Data Privacy

IT Security Hacker Regaining Reputation Of Our Company Infographics PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies.This is a IT Security Hacker Regaining Reputation Of Our Company Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers And Clients, Appropriate Service, Database Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Cyber Security Breach General Consequences Ideas PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. This is a Impact Of Cyber Security Breach General Consequences Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reputational Damage, Monetary Penalty, Operational Disruption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Our Business Approach Diagrams PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. This is a Security Agency Business Profile Our Business Approach Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Planning, Participatory Management, Productivity Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Our Global Presence Inspiration PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. This is a Manpower Corporate Security Business Profile Our Global Presence Inspiration PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Our Global Presence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Case Study Mockup PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. This is a Manpower Corporate Security Business Profile Case Study Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Solution, Benefits, The Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Organization Chart Rules PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. This is a Manpower Corporate Security Business Profile Organization Chart Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Operations Supervisor, Audit Team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Developing Firm Security Strategy Plan Addressing Different Security Priorities At Organization Business Formats PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of people security, intellectual property, brand protection, crisis management, corporate governance and information security. Presenting developing firm security strategy plan addressing different security priorities at organization business formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security of people, corporate governance, intellectual property, information security, brand protection, crisis management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
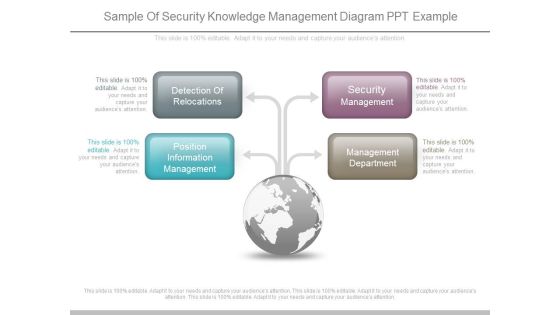
Sample Of Security Knowledge Management Diagram Ppt Example
This is a sample of security knowledge management diagram ppt example. This is a four stage process. The stages in this process are detection of relocations, position information management, security management, management department.

