Cyber Threat

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Types Of Threats In Desktop Security Management Themes PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting desktop security management types of threats in desktop security management themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like target systems, devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Types Of Threats In Data Security Ppt Layouts File Formats PDF
This slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a information security types of threats in data security ppt layouts file formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
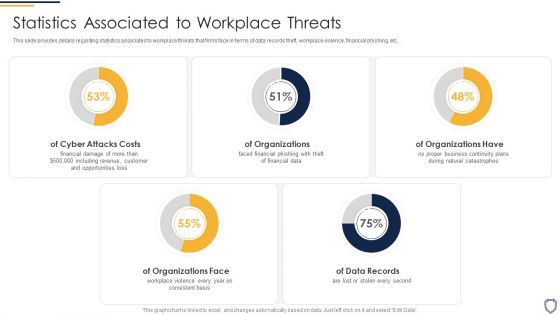
Corporate Security And Risk Management Statistics Associated To Workplace Threats Template PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. . Deliver an awe inspiring pitch with this creative corporate security and risk management statistics associated to workplace threats template pdf bundle. Topics like cyber attacks costs, organizations, organizations have, organizations face, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
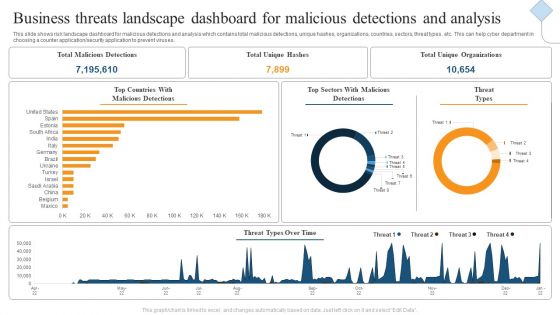
Business Threats Landscape Dashboard For Malicious Detections And Analysis Ppt Gallery Show PDF
This slide shows risk landscape dashboard for malicious detections and analysis which contains total malicious detections, unique hashes, organizations, countries, sectors, threat types, etc. This can help cyber department in choosing a counter application or security application to prevent viruses. Showcasing this set of slides titled Business Threats Landscape Dashboard For Malicious Detections And Analysis Ppt Gallery Show PDF. The topics addressed in these templates are Total Malicious Detections, Total Unique Hashes, Total Unique Organizations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF
This slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF bundle. Topics like Conference Meeting, Incident Information, Various Departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
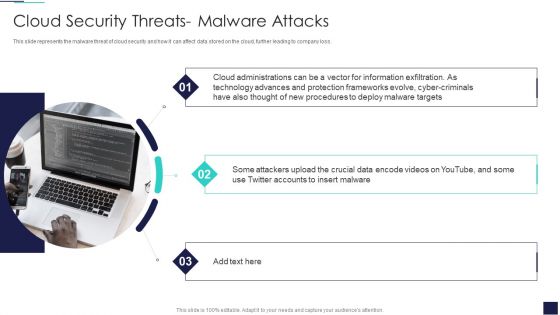
Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management For Organization Essential Assets Statistics Associated To Workplace Threats Structure PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Presenting risk management for organization essential assets statistics associated to workplace threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cyber attacks costs, data records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
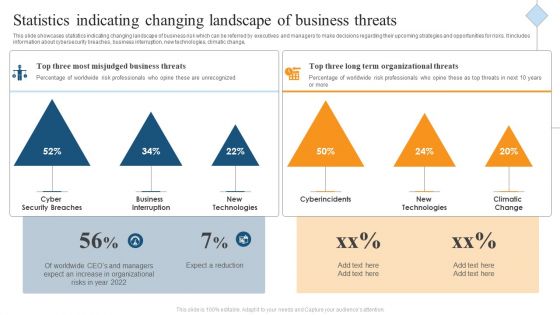
Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF
This slide showcases statistics indicating changing landscape of business risk which can be referred by executives and managers to make decisions regarding their upcoming strategies and opportunities for risks. It includes information about cybersecurity breaches, business interruption, new technologies, climatic change, Persuade your audience using this Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Breaches, Business Interruption, New Technologies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
