Table Of Safety Contents

Artificial Intelligence Security Issues And Solutions Analysis Topics PDF
The purpose of this template is to provide details of artificial intelligence AI security analysis based on the challenges faced and solutions available. It covers different applications used in AI for maintaining security and privacy. Pitch your topic with ease and precision using this Artificial Intelligence Security Issues And Solutions Analysis Topics PDF. This layout presents information on Applications, Autonomous Systems, Wireless. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward How Management Enables Effective Corporate Security Governance Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal How Management Enables Effective Corporate Security Governance Topics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF
The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. This modern and well arranged KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
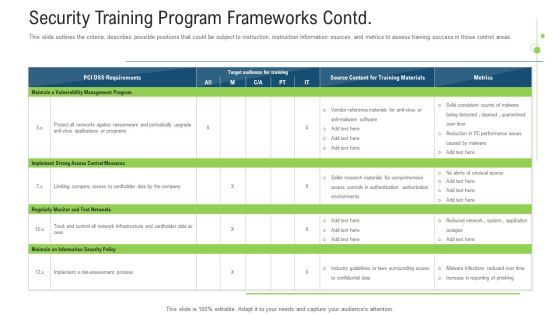
Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Make sure to capture your audiences attention in your business displays with our gratis customizable Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. The Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Determine Focus Areas To Implement Security Operations Centre Diagrams PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. Deliver an awe inspiring pitch with this creative determine focus areas to implement security operations centre diagrams pdf bundle. Topics like digital forensics and control, risk monitoring and management, system and network administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF
The purpose of this slide is to highlight the security gap analysis of the organization. Information covered in this slide is related to current vs desired state of the company, reasons identified, techniques to be used and the priority level.Deliver an awe inspiring pitch with this creative Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF bundle. Topics like Facing Ransomware, Reasons Identified, Organization Malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Cyber Security Breach Lost Revenue Portrait PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an awe inspiring pitch with this creative Impact Of Cyber Security Breach Lost Revenue Portrait PDF bundle. Topics like Social Engineering, Password Attack, Ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
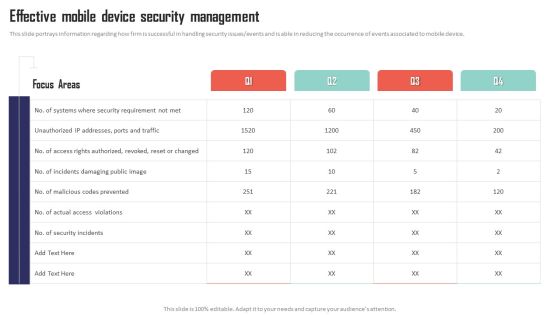
Mobile Device Management Effective Mobile Device Security Management Formats PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Want to ace your presentation in front of a live audience Our Mobile Device Management Effective Mobile Device Security Management Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

How Management Enables Effective Corporate Security Governance Graphics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. This modern and well-arranged How Management Enables Effective Corporate Security Governance Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Budget Analysis For Effective Security Management At Workplace Demonstration PDF
Firm has prepared a budget for managing security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Budget Analysis For Effective Security Management At Workplace Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Security Qualitative Risk Analysis Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management. This is categorized as certain, likely, possible, unlikely, and rare. Pitch your topic with ease and precision using this Cyber Security Qualitative Risk Analysis Matrix Background PDF. This layout presents information on Risk Matrix, High Severity, Cyber Security Qualitative. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
