Two Factor Authentication

Two Factor Authentication Example Of Ppt Presentation
This is a two factor authentication example of ppt presentation. This is a two stage process. The stages in this process are something you know, something you have.

Two Factor Authentication Icon For Cyber Threat Prevention Background PDF
Two Factor Authentication API Ppt PowerPoint Presentation Professional Templates Cpb
Presenting this set of slides with name two factor authentication api ppt powerpoint presentation professional templates cpb. This is an editable Powerpoint two stages graphic that deals with topics like two factor authentication api to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Two Factor Authentication Ppt PowerPoint Presentation Slides Diagrams Cpb
Presenting this set of slides with name two factor authentication ppt powerpoint presentation slides diagrams cpb. This is an editable Powerpoint four stages graphic that deals with topics like two factor authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Varieties Of Two Factor Authentication Method Cryptocurrency Management With Blockchain
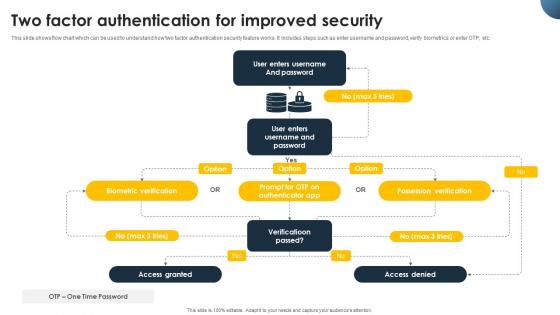
Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V today and make your presentation stand out from the rest
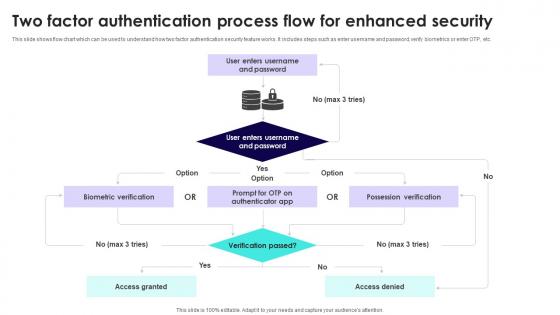
Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Are you searching for a Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V from Slidegeeks today.
Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb
Introducing our well designed Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Security App Two Factor Authentication. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
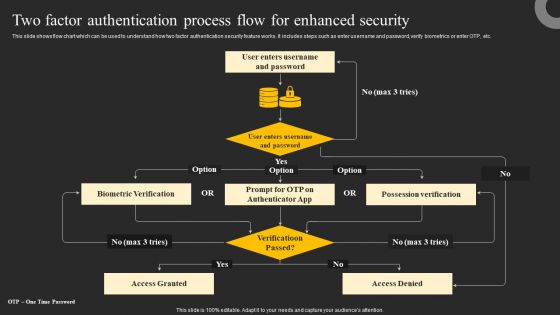
Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Explore a selection of the finest Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
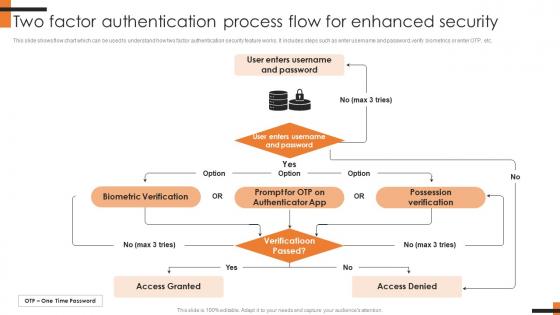
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Authentication Process Flow Of Verification Factors For User Profile Authentication Icon Portrait PDF
Persuade your audience using this authentication process flow of verification factors for user profile authentication icon portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authentication process flow of verification factors for user profile authentication icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Work Space Authentication Process Flow Of Verification Factors Icons PDF
Pitch your topic with ease and precision using this work space authentication process flow of verification factors icons pdf. This layout presents information on rust relationship, authentication, corporate data center. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Herzbergs Two Factor Theory Of Motivation Ppt PowerPoint Presentation Infographics Graphics Tutorials PDF
