Security Assessment

Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF
The following slide highlights the five phase of risk based cyber security which includes business impact analysis, risk assessment, controls, report and monitor, it provides activity, value and outcome for each phase which helps company to develop a consistent incident response process. Presenting Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Impact Analysis, Risk Assessment, Controls, Report, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF
The purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees, and retesting. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation

Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF
The following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Persuade your audience using this Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Priority, Mitigation, Controls, Automation, Governance, Risk Culture. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
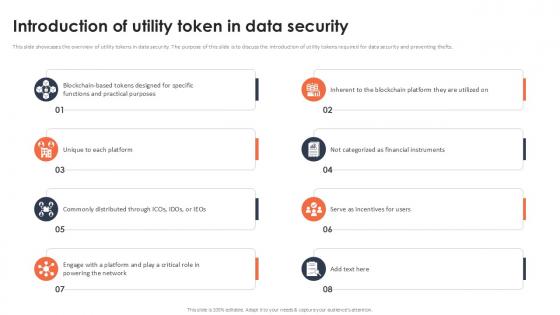
Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Explore a selection of the finest Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
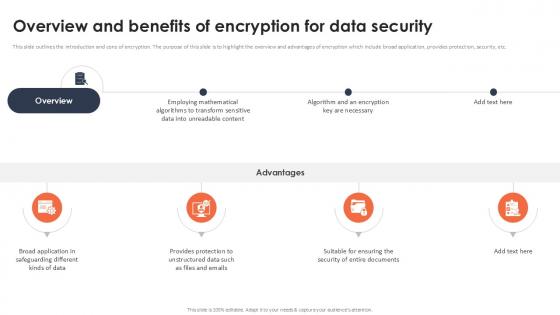
Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Retrieve professionally designed Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Slidegeeks has constructed Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
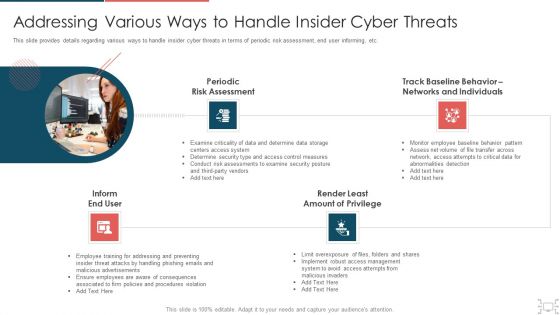
Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
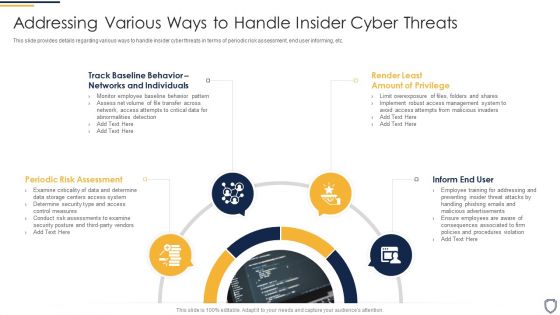
Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Infographics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a corporate security and risk management addressing various ways to handle insider cyber threats infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Physical System To Enhance Steps For Cps Security Strategy Plan Elements PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Physical System To Enhance Steps For Cps Security Strategy Plan Elements PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
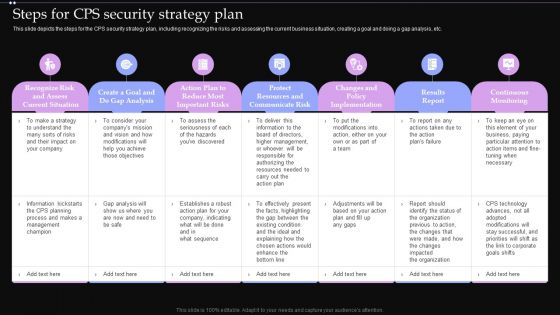
Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Do you know about Slidesgeeks Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF
This slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cloud Computing Assessment Objectives To Conclude Evidences Ppt Portfolio Pictures PDF
The slide highlights various objectives of cloud computing audit to ensure effective assessment and mitigation of IT risks. Various objectives included are manage IT risks, ensure compliance and identify security controls Persuade your audience using this Cloud Computing Assessment Objectives To Conclude Evidences Ppt Portfolio Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Manage IT Risks, Ensure Compliance, Identify Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
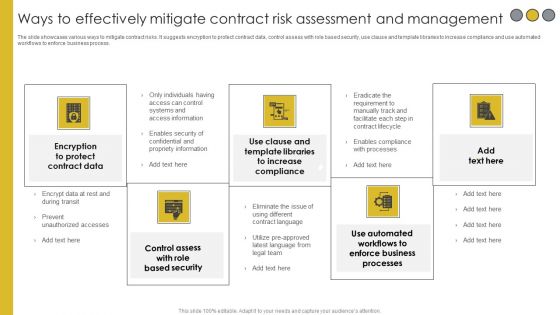
Ways To Effectively Mitigate Contract Risk Assessment And Management Download PDF
