Data Privacy

Cybersecurity Risk Scorecard Information Security Scorecard For Company With Risk Gap Professional PDF
Presenting cybersecurity risk scorecard information security scorecard for company with risk gap professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protective technology, continuous security monitoring, training of employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Security Training Program Frameworks Contd Rules PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks contd rules pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
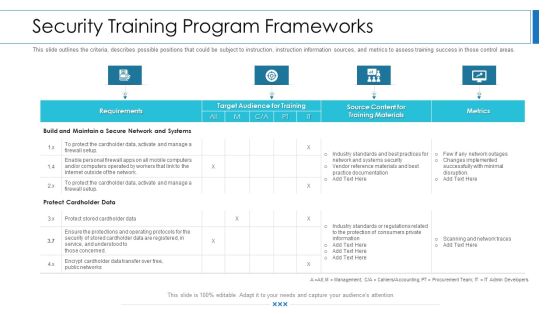
Workforce Security Realization Coaching Plan Security Training Program Frameworks Brochure PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks brochure pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions How Security Concerns Affect Firm In Present Times Structure PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative organizational security solutions how security concerns affect firm in present times structure pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
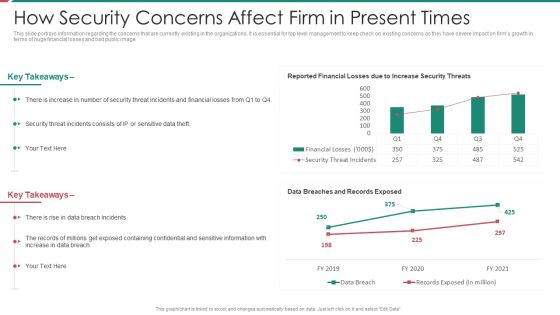
Security And Process Integration How Security Concerns Affect Firm In Present Times Microsoft PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative security and process integration how security concerns affect firm in present times microsoft pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Case Study On Security Improvement Through Security Operations Implementation Mockup PDF
This slide exhibits a case study of the SecOps application in a pharmaceutical company. It includes information about the firm, challenges, solutions, and benefits to a business. Persuade your audience using this Case Study On Security Improvement Through Security Operations Implementation Mockup PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Benefit To Business, Organisation Productivity, Average. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF
Retrieve professionally designed Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.
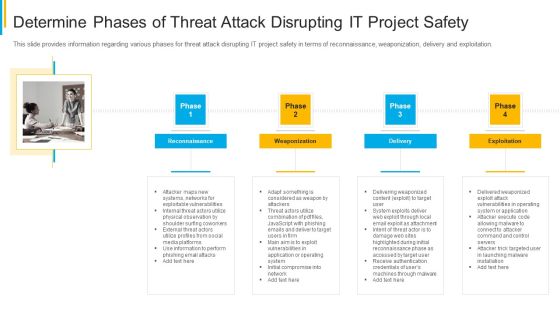
Project Security Administration IT Determine Phases Of Threat Attack Disrupting IT Project Safety Brochure PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a project security administration it determine phases of threat attack disrupting it project safety brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Protected Globe Network Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with protected global network the internet
Yellow Computer Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with yellow computer folder

Hacker Trojan Security PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with background concept of computer trojan horse

Certification Information Technology Professionals IT Certification Roadmap Elements PDF
This template covers IT Certification Roadmap for different levels such as beginners, intermediate, advanced to expert level Deliver an awe inspiring pitch with this creative certification information technology professionals it certification roadmap elements pdf bundle. Topics like information security, software development, project management, network cloud technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Operations Compliance And Security Testing Ppt PowerPoint Presentation Summary Icon
This is a operations compliance and security testing ppt powerpoint presentation summary icon. This is a three stage process. The stages in this process are quality assurance, quality analysis, qa, testing process, bugs analysis.

Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF
This slide covers framework depicting top risks and threats for IIOT disrupting the operations and processes. It also includes integration of different technologies used to increase the security for IIOT operations such as virtual patching, behaviour analysis, anti malware, risk detection, anti spear phishing, spam protection, etc. Pitch your topic with ease and precision using this Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF. This layout presents information on Operational Technology, IT Business Process, Iot Platform Middleware . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

5G Network Applications And Features Security In 5G Technology Architecture Download PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Find highly impressive 5G Network Applications And Features Security In 5G Technology Architecture Download PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download 5G Network Applications And Features Security In 5G Technology Architecture Download PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

KPI Metrics Security Icon With Dashboard Template PDF
Persuade your audience using this KPI Metrics Security Icon With Dashboard Template PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Metrics, Security Icon, Dashboard. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Stakeholder Security Audit And Recognition Icon Demonstration PDF
Persuade your audience using this Stakeholder Security Audit And Recognition Icon Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholder Security Audit, Recognition Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, iot-based attack, malware etc. Do you know about Slidesgeeks Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

CYBER Security Breache Response Strategy Cyber Security Incident Communication Strategy Topics PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Present like a pro with CYBER Security Breache Response Strategy Cyber Security Incident Communication Strategy Topics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
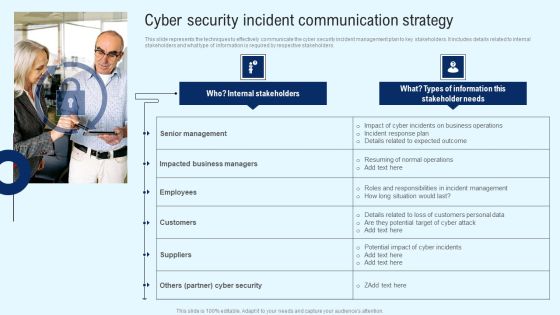
Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
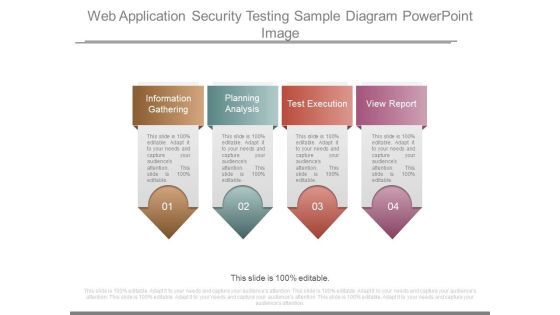
Web Application Security Testing Sample Diagram Powerpoint Image
This is a web application security testing sample diagram powerpoint image. This is a four stage process. The stages in this process are information gathering, planning analysis, test execution, view report.

Addressing Vendor Ecosystem Associated To 5G Structure PDF
This slide provides details regarding vendor ecosystem associated to 5G in terms of open-source flexibility, lock in phenomenon and engaging and strengthening open source vendors. Presenting Addressing Vendor Ecosystem Associated To 5G Structure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Open Source Flexibility, Open Source Vendors, Lock In Phenomenon. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Systems Security And Risk Management Plan Assigning Criticality Rating To Information Assets Ideas PDF
This slide showcases criticality rating that can be allocation to assets for identifying critical assets. Its key elements are asst, failure cost, failure impact and criticality rating. Do you know about Slidesgeeks Information Systems Security And Risk Management Plan Assigning Criticality Rating To Information Assets Ideas PDFThese are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Table Of Contents For IT Threats Response Playbook Clipart PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For IT Threats Response Playbook Clipart PDF. Use them to share invaluable insights on Security Incidents, Figures And Statistics, Ransom Payment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Problems Management And Action Plan Microsoft PDF
The following slide illustrates the cyber security risk management plan to outline business security threats and draft proposed strategies. It also includes elements such as objectives, issues, breach response actions, employee training etc. Persuade your audience using this Cyber Security Problems Management And Action Plan Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Breach Response Actions, Employee Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps For Information System Network And Communication Auditing Topics PDF
The following slide highlights the steps for information system network and communication audit illustrating key headings which includes basic network security, internet security, email security, cyber attack security, security patch and wireless security Presenting Steps For Information System Network And Communication Auditing Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Basic Network Security, Internet Security, Security Patch. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

