Data Privacy

Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
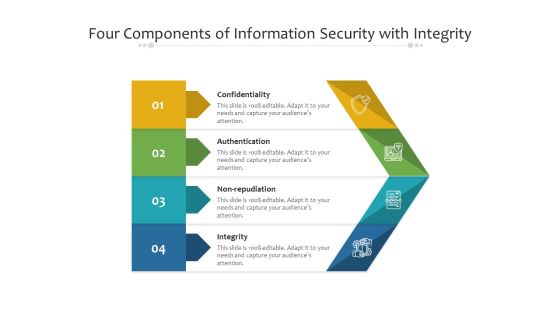
Four Components Of Information Security With Integrity Ppt PowerPoint Presentation File Gallery PDF
Presenting four components of information security with integrity ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including confidentiality, authentication, integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Securing Market Leadership Through Competitive Excellence What Is Red Ocean Strategy Formats PDF
The following slide exhibits introduction to red ocean strategy. Information covered in this slide is related to definition of red ocean strategy along with the key features. Find highly impressive Securing Market Leadership Through Competitive Excellence What Is Red Ocean Strategy Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Securing Market Leadership Through Competitive Excellence What Is Red Ocean Strategy Formats PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cyber Security Operations Center With Integrated Security Framework Ppt Gallery Graphics Design PDF
Showcasing this set of slides titled cyber security operations center with integrated security framework ppt gallery graphics design pdf. The topics addressed in these templates are security, framework, management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
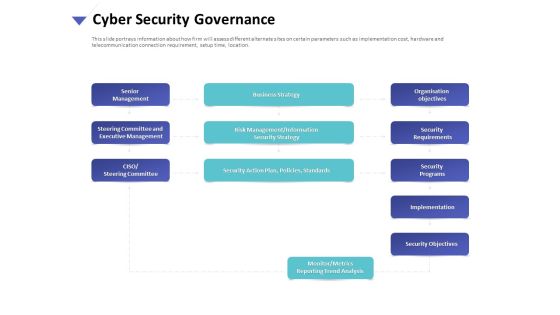
Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Agenda For Information Systems Security And Risk Management Plan Designs PDF
Find a pre-designed and impeccable Agenda For Information Systems Security And Risk Management Plan Designs PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Slidegeeks has constructed Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Circle With Icons Of Law Time And Security PowerPoint Templates
This creative business PowerPoint slide is designed with icons of law time and security. Use this slide to display information in visual manner. Use this diagram in business presentations to give better impact.

Business Information Technology Management Ppt Images
This is a business information technology management ppt images. This is a five stage process. The stages in this process are bpms, applications, communications, information security, infrastructure and operations.
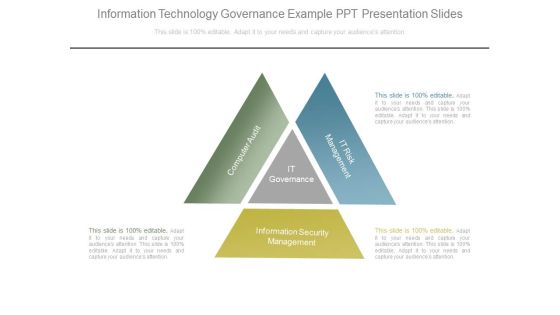
Information Technology Governance Example Ppt Presentation Slides
This is a information technology governance example ppt presentation slides. This is a three stage process. The stages in this process are computer audit, it governance, it risk management, information security management.

