Security Assessment
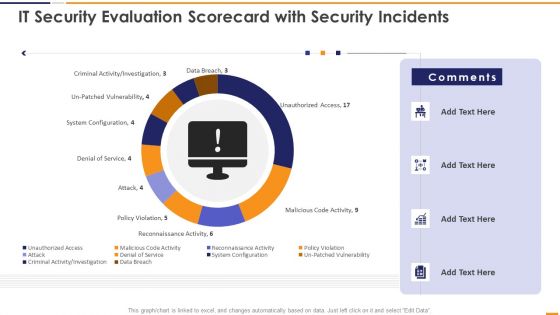
IT Security Evaluation Scorecard With Security Incidents Ppt Pictures Vector PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Security Incidents Ppt Pictures Vector PDF. Use them to share invaluable insights on Unauthorized Access Sales, Malicious Code Activity, Reconnaissance Activity Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Impact Of Information Security Loss On Organization Structure PDF
Presenting Information Security Risk Evaluation Impact Of Information Security Loss On Organization Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Financial Organization, Loss Of Productivity, Reputational Loss. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF bundle. Topics like Between Failures, Times Attackers, Management Programme can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
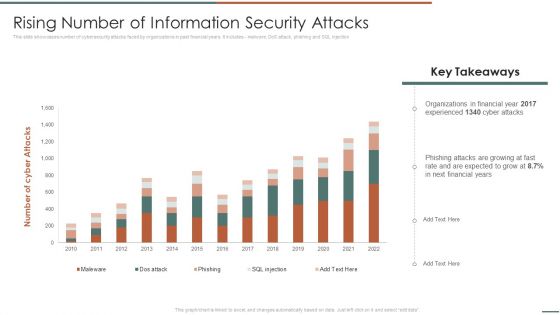
Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF. Use them to share invaluable insights on Organizations In Financial, Experienced, Phishing Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
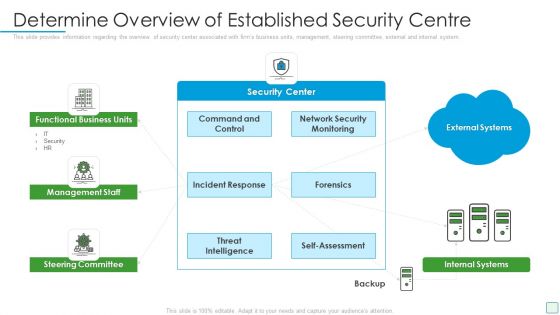
Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. This is a Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Leadership, Evaluation Direction, Change Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
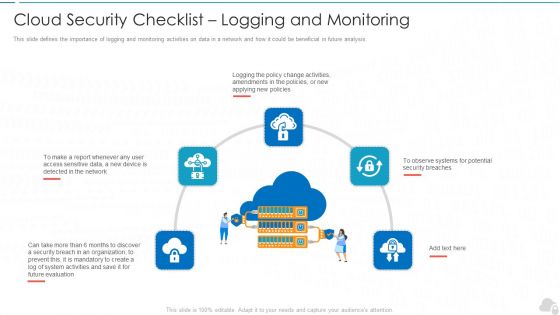
Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Pictures PDF
Presenting way to overcome security management challenges setting up an advanced security management plan pictures pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
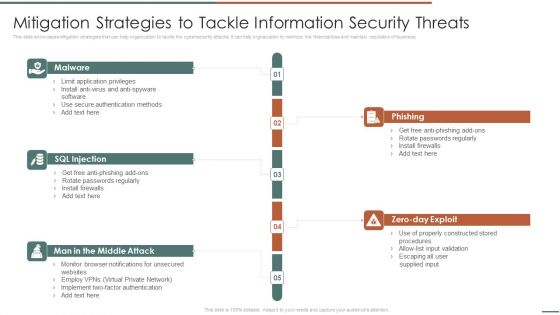
Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
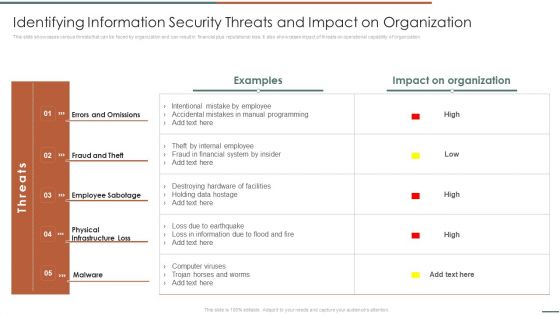
Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF bundle. Topics like Errors And Omissions, Fraud And Theft, Employee Sabotage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Information Security Attacks Faced By Organization Download PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack.Presenting Information Security Risk Evaluation Information Security Attacks Faced By Organization Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Malicious Software, Including Spyware, Ransomware Viruses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
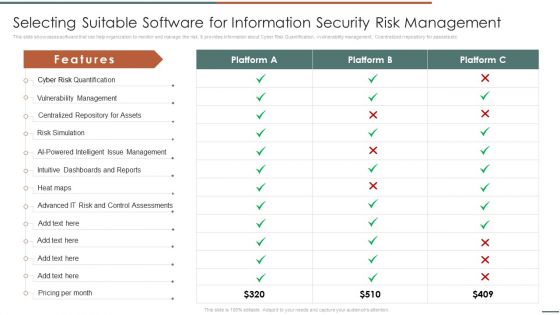
Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF
This slide showcases software that can help organization to monitor and manage the risk. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF. Use them to share invaluable insights on Vulnerability Management, Centralized Repository, Intelligent Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Income Assessment Report Compensation Structure Elements PDF
