President, Emerging Markets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Security Company Case Study Clipart PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. This is a Security Camera System Company Profile Security Company Case Study Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Integrated Solution, Value Delivered, Client Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Presenting IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Policy, Security Admin, Reputation Feeds. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Alerts Graphics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Presenting developing firm security strategy plan security incidents tracking dashboard alerts graphics pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like application whitelisting, patch applications, patch operating systems, restrict admin privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
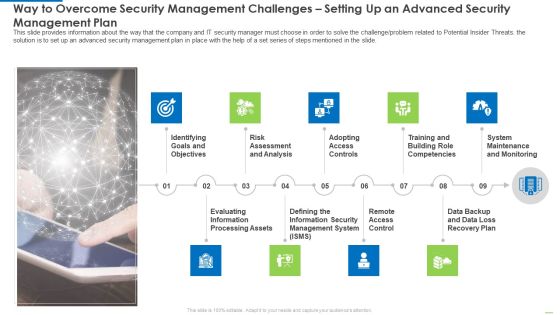
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Introduction PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment and analysis, adopting access controls, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
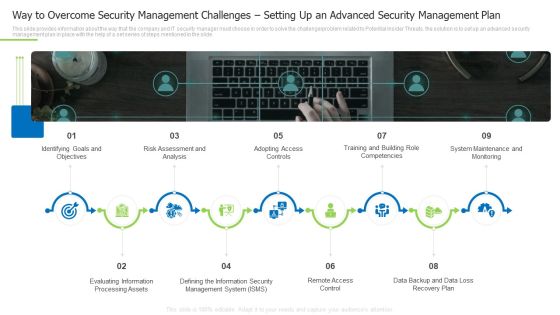
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Rules PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan rules pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
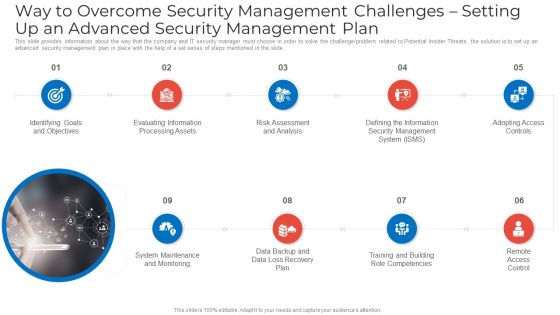
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Microsoft PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. Presenting way to overcome security management challenges setting up an advanced security management plan microsoft pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, risk assessment and analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
