Cyber Threat

Cyber Risk Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this cyber risk ppt powerpoint presentation complete deck with slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twenty three this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

IT Protection Network Protection Cyber Attack Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection network protection cyber attack ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber attack, database server security, laptop protected, cyber threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
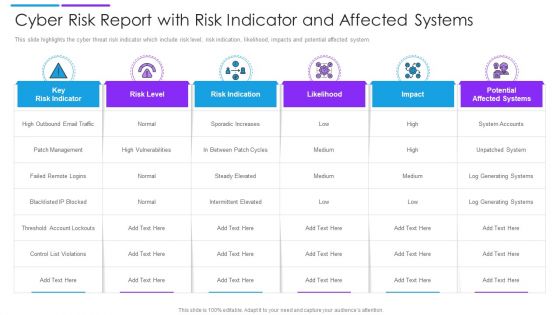
Cyber Risk Report With Risk Indicator And Affected Systems Brochure PDF
This slide highlights the cyber threat risk indicator which include risk level, risk indication, likelihood, impacts and potential affected system. Pitch your topic with ease and precision using this cyber risk report with risk indicator and affected systems brochure pdf. This layout presents information on risk indication, risk level, key risk indicator. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
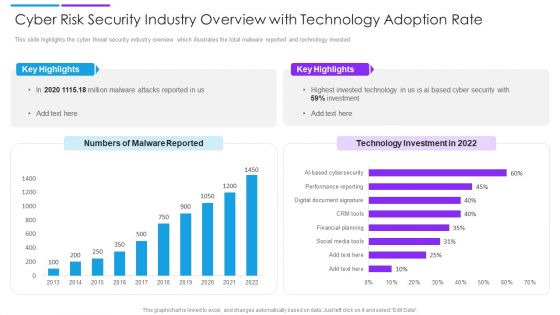
Cyber Risk Security Industry Overview With Technology Adoption Rate Slides PDF
This slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Pitch your topic with ease and precision using this cyber risk security industry overview with technology adoption rate slides pdf. This layout presents information on key highlights, technology investment, malware reported. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
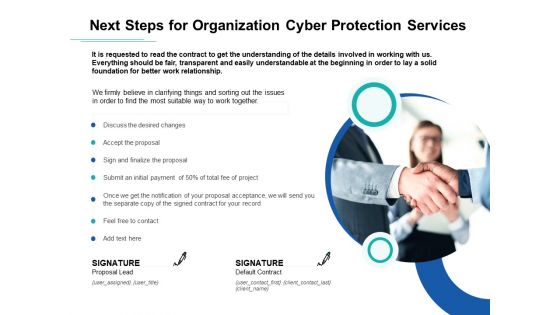
Develop Corporate Cyber Security Risk Mitigation Plan Next Steps For Organization Cyber Protection Services Topics PDF Themes PDF
Presenting develop corporate cyber security risk mitigation plan next steps for organization cyber protection services topics pdf themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like desired changes, initial payment, organization, cyber protection services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Develop Corporate Cyber Security Risk Mitigation Plan Case Study For Organization Cyber Protection Services Themes PDF Sample PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan case study for organization cyber protection services themes pdf sample pdf bundle. Topics like problem, results, our solution, low cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies To Mitigate Cyber Security Risks Amount Spent On Cyber Fraud Settlements Ppt Outline Visual Aids PDF
Presenting this set of slides with name strategies to mitigate cyber security risks amount spent on cyber fraud settlements ppt outline visual aids pdf. This is a one stage process. The stages in this process are settlements, amount, average per settlement, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
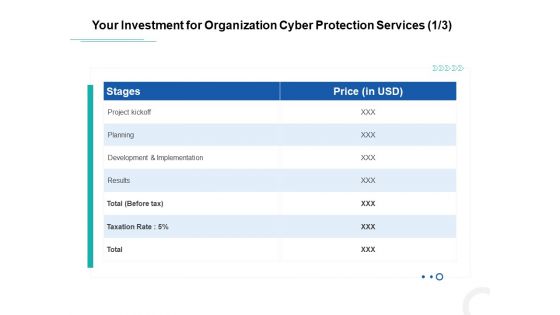
Develop Corporate Cyber Security Risk Mitigation Plan Your Investment For Organization Cyber Protection Services Planning Rules PDF
Deliver and pitch your topic in the best possible manner with this develop corporate cyber security risk mitigation plan your investment for organization cyber protection services planning rules pdf. Use them to share invaluable insights on project kickoff, planning, development and implementation, results and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Develop Corporate Cyber Security Risk Mitigation 30 60 90 Days Plan For Organization Cyber Protection Proposal Mockup PDF
This is a develop corporate cyber security risk mitigation 30 60 90 days plan for organization cyber protection proposal mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
