AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Caution
Caution

IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Presenting IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Compromise Security, Information Accessed, Existing Resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Real Time Incident Management Dashboard Formats PDF
Following slide illustrate KPI dashboard that can be used by organizations to track real time incident data. Kpis covered are number of tickets, average resolution time per customer, incidents registered per month. Presenting IT Threats Response Playbook Real Time Incident Management Dashboard Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Resolved Tickets, Average Resolution, Incidents Registered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware.This is a Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compromise Scams, Ransomware, Confidential Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Fraud Overview Types Facts And Statistics Fraud Threat Administration Guide Icons PDF
This slide provides an overview about corporate frauds along with the factual information of global fraud events. It also includes the statistics on fraud volume as well as fraud value.Deliver and pitch your topic in the best possible manner with this Corporate Fraud Overview Types Facts And Statistics Fraud Threat Administration Guide Icons PDF. Use them to share invaluable insights on Experienced Fraud, Event Past, Experienced Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Versus Target Level Assessment For Anti Fraud Program Fraud Threat Administration Guide Microsoft PDF
Following slide depicts information about the various levels of an enterprise anti-fraud program. It also delineates details about the organizations current versus targeted level in relation to various program attributes.Deliver an awe inspiring pitch with this creative Current Versus Target Level Assessment For Anti Fraud Program Fraud Threat Administration Guide Microsoft PDF bundle. Topics like Programmed Attribute, Fraud Investigation, Monitoring Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide.This is a Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Compromise, Ransomware, Malicious Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. This is a Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Detection Operation Controls, Preventive Operation Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist For Business Disaster Threat Recovery Plan Ppt Inspiration Design Ideas PDF
The given below slide depicts a checklist to successfully implement disaster recovery plan. It includes elements such as BIA, RTO, response strategy, recovery site, response team, maintenance and testing. Presenting Checklist For Business Disaster Threat Recovery Plan Ppt Inspiration Design Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Elements, Business Impact Analysis, Response Strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Average Costing On Threats Management For Data Breach Incident Demonstration PDF
This slide covers total cost incurred on response of data breach incident. It includes four categories such as incident detection and escalation, notifications, post breach response, lost business cost ,etc. Pitch your topic with ease and precision using this Average Costing On Threats Management For Data Breach Incident Demonstration PDF. This layout presents information on Lost Business Cost, Detection And Escalation, Notification. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF
This slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Pitch your topic with ease and precision using this Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF. This layout presents information on Number Breach, Total Incidents, Malicious Insider. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
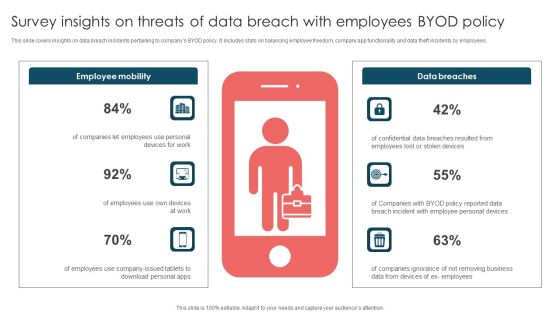
Survey Insights On Threats Of Data Breach With Employees Byod Policy Brochure PDF
This slide covers insights on data breach incidents pertaining to companys BYOD policy. It includes stats on balancing employee freedom, company app functionality and data theft incidents by employees. Presenting Survey Insights On Threats Of Data Breach With Employees Byod Policy Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Employee Mobility, Data Breaches, Employees Use. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
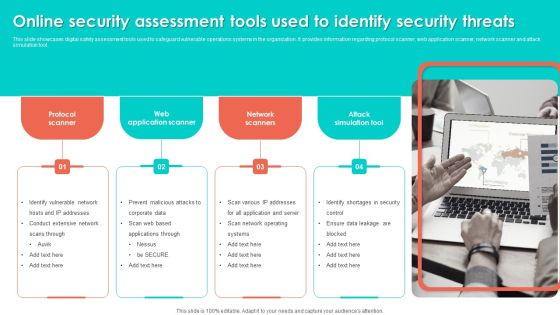
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Industry Report Of Packaged Food Products Part 1 General Mills Threats Sample PDF
Present like a pro with Industry Report Of Packaged Food Products Part 1 General Mills Threats Sample PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Overview On Mitigating Workplace IT Threats Ppt PowerPoint Presentation Complete Deck With Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Overview On Mitigating Workplace IT Threats Ppt PowerPoint Presentation Complete Deck With Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has twenty one slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance.

Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides
Arouses curiosity in the audience is the USP of this Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides. The image shown compliments the text provided. The holistic image conveys the message that we are on to something important, the deep world of business communication training. Download it now, and as always customize and edit each of the sixty five slides as per convenience and the data and the experience you are comfortable sharing with your audience.
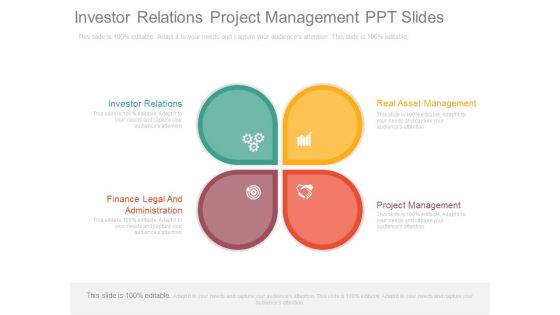
Investor Relations Project Management Ppt Slides
This is a investor relations project management ppt slides. This is a four stage process. The stages in this process are investor relations, finance legal and administration, real asset management, project management.

Actual Time Transaction Monitoring Software And Strategies Why Is Transaction Monitoring Essential Portrait PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Slidegeeks is here to make your presentations a breeze with Actual Time Transaction Monitoring Software And Strategies Why Is Transaction Monitoring Essential Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Business Case Template Improvements Business Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name business case template improvements business ppt powerpoint presentation complete deck. The topics discussed in these slides are problem, risk, improvements, business, alternative. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
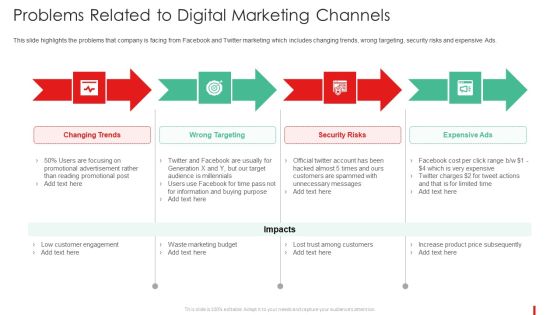
Promotion Guide To Advertise Brand On Youtube Problems Related To Digital Marketing Channels Sample PDF
This slide highlights the problems that company is facing from Facebook and Twitter marketing which includes changing trends, wrong targeting, security risks and expensive Ads.This is a Promotion Guide To Advertise Brand On Youtube Problems Related To Digital Marketing Channels Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Promotional Advertisement, Reading Promotional, Increase Product You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
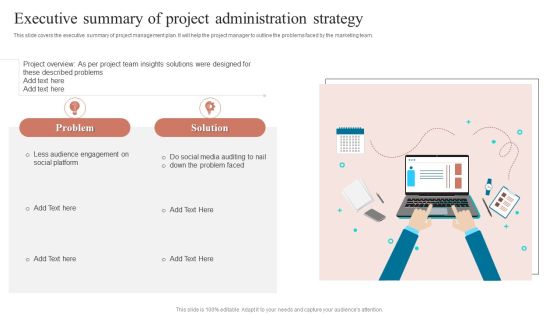
Executive Summary Of Project Administration Strategy Microsoft PDF
This slide covers the executive summary of project management plan. It will help the project manager to outline the problems faced by the marketing team.Presenting Executive Summary Of Project Administration Strategy Microsoft PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Audience Engagement, Social Platform, Described Problems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Incident Business Security Threat Ppt PowerPoint Presentation Complete Deck With Slides
This incident business security threat ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing eleven slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this incident business security threat ppt powerpoint presentation complete deck with slides PPT slideshow.

Project Quality Management Plan Initial Project Inspection Checklist Guidelines PDF
Presenting this set of slides with name project quality management plan initial project inspection checklist guidelines pdf. The topics discussed in these slide is initial project inspection checklist. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Risk Mitigation Strategy Ppt Slides
This is a risk mitigation strategy ppt slides. This is a four stage process. The stages in this process are business, success, marketing.

