Table Of Safety Contents

Corporate System Security Quality Assurance Matrix Demonstration PDF
This slide covers quality assurance for corporate system security. It includes a matrix based on functional and customer requirements for security system such as no access to restricted sites, email tracking, confidential data protection, etc. Showcasing this set of slides titled Corporate System Security Quality Assurance Matrix Demonstration PDF. The topics addressed in these templates are Customer Requirements, Functional Requirements, Centralised Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Security Architecture Training Program Guidelines PDF
The slide shows a training schedule overview for cloud security. It includes training of identify and assess management, compute and configuration management, data protection and automation, networking and logging, compliance, incident response and penetration testing and cloud wars. Showcasing this set of slides titled Cloud Computing Security Architecture Training Program Guidelines PDF. The topics addressed in these templates are Identify Access Management, Compute Configuration Management, Data Protection Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5 Kpis To Monitor And Track Network Service Assessment Information PDF
Mentioned slide outlines various kpis which can be used by IT reps to monitor network performance. The kpis mentioned in the template are latency, network jitter, packet loss, throughput and mean opinion score. It also covers information about objective, strategies implemented and actual performance of each kpis. Showcasing this set of slides titled 5 Kpis To Monitor And Track Network Service Assessment Information PDF. The topics addressed in these templates are Strategies Implemented, Network Security, Quality. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Threat Management Strategy With Strategies Ideas PDF
This slide focuses on the security risk mitigation plan which covers security components, vulnerabilities and mitigation strategies such as administrative, physical, technical and organizational safeguards with conducting workforce training, installing alarm systems, etc. Showcasing this set of slides titled Security Threat Management Strategy With Strategies Ideas PDF. The topics addressed in these templates are Security Component, Examples Of Vulnerabilities, Security Mitigation Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Crisis Management Communication Plan Microsoft PDF
This slide illustrates RACI Responsible, accountable, consulted, and informed chart of the cyber security crisis management communication plan. It includes elements such as authority, name, emergency contact etc. Showcasing this set of slides titled IT Security Crisis Management Communication Plan Microsoft PDF. The topics addressed in these templates are Chief Information Officers, Chief Information Security Officers, Crisis Management Lead Assistant. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
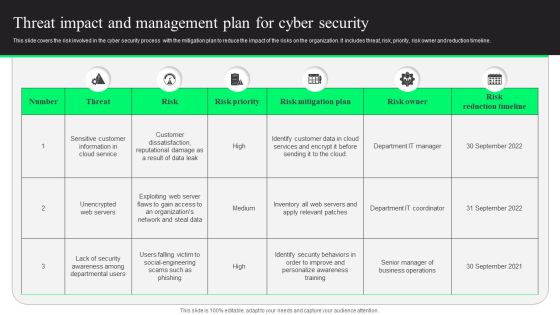
Threat Impact And Management Plan For Cyber Security Designs PDF
This slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Showcasing this set of slides titled Threat Impact And Management Plan For Cyber Security Designs PDF. The topics addressed in these templates are Risk Mitigation Plan, Risk Reduction Timeline, Customer Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Network Security Training Programs Timeline Download PDF
The slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package . Showcasing this set of slides titled Cloud Network Security Training Programs Timeline Download PDF. The topics addressed in these templates are Training Programs, Models Controls, Offense Defense Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Application Security Architecture Checklist Template PDF
The slide shows course of action for application security control and management. It includes understanding responsibility model, focusing on design andarchitect, testing, managing control, regulating and compliance needs, user training and monitoring and optimizing. Showcasing this set of slides titled Cloud Computing Application Security Architecture Checklist Template PDF. The topics addressed in these templates are Data Classification Accountability, Client Point Protection, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Impact And Probability Assessment Inspiration PDF
This slide defines the risk impact and likelihood assessment in cyber security. It includes information related to creating awareness in top management regarding technical, commercial, and branding damages deriving from suffering a cyber-attack. Showcasing this set of slides titled Cyber Security Risk Impact And Probability Assessment Inspiration PDF. The topics addressed in these templates are Business Continuity, Restoring Cost, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Conducting Cyber Security Gap Analysis Of Organization Formats PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Boost your pitch with our creative Conducting Cyber Security Gap Analysis Of Organization Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

