Security Assessment
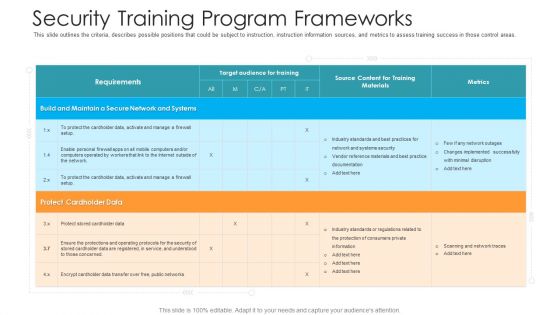
Security Training Program Frameworks Hacking Prevention Awareness Training For IT Security Themes PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on target, training, maintain, secure, implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
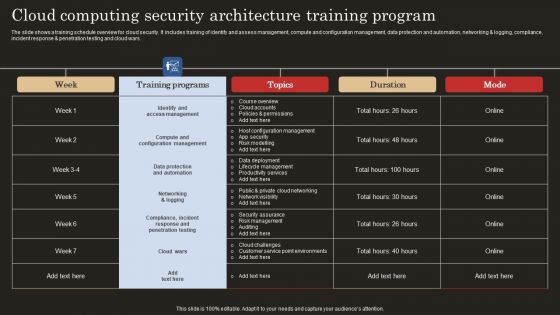
Cloud Computing Security Architecture Training Program Guidelines PDF
The slide shows a training schedule overview for cloud security. It includes training of identify and assess management, compute and configuration management, data protection and automation, networking and logging, compliance, incident response and penetration testing and cloud wars. Showcasing this set of slides titled Cloud Computing Security Architecture Training Program Guidelines PDF. The topics addressed in these templates are Identify Access Management, Compute Configuration Management, Data Protection Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementing Security Management Strategy To Mitigate Risk Overview Of Security Risk Management Process Pictures PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative implementing security management strategy to mitigate risk overview of security risk management process pictures pdf bundle. Topics like identify the risks, assess the risks, evaluate the risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workforce Security Realization Coaching Plan Security Training Program Frameworks Contd Rules PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks contd rules pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
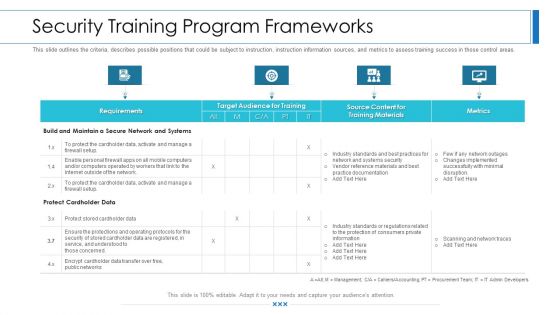
Workforce Security Realization Coaching Plan Security Training Program Frameworks Brochure PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks brochure pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
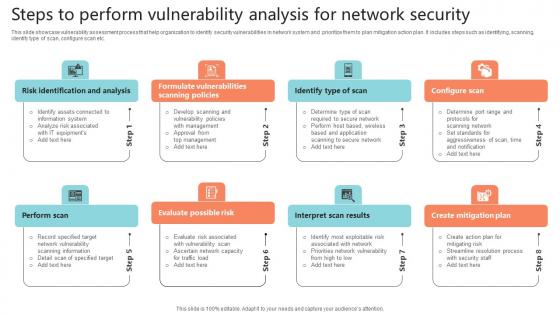
Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
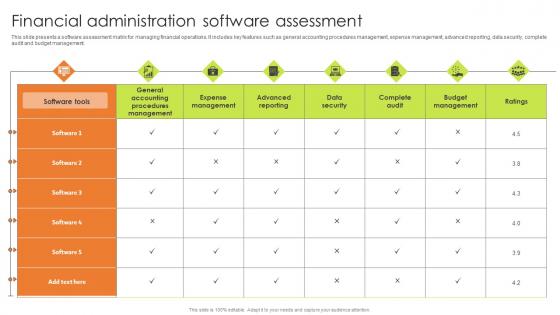
Financial Administration Software Assessment Rules Pdf
This slide presents a software assessment matrix for managing financial operations. It includes key features such as general accounting procedures management, expense management, advanced reporting, data security, complete audit and budget management. Pitch your topic with ease and precision using this Financial Administration Software Assessment Rules Pdf. This layout presents information on Expense Management, Advanced Reporting, Data Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Companys Data Safety Recognition Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative companys data safety recognition security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Vulnerability Administration Plan And Security Services Topics PDF
