AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Caution
Caution

Troubleshooting Problem Business PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with troubleshooting

Troubleshooting Problem Business PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with troubleshooting

Business Strategy Formulation Complete All Problem Puzzle Concept Statement
Rake In The Dough With
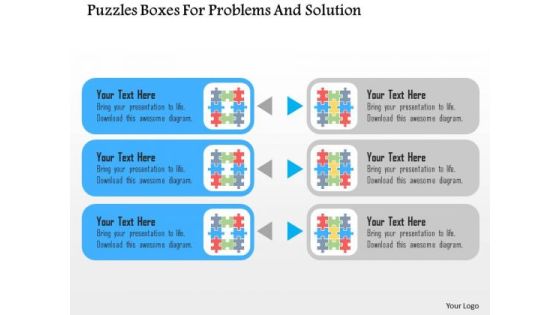
Business Diagram Puzzles Boxes For Problems And Solution Presentation Template
This slide contains graphics puzzle boxes These puzzle boxes may be used to present business solutions. Use this slide to build exclusive presentations for your viewers.

Coffee Cup With Problem Word And Icons Powerpoint Slides
This PowerPoint template contains graphics of coffee cup with cloud word and icons. You may download this PPT slide design to display your ideas in visual manner. You can easily customize this template to make it more unique as per your need.

