Table Of Safety Contents

Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Slidegeeks has constructed Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Slidegeeks has constructed Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF
The slide showcases the key difference between cyber security and cyber resilience. It compares on the basis of aspects like definition, focus, function and requirement. Showcasing this set of slides titled Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF. The topics addressed in these templates are Cyber Security, Cyber Resilience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Framework For Improving Critical Infra Cyber Security Icons PDF
The following slide exhibits framework for protection, resilience of infrastructure and other sectors important to national security. It presents information related to protection, responding, etc. Showcasing this set of slides titled Framework For Improving Critical Infra Cyber Security Icons PDF. The topics addressed in these templates are Identify, Protect, Detect. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risk Security Company Users And Protection Introduction PDF
The following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Showcasing this set of slides titled cyber risk security company users and protection introduction pdf. The topics addressed in these templates are company, users, protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Business Communication Strategies Plan Background PDF
This slide shows communication strategy plan used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person etc. Showcasing this set of slides titled Cyber Security Business Communication Strategies Plan Background PDF. The topics addressed in these templates are Communication Objective, Activity, Mode Communication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Bring Your Own Device Security Policy Compliance Framework Ideas PDF
This slide showcases the security policy compliance framework for bring your own device policy. It also includes four phases such as background study, empirical study, etc. Showcasing this set of slides titled Bring Your Own Device Security Policy Compliance Framework Ideas PDF. The topics addressed in these templates are Phases, Background Study, Empirical Study . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
RCA Action Plan For Business Cyber Security Icons PDF
This slide shows root cause analysis action plan to identify and provide strategies for overcoming cyber security threats. It include root cause, action plan and outcomes, etc. Showcasing this set of slides titled RCA Action Plan For Business Cyber Security Icons PDF Elements. The topics addressed in these templates are Root Cause, Action Plan, Outcomes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
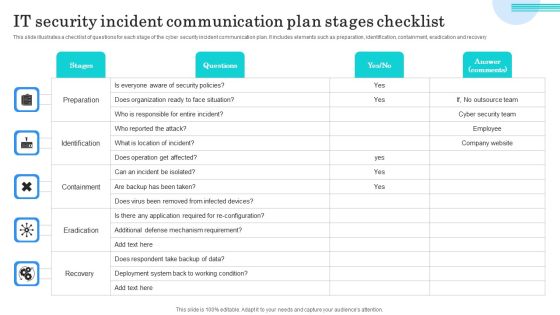
IT Security Incident Communication Plan Stages Checklist Topics PDF
This slide illustrates a checklist of questions for each stage of the cyber security incident communication plan. It includes elements such as preparation, identification, containment, eradication and recovery. Showcasing this set of slides titled IT Security Incident Communication Plan Stages Checklist Topics PDF. The topics addressed in these templates are Preparation, Identification, Containment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.

Cyber Risk Approaches For Security Protection Structure PDF
The following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Showcasing this set of slides titled cyber risk approaches for security protection structure pdf. The topics addressed in these templates are traditional approach, ai based approach, cybersecurity threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF
This slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Showcasing this set of slides titled Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF. The topics addressed in these templates are Threat, Risk, Risk Priority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF.

Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF.

Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
This slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF.

Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Slidegeeks has constructed Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF
The following slide illustrates real time onboarding, processing an monitoring. It provides information about threshold, net banking, risk level, ATM transaction, e-wallets, large transactions, know your customer KYC, etc. Slidegeeks has constructed KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Competitive Landscape Mobile App Pitch Deck Ppt File Layout PDF
Following slide differentiates the offering of company with its competitors based on different features namely secure login, scan barcodes, customer support and popup notifications. Deliver an awe inspiring pitch with this creative competitive landscape mobile app pitch deck ppt file layout pdf bundle. Topics like secure login, scan barcodes, customer support, popup notifications, location based services, offline access to content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Analysis Between Public And Private Cloud Administration System Sample PDF
This slide showcases distinguish between public and private cloud management platforms based on various basis. It also includes development testing, training services, environment security, flexibility, etc. Showcasing this set of slides titled Comparative Analysis Between Public And Private Cloud Administration System Sample PDF. The topics addressed in these templates are Storage Location, Security, Flexibility. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Data Audit Report With Description Ppt PowerPoint Presentation Inspiration Example PDF
Showcasing this set of slides titled security data audit report with description ppt powerpoint presentation inspiration example pdf. The topics addressed in these templates are attribute, description, audit status, comments, data backup, data and application management, data disaster recovery system integration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF
The following slide showcases comparison of email security gateways along with features rating and price. Main gateways included are mimecast, ironscales, avanan and trustifi. Showcasing this set of slides titled Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF. The topics addressed in these templates are Gateway Device Establishment, Establish Strong, Identity For Gateway. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Developing Supplier Risk Assessment Grid To Enhance Cyber Security Structure PDF
This slide signifies the matrix on vendor risk assessment to improve company cyber security. It includes description, rating and strategies implemented for countering thread Showcasing this set of slides titled Developing Supplier Risk Assessment Grid To Enhance Cyber Security Structure PDF. The topics addressed in these templates are Areas, Industry Factors, Supply Chain. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Communication Plan For Insider Threat In Cyber Security Awareness Background PDF
This slide shows insider threat awareness communication plan. It provides information about discussions, description, frequency, communication method, etc. Showcasing this set of slides titled Communication Plan For Insider Threat In Cyber Security Awareness Background PDF. The topics addressed in these templates are Discussions, Threat Prevention, Industrial News. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF
This slide defines the web tools to prevent from cyber attacks. It includes information related to different softwares, features and description. Showcasing this set of slides titled Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF. The topics addressed in these templates are Software Tools, Solarwinds Identity Monitor, Free Tool. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organization Project Transition Plan For Commercialization Elements PDF
This slide covers project transition plan which includes technical security, portfolio program project, service, commercialization of project. Showcasing this set of slides titled Organization Project Transition Plan For Commercialization Elements PDF. The topics addressed in these templates are Portfolio Programmer Project, Service, Commercial, Organizational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