Presenting this set of slides with name herzbergs two factor theory of motivation ppt powerpoint presentation infographics graphics tutorials pdf. This is a two stage process. The stages in this process are poor hygiene factors result in decrease of employee job satisfaction, hygiene factors, achievement, recognition, the work itself, responsibility, advancement, growth, motivators, company policies, supervision, relationship with supervisor and peers, work conditions, salary, status, security, motivating factors result in increase of employee job satisfaction. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
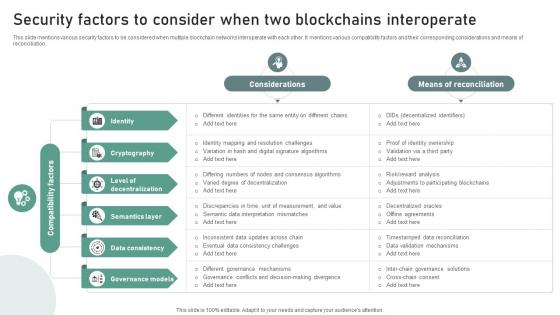
Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Create an editable Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Understanding Various Blockchain Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Want to ace your presentation in front of a live audience Our Understanding Various Blockchain Security Factors To Consider When Two Blockchains BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
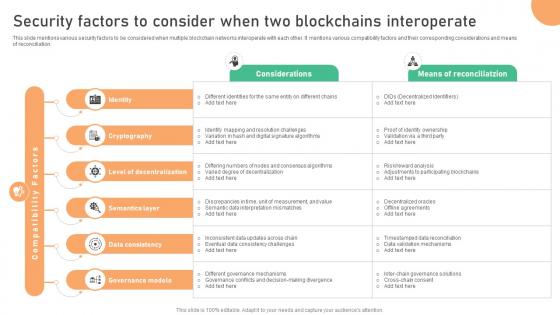
Seamless Integration The Power Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Seamless Integration The Power Security Factors To Consider When Two Blockchains BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

CRM Solutions Implementation Strategy Securing Our Data With CRM Structure PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.Deliver and pitch your topic in the best possible manner with this CRM Solutions Implementation Strategy Securing Our Data With CRM Structure PDF Use them to share invaluable insights on Factor Authentication, Communication Protection, Storage And Failover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Securing Our Data With CRM Designing And Deployment Ppt PowerPoint Presentation Icon Example File PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an awe inspiring pitch with this creative securing our data with crm designing and deployment ppt powerpoint presentation icon example file pdf bundle. Topics like crm data security, ip restriction, data storage and failover, communication protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
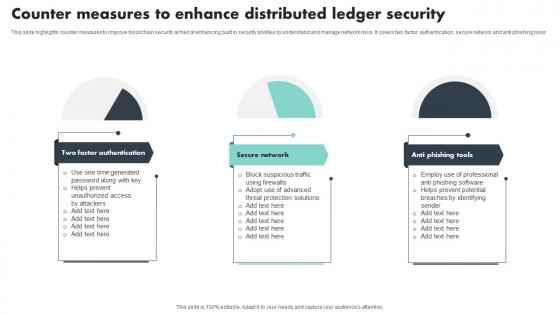
Counter Measures To Enhance Distributed Ledger Security Mockup Pdf
This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools Showcasing this set of slides titled Counter Measures To Enhance Distributed Ledger Security Mockup Pdf The topics addressed in these templates are Factor Authentication, Secure Network, Anti Phishing Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CRM Implementation Strategy Securing Our Data With CRM Summary PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a CRM Implementation Strategy Securing Our Data With CRM Summary PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Communication Protection, Restrict Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Sales CRM Cloud Solutions Deployment Securing Our Data With CRM Infographics PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a Sales CRM Cloud Solutions Deployment Securing Our Data With CRM Infographics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Storage And Failover, Communication Protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
