Table Of Safety Contents

Role Of Management In Effective Information Security Governance Rules PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Role Of Management In Effective Information Security Governance Rules PDF bundle. Topics like Senior Executives, Steering Committees, Chief Information Security Officer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF bundle. Topics like Virtualization Threats, Information Interception, Unauthorized Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
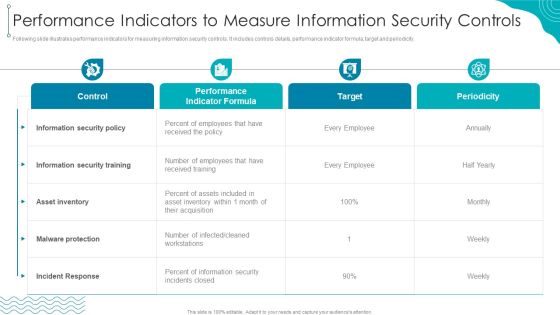
Performance Indicators To Measure Information Security Controls Designs PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity.Deliver an awe inspiring pitch with this creative Performance Indicators To Measure Information Security Controls Designs PDF bundle. Topics like Information security, received training, Incident Response can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Certified Information Systems Security Professional Cissp Details Pictures PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications.Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional Cissp Details Pictures PDF bundle. Topics like Security Specialist, Certified Information, Certifying Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF bundle. Topics like Information Security Controls, Controls, Security Policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.
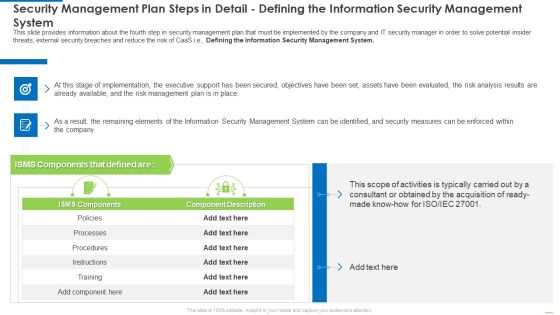
Security Management Plan Steps In Detail Defining The Information Security Management System Diagrams PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system diagrams pdf bundle. Topics like security management plan steps in detail - defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security And Governance Management Framework Elements PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. This Information Security And Governance Management Framework Elements PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security And Governance Management Framework Elements PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Mockup PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system mockup pdf. Use them to share invaluable insights on implementation, management plan, security management, security measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Estimated Security Management Plan Information PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks estimated security management plan information pdf Use them to share invaluable insights on security incidents level, security implementation, overall security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Allocating Budget For Information Security Risk Management Programme Sample PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management.Deliver an awe inspiring pitch with this creative Allocating Budget For Information Security Risk Management Programme Sample PDF bundle. Topics like Incident Management, Threat Detection, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi-tenant storage system. Deliver an awe inspiring pitch with this creative Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF bundle. Topics like Cloud Security, Threats Accessibility, Risk Actors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Security Management Plan Steps In Detail Defining The Information Security Management System Summary PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system summary pdf Use them to share invaluable insights on instructions, processes, implementation, the executive and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Advance Data Analytics At Workspace Enabling Data Security Risk Demonstration PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk demonstration pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Executing Advance Data Analytics At Workspace Enabling Data Security Risk Icons PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk icons pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