This slide defines the vulnerability management program and security services based on risk. It includes information related to integrating, assessment planning, analysis and sustainability. Persuade your audience using this Vulnerability Administration Plan And Security Services Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Integrating, Assessment Planning, Analysis And Reporting, Sustainability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Dynamic Malware Assessment Flow Chart Infographics PDF
This slide illustrates malware analysis flowchart which companies employ to learn from past attack and create more secure infrastructure for future. The elements covered in this slide are live operating system, volatile memory forensics and slide channel analysis. Showcasing this set of slides titled Dynamic Malware Assessment Flow Chart Infographics PDF. The topics addressed in these templates are Live Operating System, Volatile Memory Forensics, Slide Channel Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Administration Assessment Example Sample Ppt Files
This is a administration assessment example sample ppt files. This is a six stage process. The stages in this process are aims and objective, implementation, feasibility, consultancy, solutions, audit and testing, information security.
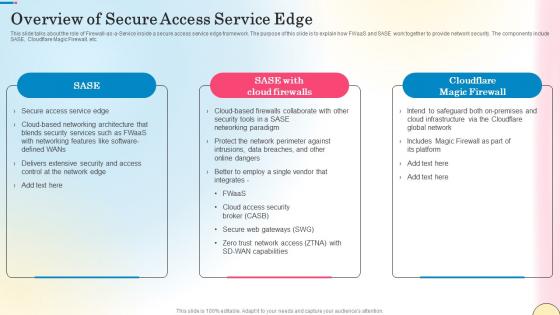
Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Find highly impressive Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

A113 Comparative Assessment Of Various Payment Cryptocurrencies
Mentioned slide demonstrates comparative analysis of various crypto coins which can be used by businesses in cashless payment. It includes key points such as launch year, trading value, transaction rate, transaction fees, privacy, block time, and trading history. There are so many reasons you need a A113 Comparative Assessment Of Various Payment Cryptocurrencies. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. There are so many reasons you need a Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc.This is a Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Management, Infrastructure Protection, Security Equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
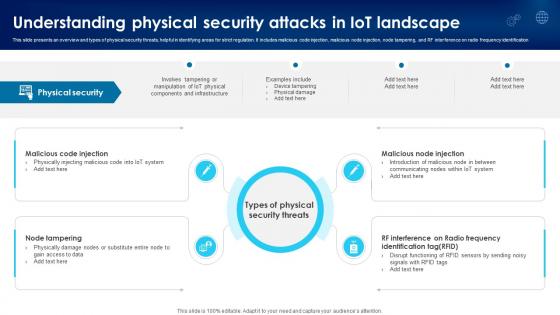
Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V
This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification. Find highly impressive Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf
This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Showcasing this set of slides titled Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf. The topics addressed in these templates are Encryption Data Rest, Consistent Patching, Inventory Assess Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
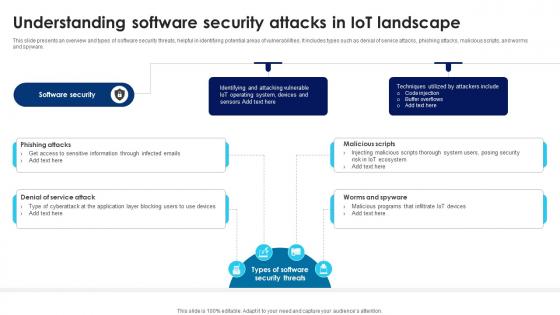
Building Trust With IoT Security Understanding Software Security Attacks In IoT Landscape IoT SS V
This slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities. It includes types such as denial of service attacks, phishing attacks, malicious scripts, and worms and spyware. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Understanding Software Security Attacks In IoT Landscape IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

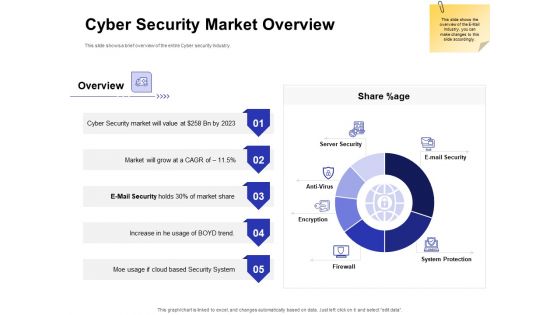
Email Security Market Research Report Cyber Security Market Overview Inspiration PDF
Presenting this set of slides with name email security market research report cyber security market overview inspiration pdf. The topics discussed in these slides are server security, e mail security, system protection, antivirus, firewall, encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Global Cloud Based Email Security Market Cyber Security Market Overview Designs PDF
Presenting this set of slides with name global cloud based email security market cyber security market overview designs pdf. The topics discussed in these slides are server security, e mail security, system protection, antivirus, firewall, encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Based Email Security Market Report Cyber Security Market Overview Ppt Infographics Format PDF
This slide shows a brief overview of the entire Cyber security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report cyber security market overview ppt infographics format pdf bundle. Topics like cyber security market overview can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
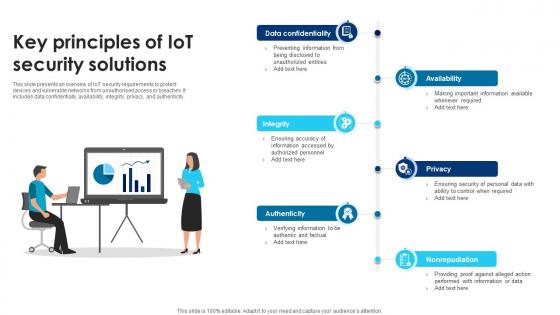
Building Trust With IoT Security Key Principles Of IoT Security Solutions IoT SS V
This slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches. It includes data confidentially, availability, integrity, privacy, and authenticity. Do you know about Slidesgeeks Building Trust With IoT Security Key Principles Of IoT Security Solutions IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
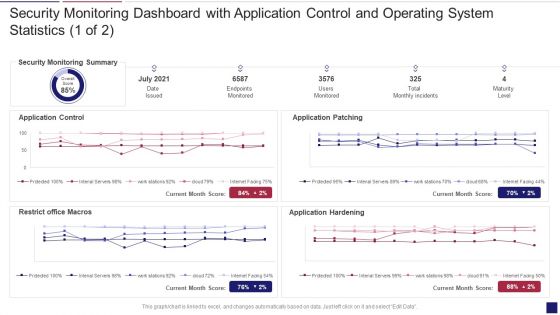
Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Security Brochure PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard security brochure pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF
Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF. Use them to share invaluable insights on Internal Vulnerabilities, Employee Awareness, Comprehensive Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
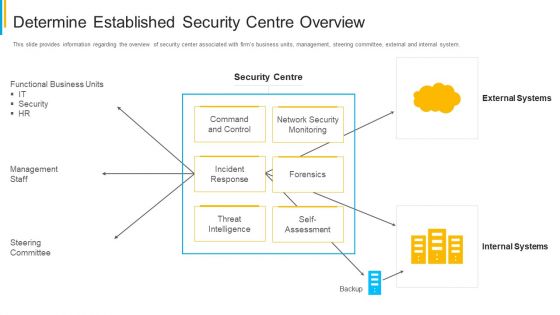
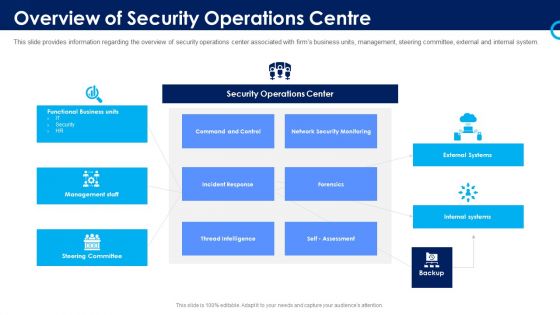
Project Security Administration IT Determine Established Security Centre Overview Infographics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this project security administration it determine established security centre overview infographics pdf. Use them to share invaluable insights on functional business units, management staff, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
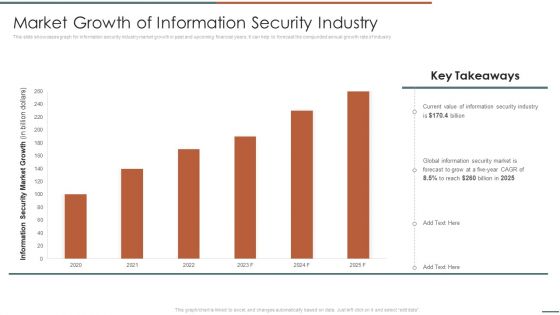
Information Security Risk Evaluation Market Growth Of Information Security Industry Infographics PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compunded annual growth rate of industry .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Market Growth Of Information Security Industry Infographics PDF. Use them to share invaluable insights on Information Security, Global Information, Security Market and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Technology Security Operations Overview Of Security Operations Centre Portrait PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this information and technology security operations overview of security operations centre portrait pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Organizational Security Solutions Overview Of Security Operations Centre Ppt Styles Graphics Pictures PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this organizational security solutions overview of security operations centre ppt styles graphics pictures pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
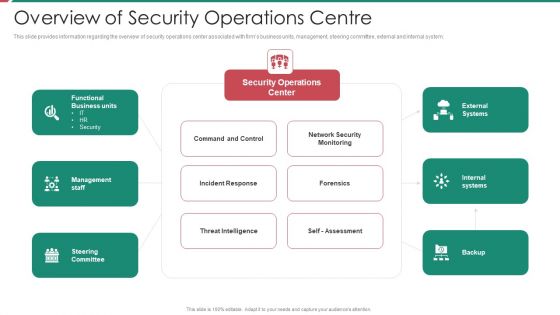
Security And Process Integration Overview Of Security Operations Centre Portrait PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security and process integration overview of security operations centre portrait pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
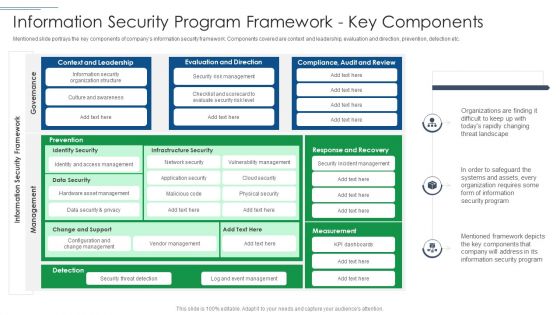
IT Security Risk Management Approach Introduction Information Security Program Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Information Security Program Themes PDF bundle. Topics like Evaluation And Direction, Organization Structure, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Based Email Security Market Report Hosted E Mail Security Ppt Ideas Rules PDF
This slide displays the overview and key features of hosted E Mail Security. This is a cloud based email security market report hosted e mail security ppt ideas rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintenance, security, miscellaneous, protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