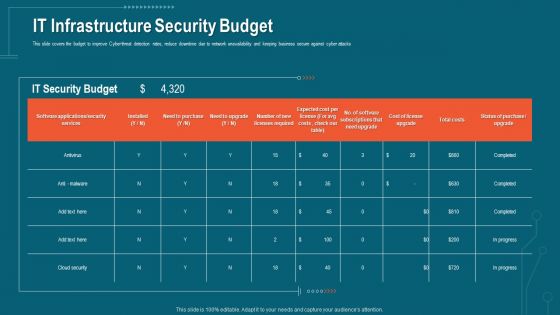
Companys Data Safety Recognition IT Infrastructure Security Budget Designs PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver and pitch your topic in the best possible manner with this companys data safety recognition it infrastructure security budget designs pdf. Use them to share invaluable insights on budget, cyber threat, business secure, software applications, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
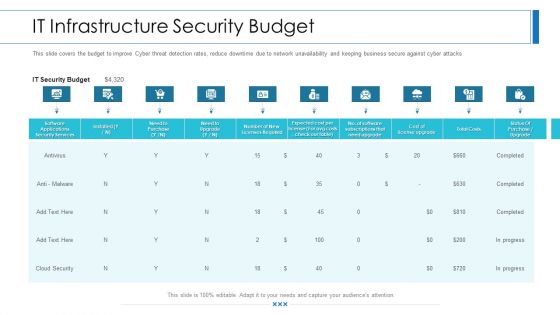
Workforce Security Realization Coaching Plan IT Infrastructure Security Budget Background PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan it infrastructure security budget background pdf bundle. Topics like software applications security services, business, it security budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
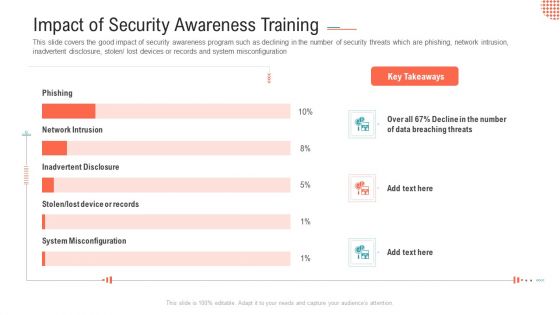
Impact Of Security Awareness Training Ppt Pictures Design Templates PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt pictures design templates pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
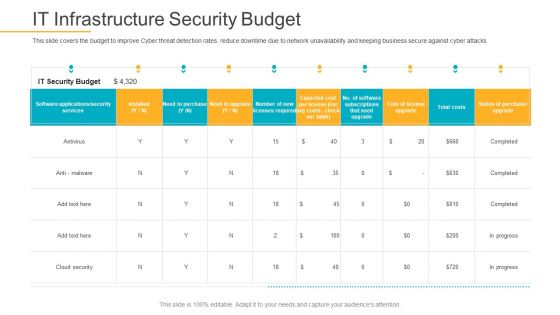
Data Breach Prevention Recognition IT Infrastructure Security Budget Rules PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition it infrastructure security budget rules pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Infrastructure Security Budget Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe inspiring pitch with this creative it infrastructure security budget hacking prevention awareness training for it security graphics pdf bundle. Topics like security, services, costs, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
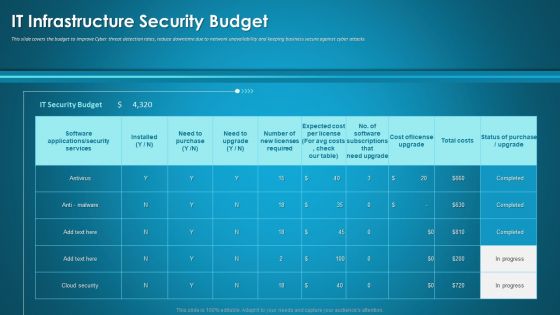
Organizational Network Security Awareness Staff Learning IT Infrastructure Security Budget Slides PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning it infrastructure security budget slides pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

It Infrastructure Security Budget Ppt Outline Mockup PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this it infrastructure security budget ppt outline mockup pdf. Use them to share invaluable insights on services, software, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

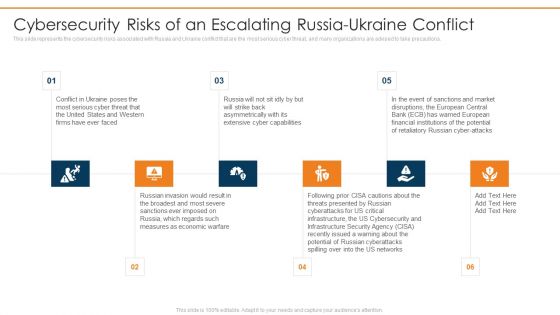
Ukraine Cyberwarfare Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Topics Pdf
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. This is a ukraine cyberwarfare cybersecurity risks of an escalating russia ukraine conflict topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conflict in ukraine poses the most serious cyber threat that the united states, russia will not sit idly by but will strike back asymmetrically with its extensive cyber capabilities, russian invasion would result in the broadest and most severe sanctions ever imposed on russia. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Risk Recognition Automation Security Intelligence Services Ppt Icon Infographics PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. This is a risk recognition automation security intelligence services ppt icon infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