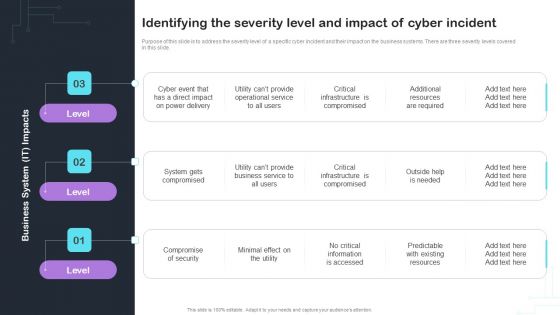
Cyber Risks And Incident Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Summary PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide. This modern and well arranged Cyber Risks And Incident Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
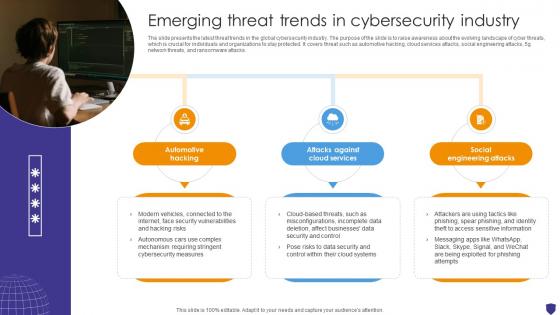
Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
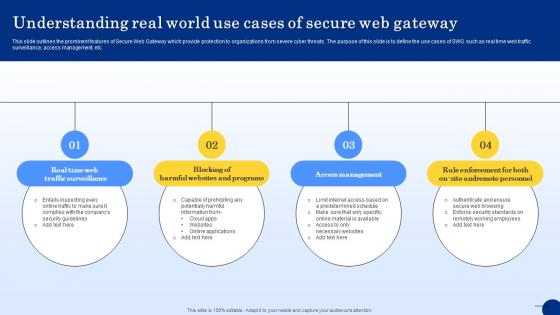
Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Risk Dashboard With Current Risks And Security Service Formats PDF
The following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Pitch your topic with ease and precision using this cyber risk dashboard with current risks and security service formats pdf. This layout presents information on current threats, current risks, regulation and policy coverage. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
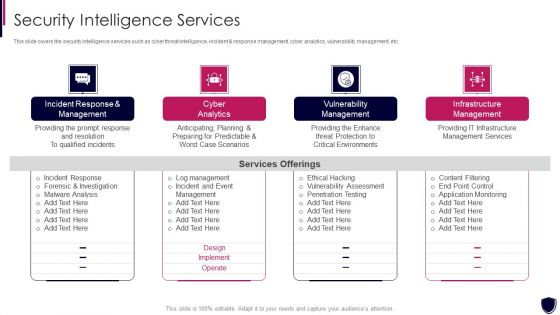
Enhancing Cyber Safety With Vulnerability Administration Security Intelligence Services Portrait PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting enhancing cyber safety with vulnerability administration security intelligence services portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
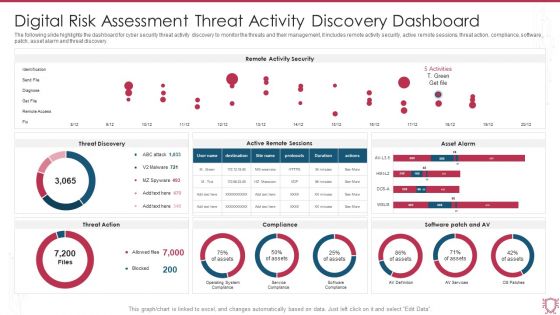
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF
The given slide reflects the upcoming cyber threats due to remote working amid of COVID -19. Some of them are pandemic associated attacks, cloud breaches and mobile security threats. Persuade your audience using this Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Pandemic Associated Attacks, Cloud Breaches, Mobile Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Cases Action Plans Process Ppt PowerPoint Presentation File Show PDF
This slide covers procedure of cyber security incident response. The purpose of this process is to examine the cyber threat and try to find the ways to mitigate the risk. It includes four steps such as identification and detection, containment, eradication and recovery and post recovery. Presenting Cyber Security Cases Action Plans Process Ppt PowerPoint Presentation File Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identification And Detection, Containment, Eradication And Recovery, Post Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
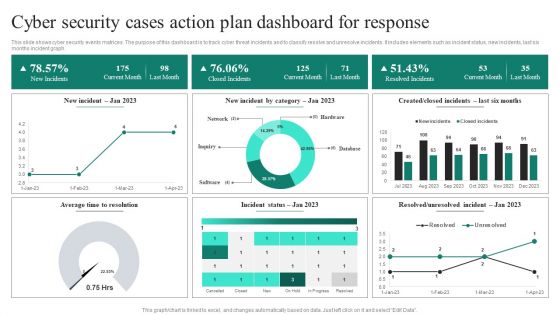
Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF
This slide shows cyber security events matrices. The purpose of this dashboard is to track cyber threat incidents and to classify resolve and unresolve incidents. It includes elements such as incident status, new incidents, last six months incident graph. Showcasing this set of slides titled Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF. The topics addressed in these templates are Current Month, Closed Incidents, Last Month, Resolved Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Dashboard For Threat Tracking In IT Security IT Ppt Outline Examples PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative dashboard for threat tracking in it security it ppt outline examples pdf bundle. Topics like monthly threat status, threats by owners, risk by threats, current risk status, threats based on role, threat report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Dashboard For Threat Tracking In Information Security Ppt PowerPoint Presentation File Example Introduction PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative info security dashboard for threat tracking in information security ppt powerpoint presentation file example introduction pdf bundle. Topics like threats by owners, risk by threats, threat report, monthly threat status, current risk status, threats based on role can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF
The given slide depicts the cyber threat analytics to track the attacks. It includes the no. of incidents, open and solved tickets, category wise no. of incidents along with malware type etc. Pitch your topic with ease and precision using this Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF. This layout presents information on Power Security Team, Open Incidents, Incidents Solved, Open Tickets. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
IT Security Dashboard For Threat Tracking In Information Technology Security Ppt Inspiration Gallery PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative it security dashboard for threat tracking in information technology security ppt inspiration gallery pdf bundle. Topics like current risk status, threat report, risk by threats, threats based on role, threats by owners can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Desktop Security Management Dashboard For Threat Tracking In Computer Security Guidelines PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative desktop security management dashboard for threat tracking in computer security guidelines pdf bundle. Topics like threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cybersecurity Dashboard For Threat Tracking In Electronic Information Security Ppt Ideas Graphics PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cybersecurity dashboard for threat tracking in electronic information security ppt ideas graphics pdf bundle. Topics like dashboard for threat tracking in electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
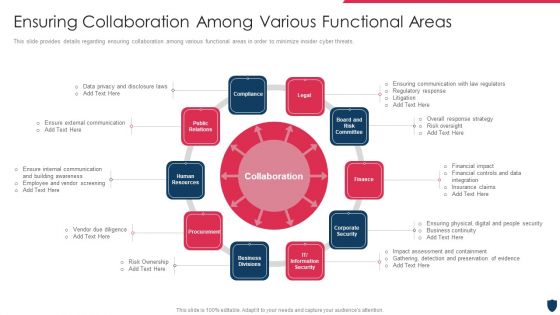
Cyber Safety Incident Management Ensuring Collaboration Among Various Functional Areas Themes PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber safety incident management ensuring collaboration among various functional areas themes pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like legal, finance, procurement, public relations, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF
The following slide depicts some key trends in cyber threats happening across the globe. It includes some facts and figures related to the malware attack, data breach records, annual losses etc. Presenting Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Malware Attack, Business Fall, Data Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information KPI Metrics Dashboard To Effectively Track Cyber Guidelines PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Welcome to our selection of the Prevention Of Information KPI Metrics Dashboard To Effectively Track Cyber Guidelines PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
Russian Cyber Attacks On Ukraine IT Cybersecurity Risks Of An Escalating Icons PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. This is a russian cyber attacks on ukraine it cybersecurity risks of an escalating icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like capabilities, economic, measures, severe, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF
The following slide represents the common types of cyber threats. It includes malware, phishing, password attacks, drive by downloads, man in the middle and denial of service attacks. Persuade your audience using this Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Malware Through, Phishing Through, Password Attacks Through. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Risk Management For Organization Essential Assets Determine Several Threat Actors Profile Inspiration PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative risk management for organization essential assets determine several threat actors profile inspiration pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Determine Several Threat Actors Profile Clipart PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management determine several threat actors profile clipart pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhancing Information Technology With Strategic Risk Management Plan To Manage Cyber Graphics PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Find highly impressive Enhancing Information Technology With Strategic Risk Management Plan To Manage Cyber Graphics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Enhancing Information Technology With Strategic Risk Management Plan To Manage Cyber Graphics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Ukraine Cyberwarfare Hybrid Warfare Cyber Rapid Response Team Crrt Structure Pdf
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyber attacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands. Presenting ukraine cyberwarfare hybrid warfare cyber rapid response team crrt structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Initiative of the European Union to strengthen defense and cooperation among member states, Group is equipped with widely used cyber toolkits for detecting, recognizing, and mitigating cyber threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
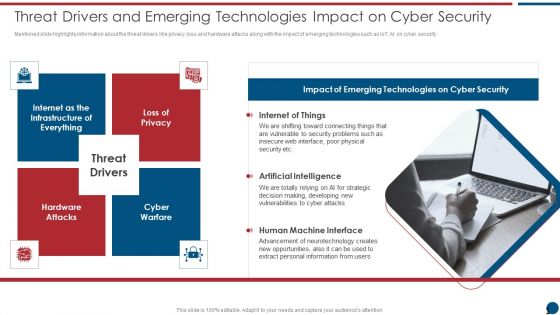
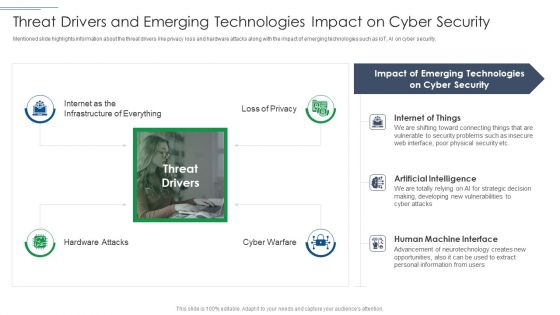
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
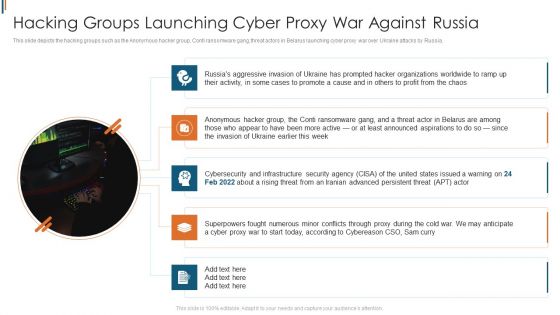
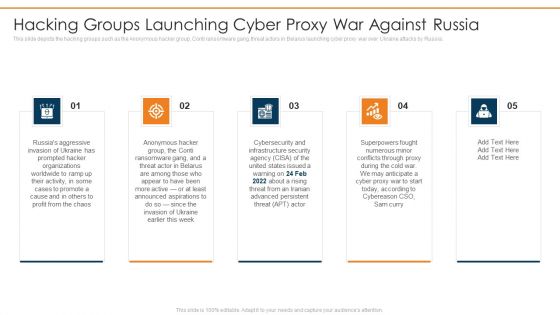
Ukraine Cyberwarfare Hacking Groups Launching Cyber Proxy War Against Russia Guidelines Pdf
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting ukraine cyberwarfare hacking groups launching cyber proxy war against russia guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Reasons And Impact Of Website Hacking On Business Elements PDF
This slide represents the hacking of our website, including the reasons behind it and its overall impact on our business, such as loss of reputation, clients, and information. Presenting cyber exploitation it reasons and impact of website hacking on business elements pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reasons behind website hacking, 2022, impact of website hacking on business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

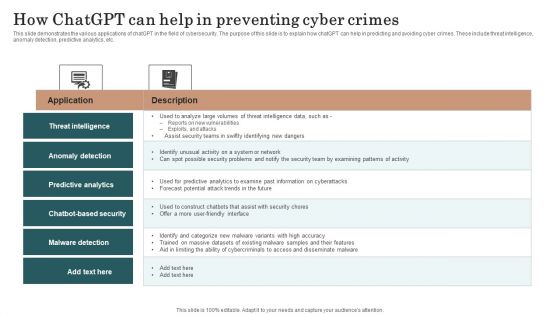
How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Regenerative Artificial Intelligence Systems How Chatgpt Can Help In Preventing Cyber Crimes Diagrams PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Regenerative Artificial Intelligence Systems How Chatgpt Can Help In Preventing Cyber Crimes Diagrams PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
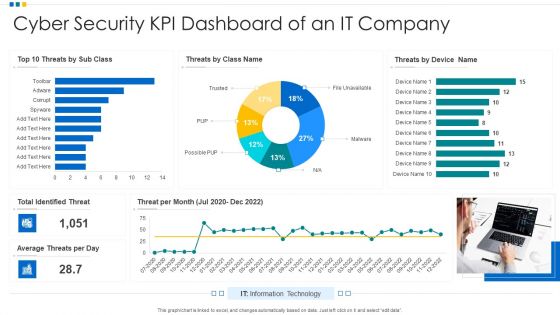
Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF
Showcasing this set of slides titled Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF. The topics addressed in these templates are Cyber Security, KPI Dashboard, Average Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Terrorism Assault Disaster Recovery Plan For The Business Template PDF
This slide illustrates the elements that will be taken into account when establishing a recovery plan for company to go back to business swiftly and successfully.This is a cyber terrorism assault disaster recovery plan for the business template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Dashboard For Threat Tracking Of Cyber Terrorism You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