ESO System Center System Ppt PowerPoint Presentation File Portrait PDF
This slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Showcasing this set of slides titled ESO System Center System Ppt PowerPoint Presentation File Portrait PDF. The topics addressed in these templates are Security Risks, Business Security, Data Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
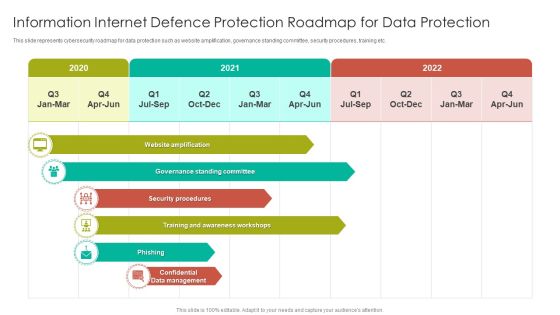
Information Internet Defence Protection Roadmap For Data Protection Topics PDF
This slide represents cybersecurity roadmap for data protection such as website amplification, governance standing committee, security procedures, training etc. Showcasing this set of slides titled Information Internet Defence Protection Roadmap For Data Protection Topics PDF. The topics addressed in these templates are Governance Standing, Security Procedures, Awareness Workshops. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting

IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF
This slide covers IT OT cyber security Team responsibilities including security department, security functions etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF.

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

WAF Features And Capabilities Ppt Pictures Designs Download PDF
This slide represents the capabilities and characteristics of a Web Application Firewall security solution. This slide aims to showcase the various features of WAF, including AI-powered traffic patterns, attack signature databases, application profiling, customization, correlation engines, and so on. Slidegeeks has constructed WAF Features And Capabilities Ppt Pictures Designs Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Solution Assessment Analysis With Multiple Options Sample PDF
This slide showcases numerous alternatives considered by organization to choose the best and suitable one as per firms requirement. It includes, budget, promotion techniques, processes, data security and financial investment. Showcasing this set of slides titled Solution Assessment Analysis With Multiple Options Sample PDF. The topics addressed in these templates are Budget, Manufacturing, Promotion Techniques. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Summary Of Audit And Review Team Findings By Severity Download PDF
This slide summarizes inspection findings by severity of an organization by audit team. It includes findings like attack surface, account security, hardened system, patching etc.Showcasing this set of slides titled Summary Of Audit And Review Team Findings By Severity Download PDF. The topics addressed in these templates are System Hardening, Data Protection, Account Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

3 Years Application Software Development Plan And Launch Timeline Themes PDF
This slide covers the action plan for application development. It include information about infrastructure, features, tools, application security along with user experience. Showcasing this set of slides titled 3 Years Application Software Development Plan And Launch Timeline Themes PDF. The topics addressed in these templates are Security, Enhancement, Internal Tools Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
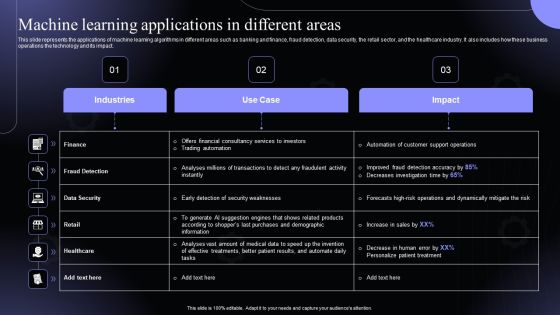
Machine Learning Applications In Different Areas Hyperautomation Software Solutions IT Designs PDF
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact.Slidegeeks has constructed Machine Learning Applications In Different Areas Hyperautomation Software Solutions IT Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Emerging Technology Trends For Business Growth Diagrams PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Emerging Technology Trends For Business Growth Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Emerging Technology Trends For Business Growth Diagrams PDF.