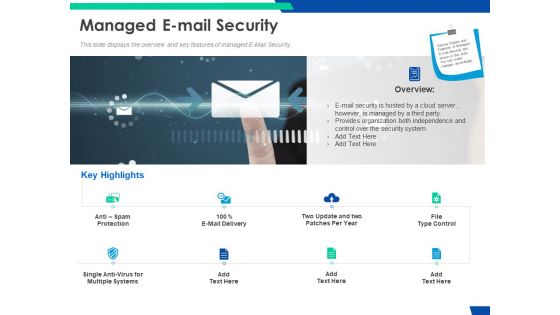
Cloud Based Email Security Market Report Managed E Mail Security Ppt Infographic Template Themes PDF
This slide displays the overview and key features of managed E Mail Security. Presenting cloud based email security market report managed e mail security ppt infographic template themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like managed e mail security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
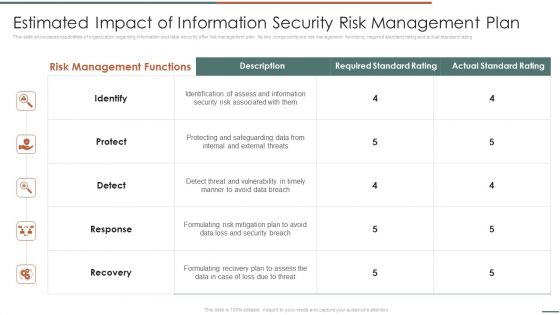
Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF. Use them to share invaluable insights on Identification Assess, Protecting Safeguarding, Detect Threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
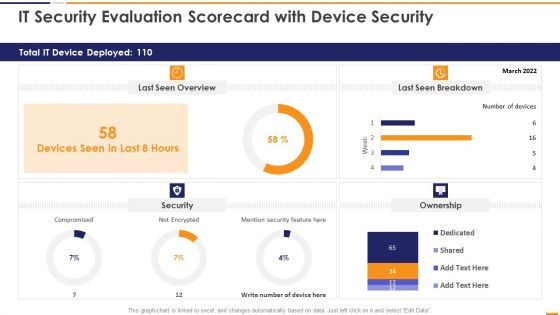
IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF bundle. Topics like Total IT Device, Last Seen Overview, Last Seen Breakdown, Mention Security Feature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
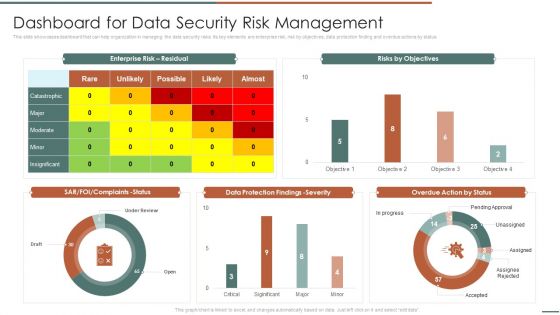
Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF bundle. Topics like Complaints Status, Protection Findings, Overdue Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF bundle. Topics like Training Of Employees, Software Implementation, Risk Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
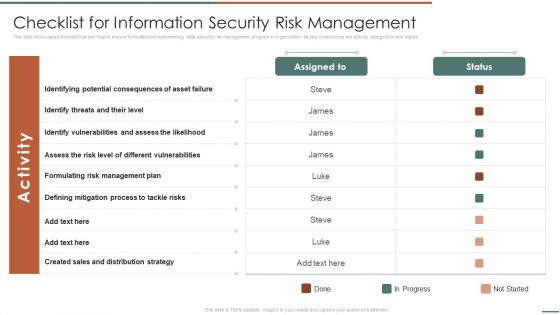
Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF bundle. Topics like Identifying Potential, Defining Mitigation, Created Sales can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF bundle. Topics like Business Disruption, Cost By Consequence, Malware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
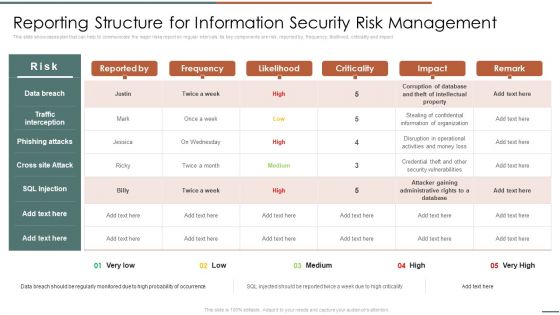
Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF bundle. Topics like Phishing Attacks, Cross Attack, Security Vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Timeline For Information Security Risk Management Training Background PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Timeline For Information Security Risk Management Training Background PDF bundle. Topics like Cybersecurity Awareness, Malware Detection, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Portfolio Risk Assessment Example Presentation Images
This is a portfolio risk assessment example presentation images. This is a five stage process. The stages in this process are identification of safety issues, assessment of safety issues, definition and programming of safety issues, implementation and follow up, safety performance.