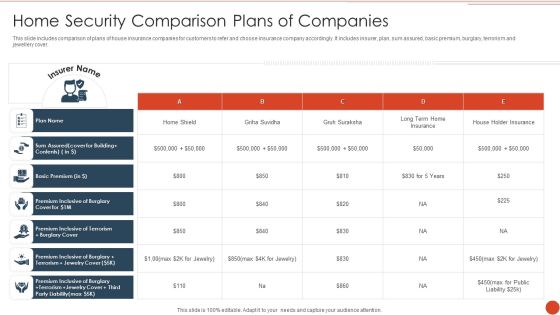
Home Security Comparison Plans Of Companies Formats PDF
This slide includes comparison of plans of house insurance companies for customers to refer and choose insurance company accordingly. It includes insurer, plan, sum assured, basic premium, burglary, terrorism and jewellery cover. Pitch your topic with ease and precision using this Home Security Comparison Plans Of Companies Formats PDF. This layout presents information on Basic Premium, Plan Name, House Holder Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Competitor Analysis Grid Of Security Software Inspiration PDF
This slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Pitch your topic with ease and precision using this Competitor Analysis Grid Of Security Software Inspiration PDF. This layout presents information on System Cleansing, Everyday Backup Option, Anti Spyware. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
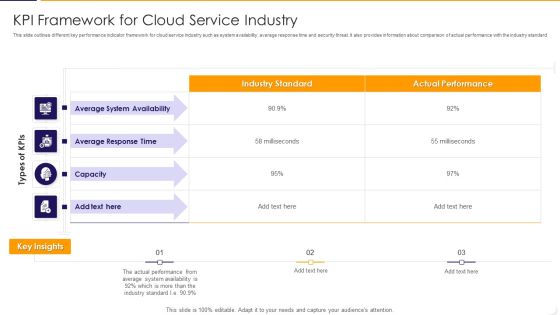
KPI Framework For Cloud Service Industry Ppt PowerPoint Presentation Gallery Styles PDF
This slide outlines different key performance indicator framework for cloud service industry such as system availability, average response time and security threat. It also provides information about comparison of actual performance with the industry standard. Pitch your topic with ease and precision using this kpi framework for cloud service industry ppt powerpoint presentation gallery styles pdf This layout presents information on average, performance, system It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Ways Through Which Security Clipart PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks ways through which security clipart pdf bundle. Topics like attack description, ways to mitigate attack, external attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Budget For Information Topics PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver and pitch your topic in the best possible manner with this effective it risk management process budget for information topics pdf. Use them to share invaluable insights on incident management, risk management, asset management, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Project Budget Evaluation Plan Pictures PDF
This slide signifies the project key performance indicator dashboard to evaluate financial budget evaluation. It covers information regarding to allocated and used budget. Pitch your topic with ease and precision using this Information Technology Project Budget Evaluation Plan Pictures PDF. This layout presents information on Develop Risk Assessment Report, Environment, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Global Information Technology Development Timeline Ppt Designs PDF
This slide represents quarterly roadmap for global information technology development illustrating operations, infrastructure, compliance and security etc. Pitch your topic with ease and precision using this Global Information Technology Development Timeline Ppt Designs PDF. This layout presents information on Departmental Auditing, Application Compatibility, Departmental Quality Assurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Accountability And Responsibility Of The Employees Information PDF
This slide covers the RACI matrix of an organization based on different departments such as facilities, plant, HR, security, project, etc.Deliver and pitch your topic in the best possible manner with this Accountability And Responsibility Of The Employees Information PDF. Use them to share invaluable insights on Identify A Minimum, Review Quotes Contractor Selection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF
This slide covers classification of cyber security events of financial organizations. The purpose of this classification is to identify events which needs immediate response. It includes elements such as severity level, cyber incidents, occurrence pattern, performance impact, data breach and financial costs Pitch your topic with ease and precision using this Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF. This layout presents information on Severity Level, Cyber Incidents, Occurrence Pattern, Performance Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
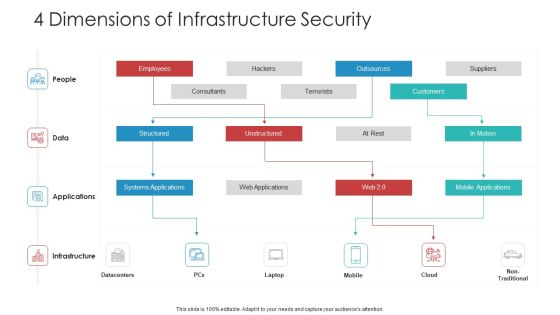
Landscape Architecture Planning And Management 4 Dimensions Of Infrastructure Security Sample PDF
Deliver an awe inspiring pitch with this creative landscape architecture planning and management 4 dimensions of infrastructure security sample pdf bundle. Topics like people, data, applications, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF
The slide showcases the steps for building efficient cyber resiliency across organization. It covers steps like secure remote working enablement, develop a comprehensive response plan, build a cyber security improvement roadmap, build detection and response capability and educating users on escalating threats. Pitch your topic with ease and precision using this Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF. This layout presents information on Objective, Initiatives, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Technology Facility Maintenance And Provider IT Service Maintenance Checklist Ppt Model Background Image PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this technology facility maintenance and provider IT service maintenance checklist ppt model background image pdf. Use them to share invaluable insights on planning meeting, preventive maintenance, security patches executive reporting, activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

What Are The Benefits Of A Cloud Security System Background PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. Deliver an awe inspiring pitch with this creative What Are The Benefits Of A Cloud Security System Background PDF bundle. Topics like Openness, Efficient Recovery, No Hardware Required can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
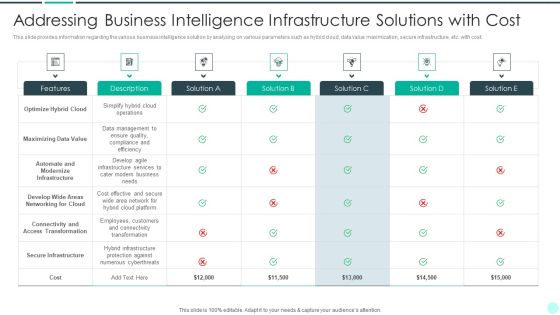
Executing Advance Data Analytics At Workspace Addressing Business Intelligence Formats PDF
This slide provides information regarding the various business intelligence solution by analyzing on various parameters such as hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace addressing business intelligence formats pdf. Use them to share invaluable insights on addressing business intelligence infrastructure solutions with cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
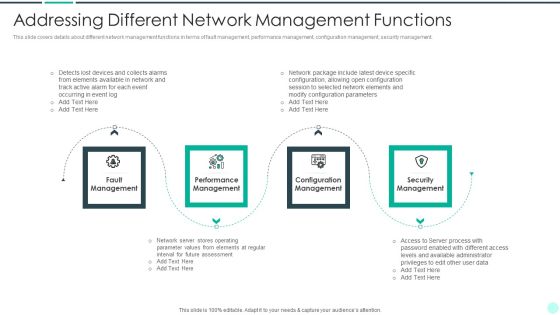
Executing Advance Data Analytics At Workspace Addressing Different Network Clipart PDF
This slide provides information regarding the various business intelligence solution by analyzing on various parameters such as hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace addressing different network clipart pdf. Use them to share invaluable insights on addressing business intelligence infrastructure solutions with cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Checklist Of Mandatory Documents Required For ISO 27001 Certification Structure PDF
