Cyber Threat
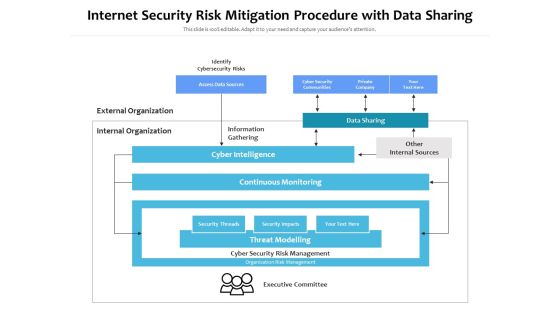
Internet Security Risk Mitigation Procedure With Data Sharing Ppt PowerPoint Presentation Pictures Show PDF
Persuade your audience using this internet security risk mitigation procedure with data sharing ppt powerpoint presentation pictures show pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including identify cybersecurity risks, external organization, internal organization, information gathering, data sharing, other internal sources, cyber intelligence, continuous monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF bundle. Topics like Business Disruption, Cost By Consequence, Malware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
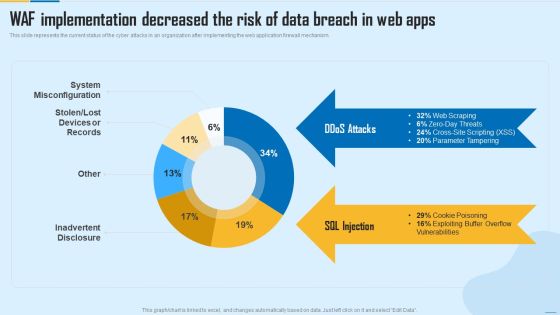
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Iot Digital Twin Technology Post Covid Expenditure Management Optimize Digitalize Supply Template PDF
This slide focuses on the optimization and digitalization of supply chain operations which covers cyber supply chain, risk analytics and physical supply chain. Deliver an awe inspiring pitch with this creative iot digital twin technology post covid expenditure management optimize digitalize supply template pdf bundle. Topics like supply chain, promotion, risk, analytics, optimization, procurement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Plan Across Key Financial Areas Portrait PDF
This slide represents cyber security strategy across key financial areas illustrating talent centric, strategic and innovative, risk focused, intelligence driven and resilient and scalable. Presenting IT Security Plan Across Key Financial Areas Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strategic And Innovative, Risk Focused, Intelligence Driven. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Optimizing Tasks Team Collaboration Agile Operations Prioritizing Agile Software Development Tasks Guidelines PDF
Presenting this set of slides with name optimizing tasks team collaboration agile operations prioritizing agile software development tasks guidelines pdf. This is a five stage process. The stages in this process are quick delivery of project deliverables, enhancing team communication, customer collaboration, minimize cyber security risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
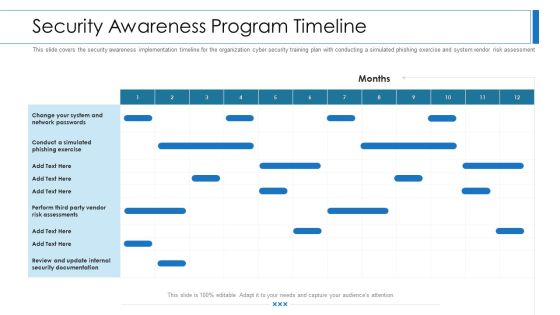
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Staff Learning Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
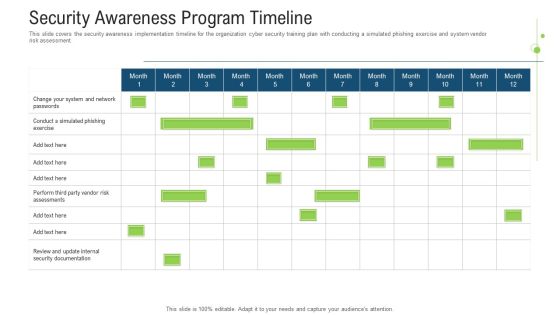
Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Managing Computer Security 30 Days Plan Designs PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 30 days plan designs pdf bundle. Topics like awareness, measured, risk, security, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Minimizing Operational Cost Through Iot Virtual Twins Implementation Optimize And Digitalize Mockup PDF
This slide focuses on the optimization and digitalization of supply chain operations which covers cyber supply chain, risk analytics and physical supply chain, Deliver and pitch your topic in the best possible manner with this minimizing operational cost through iot virtual twins implementation optimize and digitalize mockup pdf. Use them to share invaluable insights on analysis, optimization, predicative, design, optimize and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CPS Security And Privacy Life Cycle Ppt Gallery Professional PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Deliver and pitch your topic in the best possible manner with this CPS Security And Privacy Life Cycle Ppt Gallery Professional PDF. Use them to share invaluable insights on Risk, Required, Securityand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
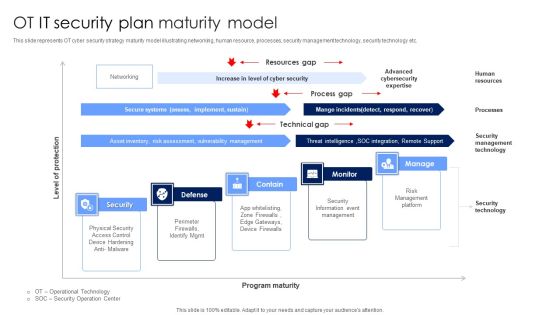
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security What Are The Benefits Of Information Technology Security Ppt Layouts Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a it security what are the benefits of information technology security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, process, potential threats, security devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF
The following slide highlights the five phase of risk based cyber security which includes business impact analysis, risk assessment, controls, report and monitor, it provides activity, value and outcome for each phase which helps company to develop a consistent incident response process. Presenting Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Impact Analysis, Risk Assessment, Controls, Report, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF
The following slide highlights the phase of cyber security incident response cycle depicting preparation phase, analysis phase, response phase, and post event phase. Persuade your audience using this Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Post Event Phase, Response Phase, Preparation Phase, Analysis Phase. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Analyzing The Real Estate Risk With Major Consequences Managing Commercial Property Risks Clipart PDF
The following slide exhibits various risks which can be used to analyze risk involved in real estate project. Information covered in this slide is related to cyber risk, physical property damager, vulnerability to accidents, lawsuits from unsatisfied clients, etc. Deliver an awe inspiring pitch with this creative Analyzing The Real Estate Risk With Major Consequences Managing Commercial Property Risks Clipart PDF bundle. Topics like Physical Property, Vulnerability Accidents, Unsatisfied Clients can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF. Use them to share invaluable insights on Risk Prevention, Risk Prevention, Risk Occurrence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Statistics Highlighting Various Risks Faced By Real Managing Commercial Property Risks Elements PDF
The following slide exhibits major statistics illustrating the different risks faced by the real estate owners and managers in two years. Information covered in this slide is related to physical property damager, tenant risks, administrative risks, cyber risks and employment issues. Deliver and pitch your topic in the best possible manner with this Key Statistics Highlighting Various Risks Faced By Real Managing Commercial Property Risks Elements PDF. Use them to share invaluable insights on Various Cybercrimes, Estate Managers, Natural Disasters and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management What Are The Benefits Of Computer Security Icons PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting desktop security management what are the benefits of computer security icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, environment, potential, devices, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Risk Management Structure In Financial Companies Roles And Responsibilities For Managing Operational Risk Topics PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. This is a operational risk management structure in financial companies roles and responsibilities for managing operational risk topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like board of directors, risk and audit committee, executive committee, investment oversight committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF
This slide showcases software that can help organization to monitor and manage the risk. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF. Use them to share invaluable insights on Vulnerability Management, Centralized Repository, Intelligent Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Selecting Suitable Software For Information Security Risk Management Information Security Risk Administration Sample PDF
This slide showcases software that can help organization to monitor and manage the risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. Want to ace your presentation in front of a live audience Our Selecting Suitable Software For Information Security Risk Management Information Security Risk Administration Sample PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.