IT Security Awareness Training Program Plan Ppt Show Tips PDF
This slide covers cybersecurity awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public wi-fi, phishing attacks, mobile device security and passwords and authentication. Showcasing this set of slides titled IT Security Awareness Training Program Plan Ppt Show Tips PDF. The topics addressed in these templates are Training Topic, Mode Of Training, Training Hours. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
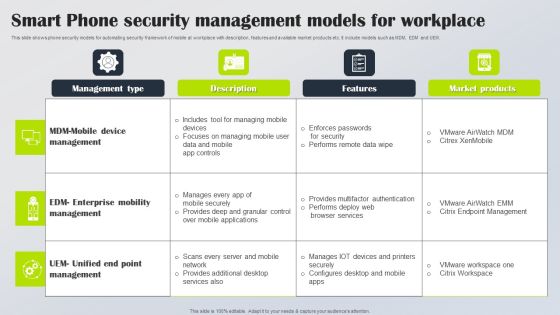
Smart Phone Security Management Models For Workplace Rules PDF
This slide shows phone security models for automating security framework of mobile at workplace with description, features and available market products etc. It include models such as MDM, EDM and UEM. Showcasing this set of slides titled Smart Phone Security Management Models For Workplace Rules PDF. The topics addressed in these templates are Management Type, Description, Features. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
RCA Plan For System Security Breach Icons PDF
This slide shows RCA format to address every activity in proper timeline for identifying potential risks and strategies to resolve same. It include elements such as event timeline, security breach activities and action plan, etc. Showcasing this set of slides titled RCA Plan For System Security Breach Icons PDF Diagrams Wd Introduction PDF Diagrams. The topics addressed in these templates are Event Timeline, Security Breach Activities, Action Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Role Of Management In Security Governance Across Firm Elements PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Boost your pitch with our creative Role Of Management In Security Governance Across Firm Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Addressing Performance Indicators To Determine Security Standards Introduction PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Boost your pitch with our creative Addressing Performance Indicators To Determine Security Standards Introduction PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Managing Cyber Security Incident Response Plan Checklist Ppt Picture PDF
This slide covers cyber security incident response plan checklist. It involves pre-requisites such as identify fundamentals, terms and contracts, identify phases, team communication plan and incident response forms. Showcasing this set of slides titled Managing Cyber Security Incident Response Plan Checklist Ppt Picture PDF. The topics addressed in these templates are Identify Fundamentals, Checklist, Terms And Contracts. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Assessment Control Measures Slides PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain likely possible unlikely and rare. Showcasing this set of slides titled Cyber Security Risk Assessment Control Measures Slides PDF. The topics addressed in these templates are Cyber Security Risk, Assessment Control Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Identification And Remediation Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain, likely, possible, unlikel, and rare. Showcasing this set of slides titled Cyber Security Risk Identification And Remediation Matrix Background PDF. The topics addressed in these templates are Cyber Security Risk Identification, Remediation Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Efficient Communication Technique In Cyber Security Mockup PDF
This slide shows communication certain strategies used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person, etc. Showcasing this set of slides titled Efficient Communication Technique In Cyber Security Mockup PDF. The topics addressed in these templates are Date, Communication Objectives, Activity, Mode Of Communication, Accountable Person. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Application Security Architecture Audit Checklist Structure PDF
The slide shows a checklist containing number of tasks needed to be done while performing application security audit. It includes tasks like developing password policies, making multi factor confirmation mandatory, supervising SaaS license, etc. Showcasing this set of slides titled Cloud Computing Application Security Architecture Audit Checklist Structure PDF. The topics addressed in these templates are Develop Password Policies, Validate Anti Attacking Protections, Set Message Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.

Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF
This slide shows worksheet representing comparison of insurance premium of different firms for insured or customer to help in making decision . it includes various facilities provided by insurance firms. Showcasing this set of slides titled Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF. The topics addressed in these templates are Purchase Price, Insurance, Medical Payments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
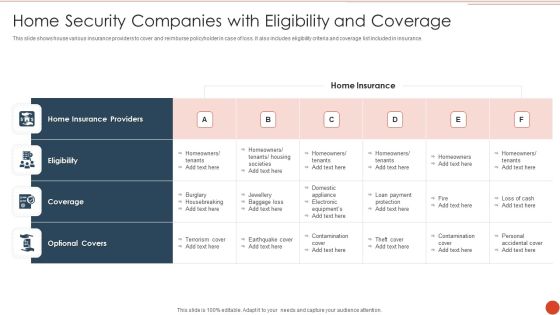
Home Security Companies With Eligibility And Coverage Infographics PDF
This slide shows house various insurance providers to cover and reimburse policyholder in case of loss. It also includes eligibility criteria and coverage list included in insurance. Showcasing this set of slides titled Home Security Companies With Eligibility And Coverage Infographics PDF. The topics addressed in these templates are Home Insurance Providers, Home Insurance, Loan Payment Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Challenges And Opportunities For Online Money Transfer Service Provider Ppt Professional Files PDF
The following slide highlights some major challenges and opportunities fund transfer service providers to grab the advantage. It includes elements such as low profit margin, reliability, security etc. Showcasing this set of slides titled Challenges And Opportunities For Online Money Transfer Service Provider Ppt Professional Files PDF. The topics addressed in these templates are Challenges, Opportunities, Traditional Providers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS
Following slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Showcasing this set of slides titled Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS. The topics addressed in these templates are Data Security Tools Evaluation, Data Security Tools Used, Budget Allocated For Tools, Data Security Software Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
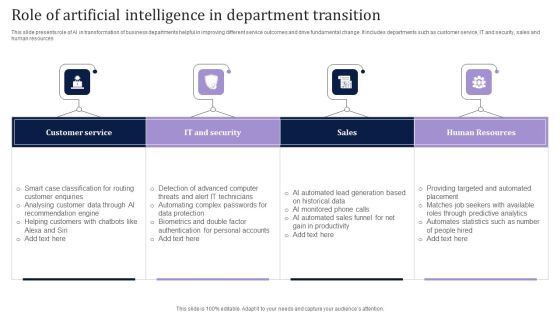
Role Of Artificial Intelligence In Department Transition Slides PDF
This slide presents role of AI in transformation of business departments helpful in improving different service outcomes and drive fundamental change. It includes departments such as customer service, IT and security, sales and human resources. Showcasing this set of slides titled Role Of Artificial Intelligence In Department Transition Slides PDF. The topics addressed in these templates are Customer Service, IT And Security, Sales. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks.Boost your pitch with our creative Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
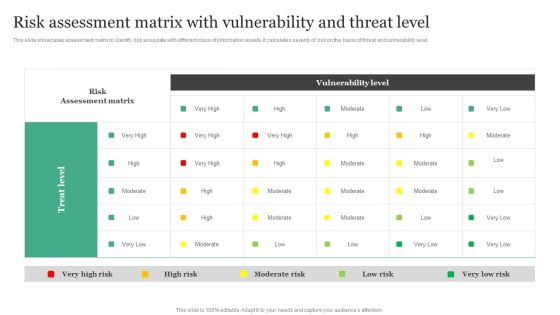
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
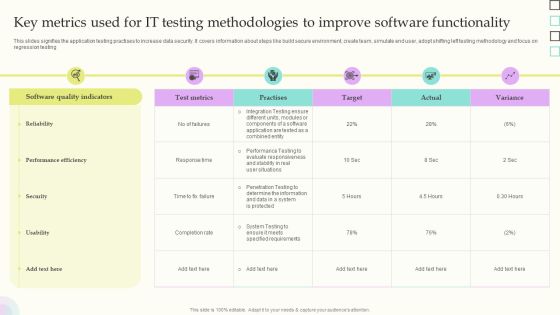
Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF
This slides signifies the application testing practises to increase data security. It covers information about steps like build secure environment, create team, simulate end user, adopt shifting left testing methodology and focus on regression testing. Showcasing this set of slides titled Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF. The topics addressed in these templates are Software Quality Indicators, Reliability, Performance Efficiency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF
This slide represents 3 year cyber security plan road map of a company for website enhancement and implementing security to operational work with specific standards. It consists security standards, training and awareness phishing users and sensitive data management. Showcasing this set of slides titled Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF. The topics addressed in these templates are Website Enhancement, Governance Subcommittee, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

4 Quarter Cyber Security Roadmap For Organization Ppt PowerPoint Presentation File Example Topics PDF
This slide covers quarterly roadmap showing evolution of cyber security in an organization with developing policies and risk assessment.It includes compliance and data backups. Showcasing this set of slides titled 4 Quarter Cyber Security Roadmap For Organization Ppt PowerPoint Presentation File Example Topics PDF. The topics addressed in these templates are Security And Compliance, Backups And DR, DR Policy Developed. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
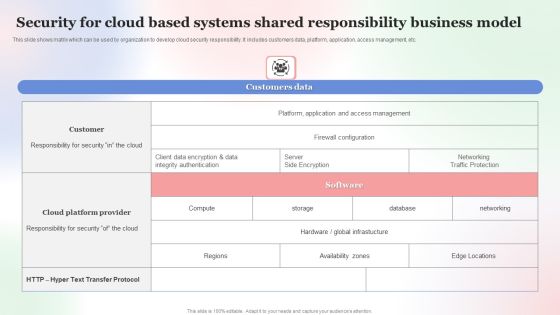
Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF
This slide shows matrix which can be used by organization to develop cloud security responsibility. It includes customers data, platform, application, access management, etc. Showcasing this set of slides titled Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF. The topics addressed in these templates are Security For Cloud Based, Systems Shared Responsibility, Business Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Smart Phone Security Techniques With Business Economy Level Brochure PDF