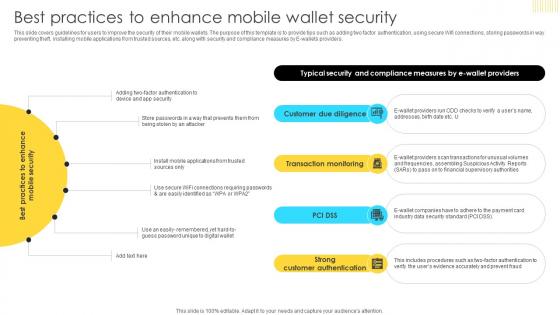
Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V
This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers. There are so many reasons you need a Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
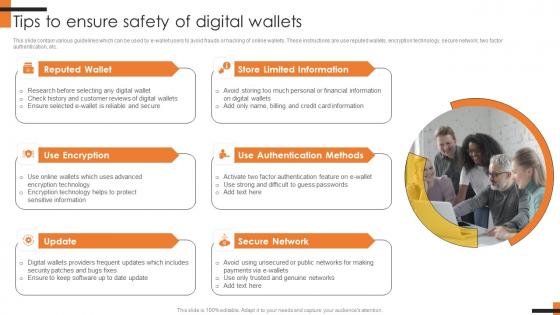
Tips To Ensure Safety Of Digital Wallets Comprehensive Smartphone Banking Information Pdf
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100Precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Tips To Ensure Safety Of Digital Wallets Comprehensive Smartphone Banking Information Pdf from Slidegeeks and deliver a wonderful presentation.
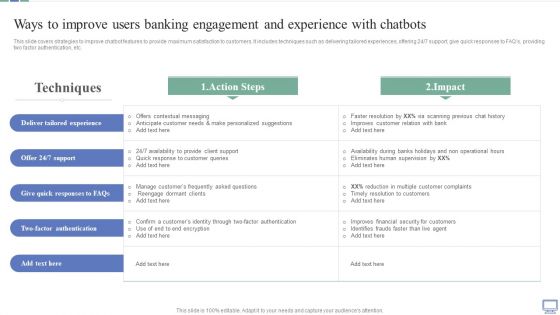
Ways To Improve Users Banking Engagement And Experience With Chatbots Information PDF
This slide covers strategies to improve chatbot features to provide maximum satisfaction to customers. It includes techniques such as delivering tailored experiences, offering 24 or 7 support, give quick responses to FAQs, providing two factor authentication, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Ways To Improve Users Banking Engagement And Experience With Chatbots Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Deployment Of Omnichannel Banking Solutions Ways To Improve Users Banking Engagement And Experience Mockup PDF
This slide covers strategies to improve chatbot features to provide maximum satisfaction to customers. It includes techniques such as delivering tailored experiences, offering 24 7 support, give quick responses to FAQ s, providing two factor authentication, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Deployment Of Omnichannel Banking Solutions Ways To Improve Users Banking Engagement And Experience Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Wireless Banking To Improve Tips To Ensure Safety Of Digital Wallets Fin SS V
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc. The Wireless Banking To Improve Tips To Ensure Safety Of Digital Wallets Fin SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
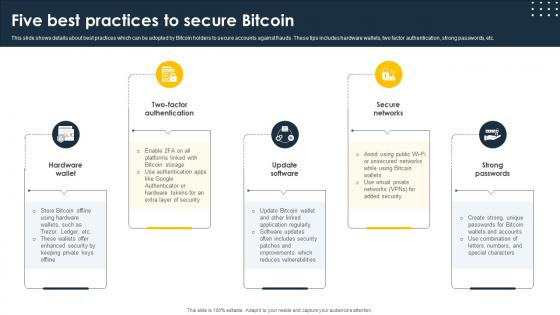
Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
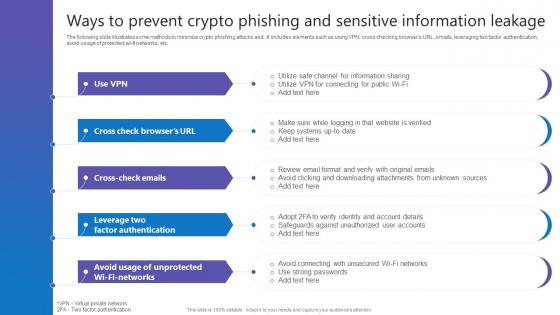
Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf today and make your presentation stand out from the rest

Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. This modern and well arranged Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.This modern and well-arranged Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Wireless Banking To Improve Strategies To Avoid Mobile Banking Frauds Fin SS V