This slide tabulates the compensation structure chart which defines various compensation and addition benefits provided to the employees in various ways.Presenting Income Assessment Report Compensation Structure Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Annual Guaranteed, Retirement Benefits, Guaranteed Bonus. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
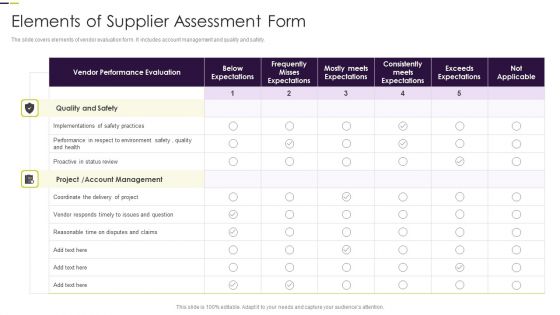
Elements Of Supplier Assessment Form Slides PDF
The slide covers elements of vendor evaluation form. It includes account management and quality and safety.Pitch your topic with ease and precision using this Elements Of Supplier Assessment Form Slides PDF. This layout presents information on Vendor Performance, Below Expectations, Misses Expectations. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
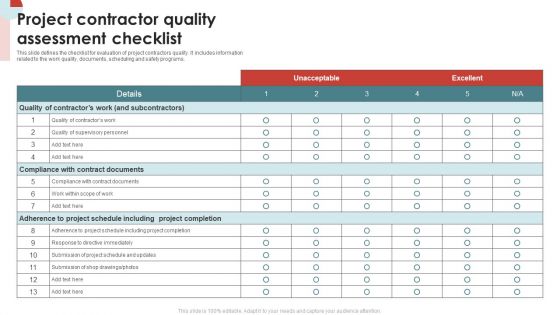
Project Contractor Quality Assessment Checklist Slides PDF
This slide defines the checklist for evaluation of project contractors quality. It includes information related to the work quality, documents, scheduling and safety programs. Showcasing this set of slides titled Project Contractor Quality Assessment Checklist Slides PDF. The topics addressed in these templates are Project, Quality, Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
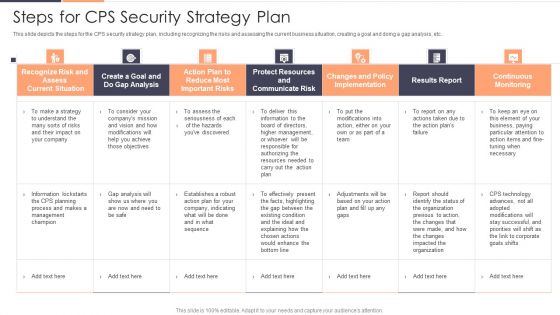
Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF. Use them to share invaluable insights on Recognize Risk, Communicate Risk, Protect Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
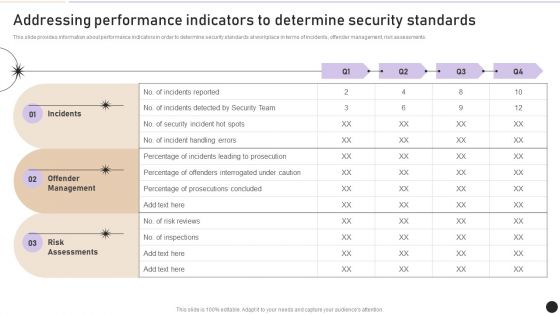
Addressing Performance Indicators To Determine Security Standards Introduction PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Boost your pitch with our creative Addressing Performance Indicators To Determine Security Standards Introduction PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Enterprise Cloud Adoption And Maturity Assessment Model Mockup PDF
This slide showcases enterprise cloud maturity assessment adoption for improve business security. It provides information regarding strategic goals, factors and impact analysis. Showcasing this set of slides titled Enterprise Cloud Adoption And Maturity Assessment Model Mockup PDF. The topics addressed in these templates are Strategic Goal, Success Factors, Impact. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Flowchart Depicting Vendor Verification System Assessment Infographics PDF
This slide focuses on the flowchart that depicts the vendor due diligence assessment which covers document submission for security review, vendor shortlisting, compliance, monitoring encryption, ensuring supportive features, evaluating capacity, approval and making final decision, etc. Presenting Flowchart Depicting Vendor Verification System Assessment Infographics PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Required Resources, Conducting Internal Process, Security Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Assessment Of Release Management Process Plan Tools Infographics PDF