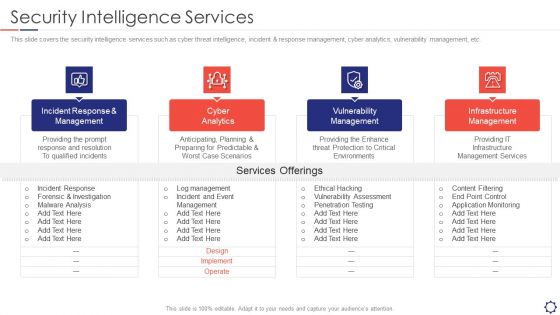
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
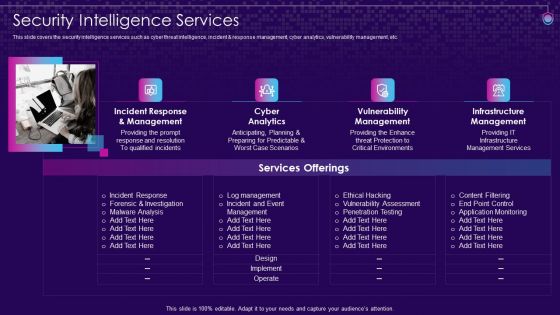
SIEM Services Security Intelligence Services Ppt Show Layouts PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem services security intelligence services ppt show layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management cyber, analytics vulnerability, management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Information And Event Management Strategies For Financial Audit And Compliance Security Intelligence Services Graphics PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. This is a security information and event management strategies for financial audit and compliance siem architecture topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
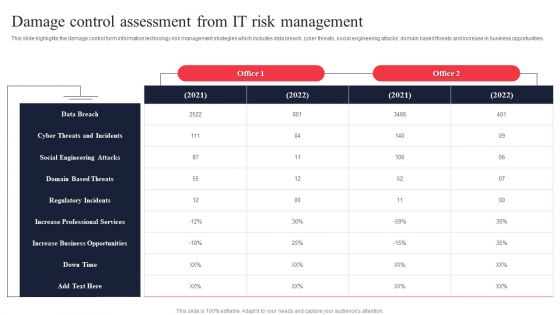
IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
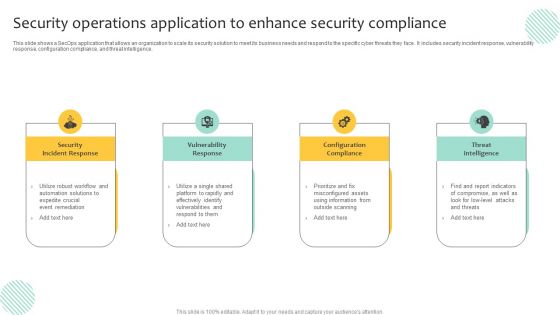
Security Operations Application To Enhance Security Compliance Rules PDF
This slide shows a SecOps application that allows an organization to scale its security solution to meet its business needs and respond to the specific cyber threats they face. It includes security incident response, vulnerability response, configuration compliance, and threat intelligence. Persuade your audience using this Security Operations Application To Enhance Security Compliance Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Configuration Compliance, Threat Intelligence, Vulnerability Response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
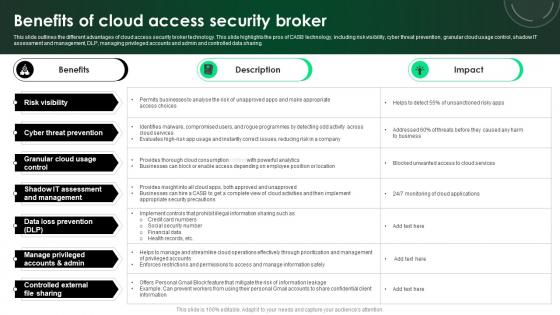
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
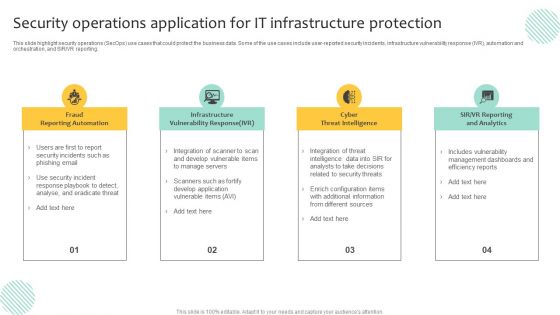
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Operations Certifications And Training Courses For IT Professionals Topics PDF
This slide exhibits training courses for security operations administrators to enhance their cyber threat management skills. It includes elements such as course, course outline, rating, pricing, frequency, and mode of training. Showcasing this set of slides titled Security Operations Certifications And Training Courses For IT Professionals Topics PDF. The topics addressed in these templates are Security Operations, Fundamental, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Management Plan Manage Playbook For Strategic Actions To Improve IT Performance Brochure Pdf
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Risk Management Plan Manage Playbook For Strategic Actions To Improve IT Performance Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
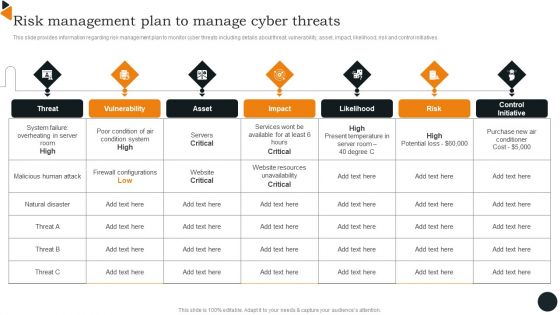
Chief Information Officers Guide On Technology Plan Risk Management Plan Introduction PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. This modern and well arranged Chief Information Officers Guide On Technology Plan Risk Management Plan Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Technology Transformation Seven Basic Goals Ppt PowerPoint Presentation Ideas Images PDF