The slide showcases various ways to mitigate contract risks. It suggests encryption to protect contract data, control assess with role based security, use clause and template libraries to increase compliance and use automated workflows to enforce business process. Presenting Ways To Effectively Mitigate Contract Risk Assessment And Management Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Encryption Protect, Control Assess Role, Use Clause Template Libraries. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

COVID 19 Mitigating Impact On High Tech Industry Impact Assessment Analysis On Various Segment Of Technology Sector Structure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry impact assessment analysis on various segment of technology sector structure pdf. The topics discussed in these slides are impact area, personnel, operations, supply chain, revenue, overall assessment, technology, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF
This slide covers five steps process for risk assessment of financial data. It includes steps as formation of data security governance framework, identify data set, financial liabilities risk assessment, prioritization of data sets and budget preparation. Presenting Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Maturity Path, Budget Preparation, Prioritize Data Sets, Identify Data Set. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Phase Of Digital Risk Assessment Framework Ppt Inspiration Model PDF
The following slide highlights the five phase of cyber security framework illustrating identify, protect, detect, respond and recover phases to build a robust cyber security. Persuade your audience using this Five Phase Of Digital Risk Assessment Framework Ppt Inspiration Model PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Protect, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF
The following slide highlights the cyber security key metrics monitoring dashboard illustrating critical applications, mission critical, other regulations, SOX, key metrics, controls, audits and cyber security training compliance. Showcasing this set of slides titled Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF. The topics addressed in these templates are Critical Applications, Mission Critical, Other Regulation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. This modern and well-arranged Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
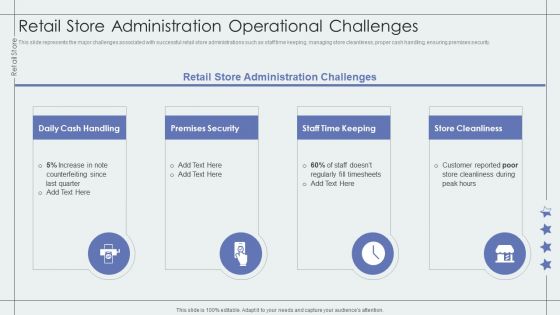
Retail Store Administration Operational Challenges Retail Outlet Performance Assessment Inspiration PDF
This slide represents the major challenges associated with successful retail store administrations such as staff time keeping, managing store cleanliness, proper cash handling, ensuring premises security. Presenting Retail Store Administration Operational Challenges Retail Outlet Performance Assessment Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Premises Security, Store Cleanliness, Counterfeiting Since. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Implement Cloud Collaboration Comparative Assessment Of Cloud And Traditional Project Structure PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc. Presenting How To Implement Cloud Collaboration Comparative Assessment Of Cloud And Traditional Project Structure PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Parameters Cloud, Capital Expenditure, Real Time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