International Organization Standardization 270001 Dashboard For Information Security Risk Management Pictures PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parcent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative international organization standardization 270001 dashboard for information security risk management pictures pdf bundle. Topics like dashboard for information security risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation And Administration Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of sevnty one slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF. Use them to share invaluable insights on Analysis Progress, Response Progress, Plan Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Agenda For Information Technology Threat Mitigation Methods Background PDF
This is a Agenda For Information Technology Threat Mitigation Methods Background PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise, Organization, Management Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Public And Private Cloud Network Icon With Secure User Information Ppt PowerPoint Presentation Infographic Template Skills PDF
Presenting public and private cloud network icon with secure user information ppt powerpoint presentation infographic template skills pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including public and private cloud network icon with secure user information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Seven Step Ppt PowerPoint Presentation Infographic Template Maker
This is a cyber security seven step ppt powerpoint presentation infographic template maker. This is a seven stage process. The stages in this process are business, management, planning, strategy, marketing.
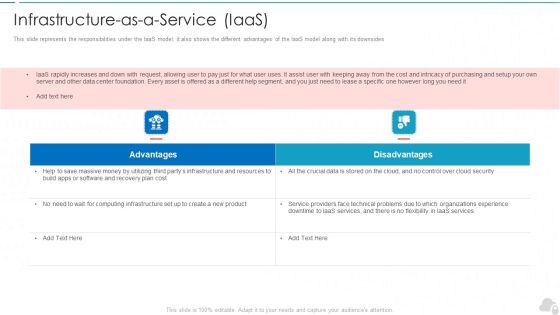
Infrastructure As A Service Iaas Cloud Computing Security IT Ppt Layouts Background Image PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a infrastructure as a service iaas cloud computing security it ppt layouts background image pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advantages, disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Contd Mockup PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a corporate security and risk management determine sequence phases for threat attack contd mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Roles And Responsibilities To Ensure Work Professional PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a corporate security and risk management roles and responsibilities to ensure work professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, unit supervisor manager responsibilities, internal investigations unit responsibilities, human resources responsibilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Threat Intelligence Services Guidelines PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a real time assessment of security threats threat intelligence services guidelines pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global intelligence, local intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Query Slide Diagram For Secure Cash Endowment Rules PDF
Persuade your audience using this query slide diagram for secure cash endowment rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including query slide diagram for secure cash endowment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Icons Slide For IT Security Ppt Icon Graphics Tutorials PDF
Deliver an awe inspiring pitch with this creative icons slide for information technology security ppt professional slideshow pdf bundle. Topics like icons slide for it security ppt icon graphics tutorials pdf can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icon For Payment Security Technology In Market Investor Transactions Summary PDF
Presenting Icon For Payment Security Technology In Market Investor Transactions Summary PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Icon For Payment Security, Technology Market Investor, Transactions Summary. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF
The following slide showcases solution offered by IT company for its customers which are see the new network, know current threats and protect with high ROI. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
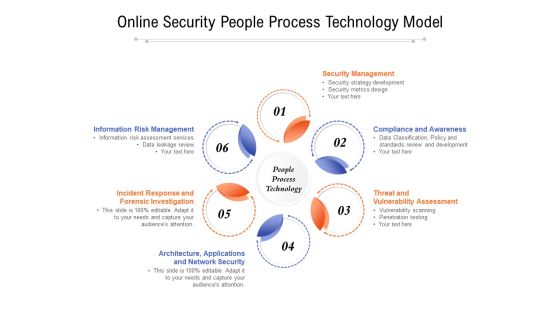
Online Security People Process Technology Model Ppt PowerPoint Presentation Slides Example Introduction PDF
Presenting online security people process technology model ppt powerpoint presentation slides example introduction pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including security management, compliance and awareness, threat and vulnerability assessment, architecture, applications, incident response and forensic investigation, information risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Table Of Contents Ppt Inspiration Professional PDF