Risk Analysis Simplified Format Ppt PowerPoint Presentation Ideas Maker
This is a risk analysis simplified format ppt powerpoint presentation ideas maker. This is a four stage process. The stages in this process are new operating system may be unstable, communication problems over system issues, we may not have the right requirements, requirements may change late in the cycle, database software may arrive late.
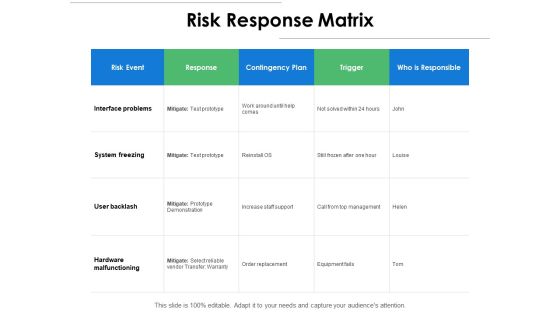
Risk Response Matrix Ppt PowerPoint Presentation Pictures Images
Presenting this set of slides with name risk response matrix ppt powerpoint presentation pictures images. The topics discussed in these slides are response, hardware malfunctioning, system freezing, interface problems, trigger. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
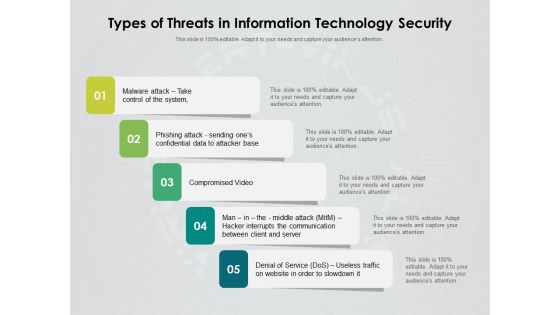
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Half Yearly Information Technology Security Roadmap For Continuous Threat Analysis Rules
Presenting the half yearly information technology security roadmap for continuous threat analysis rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Information Technology Security Roadmap For Continuous Threat Analysis Microsoft
Presenting the six months information technology security roadmap for continuous threat analysis microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
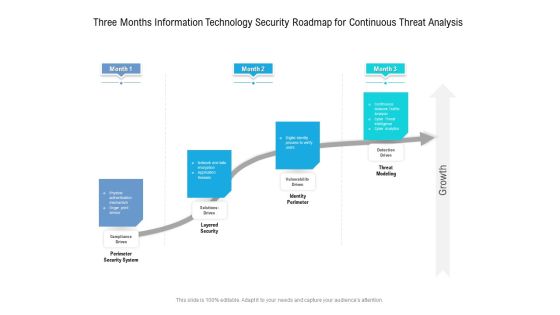
Three Months Information Technology Security Roadmap For Continuous Threat Analysis Professional
Presenting the three months information technology security roadmap for continuous threat analysis professional. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Opportunities And Threats For Penetrating In New Market Segments Geographic Expansion Strategy Steps Introduction PDF
This is a opportunities and threats for penetrating in new market segments geographic expansion strategy steps introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like target market research and prioritization, go to market model research, analysis and prioritization, developing and executing expansion plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
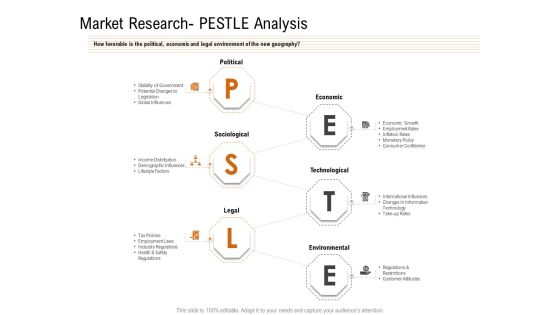
Opportunities And Threats For Penetrating In New Market Segments Market Research PESTLE Analysis Download PDF
How favorable is the political, economic and legal environment of the new geography. This is a opportunities and threats for penetrating in new market segments market research pestle analysis download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like political, economic, sociological, technological, legal. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
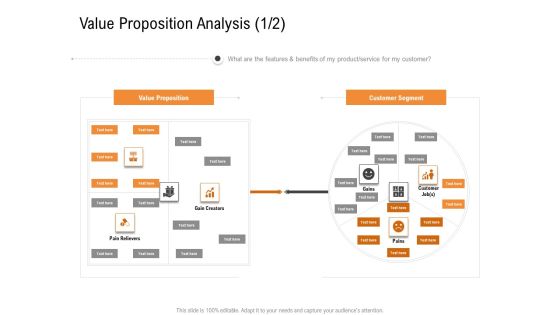
Opportunities And Threats For Penetrating In New Market Segments Value Proposition Analysis Customer Sample PDF
What are the features and benefits of my product or service for my customer. This is a opportunities and threats for penetrating in new market segments value proposition analysis customer sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like value proposition, customer segment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
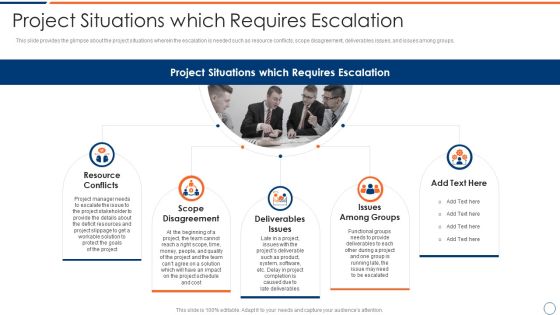
How To Intensify Project Threats Project Situations Which Requires Escalation Summary PDF
This slide provides the glimpse about the project situations wherein the escalation is needed such as resource conflicts, scope disagreement, deliverables issues, and issues among groups. Presenting how to intensify project threats project situations which requires escalation summary pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like resource conflicts, scope disagreement, deliverables issues, issues among groups. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
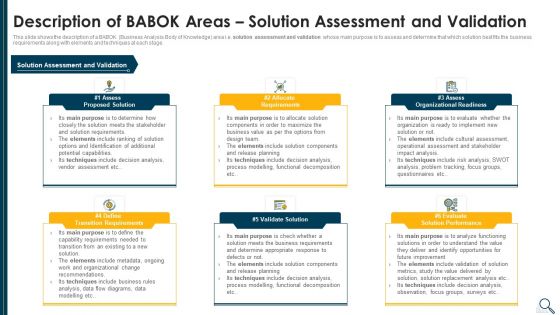
Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Slides PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. solution assessment and validation whose main purpose is to assess and determine that which solution best fits the business requirements along with elements and techniques at each stage. Presenting solution evaluation criteria assessment and threat impact matrix description of babok slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like requirements, organizational readiness, validate solution, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
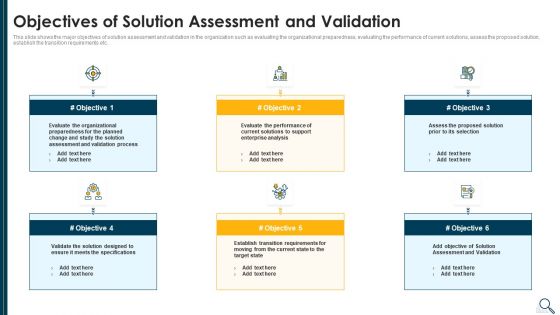
Solution Evaluation Criteria Assessment And Threat Impact Matrix Objectives Of Solution Assessment Rules PDF
This slide shows the major objectives of solution assessment and validation in the organization such as evaluating the organizational preparedness, evaluating the performance of current solutions, assess the proposed solution, establish the transition requirements etc. This is a solution evaluation criteria assessment and threat impact matrix objectives of solution assessment rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational, process, enterprise analysis, performance, evaluate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Task Ideas PDF
This slide shows the solution assessment and validation model or framework which helps to assess and determine that which solution best fits the business requirements along with the model inputs and outputs. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix solution assessment and validation task ideas pdf. Use them to share invaluable insights on solution assessment and validation model of the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