Roles And Responsibilities Of Cyber Security Team Designs PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide.This is a Roles And Responsibilities Of Cyber Security Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Operations Manager, Risk Manager . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
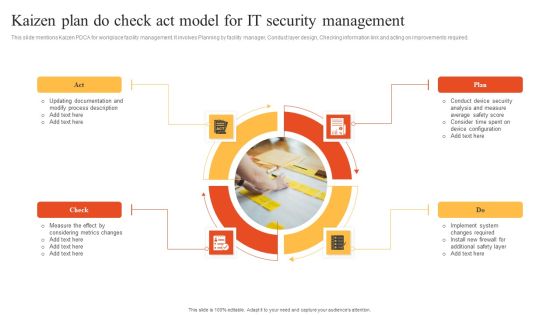
Kaizen Plan Do Check Act Model For IT Security Management Information PDF
This slide mentions Kaizen PDCA for workplace facility management. It involves Planning by facility manager, Conduct layer design, Checking information link and acting on improvements required. Presenting Kaizen Plan Do Check Act Model For IT Security Management Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Check, Plan, Act. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Workforce Security Realization Coaching Plan Idea Generation Ppt Infographics Display PDF
This is a workforce security realization coaching plan idea generation ppt infographics display pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like idea generation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF.
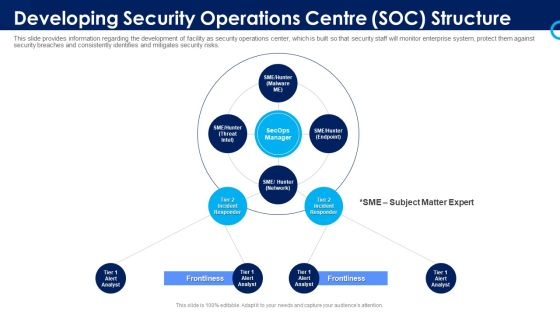
Organizational Security Solutions Developing Security Operations Centre SOC Structure Introduction PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting organizational security solutions developing security operations centre soc structure introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
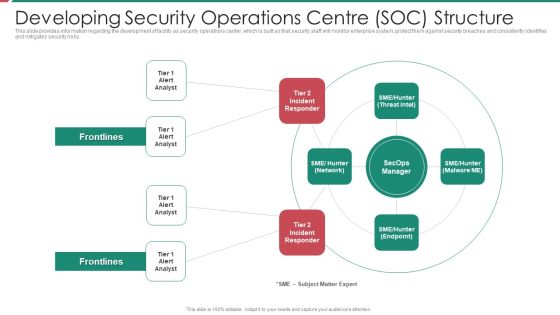
Security And Process Integration Developing Security Operations Centre SOC Structure Inspiration PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting security and process integration developing security operations centre soc structure inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Introducing Security At Workplace To Ensure Assets Safety Introduction PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Presenting developing firm security strategy plan introducing security at workplace to ensure assets safety introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security policy, organizational strategy, security mission statement, strategic security objectives. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
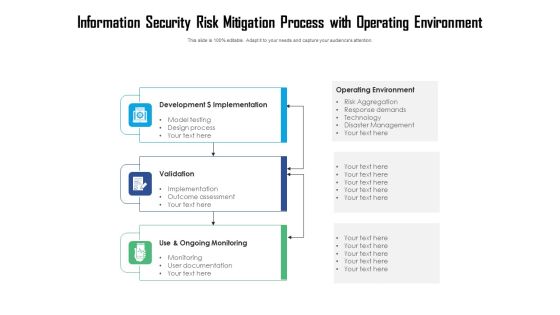
Information Security Risk Mitigation Process With Operating Environment Ppt PowerPoint Presentation File Templates PDF
Persuade your audience using this information security risk mitigation process with operating environment ppt powerpoint presentation file templates pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including development dollar implementation, validation, use and ongoing monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
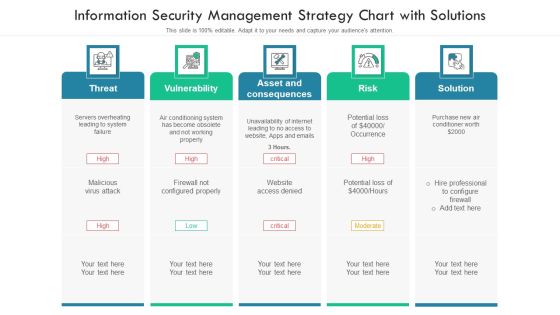
Information Security Management Strategy Chart With Solutions Ppt PowerPoint Presentation File Slides PDF
Persuade your audience using this information security management strategy chart with solutions ppt powerpoint presentation file slides pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including threat, vulnerability, risk, solution. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Risk Mitigation Strategy With Problem Statement Ppt PowerPoint Presentation File Background Image PDF
Persuade your audience using this information security risk mitigation strategy with problem statement ppt powerpoint presentation file background image pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including problem statement, business solution, hayes methodology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.

Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Folder With Arrow Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with illustration of blue glass folder with white arrow

Protected Email Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with brass key inserted into a large chrome at/email symbol

Computer Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with yellow computer folder with shield

Protected Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with folder

Protection Question Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with laptop with question mark

Person Browsing Securely Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with person sitting on the floor, chatting using a notebook

Person Browsing Securely Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with person sitting on the floor, chatting using a notebook

Security Functioning Centre Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fifty six slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Desktop Security Management Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF.

Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Techniques And Strategies To Reduce Security Management Risks Security Risk Management Assessment Checklist Demonstration PDF
This slide shows a security risk management assessment checklist with multiple categories.Presenting techniques and strategies to reduce security management risks security risk management assessment checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, responding to security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Development And Integration Of Cyber Security Incident Administration Information PDF
Slidegeeks is here to make your presentations a breeze with Agenda Development And Integration Of Cyber Security Incident Administration Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Growth Guidelines PDF
This slide portrays information regarding the dashboard that firm will track various security incidents detected. These incidents will be managed in order to avoid security risks. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan security incidents tracking dashboard growth guidelines pdf. Use them to share invaluable insights on number of open security incidents, open security incidents by age, average age of open security incidents, security incident backlog growth and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
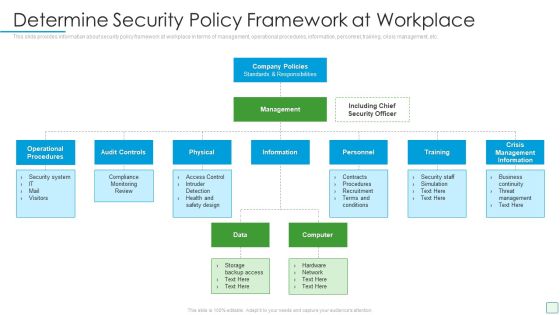
Developing Firm Security Strategy Plan Determine Security Policy Framework At Workplace Template PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Presenting developing firm security strategy plan determine security policy framework at workplace template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like operational procedures, audit controls, physical, training, crisis management information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
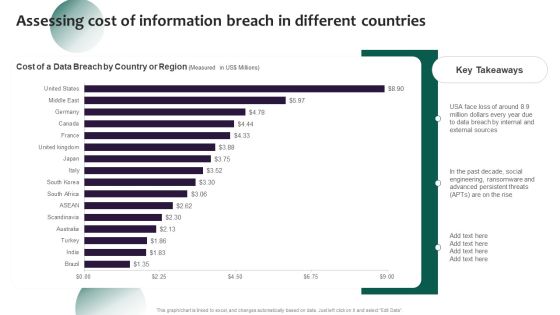
Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Key Takeaways, Countries, Region and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

IT Security Main Steps Of Operational Security Ppt Show Design Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting it security main steps of operational security ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like assessment of risks, potential threats, sensitive information, analyze security holes and vulnerabilities, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
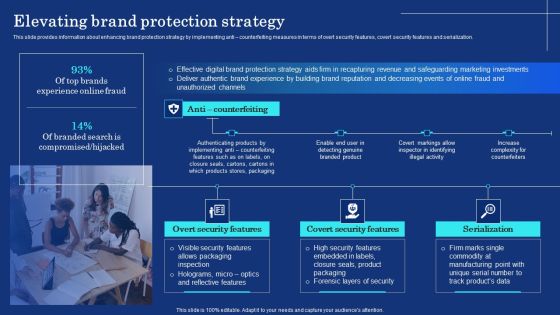
Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