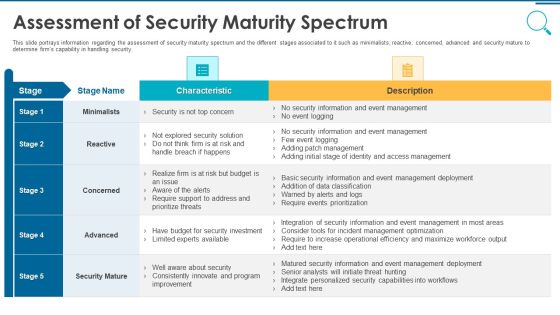
Information And Technology Security Operations Assessment Of Security Maturity Spectrum Template PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative information and technology security operations assessment of security maturity spectrum template pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Impact Assessment Matrix Information PDF
Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact assessment matrix information pdf. Use them to share invaluable insights on financial, reputation, regulatory, operational and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
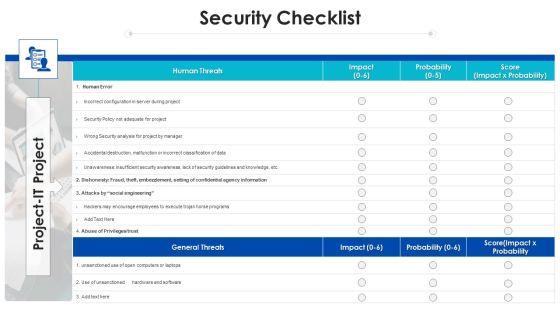
Project Assessment Templates Bundle Security Checklist Ppt Gallery Information PDF
Deliver and pitch your topic in the best possible manner with this Project Assessment Templates Bundle Security Checklist Ppt Gallery Information PDF. Use them to share invaluable insights on Human Threats, General Threats, Social Engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information And Technology Security Operations Impact Of Effective Security Management Icons PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative information and technology security operations impact of effective security management icons pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
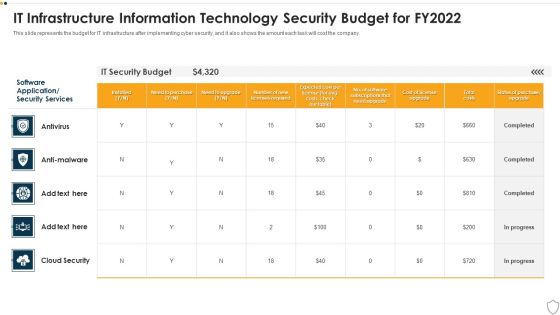
IT Security It Infrastructure Information Technology Security Budget For FY2022 Brochure PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative it security it infrastructure information technology security budget for fy2022 brochure pdf bundle. Topics like it infrastructure information technology security budget for fy2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Timeline For The Implementation Of Information Technology Security Structure PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative it security timeline for the implementation of information technology security structure pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Difference Between Cloud Security Solutions And Traditional Topics PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Cloud Information Security Difference Between Cloud Security Solutions And Traditional Topics PDF bundle. Topics like Cloud Security, Rapidly Scalable, Diminished Opportunity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF
This slide showcases software that can help organization to monitor and information security risk. It provides information about Cyber Risk Quantification, vulnerability management, Centralized repository for assets etc. Get a simple yet stunning designed Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
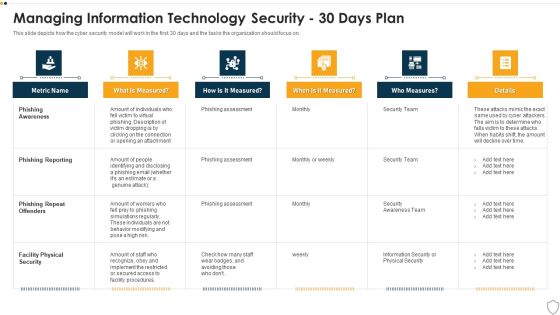
IT Security Managing Information Technology Security 30 Days Plan Themes PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Consequences Diagrams PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk assessment worksheet consequences diagrams pdf bundle. Topics like threat encountered, its vulnerability, asset and consequences, risk to the firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information and technology security operations security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
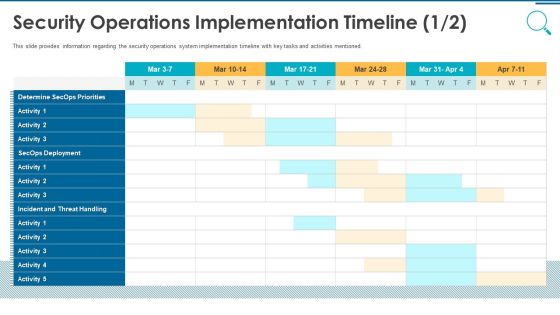
Information And Technology Security Operations Security Operations Implementation Timeline Activity Professional PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative information and technology security operations security operations implementation timeline activity professional pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
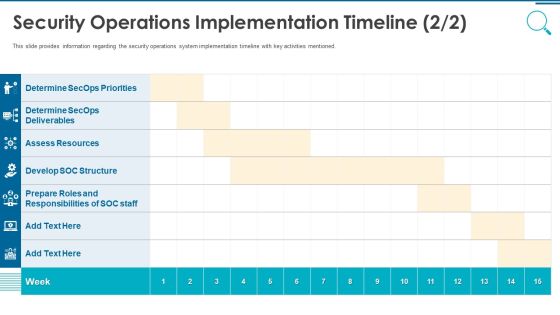
Information And Technology Security Operations Security Operations Implementation Timeline Staff Template PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this information and technology security operations security operations implementation timeline staff template pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
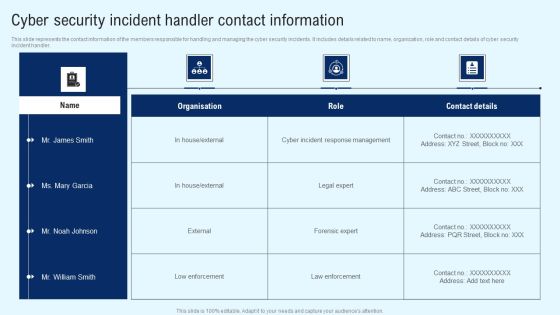