Four Month Project Timeline Swimlane Timeline Guidelines PDF
This slide represents four month project scheduling swimlane timeline illustrating departments and there tasks such as team members, technology , security, resource allocation, employee staffing etc. Showcasing this set of slides titled four month project timeline swimlane timeline guidelines pdf. The topics addressed in these templates are security, technology, team members. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Evaluation For Venture Debt Funding And Traditional Bank Loan Portrait PDF
This slide represents comparative evaluation for venture debt financing and traditional bank loan illustrating security, warrants and interest rates. Showcasing this set of slides titled comparative evaluation for venture debt funding and traditional bank loan portrait pdf. The topics addressed in these templates are security, warrants, interest rates. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Loss Prevention Checklist To Minimize Inventory Shrinkage Elements PDF
Following slide illustrates an effective checklist used for loss prevention in the retail sector. The checklist covers key points such as physical security, cash handling, product and staff. Showcasing this set of slides titled Loss Prevention Checklist To Minimize Inventory Shrinkage Elements PDF. The topics addressed in these templates are Physical Security, Product, Functioning Alarm System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Standard Computing Vs Modern Based Erp Software Download PDF
This slide illustrates the difference between standard ERP software and cloud based software. The key attributes include hosting procedure, security, pricing, and performance. Showcasing this set of slides titled Standard Computing Vs Modern Based Erp Software Download PDF. The topics addressed in these templates are Security, Pricing, Performance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Attributes Of Mezzanine Financing Capital Structure Graphics PDF
This slide covers features of different mezzanine finance debts. It includes categories such as preferred and common equity, subordinated debt along with senior secured debt. Showcasing this set of slides titled Key Attributes Of Mezzanine Financing Capital Structure Graphics PDF. The topics addressed in these templates are Common Equity, Subordinated Debt, Senior Secured Debt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
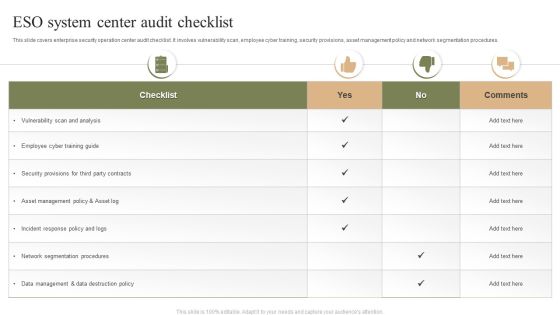
ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Showcasing this set of slides titled ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF. The topics addressed in these templates are Checklist, Employee Cyber, Training Guide. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Limitations And Solution In Using Online Certificate Ppt Icon Show PDF
This slide showcases the challenges faced in using and managing the digital certificate. It includes limitations such as security, slow performance, integration and management. Showcasing this set of slides titled Limitations And Solution In Using Online Certificate Ppt Icon Show PDF. The topics addressed in these templates are Security, Slow Performance, Integration, Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF
This slide covers the strategies to overcome network complexities and increase reliability, enhanced user experience, increasing efficiency and high security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Formats PDF.
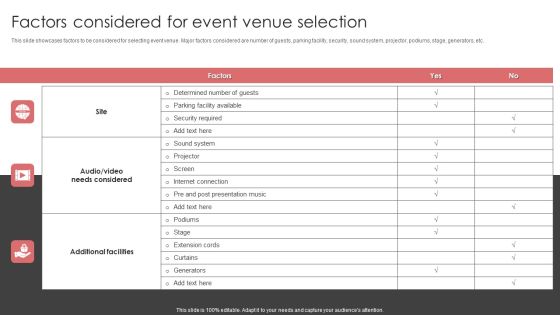
New Product Launch Event Management Activities Factors Considered For Event Venue Selection Diagrams PDF
This slide showcases factors to be considered for selecting event venue. Major factors considered are number of guests, parking facility, security, sound system, projector, podiums, stage, generators, etc.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our New Product Launch Event Management Activities Factors Considered For Event Venue Selection Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into New Product Launch Event Management Activities Factors Considered For Event Venue Selection Diagrams PDF.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF

New Website Launch Strategy Major Bottlenecks Faced In Launching New Business Website Topics PDF
Following slide outline major challenges faced by businesses in new website launch which can lead to decreased business performance. It includes challenges such as poor website design, low quality content, security issues, unoptimized SEO, and website non monitoring. Boost your pitch with our creative New Website Launch Strategy Major Bottlenecks Faced In Launching New Business Website Topics PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