E Payment Transaction System Payment Security And Fraud Management Solutions Development Professional PDF
This is a E payment transaction system payment security and fraud management solutions development professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recognizing users and streamlining the payments process with zero added friction, operational costs, software development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workforce Security Realization Coaching Plan Post It Notes Ppt Slides Graphics Template PDF
This is a workforce security realization coaching plan post it notes ppt slides graphics template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
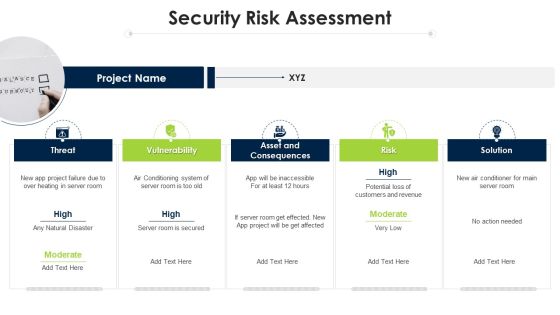
Program Evaluation Templates Bundle Security Risk Assessment Ppt Infographic Template Brochure PDF
This is a program evaluation templates bundle security risk assessment ppt infographic template brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like solution, risk, asset and consequences, vulnerability, threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Log Management Services Metrics Slides PDF
This is a real time assessment of security threats log management services metrics slides pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configurations, log management, metrics, virtualization, databases. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
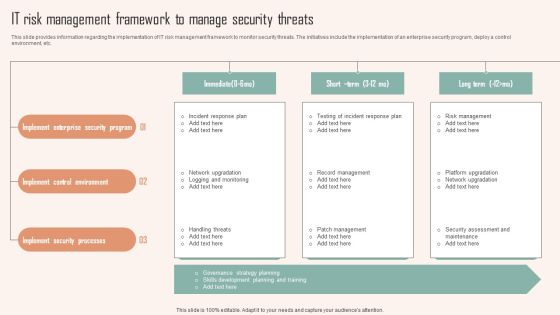
IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Are you searching for a IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Risk Management Framework To Manage Security Threats Ppt PowerPoint Presentation File Outline PDF from Slidegeeks today.

Cyber Exploitation IT Use Of Security Programs Mockup PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing The Various Security Incidents And Attacks Icons PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.Create an editable Addressing The Various Security Incidents And Attacks Icons PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing The Various Security Incidents And Attacks Icons PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Virtual Coinage Icon For Secured Payment System Professional PDF
Presenting Virtual Coinage Icon For Secured Payment System Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Virtual Coinage Icon, Secured Payment System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
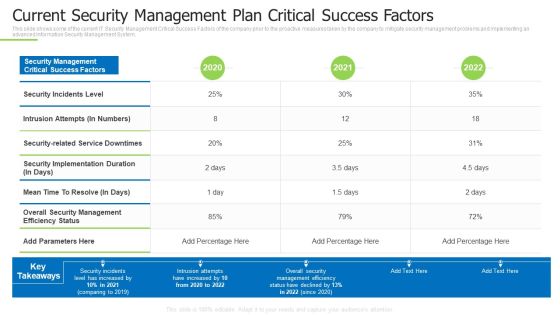
Techniques And Strategies To Reduce Security Management Risks Current Security Management Plan Ideas PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks current security management plan ideas pdf bundle. Topics like intrusion attempts, overall security management, security incidents level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
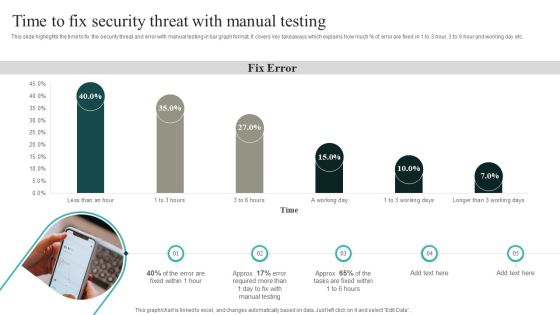
IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF

Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
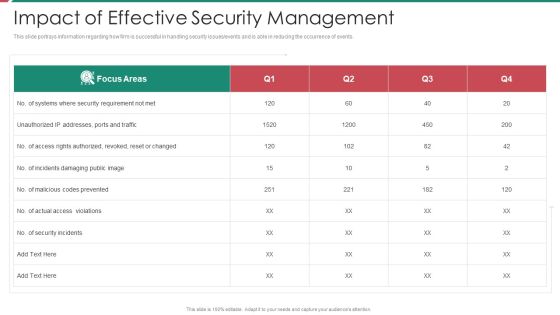
Security And Process Integration Impact Of Effective Security Management Topics PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative security and process integration impact of effective security management topics pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Effective Security Management At Workplace Structure PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan effective security management at workplace structure pdf. Use them to share invaluable insights on effective security management at workplace and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home