Best Practices To Optimize Growth And Development Program Information PDF
The following slide highlights some major ways to improve training and development program at workspace. It includes activities such as job swap, inviting industry specialist, access to free learning resources, right of ownership etc. Presenting Best Practices To Optimize Growth And Development Program Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Entrepreneur Activities, Right Of Ownership, Industry Awareness. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
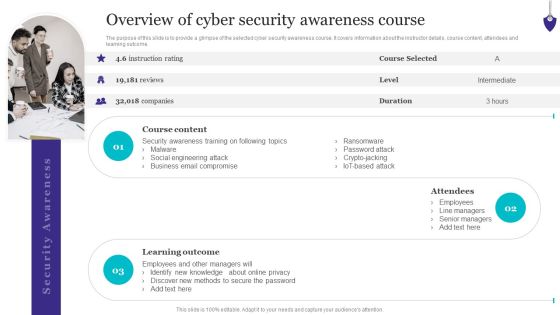
Organizing Security Awareness Overview Of Cyber Security Awareness Course Template PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Organizing Security Awareness Overview Of Cyber Security Awareness Course Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Organizing Security Awareness Overview Of Cyber Security Awareness Course Template PDF.
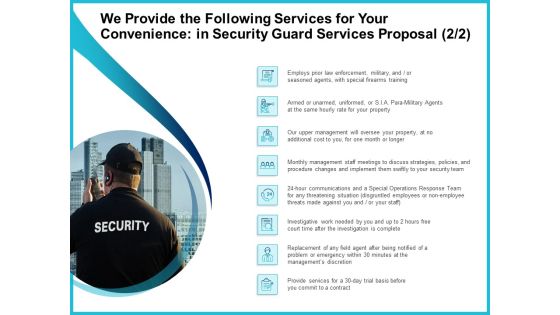
Uniformed Security We Provide The Following Services For Your Convenience In Security Guard Services Proposal Formats PDF
Deliver an awe inspiring pitch with this creative uniformed security we provide the following services for your convenience in security guard services proposal formats pdf bundle. Topics like training, strategies, policies, management, investigative can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Safety And Security Incident Report Writing Tips Pictures PDF
This slide shows tips which can be used to prepare security incident report. These tips are include proof, observe and utilize software. Persuade your audience using this Safety And Security Incident Report Writing Tips Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Include Proof, Observe, Utilize Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Security Software Company Investor Funding Elevator Pitch Deck Table Of Contents Demonstration PDF
Boost your pitch with our creative Security Software Company Investor Funding Elevator Pitch Deck Table Of Contents Demonstration PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Security Incident Response Plan Timeline Mockup PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Incident Response Plan Timeline Mockup PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
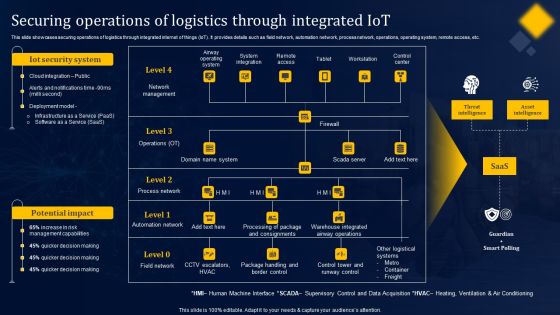
Securing Operations Of Logistics Through Integrated Iot Structure PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Securing Operations Of Logistics Through Integrated Iot Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
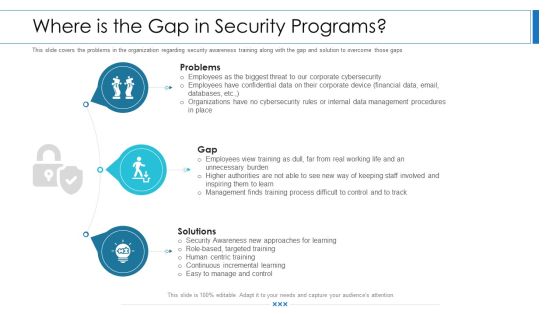
Workforce Security Realization Coaching Plan Where Is The Gap In Security Programs Ppt Show Master Slide PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a workforce security realization coaching plan where is the gap in security programs ppt show master slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Are you searching for a Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF from Slidegeeks today.

Cyber Security Automation Framework Ppt PowerPoint Presentation Complete With Slides
In the rainbow of business colours of any PPT Presentation, it is important to realise that structure and framework is the real pain point that the customer wants to resolve through a presentation. Our products are the answer, as illustrated through this Cyber Security Automation Framework Ppt PowerPoint Presentation Complete With Slides. Learn how the structure of a business presentation is to be fleshed out using this forty two slide complete deck. Examine the relevance of concepts like business planning, market strategies and customer pain points etc to arrive at a comprehensive understanding of the needs of all stakeholders. This can serve as the master blueprint to help you analyze any business scenario you may face. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