The following slide showcases the comparison of various release management tools to select the best alternative. It mainly constitutes of three elements tool name, features failure detection, risk minimization, security and compliance and cost. Presenting Comparative Assessment Of Release Management Process Plan Tools Infographics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Requires Least, Coding Skills, Cost. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Assessment Tool To Analyze Network Capabilities Pictures Pdf
This slide showcase assessment tool to analyze network competency that helps organization to secure network loop holes. It includes elements such as assessment tools, capabilities, free trail period and cost.Showcasing this set of slides titled Assessment Tool To Analyze Network Capabilities Pictures Pdf The topics addressed in these templates are Examine Network, Flexible Assessment, Recovery Capabilities All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
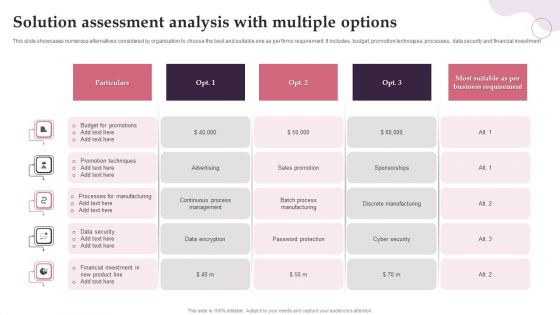
Solution Assessment Analysis With Multiple Options Sample PDF
This slide showcases numerous alternatives considered by organization to choose the best and suitable one as per firms requirement. It includes, budget, promotion techniques, processes, data security and financial investment. Showcasing this set of slides titled Solution Assessment Analysis With Multiple Options Sample PDF. The topics addressed in these templates are Budget, Manufacturing, Promotion Techniques. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Assessment Of Financial Management Software Brochure PDF
This slide showcases comparative analysis of top financial management software. It provides details Bonsai, Mint, Moneydance, Honeydue, accounting automation, financial reports, financial data security, etc. Find a pre-designed and impeccable Comparative Assessment Of Financial Management Software Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF
Mentioned slide displays a five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF bundle. Topics like Assess Security, Gap Analysis, Gap Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Slidegeeks is here to make your presentations a breeze with Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Malware Assessment Process To Prevent Future Cyberattacks Structure PDF
This slide represents malware analysis insights which benefit organizations to mitigate threat and prevent future occurrences. Steps included in this slide are expanding malware sample size, utilizing automation and secure environment, analyzing malware, etc. Presenting Malware Assessment Process To Prevent Future Cyberattacks Structure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Expand Malware Sample, Utilize Secure Environment, Capture Store Virtual. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparative Assessment Of Logistics Service Firm Professional PDF