Persuade your audience using this technology transformation seven basic goals ppt powerpoint presentation ideas images pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including safeguarding digital resources cyber threats, technology optimization to push faster and respond to changes, technology optimization more productive, secure, track and react to conditions real time, optimizing investment protection to reduce resources and administration, ensuring threats handled and fully complied security, build modern business plan grabbing new opportunities. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
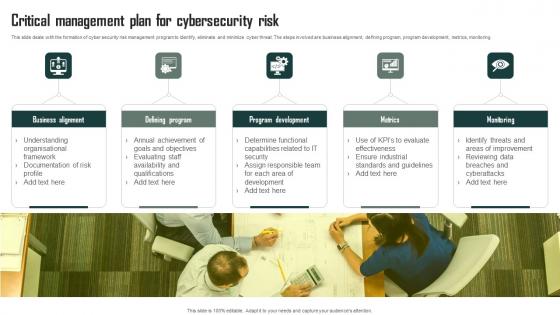
Critical Management Plan For Cybersecurity Risk Demonstration Pdf
This slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring Pitch your topic with ease and precision using this Critical Management Plan For Cybersecurity Risk Demonstration Pdf This layout presents information on Business Alignment, Defining Program, Program Development It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Data Wiper Spyware Attack Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Background PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions.This is a data wiper spyware attack cybersecurity risks of an escalating russia ukraine conflict background pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extensive cyber capabilities, russian invasion would, measures as economic warfare You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity ML Business Applications Sample Pdf
This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities. Pitch your topic with ease and precision using this Cybersecurity ML Business Applications Sample Pdf. This layout presents information on Email Monitoring, Machine Leaning, Detecting Malicious Entities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Risk Management For Organization Essential Assets Addressing Various Ways To Handle Icons PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting risk management for organization essential assets addressing various ways to handle icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management For Organization Essential Assets Addressing Various Ways To Handle Insider Graphics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a risk management for organization essential assets addressing various ways to handle insider graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, track baseline behavior networks and individuals, render least amount of privilege, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategy Of Proactive Security Process Ppt Presentation
This is a strategy of proactive security process ppt presentation. This is a three stage process. The stages in this process are environment scanning, pear networking, result, threat detection, incident response, cyber incident.
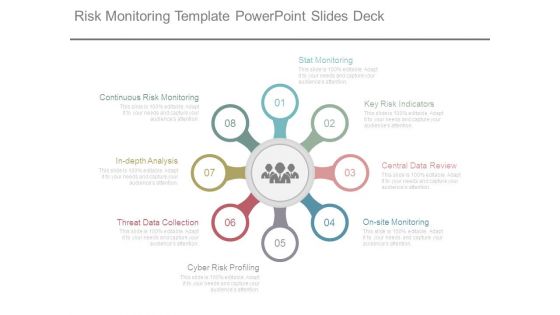
Risk Monitoring Template Powerpoint Slides Deck
This is a risk monitoring template powerpoint slides deck. This is a eight stage process. The stages in this process are stat monitoring, key risk indicators, central data review, on site monitoring, cyber risk profiling, threat data collection, in depth analysis, continuous risk monitoring.