This slide shows various phone security techniques that can be adopted by an organization to prevent loss of business data and theft. It include techniques such as user authentication, one-time password and smartcard, etc. Showcasing this set of slides titled Key Smart Phone Security Techniques With Business Economy Level Brochure PDF. The topics addressed in these templates are Security Level, Usage, Economy Value. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF
This slide highlights scorecard related to security breaches in gaming field. The purpose of this template is to rate the incidents based on severity. It includes elements such as account taken over, personal details posting on web, spyware, data breaches and cyber bullying. Showcasing this set of slides titled Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF. The topics addressed in these templates are Incident, Score, Data Breaches, Low, High. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF
This slide covers cyber security incident response proposition. The purpose of this plan is to provide direction of action to the whole response team. It includes elements such as list of incidents, their responses, responsible person and resolve date. Showcasing this set of slides titled Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF. The topics addressed in these templates are Data Stealing Through, Network Monitoring, Server Crashing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Kpis To Measure Phishing Scams And Attacks Topics PDF
Mentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Showcasing this set of slides titled cyber security kpis to measure phishing scams and attacks topics pdf. The topics addressed in these templates are cyber security kpis to measure phishing scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF
This slide highlights security risks occurred in the company. The purpose of this template is to report the severity of security threats. It also includes action steps taken in prevention or resolution of security incidents along with risk categories. Showcasing this set of slides titled Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF. The topics addressed in these templates are Incidents, Category, Severity, Response Action Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Operations Certifications And Training Courses For IT Professionals Topics PDF
This slide exhibits training courses for security operations administrators to enhance their cyber threat management skills. It includes elements such as course, course outline, rating, pricing, frequency, and mode of training. Showcasing this set of slides titled Security Operations Certifications And Training Courses For IT Professionals Topics PDF. The topics addressed in these templates are Security Operations, Fundamental, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
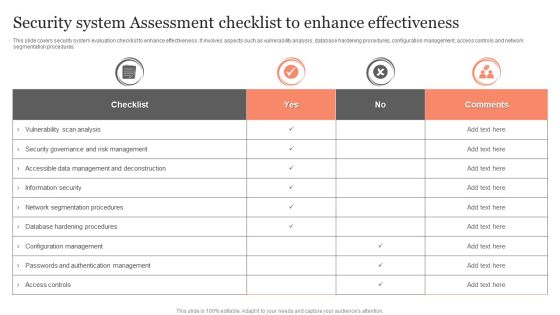
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF
The following slide illustrates some SaaS security threats to enhance security practices and eliminate them. It includes elements such as phishing, account takeovers, lack of transparency etc. Showcasing this set of slides titled Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF. The topics addressed in these templates are Comprehending Risks, Phishing, Account Takeovers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Analysis Of Various Security For Cloud Based Systems Tools Formats PDF
This slide shows comparison amongst various cloud security tools which can be used by the organization to select the best suitable tool. it also includes details about features, price and ratings. Showcasing this set of slides titled Comparative Analysis Of Various Security For Cloud Based Systems Tools Formats PDF. The topics addressed in these templates are Comparative Analysis, Various Security For Cloud, Based Systems Tools. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF
This slide illustrates list of best practices for API security testing to ensure it is thorough. It includes budget resources and time, define the test types to run, etc. Showcasing this set of slides titled Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF. The topics addressed in these templates are Application Programming, Interface Security, Testing Practices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF
This slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Showcasing this set of slides titled E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF. The topics addressed in these templates are Business Security Risks, Threat Type, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF
This slide shows the monthly project management timeline for website development which includes two teams such as UX and Backend team whose main tasks are system designing, getting approval from client, creating wireframes of pages, defining website policies, etc. Showcasing this set of slides titled Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF. The topics addressed in these templates are Staffing Resource Planning, Staff Recruiting, Architecture Planning. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF
This slide covers monthly cybersecurity awareness training program timeline. It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Showcasing this set of slides titled Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF. The topics addressed in these templates are Authentication And Passwords, Conduct Phishing Exercise, Remote Access Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF
The following slide showcases various tools to prevent cyber attacks. It comprises of tool name, period of free trial, its features and the estimated cost. Showcasing this set of slides titled Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF. The topics addressed in these templates are Free Trial, Cost, User Friendly, Highly Automated. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
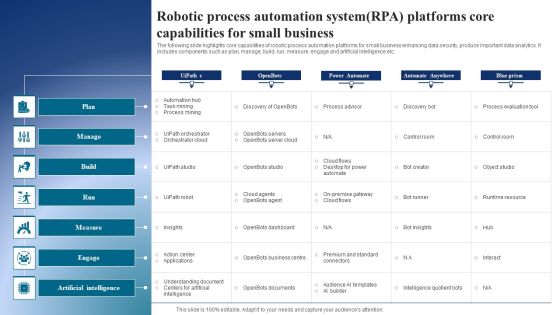
Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF
The following slide highlights core capabilities of robotic process automation platforms for small business enhancing data security, produce important data analytics. It includes components such as plan, manage, build, run, measure, engage and artificial intelligence etc. Showcasing this set of slides titled Robotic Process Automation Systemrpa Platforms Core Capabilities For Small Business Structure PDF. The topics addressed in these templates are Plan, Manage, Build . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Boost your pitch with our creative IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Best Practices For Optimizing Unstructured Data Implementation Ideas PDF
This slide describe the key practices to optimize the use of structured data for business sites. It covers practices such as effective management of unstructured data, plan for ongoing data mobility and enable secure data self-service. Showcasing this set of slides titled Best Practices For Optimizing Unstructured Data Implementation Ideas PDF. The topics addressed in these templates are Best Practices, Implementations, Responsible Owner, Additional Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparison Of Various Cyber Protection Software Portrait PDF
This slide shows comparative analysis of various cyber protection tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Comparison Of Various Cyber Protection Software Portrait PDF. This layout presents information on Compatibility, Price, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Layer Based Integrate IOT Blockchain Platform Architecture Microsoft PDF
This slide covers multiple layers of architectural system based on IoT blockchain platforms. It includes layers such as application, connectivity, IoT physical layers and service layers comprising of device management, data visualization, big data analytics, consensus management, distributed ledger, smart contracts, API interface, message broker, security management, etc. Showcasing this set of slides titled Layer Based Integrate IOT Blockchain Platform Architecture Microsoft PDF. The topics addressed in these templates are Application Layer, Connectivity Layers, IOT Physical Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roadmap For Business Transition Strategic Management Plan Diagrams PDF
This slide illustrates business transition strategic plan timeline for smooth changes in business operations. It includes cut to core services, creating simpler core operations and innovate with new alliances etc. Showcasing this set of slides titled Roadmap For Business Transition Strategic Management Plan Diagrams PDF. The topics addressed in these templates are Secure Important Features, Creating Simpler Services, Customer Focused. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Consumer Demand Survey Sheet With Classifications Topics PDF
This slide showcases customer requirements survey sheet with classifications. It includes details about schedule management, costs, quality, safety, Attractive, must be, indifferent, etc. Pitch your topic with ease and precision using this Consumer Demand Survey Sheet With Classifications Topics PDF. This layout presents information on Customer, Environmental, Quality. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home