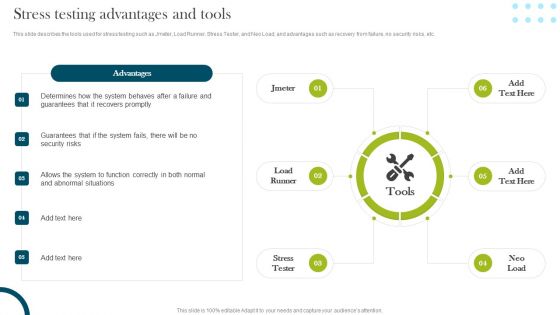
Stress Testing Advantages And Tools Compliance Assessment Ppt File Portrait PDF
This slide describes the tools used for stress testing such as Jmeter, Load Runner, Stress Tester, and Neo Load, and advantages such as recovery from failure, no security risks, etc. This Stress Testing Advantages And Tools Compliance Assessment Ppt File Portrait PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
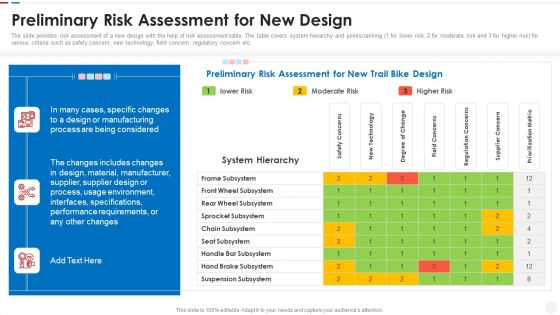
Failure Methods And Effects Assessments FMEA Preliminary Risk Assessment For New Design Ideas PDF
The slide provides risk assessment of a new design with the help of risk assessment table. The table covers system hierarchy and points or ranking 1 for lower risk, 2 for moderate risk and 3 for higher risk for various criteria such as safety concern, new technology, field concern, regulatory concern etc. Deliver an awe inspiring pitch with this creative failure methods and effects assessments fmea preliminary risk assessment for new design ideas pdf bundle. Topics like requirements, environment, performance, process, supplier can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Assessing Debt And Equity Fundraising Alternatives For Business Growth Comparative Assessment Inspiration PDF
This slide showcases comparison table that can help organization to evaluate the different banks available in market to obtain loans. Its key components are bank, amount, interest rate, EMI per month, time period and collateral needed. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Assessing Debt And Equity Fundraising Alternatives For Business Growth Comparative Assessment Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Assessing Debt And Equity Fundraising Alternatives For Business Growth Comparative Assessment Inspiration PDF today and make your presentation stand out from the rest.

Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Present like a pro with Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
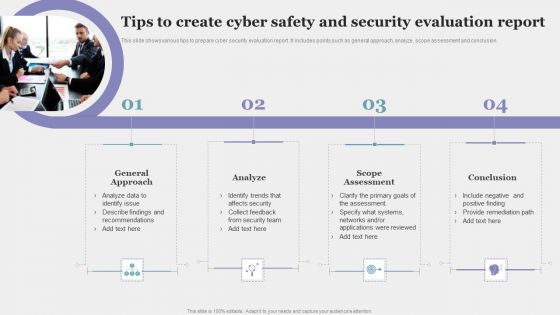
Tips To Create Cyber Safety And Security Evaluation Report Pictures PDF
This slide shows various tips to prepare cyber security evaluation report. It includes points such as general approach, analyze, scope assessment and conclusion. Persuade your audience using this Tips To Create Cyber Safety And Security Evaluation Report Pictures PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including General Approach, Analyze, Scope Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
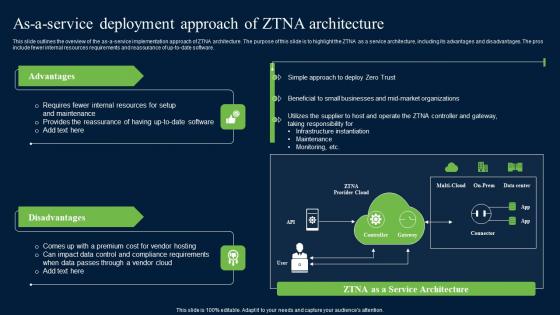