Risk Management For Organization Essential Assets Ensuring Collaboration Among Various Slides PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting risk management for organization essential assets ensuring collaboration among various slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like procurement, finance, legal, public relations, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
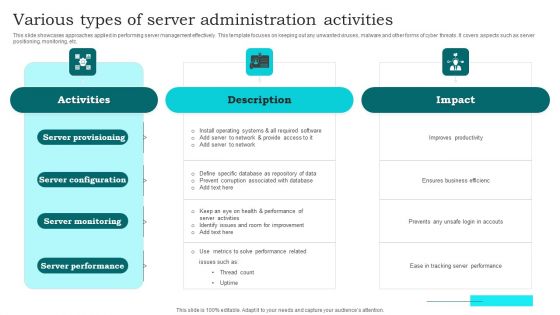
Various Types Of Server Administration Activities Clipart PDF
This slide showcases approaches applied in performing server management effectively. This template focuses on keeping out any unwanted viruses, malware and other forms of cyber threats. It covers aspects such as server positioning, monitoring, etc. Presenting Various Types Of Server Administration Activities Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Server Provisioning, Server Configuration, Server Monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
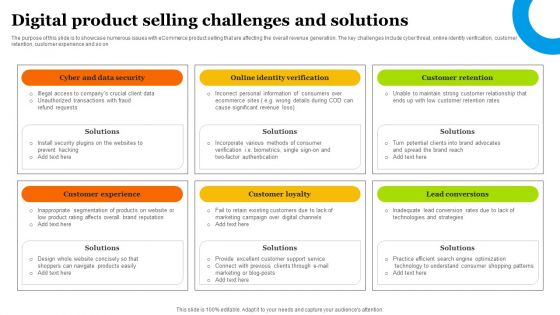
Digital Product Selling Challenges And Solutions Information PDF
The purpose of this slide is to showcase numerous issues with eCommerce product selling that are affecting the overall revenue generation. The key challenges include cyber threat, online identity verification, customer retention, customer experience and so on. Persuade your audience using this Digital Product Selling Challenges And Solutions Information PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Experience, Customer Loyalty, Lead Conversions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
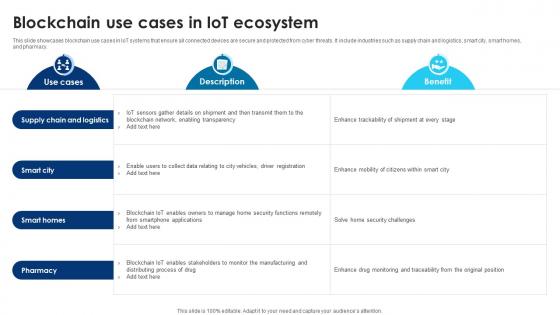
Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V
This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
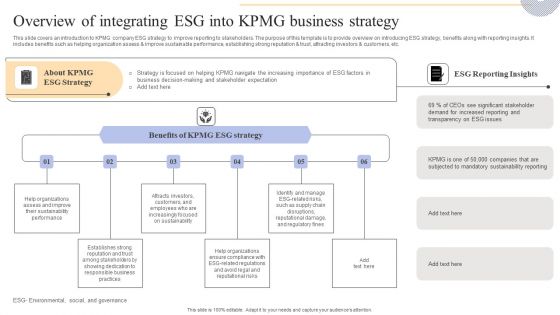
Overview Of Integrating Esg Into KPMG Business Strategy Background PDF
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. This Overview Of Integrating Esg Into KPMG Business Strategy Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Overview Of Integrating Esg Into KPMG Business Strategy Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Welcome to our selection of the Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.

Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide
This slide discusses the importance and driver of software development security. The purpose of this slide is to explain the importance of security in software development and its key drivers, which are cyber threat defense, data privacy, regulatory adherence, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide a try. Our experts have put a lot of knowledge and effort into creating this impeccable Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V
The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
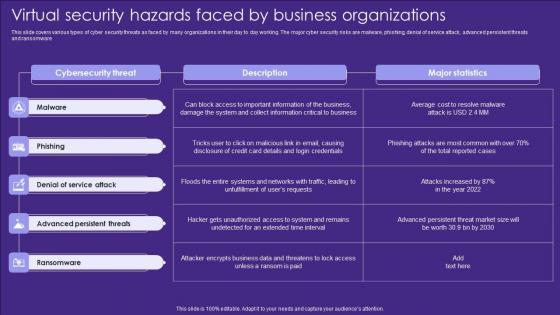
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home