Implementing Cyber Security Incident Cyber Security Incident Handler Contact Information Diagrams PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Want to ace your presentation in front of a live audience Our Implementing Cyber Security Incident Cyber Security Incident Handler Contact Information Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Create an editable Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF can be your best option for delivering a presentation. Represent everything in detail using Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
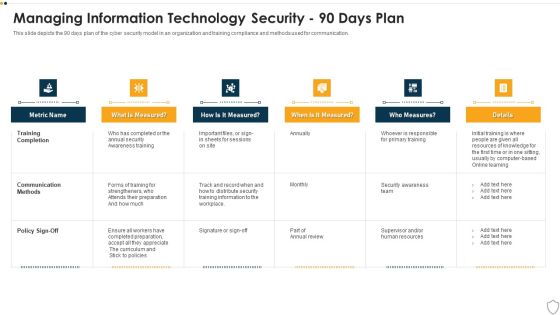
IT Security Managing Information Technology Security 90 Days Plan Sample PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 90 days plan sample pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
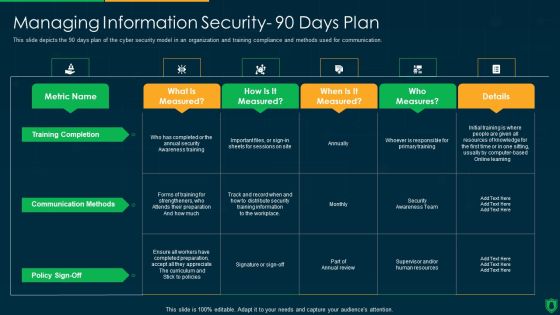
Info Security Managing Information Security 90 Days Plan Ppt PowerPoint Presentation Gallery Maker PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative info security managing information security 90 days plan ppt powerpoint presentation gallery maker pdf bundle. Topics like training completion, communication methods, policy sign off, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Cloud Security Best Practices Ppt Infographic Template Example Topics PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Cloud Security Best Practices Ppt Infographic Template Example Topics PDF. Use them to share invaluable insights onSecure Cloud, Cloud Protection, Cloud Utilization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Technology Security Operations Selecting Suitable Security Incident Management Software Diagrams PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative information and technology security operations selecting suitable security incident management software diagrams pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Information Security Decision Framework Prism Workflow Brochure PDF
Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security decision framework prism workflow brochure pdf. Use them to share invaluable insights on implement, standardize, monitor, risk rating level, resource allocation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Budget For Information Security Management Brochure PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an awe inspiring pitch with this creative cyber security risk management plan budget for information security management brochure pdf bundle. Topics like functional area, software name, training duration, training cost, number of employees, total training cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Steps For Information Security Risk Management Slides PDF
This slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Developing IT Security Strategy Steps For Information Security Risk Management Slides PDF from Slidegeeks and deliver a wonderful presentation.

Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF today and make your presentation stand out from the rest.

CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Slidegeeks is here to make your presentations a breeze with CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

IT Security Cyber Threat Landscape In Information Technology Security Download PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this it security cyber threat landscape in information technology security download pdf. Use them to share invaluable insights on business, competitors, reputation damage, organized criminals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Cyber Threat Landscape In Information Security Ppt PowerPoint Presentation File Slides PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this info security cyber threat landscape in information security ppt powerpoint presentation file slides pdf. Use them to share invaluable insights on business disruption, financial theft, fraud, reputation damage, tenant damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Information security Awareness Training For Staff Ppt PowerPoint Presentation Gallery Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this info security information security awareness training for staff ppt powerpoint presentation gallery template pdf. Use them to share invaluable insights on senior executives, project managers, it teams, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