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. Welcome to our selection of the Wireless Banking To Improve Strategies To Avoid Mobile Banking Frauds Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
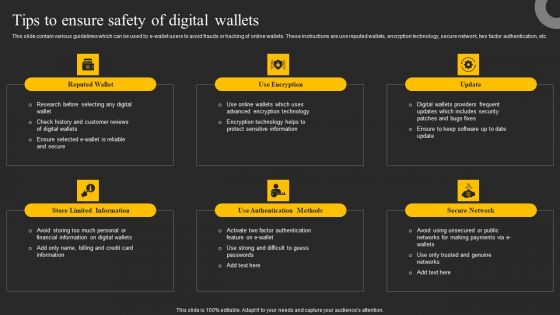
Tips To Ensure Safety Of Digital Wallets Ppt Summary Slide Download PDF
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc. Welcome to our selection of the Tips To Ensure Safety Of Digital Wallets Ppt Summary Slide Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Ways To Improve Users Banking Engagement And Experience With Chatbots Ppt Icon Portrait PDF
This slide covers strategies to improve chatbot features to provide maximum satisfaction to customers. It includes techniques such as delivering tailored experiences, offering 24 into 7 support, give quick responses to FAQs, providing two factor authentication, etc. This Ways To Improve Users Banking Engagement And Experience With Chatbots Ppt Icon Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Omnichannel Strategy Implementation For Banking Solutions Ways To Improve Users Banking Engagement Background PDF
This slide covers strategies to improve chatbot features to provide maximum satisfaction to customers. It includes techniques such as delivering tailored experiences, offering 24 7 support, give quick responses to FAQs, providing two factor authentication, etc. Welcome to our selection of the Omnichannel Strategy Implementation For Banking Solutions Ways To Improve Users Banking Engagement Background PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
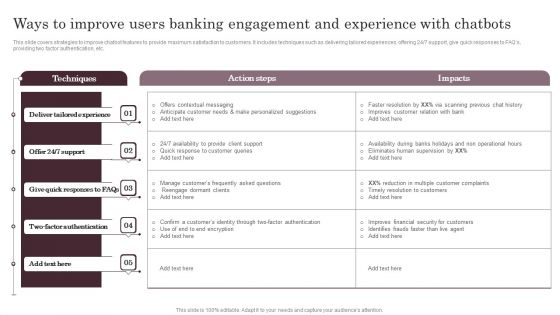
Ways To Improve Users Banking Engagement And Experience With Chatbots Infographics PDF
This slide covers strategies to improve chatbot features to provide maximum satisfaction to customers. It includes techniques such as delivering tailored experiences, offering 24 into 7 support, give quick responses to FAQs, providing two factor authentication, etc. Slidegeeks has constructed Ways To Improve Users Banking Engagement And Experience With Chatbots Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Mastering Blockchain Wallets Tips For Selecting The Ideal Crypto Software Wallet BCT SS V
This side covers recommendations for selecting most suitable software wallet for managing their cryptocurrencies. The purpose of this template is to provide best practices for selecting ideal software wallet such as checking reputation of company, two factor authentication, ensuring backup mechanism, number of cryptocurrencies, finding adequate transparency, etc. Explore a selection of the finest Mastering Blockchain Wallets Tips For Selecting The Ideal Crypto Software Wallet BCT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mastering Blockchain Wallets Tips For Selecting The Ideal Crypto Software Wallet BCT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

IoT Device Management Fundamentals Key Factors For Selecting Right IoT Device Management IoT Ss V