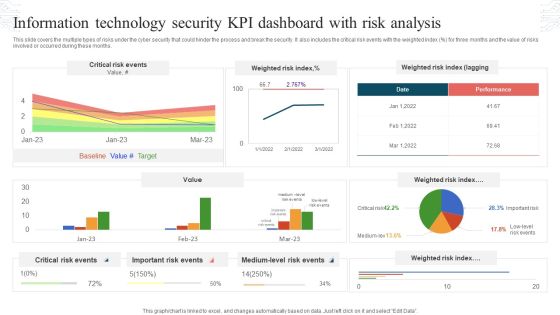
Information Technology Security KPI Dashboard With Risk Analysis Topics PDF
This slide covers the multiple types of risks under the cyber security that could hinder the process and break the security. It also includes the critical risk events with the weighted index percent for three months and the value of risks involved or occurred during these months. Showcasing this set of slides titled Information Technology Security KPI Dashboard With Risk Analysis Topics PDF. The topics addressed in these templates are Critical Risk Events, Weighted Risk Index, Important Risk Events. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Units Risk Ratings And Analysis Software Dashboard Ideas PDF
This slide covers risk distribution among different business units. It also includes inherent risk ratings for anti-bribery, commodity markets, competition, cyber security along with residual risk distribution matrix. Pitch your topic with ease and precision using this Business Units Risk Ratings And Analysis Software Dashboard Ideas PDF. This layout presents information on Risk Dashboard, Inherent Risk Medium, Controls Rising Weak. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Management Risk And Compliance Model Summary PDF
The following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Showcasing this set of slides titled Cloud Security Management Risk And Compliance Model Summary PDF. The topics addressed in these templates are Governance, Risk, Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roles And Responsibilities For Managing Operational Risk Slides PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.This is a roles and responsibilities for managing operational risk slides pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk and audit committee, executive committee, investment oversight committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Risk Assessment Management Dashboard With Geographical Distribution Clipart PDF
The following slide highlights the cyber security risk management dashboard with dashboard with geographical distribution depicting incident volume by severity, open incidents, root cause details, divisional details and geographical distribution of risks. Pitch your topic with ease and precision using this Digital Risk Assessment Management Dashboard With Geographical Distribution Clipart PDF. This layout presents information on Geographical Distribution, Root Cause Details, Divisional Details, Social Engineering. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Risk Assessment On Effective IT Service Excellence Designs PDF
This slide signifies the bar graph comparison on growth and benefits provided by IT services. It includes various assistance like cost control, cyber security risk, data analytics and anti virus protection. Showcasing this set of slides titled Comparative Risk Assessment On Effective IT Service Excellence Designs PDF. The topics addressed in these templates are Software Management, Incident Management, Release Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