Table Of Contents Organizations Risk Management And IT Security Workplace Elements PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Organizations Risk Management And IT Security Workplace Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
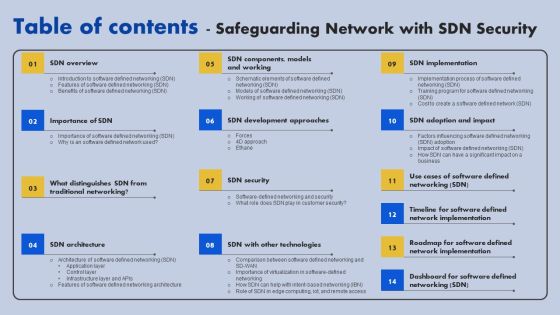
Table Of Contents Safeguarding Network With SDN Security Ppt Ideas Design Ideas PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Safeguarding Network With SDN Security Ppt Ideas Design Ideas PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
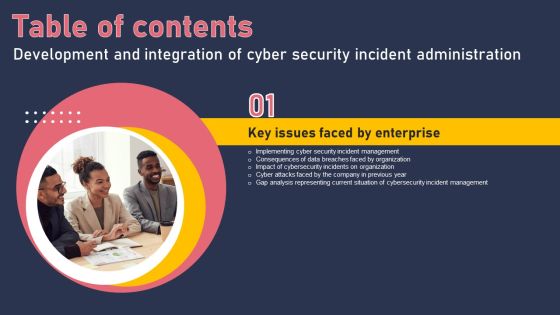
Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF
Want to ace your presentation in front of a live audience Our Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
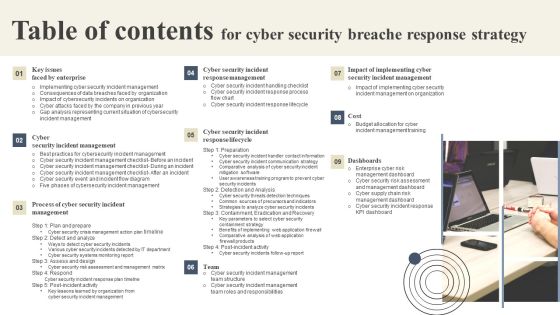
Table Of Contents For Cyber Security Breache Response Strategy Formats PDF
Want to ace your presentation in front of a live audience Our Table Of Contents For Cyber Security Breache Response Strategy Formats PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Home Security System Vector Icon Ppt PowerPoint Presentation File Influencers
Presenting this set of slides with name home security system vector icon ppt powerpoint presentation file influencers. This is a four stage process. The stages in this process are iot icon, smartphone vector, headphones. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Formation Of Acquired Entities Security Ppt PowerPoint Presentation Portfolio Images
Presenting this set of slides with name formation of acquired entities security ppt powerpoint presentation portfolio images. This is a four stage process. The stages in this process are formation, entities, business, development, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Vector Icon Ppt PowerPoint Presentation Ideas Example File
Presenting this set of slides with name cyber security vector icon ppt powerpoint presentation ideas example file. This is a one stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide Implementing Cyber Security Incident Management Graphics PDF
Introducing our well designed Icons Slide Implementing Cyber Security Incident Management Graphics PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812
Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with bank with computer mouse

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Information Technology Touch Points With Technical Solutions Topics PDF
This slide covers IT pain points which are faced by companies with various solutions to overcome these barriers. These includes information security, high turnover rates, IT compliances, and lack of expertise. Pitch your topic with ease and precision using this Key Information Technology Touch Points With Technical Solutions Topics PDF. This layout presents information on Information Security, High Turnover Rates, Lack Expertise. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Info Safety And ISO 27001 Risk Assessment Worksheet Ppt PowerPoint Presentation File Slideshow PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Risk Assessment Worksheet Ppt PowerPoint Presentation File Slideshow PDF bundle. Topics like Risk Encountered, Vulnerability, Asset And Consequences, Risk To Firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Information And Security Risk Mitigation Strategy Ppt PowerPoint Presentation File Format PDF
Persuade your audience using this business information and security risk mitigation strategy ppt powerpoint presentation file format pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including business information and security risk mitigation strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Introduction To Secure Digital Wallets For Financial Transactions Guidelines PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Want to ace your presentation in front of a live audience Our Introduction To Secure Digital Wallets For Financial Transactions Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Secure Access Service Edge SASE Architecture Ppt Inspiration Grid PDF
This slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. This Secure Access Service Edge SASE Architecture Ppt Inspiration Grid PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