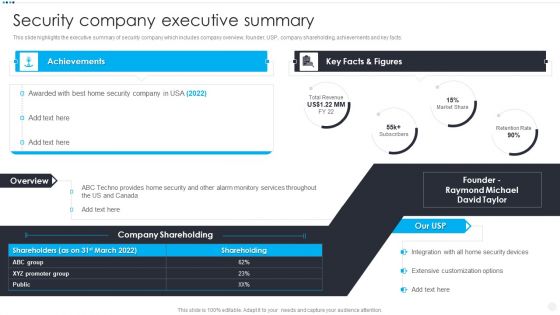
Smart Home Security Solutions Company Profile Security Company Executive Summary Summary PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Security Company Executive Summary Summary PDF. Use them to share invaluable insights on Key Facts Figures, ABC Techno Provides, Monitory Services Throughout and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF. Use them to share invaluable insights on Monitory Services, Company Shareholding, Extensive Customization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Based Email Security Market Report Key Stats Security Ppt Slides Demonstration PDF
Use this slide displays a complete overview of the E Mail security Market. Deliver and pitch your topic in the best possible manner with this cloud based email security market report key stats security ppt slides demonstration pdf. Use them to share invaluable insights on key stats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
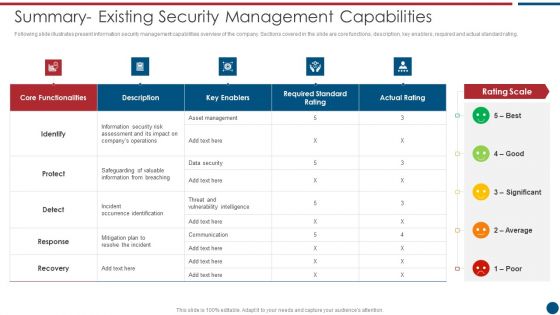
Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
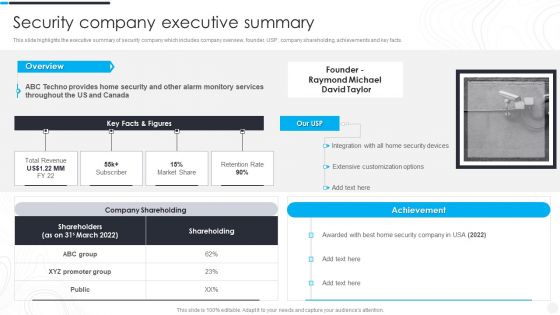
Security Camera System Company Profile Security Company Executive Summary Formats PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Executive Summary Formats PDF bundle. Topics like Company Shareholding, Customization Options, Raymond Michael can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
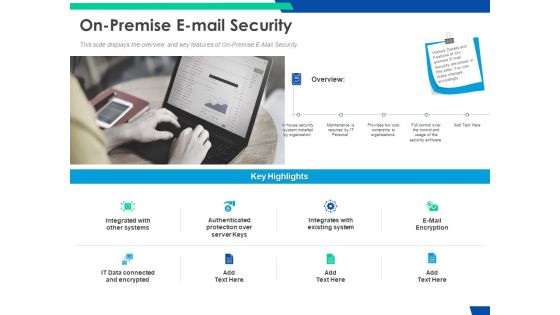
Cloud Based Email Security Market Report On Premise E Mail Security Ppt Ideas Design Inspiration PDF
This slide displays the overview and key features of On Premise E Mail Security. This is a cloud based email security market report on premise e mail security ppt ideas design inspiration pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like on premise e mail security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Overview Of Cyber Security Awareness Course Template PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Organizing Security Awareness Overview Of Cyber Security Awareness Course Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Organizing Security Awareness Overview Of Cyber Security Awareness Course Template PDF.
Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyze risks, evaluate and treat risks.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF. Use them to share invaluable insights on Establish The Context, Identify Risks, Analyze Risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF. Use them to share invaluable insights on Required Standard Rating Actual, Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating,This is a Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Untrained Employees, Complex Risk, Management Policy . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Identifying Employees For Information Security Training Programme Background PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Identifying Employees For Information Security Training Programme Background PDF. Use them to share invaluable insights on Threat Scanning, Malware Detection, Report Formulation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF. Use them to share invaluable insights on Rating Breakdown, Vulnerabilities, Response Progress and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
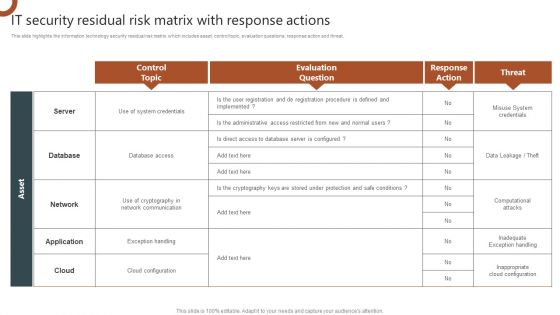
IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
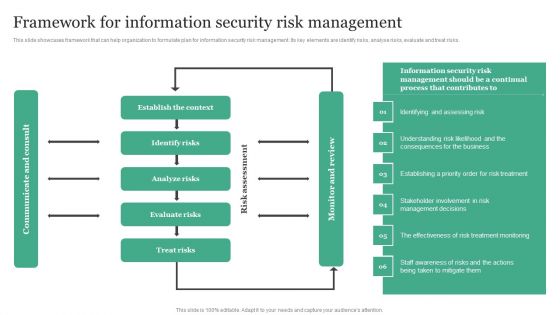
Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF can be your best option for delivering a presentation. Represent everything in detail using Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Information Systems Security And Risk Management Plan Framework For Information Security Risk Management Formats PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Create an editable Information Systems Security And Risk Management Plan Framework For Information Security Risk Management Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Information Systems Security And Risk Management Plan Framework For Information Security Risk Management Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
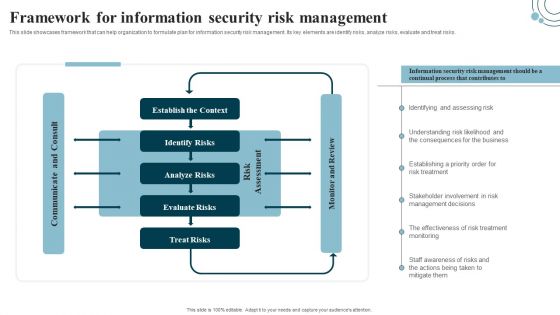
Developing IT Security Strategy Framework For Information Security Risk Management Ideas PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyze risks, evaluate and treat risks. Create an editable Developing IT Security Strategy Framework For Information Security Risk Management Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Developing IT Security Strategy Framework For Information Security Risk Management Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Slidegeeks is here to make your presentations a breeze with Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

 Home
Home