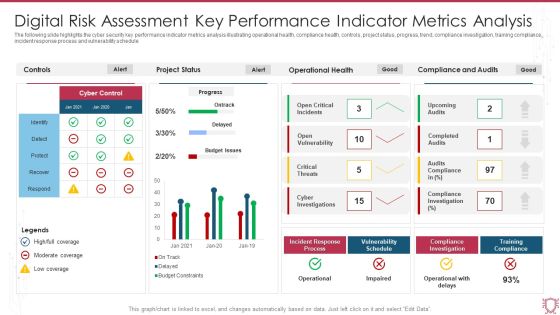
Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF
The following slide highlights the cyber security key performance indicator metrics analysis illustrating operational health, compliance health, controls, project status, progress, trend, compliance investigation, training compliance, incident response process and vulnerability schedule. Showcasing this set of slides titled Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF. The topics addressed in these templates are Project Status, Operational Health, Compliance And Audits. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Initiatives To Produce Effective Concept For Logistic Firm Risks Involved In Technology Formats PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies or Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this initiatives to produce effective concept for logistic firm risks involved in technology formats pdf. Use them to share invaluable insights on connectivity risk, cyber security risk, inventory management risk, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
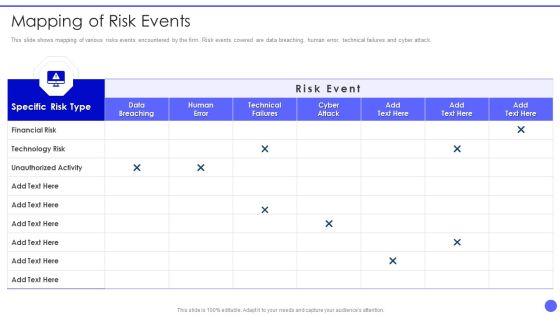
Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF. Use them to share invaluable insights on Specific Risk Type, Financial Risk, Technology Risk, Unauthorized Activity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
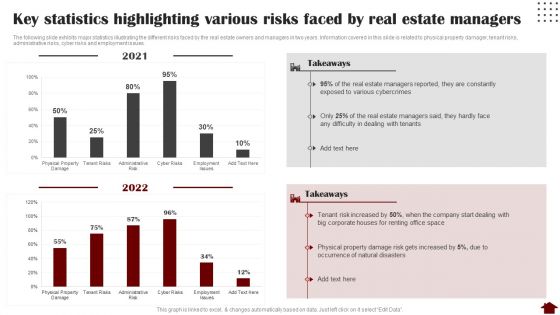
Key Statistics Highlighting Various Risks Faced By Real Estate Managers Mockup PDF
The following slide exhibits major statistics illustrating the different risks faced by the real estate owners and managers in two years. Information covered in this slide is related to physical property damager, tenant risks, administrative risks, cyber risks and employment issues. Deliver and pitch your topic in the best possible manner with this Key Statistics Highlighting Various Risks Faced By Real Estate Managers Mockup PDF. Use them to share invaluable insights on Key Statistics Highlighting, Various Risks, Real Estate Managers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
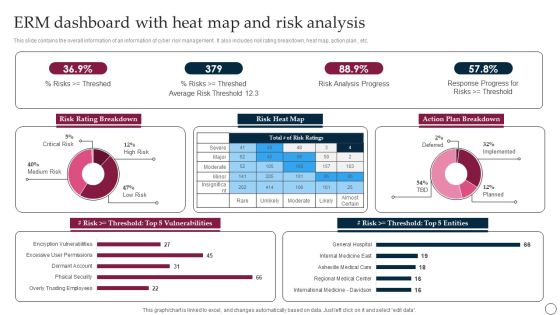
ERM Dashboard With Heat Map And Risk Analysis Ppt PowerPoint Presentation File Backgrounds PDF
This slide contains the overall information of an information of cyber risk management . It also includes risk rating breakdown, heat map, action plan , etc. Showcasing this set of slides titled ERM Dashboard With Heat Map And Risk Analysis Ppt PowerPoint Presentation File Backgrounds PDF. The topics addressed in these templates are Risk Rating Breakdown, Average Risk, Risk Analysis Progress. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
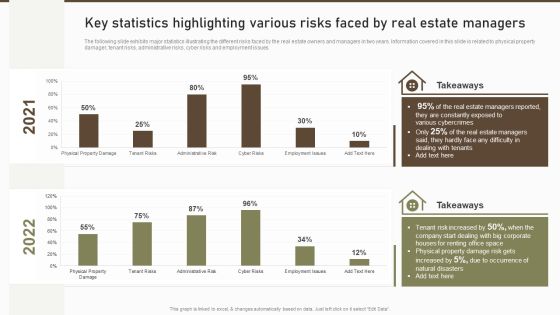
Key Statistics Highlighting Various Risks Faced By Real Estate Managers Microsoft PDF