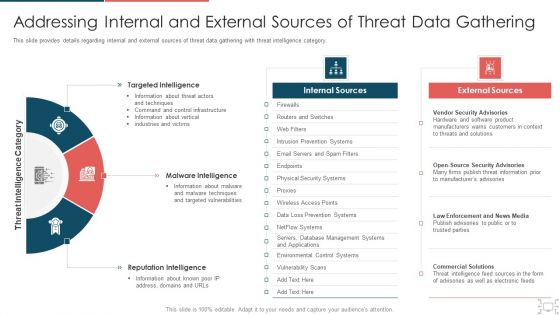
cyber security administration in organization addressing internal and external sources of gathering structure pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a cyber security administration in organization addressing internal and external sources of gathering structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, sources, internal, intelligence, reputation . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pre And Post Process Results Of Cyber Security Process Changes Sample PDF
This slide shows reduction in threats percentage after adopting cyber security. It includes computer virus, data breach, DOS and phishing. Pitch your topic with ease and precision using this Pre And Post Process Results Of Cyber Security Process Changes Sample PDF. This layout presents information on Process Results, Process Changes, Key Insights. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
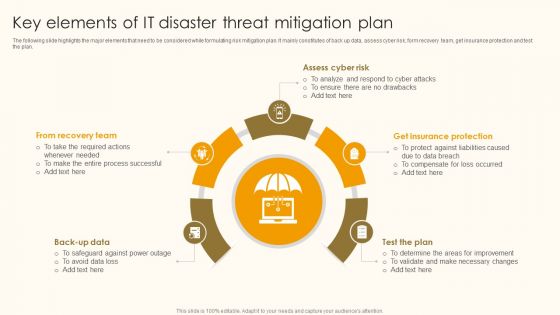
Key Elements Of IT Disaster Threat Mitigation Plan Ppt Show Files PDF
The following slide highlights the major elements that need to be considered while formulating risk mitigation plan. It mainly constitutes of back up data, assess cyber risk, form recovery team, get insurance protection and test the plan. Persuade your audience using this Key Elements Of IT Disaster Threat Mitigation Plan Ppt Show Files PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including From Recovery Team, Assess Cyber Risk, Get Insurance Protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Security Threat Analysis Plan With Agents And Tactics Ppt PowerPoint Presentation Gallery Infographic Template PDF
Showcasing this set of slides titled internet security threat analysis plan with agents and tactics ppt powerpoint presentation gallery infographic template pdf. The topics addressed in these templates are corporations, hacktivists, cyber fighters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Boost your pitch with our creative Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf
This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc. The Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Management Inspiration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting enhancing cyber safety with vulnerability administration security information and event management inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data retention, forensic analysis, dashboards, data correlation, data aggregation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Online Security Learning System For Malware Threat Control Ppt PowerPoint Presentation Layouts Portfolio PDF
Presenting this set of slides with name online security learning system for malware threat control ppt powerpoint presentation layouts portfolio pdf. This is a three stage process. The stages in this process are network protection and control, access control protection, email and web browser protections, virus penetration testing and control fundamentals, password protection, wireless protection, cyber incitement management, ethical hacking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigation Strategies For Operational Threat Operational Risks Mapping Ppt File Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks mapping ppt file graphics pdf. Use them to share invaluable insights on technology risk, transaction processing risk, unauthorized activity, business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home