Table Of Safety Contents
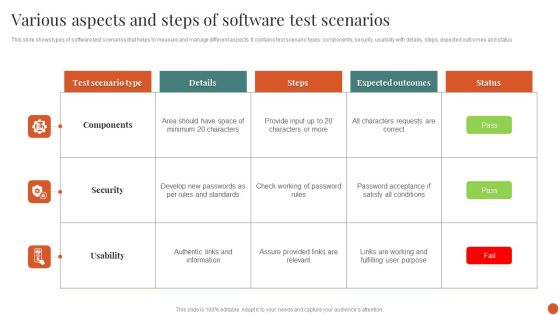
Various Aspects And Steps Of Software Test Scenarios Formats PDF
This slide shows types of software test scenarios that helps to measure and manage different aspects. It contains test scenario types components, security, usability with details, steps, expected outcomes and status.Showcasing this set of slides titled Various Aspects And Steps Of Software Test Scenarios Formats PDF. The topics addressed in these templates are Expected Outcomes, Characters Requests, Assure Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Before Event Tasks Budget Estimation Prior Launch Event Summary PDF
This slide showcases the estimated cost for venue, decor and food. It further includes security fee, A OR V equipment charges, lighting and flower cost. Boost your pitch with our creative Budget Before Event Tasks Budget Estimation Prior Launch Event Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Client Investment And Financial Planning Meeting Schedule Graphics PDF
This slide presents a meeting schedule plan of a financial company to do investment planning for its customers. It includes tasks like goals clarification, debt management, liquidity planning, social security planning, cash flow plan approval, etc. Showcasing this set of slides titled Client Investment And Financial Planning Meeting Schedule Graphics PDF. The topics addressed in these templates are Meeting, Foundation, Growth. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Website SEO Checklist To Improve Traffic Management Results Rules PDF
This slide showcases checklist point to ensure no disruption in traffic movement to the website and within the website. Key points included here are use of relevant keywords on each page, use of interlinks, URL security, installation of Google search console and analytic etc. Showcasing this set of slides titled Website SEO Checklist To Improve Traffic Management Results Rules PDF. The topics addressed in these templates are Tasks, In Progress, Completed. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Software For Gaming Application Personal Computer Summary PDF
Following slide showcase software for personal computer PC gaming that can be used by gaming industry to match game skillset and requirements. It include elements such as gaming software, features, pros, cons and additional notes. Showcasing this set of slides titled Various Software For Gaming Application Personal Computer Summary PDF. The topics addressed in these templates are Team Speak, Performance Optimization, Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Objectives Of Implementing Identify And Access Management Technique Clipart PDF
This slide shows business goals that can be achieved by identification and access management strategy by systematically implementing concerned business activities. It include objectives such as security system, business verticals integration , etc. Showcasing this set of slides titled Business Objectives Of Implementing Identify And Access Management Technique Clipart PDF. The topics addressed in these templates are Business Activities, Impact, Objective. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Website Design Procedure Gant Chart Graphics PDF
This slide showcases website design gantt chart illustrates helpful resource for both designers and clients, since it keeps everyone focused on the work and objectives at hand. It includes starting point , activities under process , summary element , finish etc. Showcasing this set of slides titled Website Design Procedure Gant Chart Graphics PDF. The topics addressed in these templates are Stages, Weeks, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF
This slide describes the implementation cost of security operations, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Boost your pitch with our creative Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Physical Fitness Program Budget Plan For Small Business Guidelines PDF
Following slide provide insight about budget plan which can be used by small firms for managing organisation finance. It includes key components such as expense category, estimated budget, actual cost, variance and variance percentage. Showcasing this set of slides titled Physical Fitness Program Budget Plan For Small Business Guidelines PDF. The topics addressed in these templates are Revenue, Expenses, Event Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Clinical Trial Phases With Goals And Patients Number Medical Research Phases For Clinical Tests Information PDF
In this slide, tabulation is done of key objectives of each step of clinical research trials. It also provides information regarding the count of volunteers that underwent trials to check drug safety. Find a pre designed and impeccable Clinical Trial Phases With Goals And Patients Number Medical Research Phases For Clinical Tests Information PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Find highly impressive Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Explore a selection of the finest Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF
This slide showcases software that can help organization to monitor and manage the information security. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc. Explore a selection of the finest Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Developing IT Security Strategy Reporting Structure For Information Security Risk Sample PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Reporting Structure For Information Security Risk Sample PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Google Cloud Service Models Google Cloud Platform Services Overview Information PDF
This slide talks about the overview of google cloud platform services. The purpose of this slide is to demonstrate the various google cloud platform services. The services include compute, management, networking, storage and database, big data, identity and security, and machine learning. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Google Cloud Service Models Google Cloud Platform Services Overview Information PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain.Find highly impressive Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.

Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF
This slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Explore a selection of the finest Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Role Of Management In Security Governance Across Firm Summary PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Explore a selection of the finest Role Of Management In Security Governance Across Firm Summary PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Role Of Management In Security Governance Across Firm Summary PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
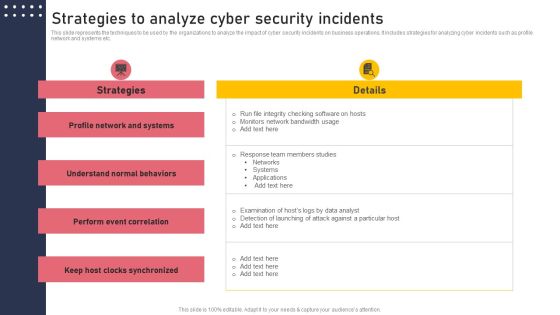
Strategies To Analyze Cyber Security Incidents Structure PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Find highly impressive Strategies To Analyze Cyber Security Incidents Structure PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Strategies To Analyze Cyber Security Incidents Structure PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF
This slide provides information regarding risk response plan for firms in terms of employee safety, development of cross functional team, ensuring liquidity and developing contingency plan, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Component Matrix Of IT Risk Control Strategies Risk Management Guidelines PDF
This slide focuses on the component matrix of information technology risk management which shows risk level associated with multiple IT projects with reference to components such as safety, vendor and regulation concerns, new technology, degree of change, etc. Pitch your topic with ease and precision using this Component Matrix Of IT Risk Control Strategies Risk Management Guidelines PDF. This layout presents information on IT Projects, Moderate Risk, Lower Risk, Higher Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
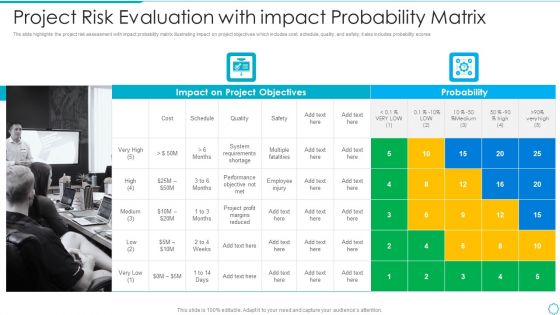
Project Risk Evaluation With Impact Probability Matrix Introduction PDF
The slide highlights the project risk assessment with impact probability matrix illustrating impact on project objectives which includes cost, schedule, quality, and safety, it also includes probability scores Pitch your topic with ease and precision using this project risk evaluation with impact probability matrix introduction pdf This layout presents information on system requirements shortage, performance objective, employee injury It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Customer In Store Purchase Experience New Shopper Imperatives To Determine Consumer Structure PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Deliver and pitch your topic in the best possible manner with this Customer In Store Purchase Experience New Shopper Imperatives To Determine Consumer Structure PDF. Use them to share invaluable insights on Imperative, Priority Shopper, Flexibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Retailer Instructions Playbook New Shopper Imperatives To Determine Consumer Preferences Inspiration PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. all imperatives are assessed based on priority of shopper. Deliver and pitch your topic in the best possible manner with this Retailer Instructions Playbook New Shopper Imperatives To Determine Consumer Preferences Inspiration PDF. Use them to share invaluable insights on Planning, Environmental Consciousness, Manufacturing Process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Retail Shop Administration New Shopper Imperatives To Determine Consumer Preferences Professional PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Want to ace your presentation in front of a live audience Our Retail Shop Administration New Shopper Imperatives To Determine Consumer Preferences Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
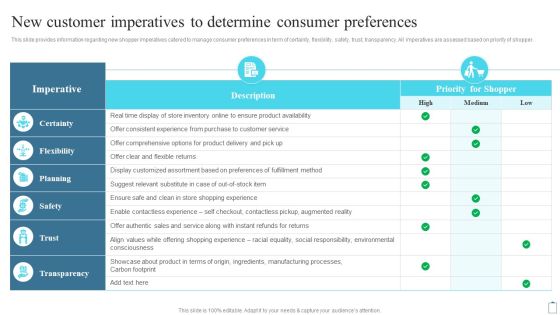
New Customer Imperatives To Determine Consumer Preferences Customer Engagement Administration Pictures PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Find a pre-designed and impeccable New Customer Imperatives To Determine Consumer Preferences Customer Engagement Administration Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