IT Security Hacker Phases Of Hacking Topics PDF
This slide represents the phases of hacking, including reconnaissance, scanning, gaining access to the victims computer, maintaining access, and clearing tracks.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Phases Of Hacking Topics PDF. Use them to share invaluable insights on Maintaining Access, Reconnaissance, Gaining Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Purpose Of Ethical Hacking Slides PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Purpose Of Ethical Hacking Slides PDF. Use them to share invaluable insights on Vulnerabilities Discovered, Malevolent Hackers, Malevolent Hackers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF
Welcome to our selection of the Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF
Slidegeeks is here to make your presentations a breeze with Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Table Of Contents For Mobile Banking For Convenient And Secure Online Payments Ppt Ideas Shapes PDF
Slidegeeks is here to make your presentations a breeze with Table Of Contents For Mobile Banking For Convenient And Secure Online Payments Ppt Ideas Shapes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Table Of Contents Enhancing Cloud Security With CASB Ppt PowerPoint Presentation File Deck PDF
Present like a pro with Table Of Contents Enhancing Cloud Security With CASB Ppt PowerPoint Presentation File Deck PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Quarter Wise Business Progress With Teamwork Ppt PowerPoint Presentation File Information PDF
Persuade your audience using this quarter wise business progress with teamwork ppt powerpoint presentation file information pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 2019 to 2020, process, teamwork, global, security, time. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Financing Catalogue For Security Underwriting Agreement IPO Roadshow Topics PDF
The slide provides an overview of the IPO Roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc. This is a financing catalogue for security underwriting agreement ipo roadshow topics pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merchant bankers, portfolio managers, financials institutions, foreign investors, insurance companies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Workplace Employee Assistance Program Structure PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a project security administration it workplace employee assistance program structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Prepare A Disaster Recovery Plan Demonstration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a desktop security management prepare a disaster recovery plan demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, location, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. This is a Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Case Undersubscription, Interested Investors, Normal Subscription You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively.This is a IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disasters, Physical Location, Assessment Report. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetxary penalty and operational disruption. If you are looking for a format to display your unique thoughts, then the professionally designed Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
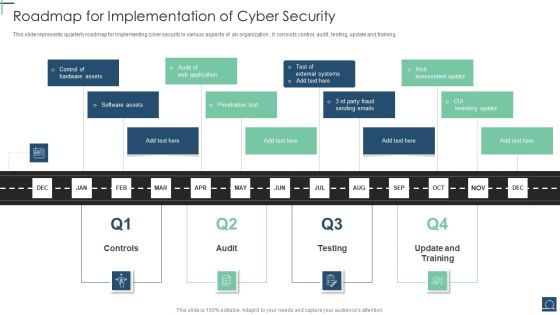
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
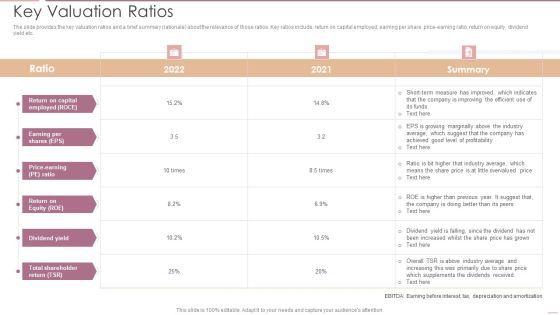
Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF
The slide provides the key valuation ratios and a brief summary rationale about the relevance of those ratios. Key ratios include return on capital employed, earning per share, price-earning ratio, return on equity, dividend yield etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF Use them to share invaluable insights on Measure Improved, Dividends Received, Total Shareholder and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF
The slide provides the key unique points product differentiation of the products comparing to its competitors. Key points include low product cost, large portfolio of assets under management, industry experience etc. Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF. Use them to share invaluable insights on Under Management, Transaction Cost, Minimum Transaction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF
This slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Take your projects to the next level with our ultimate collection of SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Computer Security Incident Handling Cyber Security Governance Ppt Gallery Summary PDF
Presenting this set of slides with name computer security incident handling cyber security governance ppt gallery summary pdf. The topics discussed in these slides are senior management, business strategy, security objectives, implementation, security requirements, risk management or information security strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

 Home
Home