This slide exhibits specific factors to consider for selecting an IoT device management platform. These factors include connectivity management, scalability, security, and ability to adapt technological changes. The IoT Device Management Fundamentals Key Factors For Selecting Right IoT Device Management IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
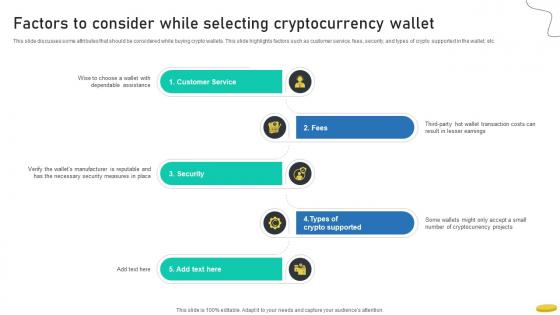
Factors To Consider While Selecting Cryptocurrency Wallet Cryptocurrency Management With Blockchain
This slide discusses some attributes that should be considered while buying crypto wallets. This slide highlights factors such as customer service, fees, security, and types of crypto supported in the wallet, etc.The Factors To Consider While Selecting Cryptocurrency Wallet Cryptocurrency Management With Blockchain is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. The Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Execution Of Product Lifecycle Product Lifecycle Effective Influencing Factors Guidelines Pdf
This slide covers factors determining the product lifecycle. The purpose of this template is to provide information based on several factors that improves the sales of a product. It includes factors such as rate of technical changes, rate of market acceptance, ease of competitive entry, risk bearing capacity, protection by patent, etc. The Execution Of Product Lifecycle Product Lifecycle Effective Influencing Factors Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
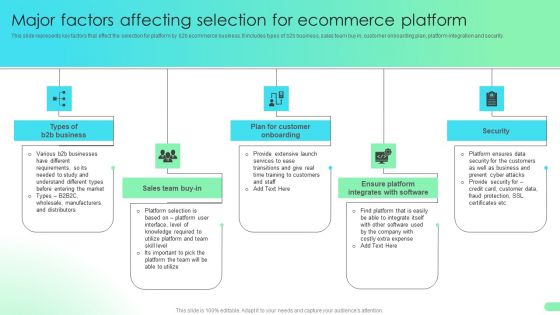
Major Factors Affecting Selection For Ecommerce Platform Comprehensive Guide For Developing Microsoft PDF
This slide represents key factors that effect the selection for platform by b2b ecommerce business. It includes types of b2b business, sales team buy in, customer onboarding plan, platform integration and security.The Major Factors Affecting Selection For Ecommerce Platform Comprehensive Guide For Developing Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Key Factors For Business Success Person Holding Key In Hand Ppt Powerpoint Presentation Ideas Background Designs
This is a key factors for business success person holding key in hand ppt powerpoint presentation ideas background designs. This is a four stage process. The stages in this process are eys for success, keys for achievement, highlights for success.

Key Factors For Customer Success Management Ppt Powerpoint Presentation Outline Guide
This is a key factors for customer success management ppt powerpoint presentation outline guide. This is a three stage process. The stages in this process are eys for success, keys for achievement, highlights for success.

Key Factors To Achieving Competitive Success Ppt Powerpoint Presentation Outline Ideas
This is a key factors to achieving competitive success ppt powerpoint presentation outline ideas. This is a three stage process. The stages in this process are eys for success, keys for achievement, highlights for success.