As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Boost your pitch with our creative As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Utilizing Infrastructure Management Using Latest Methods Interdependence Resiliency And Security Themes PDF
This is a utilizing infrastructure management using latest methods interdependence resiliency and security themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical infrastructure dependencies and interdependencies assessment framework, infrastructure resilience wheel, lifecycle adaptive components resilience framework, dimensions infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF. Use them to share invaluable insights on Recognize Critical, Discover Malicious, Risk Assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
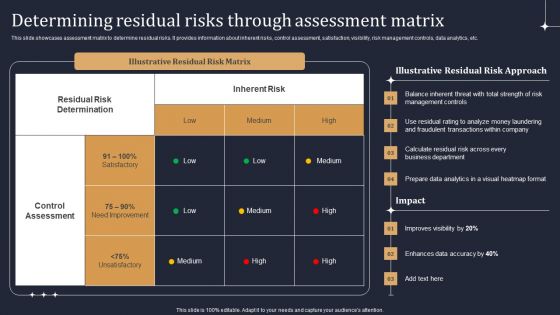
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
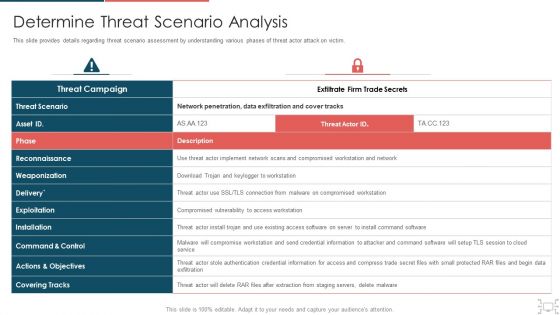
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Table Of Contents Structure PDF
Presenting techniques and strategies to reduce security management risks table of contents structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
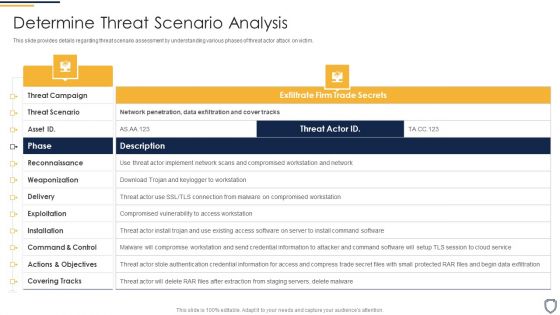
Corporate Security And Risk Management Determine Threat Scenario Analysis Formats PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative corporate security and risk management determine threat scenario analysis formats pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Steps Of Contractor Security Management Ppt PowerPoint Presentation Inspiration Show PDF
Presenting this set of slides with name key steps of contractor security management ppt powerpoint presentation inspiration show pdf. This is a five stage process. The stages in this process are use of third party prequalifying companies, assessment of contractor safety statistics, internal checklist to assign grades to contractors during prequalification, verification of contractor certifications and permits on site safety orientations, periodic assessments during contract term. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
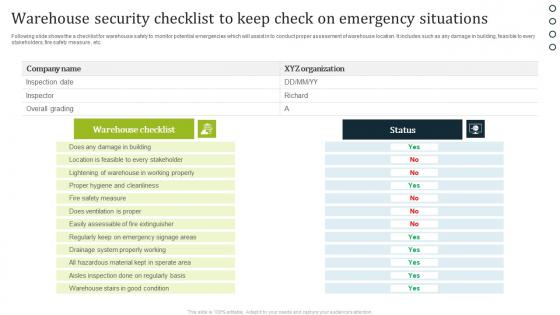
Warehouse Security Checklist To Keep Check On Emergency Situations Professional Pdf
Following slide shows the a checklist for warehouse safety to monitor potential emergencies which will assist in to conduct proper assessment of warehouse location. It includes such as any damage in building, feasible to every stakeholders, fire safety measure , etc. Pitch your topic with ease and precision using this Warehouse Security Checklist To Keep Check On Emergency Situations Professional Pdf. This layout presents information on Warehouse Checklist, Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
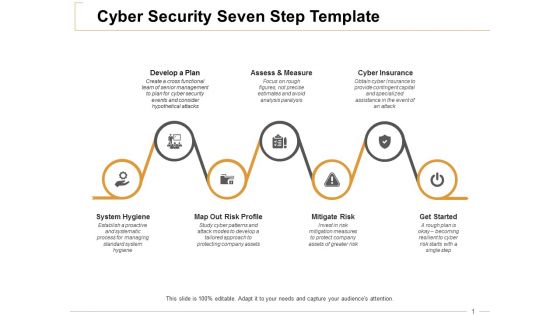
Cyber Security Seven Step Cyber Insurance Ppt PowerPoint Presentation Infographic Template Graphic Tips
This is a cyber security seven step cyber insurance ppt powerpoint presentation infographic template graphic tips. This is a seven stage process. The stages in this process are develop a plan, assess and measure, cyber insurance, mitigate risk, get started.