Following slide displays checklist of mandatory documents required to get ISO 27001 certification along with the status. Deliver an awe inspiring pitch with this creative Checklist Of Mandatory Documents Required For ISO 27001 Certification Structure PDF bundle. Topics like Mandatory Documents, Information Security, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan System Management Checklist With Key Activities Structure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative cyber security risk management plan system management checklist with key activities structure pdf bundle. Topics like system monitoring, data backup, security patches, virus scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Deliver and pitch your topic in the best possible manner with this Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF. Use them to share invaluable insights on Risks, Current Value, Risk Level and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
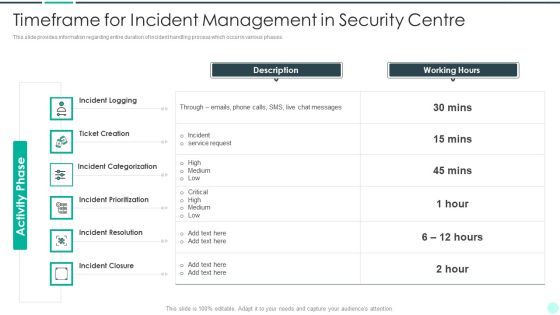
Executing Advance Data Analytics At Workspace Timeframe For Incident Management Download PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace timeframe for incident management download pdf. Use them to share invaluable insights on timeframe for incident management in security centre and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Advance Data Analytics At Workspace Addressing Business Intelligence Background PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative executing advance data analytics at workspace addressing business intelligence background pdf bundle. Topics like contingency plan for threat handling in security centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Checklist Of Mandatory Documents Required For ISO 27001 Certification Topics PDF
Following slide displays checklist of mandatory documents required to get ISO 27001 certification along with the status. Deliver an awe inspiring pitch with this creative Checklist Of Mandatory Documents Required For ISO 27001 Certification Topics PDF bundle. Topics like Information Security, Statement Of Applicability, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
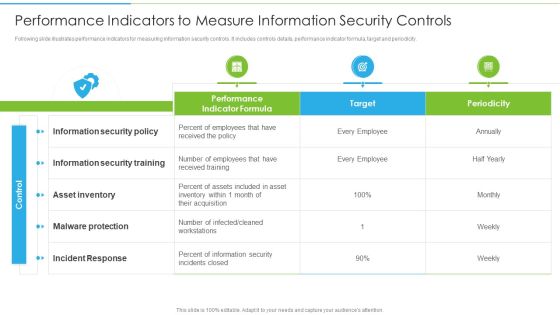
Ways To Accomplish ISO 27001 Accreditation Performance Indicators To Measure Information Summary PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Performance Indicators To Measure Information Summary PDF bundle. Topics like Information Security, Asset Inventory, Malware Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
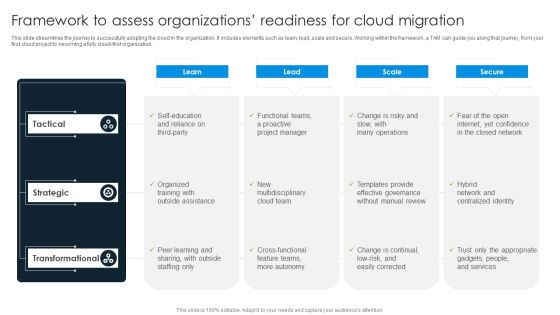
Framework To Assess Organizations Readiness For Cloud Migration Information PDF
This slide streamlines the journey to successfully adopting the cloud in the organization. It includes elements such as learn, lead, scale and secure. Working within the framework, a TAM can guide you along that journey, from your first cloud project to becoming a fully cloud-first organization. Pitch your topic with ease and precision using this Framework To Assess Organizations Readiness For Cloud Migration Information PDF. This layout presents information on Tactical, Strategic, Transformational. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Strategies To Mitigate Cyber Security Risks Dashboard Incident Tracking Ppt Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard incident tracking ppt model pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, disable untrusted microsoft office macros, user application hardening, multi factor authentication, daily backup important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Comparative Assessment Of Various Threat Agents Slides PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management comparative assessment of various threat agents slides pdf. Use them to share invaluable insights on comparative assessment of various threat agents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Security Assessment Matrix Of Cyber Risks Ppt PowerPoint Presentation Icon Styles PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative info security assessment matrix of cyber risks ppt powerpoint presentation icon styles pdf bundle. Topics like employee devices, webserver network, cloud, retail, data center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF bundle. Topics like Risks Description, Technology, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Analysis For Effective Threat Management In Securing Workplace Professional PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Impact Analysis For Effective Threat Management In Securing Workplace Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF
This slide outlines the recommended steps for successfully integrating SecOps into an organization. The purpose of this slide is to showcase the best practices for implementing security operations in an organization. The main steps include performing formal SecOps training, avoiding potential pitfalls and offering practical SecOps tools. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. The Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
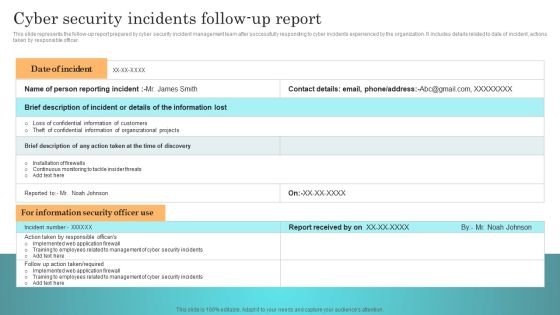
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
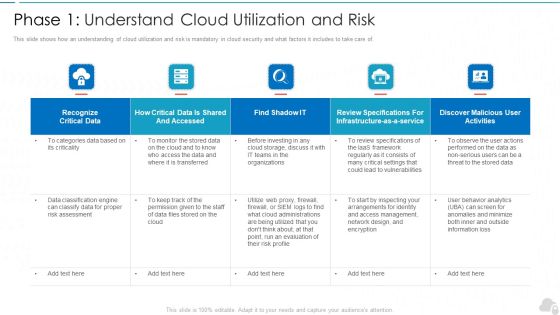
Phase 1 Understand Cloud Utilization And Risk Cloud Computing Security IT Ppt Summary Smartart PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this phase 1 understand cloud utilization and risk cloud computing security it ppt summary smartart pdf. Use them to share invaluable insights on recognize critical data, infrastructure, evaluation, vulnerabilities, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Role Of ZTNA To Improve Business Operations And Security Slides PDF
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. There are so many reasons you need a Role Of ZTNA To Improve Business Operations And Security Slides PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Capability Model For Strategy Architecture And Governance Clipart PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services.Are you searching for a Cloud Capability Model For Strategy Architecture And Governance Clipart PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cloud Capability Model For Strategy Architecture And Governance Clipart PDF from Slidegeeks today.
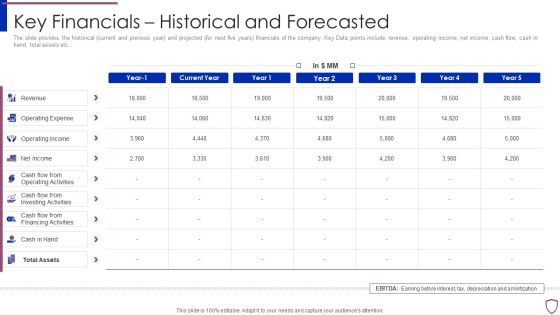
Financing Catalogue For Security Underwriting Agreement Key Financials Historical And Forecasted Template PDF
The slide provides the historical current and previous year and projected for next five years financials of the company. Key Data points include revenue, operating income, net income, cash flow, cash in hand, total assets etc. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement key financials historical and forecasted template pdf bundle. Topics like revenue, operating expense, operating income, net income, cash flow from operating activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
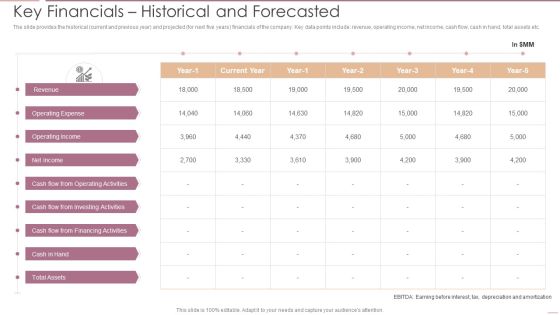
Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF
The slide provides the historical current and previous year and projected for next five year financials of the company. Key data points include revenue, operating income, net income, cash flow, cash in hand, total assets etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF bundle. Topics like Operating Expense, Operating Income, Operating Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Matrix To Select Suitable Vendor Microsoft PDF
This slide shows comparison matrix which can be used by organizations to compare vendors. It includes various metrics demand handling capabilities, customer services, price per unit, data security level, etc. Pitch your topic with ease and precision using this Comparative Matrix To Select Suitable Vendor Microsoft PDF. This layout presents information on Select Suitable, Vendor. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home