Risk Return Plot Ppt Slides
This is a risk return plot ppt slides. This is a nine stage process. The stages in this process are business, finance, marketing.
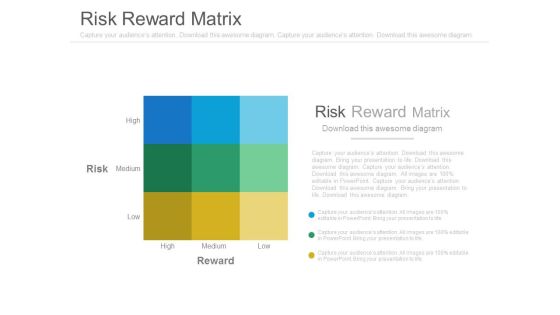
Risk Reward Matrix Ppt Slides
This is a risk reward matrix ppt slides. This is a three stage process. The stages in this process are business, marketing, success.
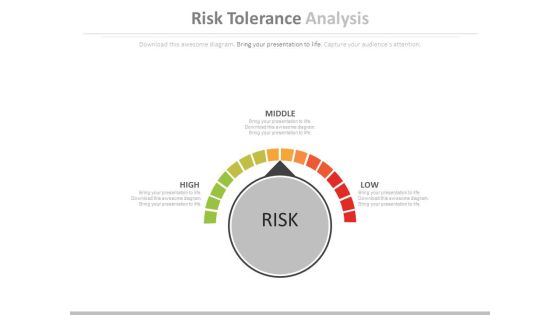
Risk Tolerance Analysis Ppt Slides
This is a risk tolerance analysis ppt slides. This is a three stage process. The stages in this process are technology, business, marketing.

Risk Tolerance Matrix Ppt Slides
This is a risk tolerance matrix ppt slides. This is a three stage process. The stages in this process are tables, business, marketing.

Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Best Practices For IT Risk Mitigation Background PDF
The following slide illustrates the best practices to remediate IT threats. It includes elements such as discovering and categorizing assets, evaluating risk, monitoring and examining, prioritizing, planning process etc. Presenting Best Practices For IT Risk Mitigation Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Evaluate Risk, Prioritize Risk, Plan Remediation Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Logistics Threat Management Strategies Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this logistics threat management strategies ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Threat Estimate Scenario Analysis Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this threat estimate scenario analysis ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Managerial Threat And Command Technology Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this managerial threat and command technology ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Threat Scenario Technological Externalities Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this threat scenario technological externalities ppt powerpoint presentation complete deck with slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Areas Business Icons PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. business analysis planning and monitoring whose main purpose is to develop estimates of business analysis tasks, determine the business analyses deliverables, identify stakeholders, determine business analysis process etc. along with elements and techniques at each stage. Presenting solution evaluation criteria assessment and threat impact matrix description of babok areas business icons pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like plan business, conduct stakeholder analysis, business analysis, communication, requirements management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Areas Requirements Guidelines PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. requirements management and communication whose main purpose is to ensure that all the stakeholders understand the solution and are communicated on regular events or intervals regarding the solution along with elements and techniques at each stage. This is a solution evaluation criteria assessment and threat impact matrix description of babok areas requirements guidelines pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like requirements, management, analysis, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
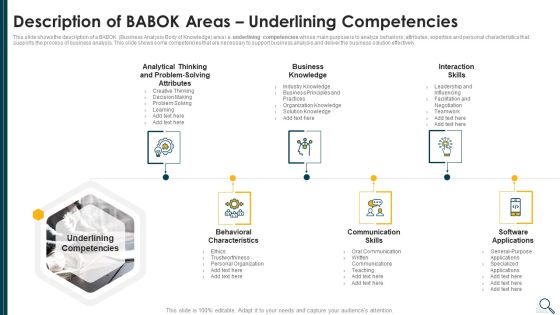
Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Areas Underlining Ideas PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. requirements analysis whose main purpose is to analyze and study the stated solution requirements in order to define the capabilities of a potential solution etc. along with elements and techniques at each stage. Presenting solution evaluation criteria assessment and threat impact matrix description of babok areas underlining ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like requirement priority, organize requirements, requirement specification, requirement verification. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Areas Professional PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. underlining competencies whose main purpose is to analyze behaviors, attributes, expertise and personal characteristics that supports the process of business analysis. This slide shows some competencies that are necessary to support business analysis and deliver the business solution effectively. This is a solution evaluation criteria assessment and threat impact matrix description of babok areas professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization knowledge, software applications, communication skills, behavioral characteristics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
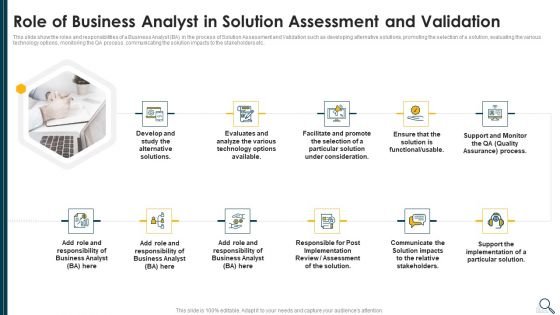
Solution Evaluation Criteria Assessment And Threat Impact Matrix Role Of Business Analyst Download PDF
This slide show the roles and responsibilities of a Business Analyst BA in the process of Solution Assessment and Validation such as developing alternative solutions, promoting the selection of a solution, evaluating the various technology options, monitoring the QA process, communicating the solution impacts to the stakeholders etc.. Presenting solution evaluation criteria assessment and threat impact matrix role of business analyst download pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like develop, analyze, technology, implementation, communicate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Areas Enterprise Elements PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. enterprise analysis whose main purpose is to identify business needs, evaluate the investment necessary, identify business requirements, determine feasible business solution etc.. along with elements and techniques at each stage. This is a solution evaluation criteria assessment and threat impact matrix description of babok areas enterprise elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine, analysis, techniques, investment, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strengths Weaknesses Opportunities And Threats Analysis Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Strengths Weaknesses Opportunities And Threats Analysis Ppt PowerPoint Presentation Complete Deck With Slides This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the thirty slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Executive Leadership Programs Thinking Critically Making Decisions Solving Problems Template Investigation Template PDF
Presenting this set of slides with name executive leadership programs thinking critically making decisions solving problems template investigation template pdf. This is a four stage process. The stages in this process are identify and define authentic problems and significant questions investigation, plan and manage activities to develop solution complete project, collect and analyze data to identify solutions and make informed decisions, use multiple processes and diverse perspective to explore alternative solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Project Management Budget Project Delivery Ppt PowerPoint Presentation Professional Diagrams
This is a project management budget project delivery ppt powerpoint presentation professional diagrams. This is a three stage process. The stages in this process are business, management, marketing, compare.