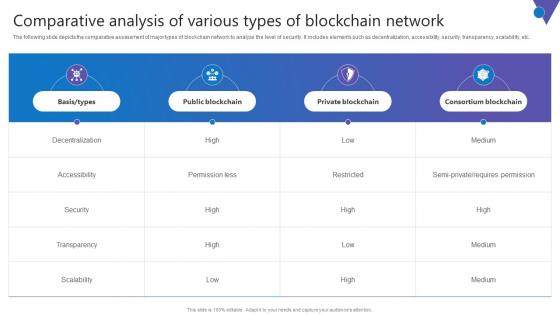
Comparative Analysis Of Various Comprehensive Guide To Blockchain Digital Security Slides Pdf
The following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc. Find a pre designed and impeccable Comparative Analysis Of Various Comprehensive Guide To Blockchain Digital Security Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
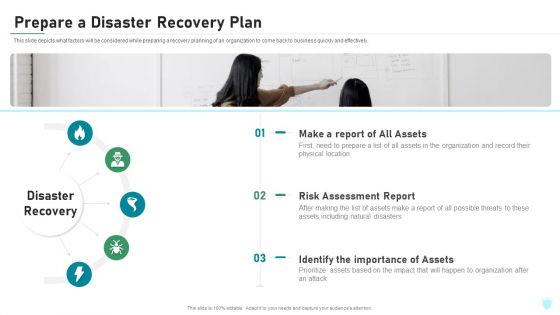
Prepare A Disaster Recovery Plan IT Security IT Ppt Ideas Graphics Design PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting prepare a disaster recovery plan it security it ppt ideas graphics design pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like make a report of all assets, risk assessment report, identify the importance of assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Prepare A Disaster Recovery Plan Ppt Model Aids PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting information security prepare a disaster recovery plan ppt model aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, location, risk assessment report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
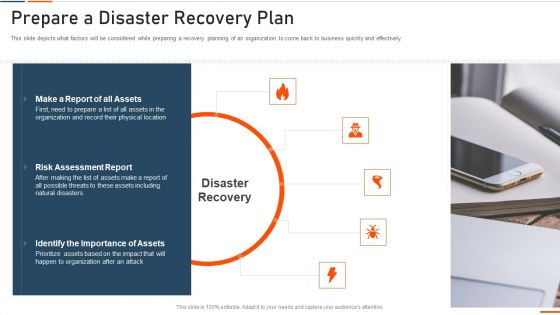
Information Technology Security Prepare A Disaster Recovery Plan Ppt Ideas Inspiration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a information technology security prepare a disaster recovery plan ppt ideas inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment report, identify importance assets, report assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
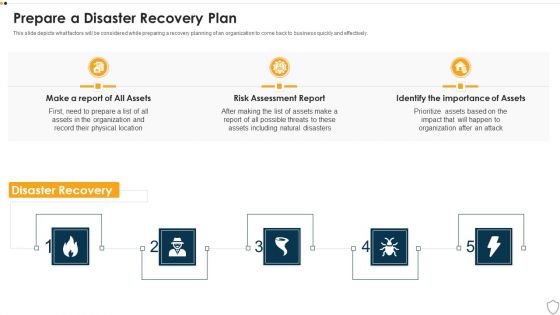
IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Prepare A Disaster Recovery Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a info security prepare a disaster recovery plan ppt powerpoint presentation file portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disaster recovery, risk assessment report, identify importance assets, disaster recovery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V
The slide depicts risk assessment for the cybersecurity industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability. It covers potential hazards associated with data beaches, phishing attacks, malware, regulatory compliance, and IoT security issues. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V from Slidegeeks and deliver a wonderful presentation.

Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf
This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf
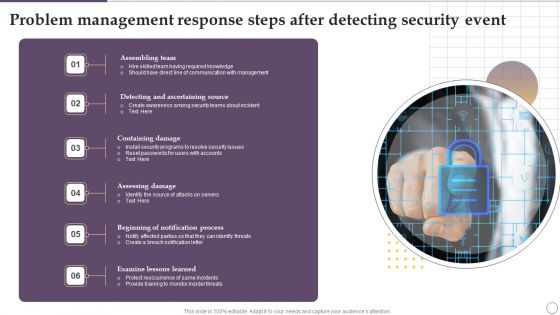
Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF
Presenting Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Assembling Team, Containing Damage, Assessing Damage, Examine Lessons Learned. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
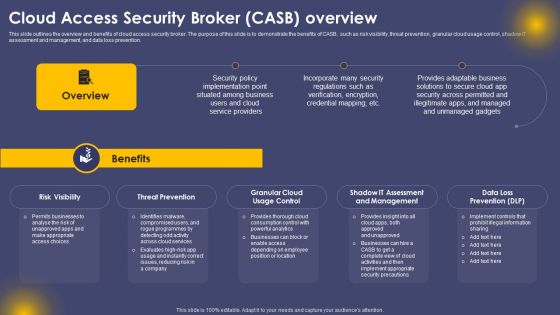
Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF today and make your presentation stand out from the rest.
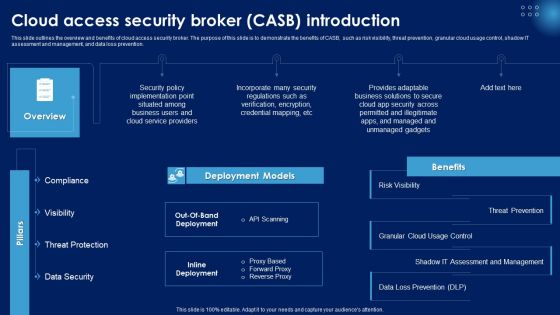
Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.

Three Staged Security Process Infographic Ppt PowerPoint Presentation File Infographic Template PDF
Presenting this set of slides with name three staged security process infographic ppt powerpoint presentation file infographic template pdf. This is a three stage process. The stages in this process are assess and learn, strategize and plan, implement and support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Staff Background PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security operations implementation timeline staff background pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Research Objectives To Understand Global Security Industry PPT Template IR SS V
The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats. The slide portrays the research objectives overview of the defense industry report. It aims to cover the different objectives which are used to understand the research conducted while preparing the report. It includes market research objectives, technological objectives, future purpose objectives for understanding the global defense market. Are you searching for a Research Objectives To Understand Global Security Industry PPT Template IR SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Research Objectives To Understand Global Security Industry PPT Template IR SS V from Slidegeeks today.

4 Step Cycle To Ensure HR Security And Well Being Graphics PDF
This slide highlights four stage cycle to ensure HR safety and well being in an organization. The purpose of this template is to create an efficient and safe working culture and to improve employee wellbeing to increase their contribution. It includes stages of regular risk assessment, implementation of safety measures, monitoring regular compliance and continuous improvement. Presenting 4 Step Cycle To Ensure HR Security And Well Being Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assess And Identify Risks, Implement Safety Measures, Monitor Safety Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Laptop With Lock And Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Internet PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Download and present our Computer PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas.Use these PowerPoint slides for presentations relating to Computer security concept, computer, internet, success, technology, security. The prominent colors used in the PowerPoint template are Brown, Black, Gray. People tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our security PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. PowerPoint presentation experts tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Presenters tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. The feedback we get is that our technology PowerPoint templates and PPT Slides are readymade to fit into any presentation structure.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
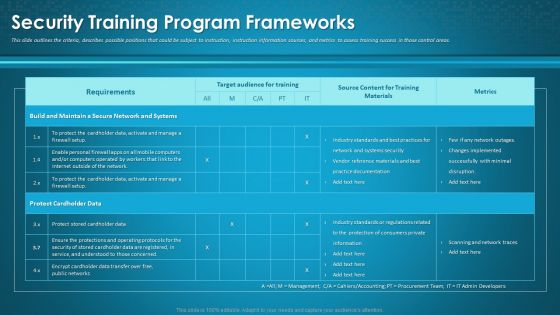
Organizational Network Awareness Staff Learning Security Training Program Frameworks Sample PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this organizational network awareness staff learning security training program frameworks sample pdf. Use them to share invaluable insights on target audience for training, source content, metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Companys Data Safety Recognition Security Training Program Frameworks Contd Infographics PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this companys data safety recognition security training program frameworks contd infographics pdf. Use them to share invaluable insights on requirements, target audience, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Breach Prevention Recognition Security Training Program Frameworks Contd Template PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security training program frameworks contd template pdf bundle. Topics like measures, instruction information sources, target audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home