This slide shows comparative analysis of logistics services firm. It provides information about express delivery, cash on delivery, bulk shipping, exchange logistics, secured delivery, fulfilment, etc. Showcasing this set of slides titled Comparative Assessment Of Logistics Service Firm Professional PDF. The topics addressed in these templates are Technological, Services, Delivery. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Info Safety And ISO 27001 Risk Assessment Worksheet Ppt PowerPoint Presentation File Slideshow PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Risk Assessment Worksheet Ppt PowerPoint Presentation File Slideshow PDF bundle. Topics like Risk Encountered, Vulnerability, Asset And Consequences, Risk To Firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF
The following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Want to ace your presentation in front of a live audience Our Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Comparative Assessment Of Cloud And Traditional Project Management Microsoft PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc.There are so many reasons you need a Comparative Assessment Of Cloud And Traditional Project Management Microsoft PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Preliminary Risk Assessment For New Design FMEA Techniques For Process Assessment Background PDF
The slide provides risk assessment of a new design with the help of risk assessment table. The table covers system hierarchy and points or ranking 1 for lower risk, 2 for moderate risk and 3 for higher risk for various criteria such as safety concern, new technology, field concern, regulatory concern etc.Deliver and pitch your topic in the best possible manner with this Preliminary Risk Assessment For New Design FMEA Techniques For Process Assessment Background PDF. Use them to share invaluable insights on Manufacturing Process, Manufacturer Supplier, Usage Environment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Assessment Of Retail Store Inventory Stockout And Overstock Status Retail Outlet Performance Assessment Topics PDF
This slide illustrates the current assessment of the stockout and overstock status of multiple products. It also provides information regarding on hand quantity, days of supply, and safety stock.Deliver and pitch your topic in the best possible manner with this Assessment Of Retail Store Inventory Stockout And Overstock Status Retail Outlet Performance Assessment Topics PDF. Use them to share invaluable insights on Inventory Imbalances, Overstock, Safety Stock and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Retail Store Inventory Safety Stock Assessment Retail Outlet Performance Assessment Themes PDF