Presenting this set of slides with name strategies to mitigate cyber security risks table of contents ppt inspiration professional pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role personnel, cost associated to firm, impact analysis dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Table Of Contents Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name cyber security implementation framework table of contents ppt powerpoint presentation icon portfolio pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role of personnel, cost associated to firm, impact analysis, dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Automation Tools Integration Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes IT Security Automation Tools Integration Ppt PowerPoint Presentation Complete Deck With Slides and has templates with professional background images and relevant content. This deck consists of total of fourty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Table Of Contents Ppt Inspiration Guide PDF
Deliver an awe inspiring pitch with this creative table of contents ppt inspiration guide pdf bundle. Topics like security awareness program, security strategies, budget, communication plan, security awareness, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategic Compliance Safety And Security Management Plan Microsoft PDF
The slide showcases an outline of a plan incorporating compliance strategy that help teams maintain a safe, efficient process, produce quality products and adhere to relevant legal regulations. It covers aspects such as objective, goals, activities, responsible owner, timeframe, status and additional comments. Persuade your audience using this Strategic Compliance Safety And Security Management Plan Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Compliance Plan, It Security, Potential. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
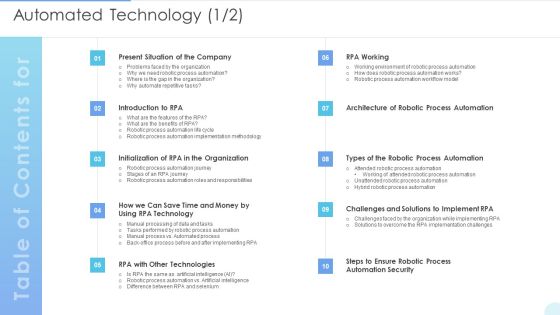
Table Of Contents Automated Technology Diagrams PDF
Deliver an awe inspiring pitch with this creative Table Of Contents Automated Technology Diagrams PDF bundle. Topics like Robotic Process Automation, Automation Security, Technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
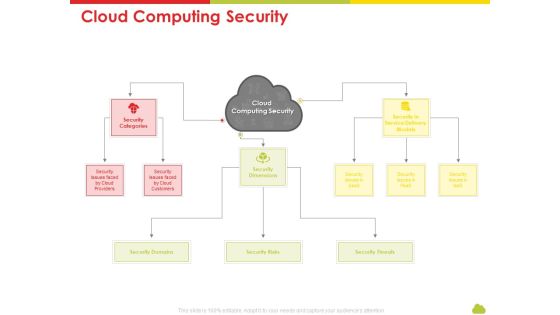
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Security Rules PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan cloud computing security rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like risks, threats, domains, service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Cyber Security Automation Framework Icons PDF
Find a pre designed and impeccable Agenda For Cyber Security Automation Framework Icons PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda IT Security Automation Systems Guide Sample PDF
Find a pre designed and impeccable Agenda IT Security Automation Systems Guide Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Organizations Risk Management And IT Security Portrait PDF
Find a pre designed and impeccable Agenda Organizations Risk Management And IT Security Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Deploying Cyber Security Incident Response Administration Guidelines PDF
Find a pre designed and impeccable Agenda For Deploying Cyber Security Incident Response Administration Guidelines PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Securing Market Leadership Through Competitive Excellence Pictures PDF
Find a pre designed and impeccable Agenda Securing Market Leadership Through Competitive Excellence Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Cyber Security Breache Response Strategy Slides PDF
Find a pre designed and impeccable Agenda For Cyber Security Breache Response Strategy Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Implementing Cyber Security Incident Management Template PDF
Find a pre designed and impeccable Agenda Implementing Cyber Security Incident Management Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cloud Technology Risks With Security Incident Management Ppt PowerPoint Presentation Gallery Graphics Template PDF
Presenting cloud technology risks with security incident management ppt powerpoint presentation gallery graphics template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification and allowance, management interface vulnerability, security incident management, application security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home