WAF Introduction Comparison Between Blocklist And Allowlist WAF Rules PDF
This slide outlines the difference between blocklist and allowlist web application firewall. The purpose of this slide is to highlight the key differences between negative and positive security models of web application firewalls. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our WAF Introduction Comparison Between Blocklist And Allowlist WAF Rules PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into WAF Introduction Comparison Between Blocklist And Allowlist WAF Rules PDF
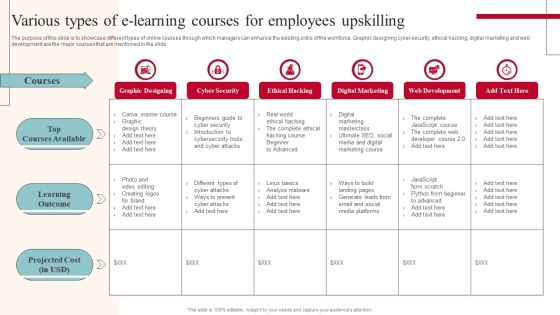
Various Types Of E Learning Courses For Employees Upskilling Ideas PDF
The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide. Slidegeeks has constructed Various Types Of E Learning Courses For Employees Upskilling Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
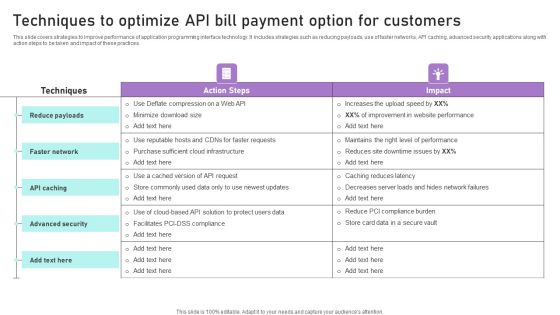
Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Techniques To Optimize API Bill Payment Option For Customers Ppt Infographics Example PDF.

Top Zero Trust Network Access Software Solutions Microsoft PDF
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Top Zero Trust Network Access Software Solutions Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Top Zero Trust Network Access Software Solutions Microsoft PDF.

Aligning Business Information Protection Program Action Structure PDF
This slide covers aligning business security program action which includes direct product evaluation participation and impact analysis.Showcasing this set of slides titled Aligning Business Information Protection Program Action Structure PDF. The topics addressed in these templates are Setting Priorities, Assets Stakeholders, Decision Making. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
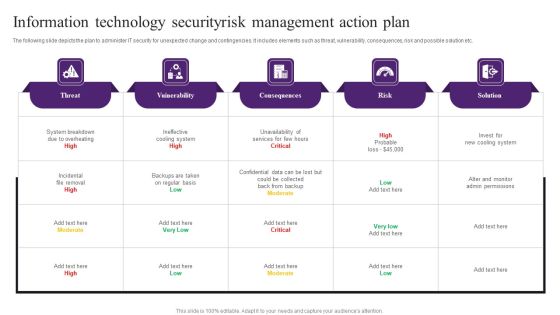
Information Technology Securityrisk Management Action Plan Themes PDF
The following slide depicts the plan to administer IT security for unexpected change and contingencies. It includes elements such as threat, vulnerability, consequences, risk and possible solution etc. Showcasing this set of slides titled Information Technology Securityrisk Management Action Plan Themes PDF. The topics addressed in these templates are Consequences, Vuinerability, System Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Home Security Proposal Form For Insured Elements PDF
The following slide includes proposal form of home insurance for the insured to fulfil the purpose of cover and reimbursement from company against any loss. It includes agents name, number and personal details of proposer. Showcasing this set of slides titled Home Security Proposal Form For Insured Elements PDF. The topics addressed in these templates are Home Security, Proposal Form Insured. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparison Of Digitization Of Security Systems Service Packages Information PDF
The following slide highlights multiple digitization of security systems services which are offered by third party to an organization. Information covered in this slide is related to features of each service such as incidents, bot action, integrations, custom integration, custom playbooks, reports etc. Showcasing this set of slides titled Comparison Of Digitization Of Security Systems Service Packages Information PDF. The topics addressed in these templates are Key Features, Custom Integration, Custom Playbooks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Software Glitch Tracking Status Download PDF
This slide represents reason of defects with their weightage in software testing. It include factors such as design issue, security flaws, document issue, code related issue etc. Showcasing this set of slides titled Business Software Glitch Tracking Status Download PDF. The topics addressed in these templates are Requirements Misinterpretation, Architecture Design Issues, Code Related Issue . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home