The following slide exhibits major statistics illustrating the different risks faced by the real estate owners and managers in two years. Information covered in this slide is related to physical property damager, tenant risks, administrative risks, cyber risks and employment issues. Deliver an awe inspiring pitch with this creative Key Statistics Highlighting Various Risks Faced By Real Estate Managers Microsoft PDF bundle. Topics like Estate Managers, Constantly Exposed, Various Cybercrimes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
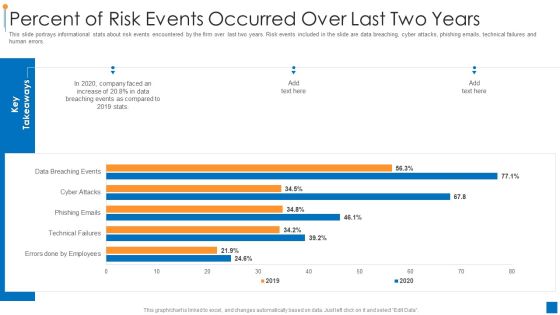
International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives Scorecard To Check Cybersecurity And Digital Risk Preparedness Rules PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative data safety initiatives scorecard to check cybersecurity and digital risk preparedness rules pdf bundle. Topics like risk prevention considerations, score, standard rating, top management displays can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF bundle. Topics like Technical Failures, Phishing Emails, Data Breaching can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
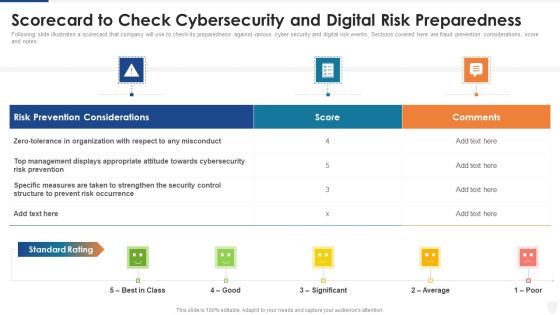
Scorecard To Check Cybersecurity And Digital Risk Preparedness Ppt Layouts Brochure PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this scorecard to check cybersecurity and digital risk preparedness ppt layouts brochure pdf. Use them to share invaluable insights on organization, management, measures, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Minimize Cloud Risks Medical Care Business Case Competition ABS Healthcare Company Overview Introduction PDF
This slide shows details about ABC Carbonated Drink Company such as company type, employees, headquarters, annual revenue, CEO, founding year etc. This is a minimize cloud risks medical care business case competition ABS healthcare company overview introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business overview, annual revenue, cyber security cases, manufactures, global advertising expenses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
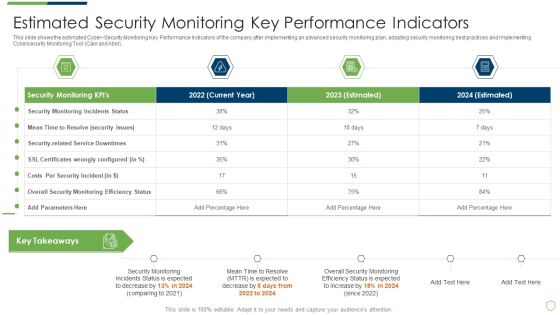
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
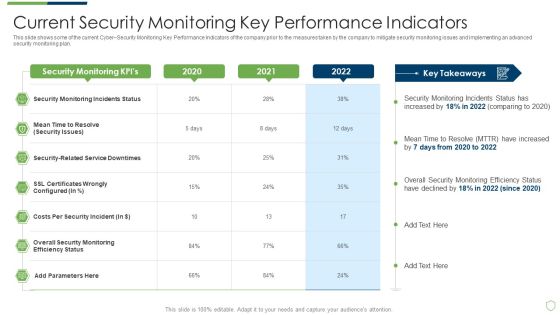
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF
The following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Presenting Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Responsibilities, Security Awareness, Data Support, Data Segregation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Web App Firewall Services IT WAF Implementation Decreased The Risk Of Data Breach In Web Apps Portrait PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this web app firewall services it waf implementation decreased the risk of data breach in web apps portrait pdf. Use them to share invaluable insights on waf implementation decreased the risk of data breach in web apps and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home