Key Factors Data Security For A Business Ppt PowerPoint Presentation Styles Layouts PDF
Persuade your audience using this key factors data security for a business ppt powerpoint presentation styles layouts pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including risks related to lack of visibility, risks related to human actions, key threat actors of the data risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Parameters To Establish Overall Devops Value IT Addressing Vital Success Factors Associated To Devops Contd Mockup PDF
This slide provides information regarding the critical success factors associated to DevOps in terms of service and product ownership, cross functional teams and implementing security in DevOps. This is a key parameters to establish overall devops value it addressing vital success factors associated to devops contd mockup pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like execute devops ci or cd automation toolset, tracking and kpis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Email Prevention Guidelines For Employees Formats PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi-factor authentication for email login credentials. Presenting cyber exploitation it email prevention guidelines for employees formats pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like usage of a spam filter, usage of mfa. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF. Use them to share invaluable insights on Factor Authentication, Phishing Malware, Accessing Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an awe inspiring pitch with this creative Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF bundle. Topics like Security And Compliance, Factor Authentication, Security Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Practices For Business To Increase Online Security Introduction PDF
This slide highlights best practices for business to increase digital safety which help prevent and mitigate inherent risk. It provides information about antivirus, software upgradation, suspicious emails, VPN and 2 factor authentication. Presenting Best Practices For Business To Increase Online Security Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Vulnerabilities, Factor Authentication, Avoid Suspicious Emails. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF. Use them to share invaluable insights on Security And Compliance, SAML Authentication, Data Subject Requests and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
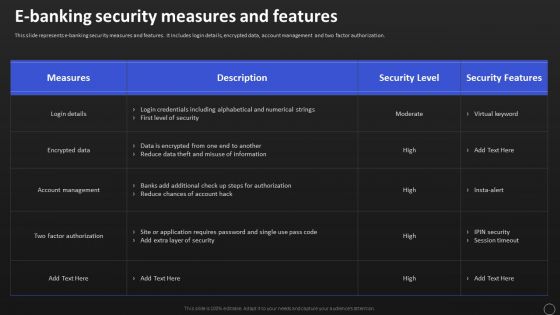
Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF
This slide represents e banking security measures and features. It includes login details, encrypted data, account management and two factor authorization. This Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system. This is a What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Developing, Essential Strategy, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
What Makes Cloud Security Different Cloud Computing Security IT Ppt Summary Icons PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi-tenant storage system. Deliver an awe inspiring pitch with this creative what makes cloud security different cloud computing security it ppt summary icons pdf bundle. Topics like convenience over security, centralization and multi tenant storage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
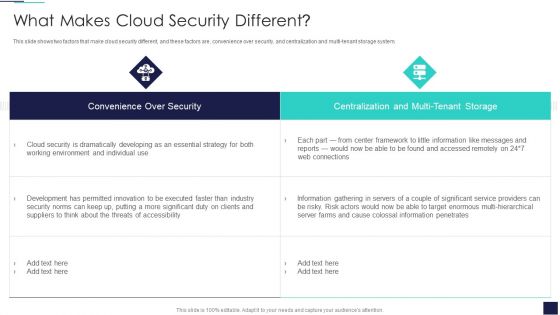
Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi-tenant storage system. Deliver an awe inspiring pitch with this creative Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF bundle. Topics like Cloud Security, Threats Accessibility, Risk Actors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
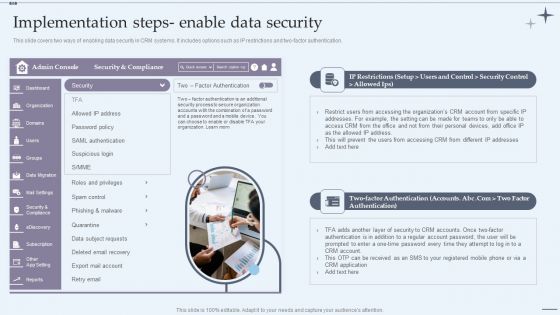
CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Presenting CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Marketing Executive, Marketing Intern, Sales Executive. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home