This slide shows the current performance of inventory operations providing information regarding customer and predicted demand, excess and deficit values, desired and actual safety stocks in days along with the forecast accuracy.Deliver and pitch your topic in the best possible manner with this Retail Store Inventory Safety Stock Assessment Retail Outlet Performance Assessment Themes PDF. Use them to share invaluable insights on Customer Demand, Predicted Demand, Actual Safety and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Risk Analysis With Reviewing And Improving Ppt PowerPoint Presentation Professional Graphics Download PDF
Persuade your audience using this security risk analysis with reviewing and improving ppt powerpoint presentation professional graphics download pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including assessing security risks, reviewing and improving, monitoring and recording. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF
Presenting Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Scenario Assessment, Security Capabilities, Overview Of Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Information Security Contd Ppt Show Topics PDF
This is a table of contents for information security contd ppt show topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, requirement, data security, data risk assessment, steps for mitigation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
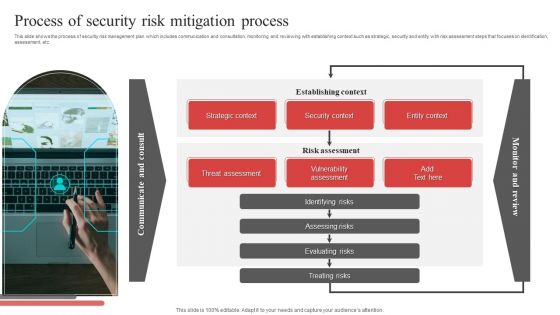
Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide shows the process of security risk management plan which includes communication and consultation, monitoring and reviewing with establishing context such as strategic, security and entity with risk assessment steps that focuses on identification, assessment, etc. Presenting Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Strategic Context, Security Context, Entity Context, Establishing Context. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
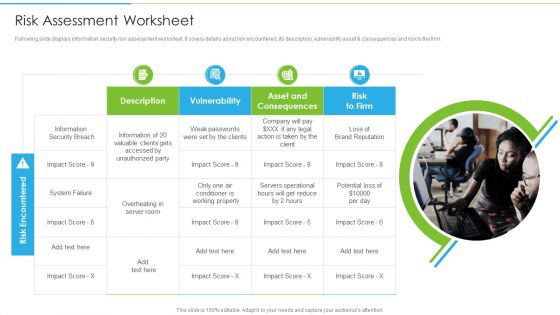
Ways To Accomplish ISO 27001 Accreditation Risk Assessment Worksheet Elements PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm. Presenting Ways To Accomplish ISO 27001 Accreditation Risk Assessment Worksheet Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Asset Consequences, Information Security, Weak Passwords. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
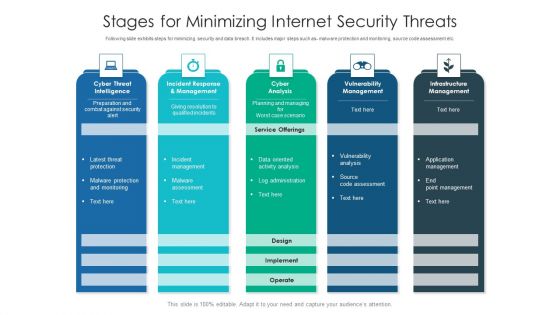
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
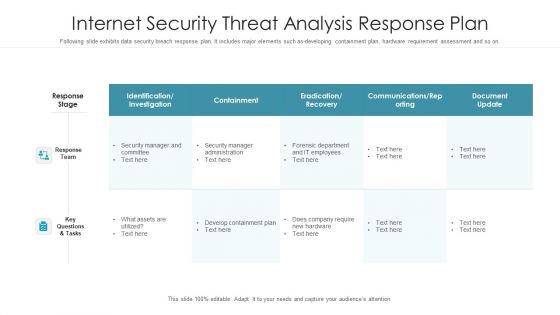
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
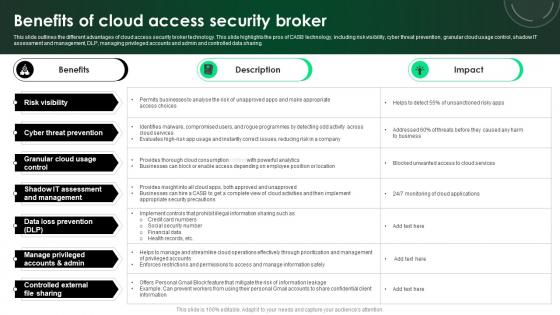
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Unified Security Management Ppt Template Example Of Ppt Presentation
This is a unified security management ppt template example of ppt presentation. This is a four stage process. The stages in this process are assess the network, find threats, data loss prevention, gateway anti virus.