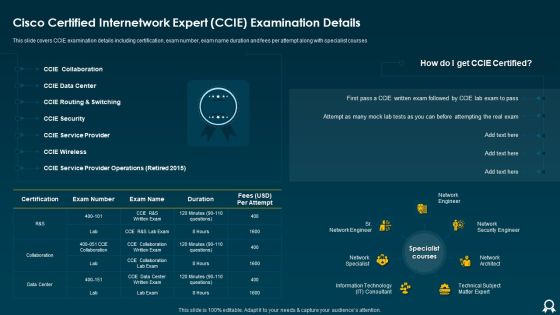
IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF
This slide covers CCIE examination details including certification, exam number, exam name duration and fees per attempt along with specialist courses. Deliver and pitch your topic in the best possible manner with this IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF. Use them to share invaluable insights on Data Center, Service Provider, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
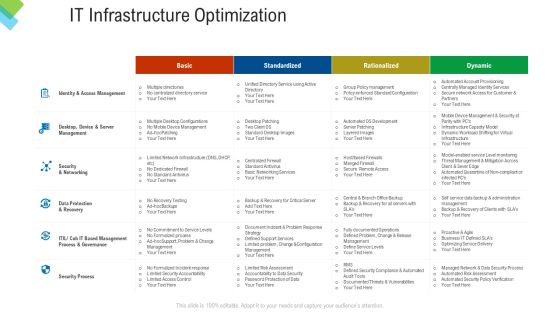
Construction Management Services IT Infrastructure Optimization Themes PDF
Deliver and pitch your topic in the best possible manner with this construction management services it infrastructure optimization themes pdf. Use them to share invaluable insights on security process, security and networking, management process, data protection, server management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF. Use them to share invaluable insights on Cloud Frameworks, Information Division, Cautious Scaling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Why Cloud Security Is Important Pictures PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Why Cloud Security Is Important Pictures PDF bundle. Topics like Centralized Security, Cost Effective, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF Use them to share invaluable insights on Account Access, Data Exfiltration, Network Connections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
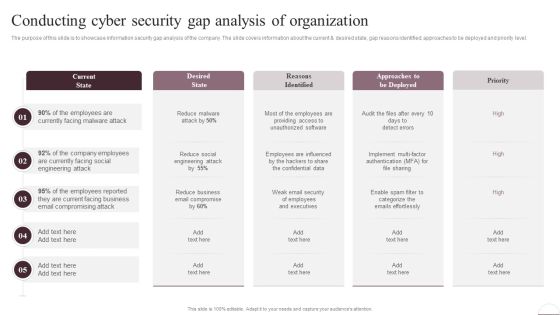
Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
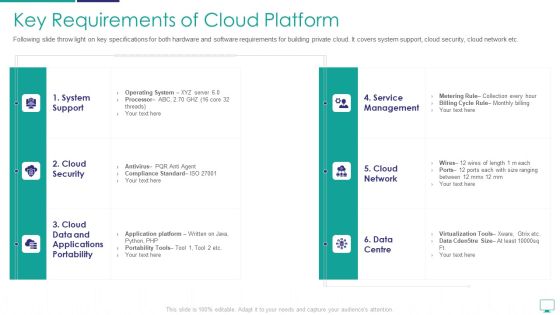
Key Requirements Of Cloud Platform Information PDF
Following slide throw light on key specifications for both hardware and software requirements for building private cloud. It covers system support, cloud security, cloud network etc. Deliver an awe inspiring pitch with this creative key requirements of cloud platform information pdf bundle. Topics like operating system, application platform, compliance standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
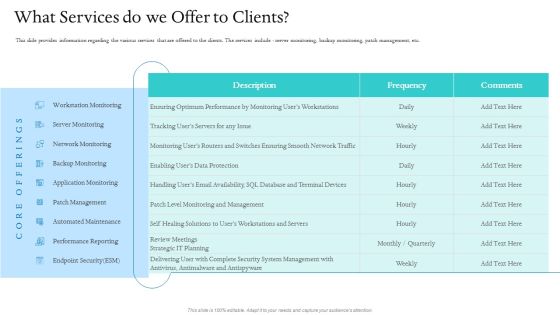
Information Technology Facilities Governance What Services Do We Offer To Clients Ppt Infographics Inspiration PDF
This slide provides information regarding the various services that are offered to the clients. The services include - server monitoring, backup monitoring, patch management, etc. Deliver an awe inspiring pitch with this creative information technology facilities governance what services do we offer to clients ppt infographics inspiration pdf bundle. Topics like performance reporting, endpoint security, network monitoring, server monitoring, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF
This slide provides information regarding ITIL process areas in terms of service strategy and service design and associated sequential activities. Deliver an awe inspiring pitch with this creative Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF bundle. Topics like Sequential Activities Processes, Strategy Management Execution, Sequential Activities Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
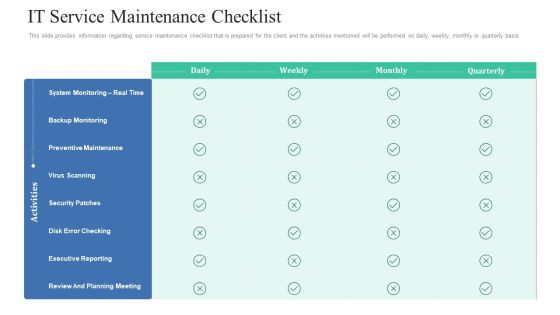
Retaining Clients Improving Information Technology Facilities IT Service Maintenance Checklist Graphics PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver an awe-inspiring pitch with this creative retaining clients improving information technology facilities it service maintenance checklist graphics pdf bundle. Topics like preventive maintenance, security patches, executive reporting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home