Project Manager Project Team Ppt PowerPoint Presentation Gallery Design Inspiration
This is a project manager project team ppt powerpoint presentation gallery design inspiration. This is a five stage process. The stages in this process are business, management, marketing, compare.

Project Manager Project Team Ppt PowerPoint Presentation Ideas Format
This is a project manager project team ppt powerpoint presentation ideas format. This is a two stage process. The stages in this process are business, management, strategy, analysis, marketing.

Project Manager Project Team Ppt PowerPoint Presentation Slides Format
This is a project manager project team ppt powerpoint presentation slides format. This is a two stage process. The stages in this process are business, planning, strategy, marketing, management.

Project Management Project Team Ppt PowerPoint Presentation Inspiration Rules
This is a project management project team ppt powerpoint presentation inspiration rules. This is a six stage process. The stages in this process are marketing, business, management, planning, strategy.
Project Manager Project Team Ppt PowerPoint Presentation Gallery Shapes
This is a project manager project team ppt powerpoint presentation gallery shapes. This is a five stage process. The stages in this process are business, planning, strategy, marketing, management.

Project Change Control Management Tools Comparative Analysis Information PDF
This slide represents the table showing comparison between project change control tools. It shows comparison on the basis of features such as problem, incident and compliance management, change calendaring, tasks prioritization, automatic communication and data mining. Presenting Project Change Control Management Tools Comparative Analysis Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Compliance Management, Automatic Communication, Incident Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
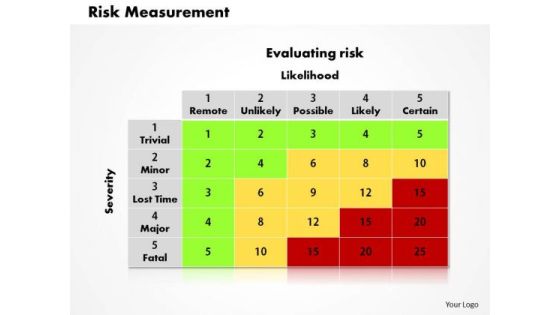
Risk Measurement Business PowerPoint Presentation
Get Out Of The Dock With Our Risk Measurement Business Powerpoint Presentation Powerpoint Templates. Your Mind Will Be Set Free. Play The Doctor With Our success Powerpoint Templates. Control Operations With Your Ideas.

Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