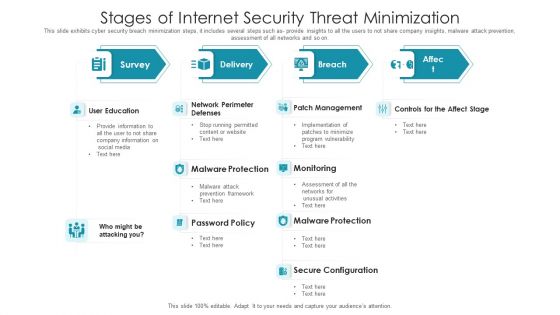
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
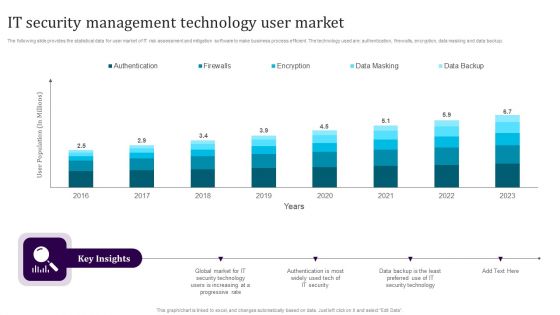
IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
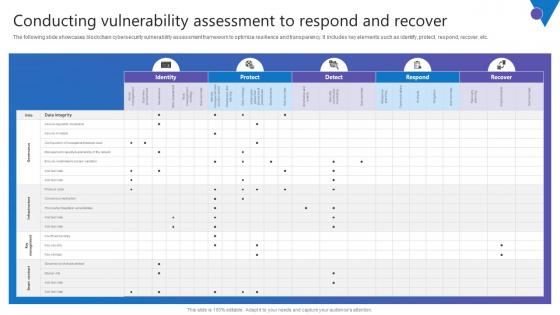
Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf
The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively.This is a IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disasters, Physical Location, Assessment Report. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CASB 2 0 IT Cloud Access Security Broker CASB Introduction
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. This CASB 2 0 IT Cloud Access Security Broker CASB Introduction is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Cloud Access Security Broker CASB Introduction features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
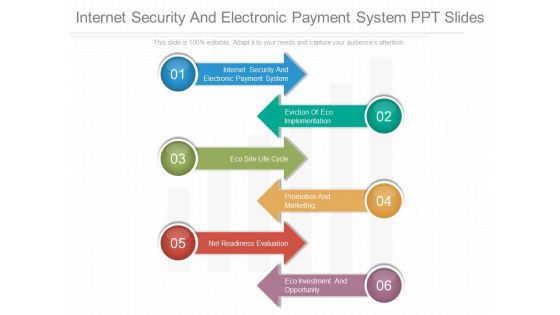
Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.
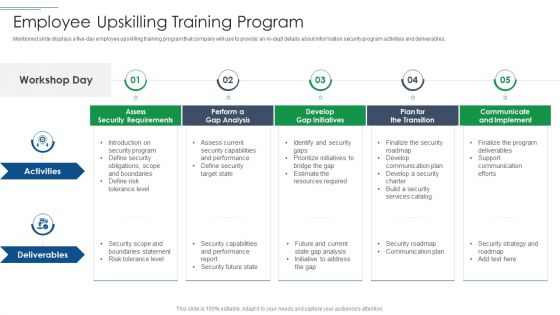
IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. This is a IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Develop Gap Initiatives, Communicate And Implement, Assess Security Requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
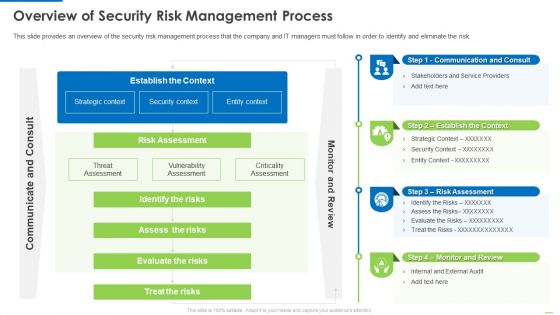
Overview Of Security Risk Management Process Demonstration PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver and pitch your topic in the best possible manner with this Overview of security risk management process demonstration pdf. Use them to share invaluable insights on identify the risks, assess the risks, evaluate the risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home