One Week Staff Training Program Schedule Ppt Pictures Samples PDF
This slide covers seven days employee training plan. It includes daily training schedule on topics such as safety, inclusion, customer relation, marketing, mechanical, legal, conflict, etc. Pitch your topic with ease and precision using this One Week Staff Training Program Schedule Ppt Pictures Samples PDF. This layout presents information on Customer Relation, After Sales, Mechanical, Marketing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF
This slide talks about the various advantages of SOC-as-a-Service for organizations. The purpose of this slide is to highlight the main pros of security operations centers, including lowering the risk of data breaches, quick detection and remediation, ability to scale, resource optimization, enhanced maturity, and lowering costs. Find highly impressive Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

E Commerce Business Development Plan E Commerce Services To Enhance Customer Experience Graphics PDF
This slide outlines various services provided by e-commerce businesses to improve customer experience. It showcases services such as online product catalog, secure payment processing, shipping and delivery, personalized recommendations and customer service and support. Explore a selection of the finest E Commerce Business Development Plan E Commerce Services To Enhance Customer Experience Graphics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our E Commerce Business Development Plan E Commerce Services To Enhance Customer Experience Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Find highly impressive Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. Explore a selection of the finest Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
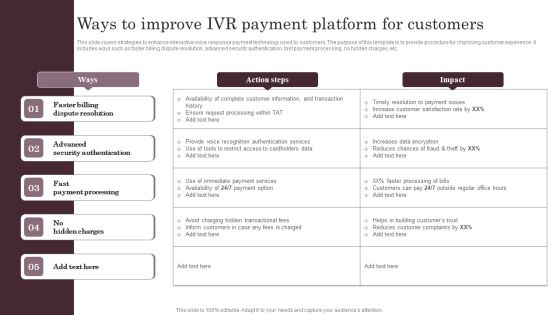
Omnichannel Services Solution In Financial Sector Ways To Improve IVR Payment Platform Infographics PDF
This slide covers strategies to enhance interactive voice response payment technology used by customers. The purpose of this template is to provide procedure for improving customer experience. It includes ways such as faster billing dispute resolution, advanced security authentication, fast payment processing, no hidden charges, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Omnichannel Services Solution In Financial Sector Ways To Improve IVR Payment Platform Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Explore a selection of the finest CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Boost your pitch with our creative Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
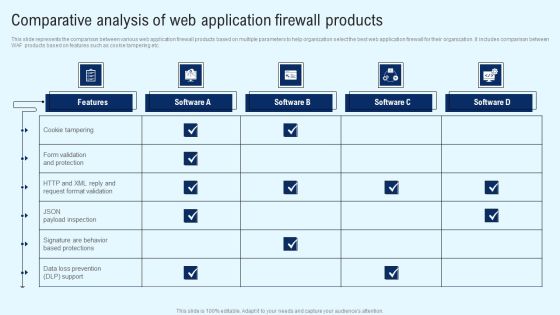
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Find highly impressive Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
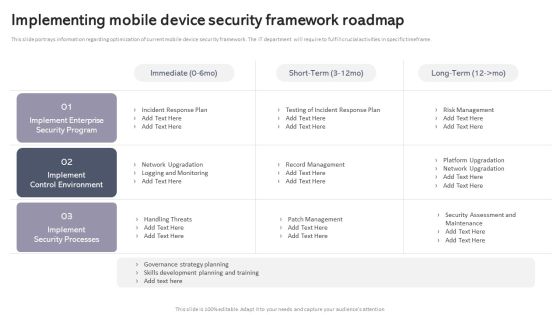
Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Explore a selection of the finest Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
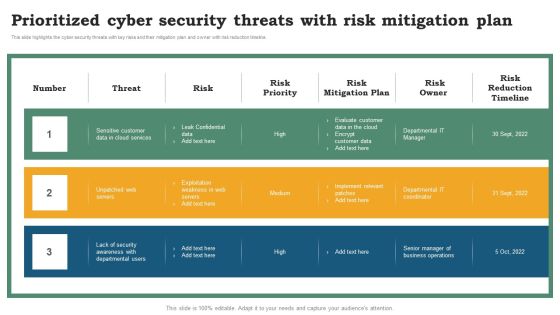
Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Explore a selection of the finest Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
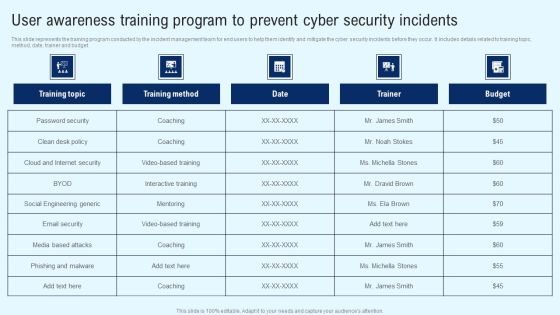
Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
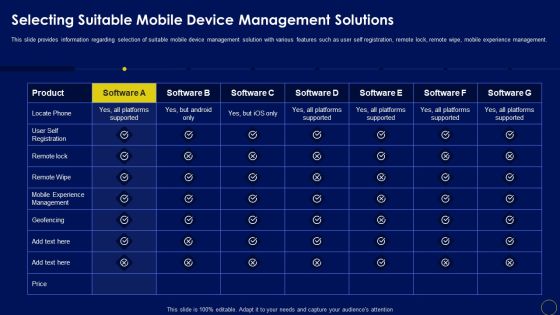
Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.

Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF
This slide showcases checklist for auditing transaction monitoring system. It provides information about scenarios, thresholds, client segmentation, rules, false positive, false negative, money laundering, transaction patterns, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Explore a selection of the finest Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

5 Investment Opportunities For Growth In Healthcare Sector Diagrams PDF
This slide highlights investment opportunities to foster growth in the healthcare sector. The purpose of growth in the healthcare sector is to achieve advancements, improve patient experience and generate financial returns for investors. These opportunities aim to develop innovative healthcare technologies and services to address needs and improve outcomes. It also provides benefits derived from each opportunity. Showcasing this set of slides titled 5 Investment Opportunities For Growth In Healthcare Sector Diagrams PDF. The topics addressed in these templates are Biotech And Pharmaceutical Innovations, Potential, Cyber Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Why Omnichannel Strategy Is Important In Banking Sector Ppt Styles Topics PDF
This slide covers top benefits of deploying omnichannel strategies in banking sector to enhance both financial and operational efficiencies. It includes points of importance such as digital operations, new revenue streams, personalized services and enhanced security. Explore a selection of the finest Why Omnichannel Strategy Is Important In Banking Sector Ppt Styles Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Why Omnichannel Strategy Is Important In Banking Sector Ppt Styles Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Overview Of Zero Trust Solution Categories Background PDF
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Boost your pitch with our creative Overview Of Zero Trust Solution Categories Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Evaluation Of Technologies And Vendors To Be Implemented Across Warehouse Facility Guidelines PDF
This slide presents a table for assessing the right automation technologies for warehouses and vendors that help in their maintenance. It includes a comparison of Cobots and autonomous mobile robots using criteria such as, functionality, scalability, integration, support and maintenance, cost, vendor reputation, implementation timeframe, and security. This Evaluation Of Technologies And Vendors To Be Implemented Across Warehouse Facility Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cost Saving Benefits Of Implementing Data Center Risks And Mitigation Strategies For Data Center Relocation Brochure PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cost Saving Benefits Of Implementing Data Center Risks And Mitigation Strategies For Data Center Relocation Brochure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

WAF Introduction Web Application Firewall Use Cases Topics PDF
This slide outlines the main application areas of web application firewall systems. The purpose of this slide is to showcase the various use cases of WAF, including patching vulnerabilities, complying with security and regulatory regulations, enforcing content policies, securing websites and applications, and so on. Presenting this PowerPoint presentation, titledWAF Introduction Web Application Firewall Use Cases Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting thisWAF Introduction Web Application Firewall Use Cases Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizableWAF Introduction Web Application Firewall Use Cases Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

IT Cost Reduction Strategies Determine Suitable IT Cost Optimization Solutions Summary PDF
This slide provides information regarding selection of suitable IT cost optimization solution by analyzing on various parameters such as optimizing hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Find highly impressive IT Cost Reduction Strategies Determine Suitable IT Cost Optimization Solutions Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IT Cost Reduction Strategies Determine Suitable IT Cost Optimization Solutions Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Elements Of Enterprise Risk Management Taxonomy Introduction To ERM Topics PDF
This slide represents the components of risk taxonomy to help key stakeholders to identify potential problems before they occur to effectively plan risk-handling activities. It includes details related to levels such as security and authentication, documentation, monitoring etc.Boost your pitch with our creative Elements Of Enterprise Risk Management Taxonomy Introduction To ERM Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

 Home
Home