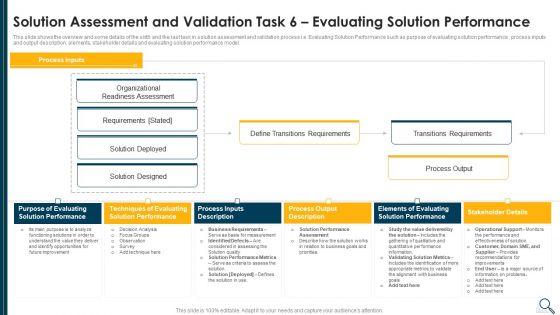
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Information PDF
This slide shows the overview and some details of the sixth and the last task in solution assessment and validation process i.e. Evaluating Solution Performance such as purpose of evaluating solution performance , process inputs and output description, elements, stakeholder details and evaluating solution performance model. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix solution assessment and validation information pdf bundle. Topics like evaluating, performance, organizational, process output can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Solution Evaluation Criteria Assessment And Threat Impact Matrix Assess Organizational Readiness Icons PDF
This slide explains the various elements of force field analysis framework such as proposed change, pushing forces, forces resisting change etc. along with the benefits of force field analysis tool. This is a solution evaluation criteria assessment and threat impact matrix assess organizational readiness icons pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce issues, execution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Business Analysis Body Introduction PDF
This slide shows the framework that illustrates the business analysis tasks that need to be performed in order to understand and evaluate that how the desired solution will deliver value to the company. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix business analysis body introduction pdf bundle. Topics like enterprise analysis, requirements analysis, communication, requirements management, business analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
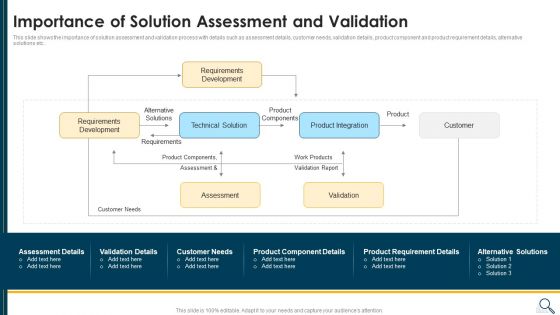
Solution Evaluation Criteria Assessment And Threat Impact Matrix Importance Of Solution Assessment Clipart PDF
This slide shows the importance of solution assessment and validation process with details such as assessment details, customer needs, validation details, product component and product requirement details, alternative solutions etc. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix importance of solution assessment clipart pdf. Use them to share invaluable insights on requirements development, product integration, customer, product components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Advance Data Analytics At Workspace Contingency Plan For Threat Handling Slides PDF
This slide covers details regarding the network optimization capabilities in terms of advanced caching capabilities, TCP layer optimization, global balancing of load, etc. This is a executing advance data analytics at workspace contingency plan for threat handling slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like caching capabilities, routing optimization, layer optimization, distributed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Estimating Total Cost Of Ownership Of SIEM Real Time Assessment Of Security Threats Infographics PDF
This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver and pitch your topic in the best possible manner with this estimating total cost of ownership of siem real time assessment of security threats infographics pdf. Use them to share invaluable insights on ongoing expenses, cost breakdown, siem solution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats What Our Clients Say About Us Portrait PDF
This slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation. This is a real time assessment of security threats what our clients say about us portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like what our clients say about us. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Real Time Assessment Of Security Threats What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting real time assessment of security threats what sets us apart microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, cost ownership and roi, dynamic business, productivity improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Real Time Assessment Of Security Threats Which Hosting Model Is Right For You Clipart PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. This is a real time assessment of security threats which hosting model is right for you clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs and management, company, hardware and software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Real Time Assessment Of Security Threats Key Features Of SIEM Software Inspiration PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting real time assessment of security threats key features of siem software inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like compliance and internal auditing, high scalability, classification and enrichment, security automation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Our Companys Mission Vision And Values Rules PDF
This slide provides the details of our company mission, vision and values to provide unique services to the customers. Presenting real time assessment of security threats our companys mission vision and values rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like our mission, our vision, our values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Our Management Team Graphics PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a real time assessment of security threats our management team graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
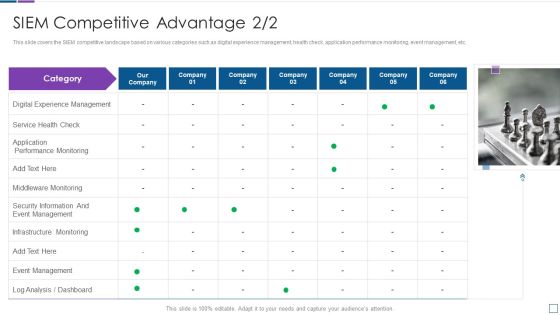
Real Time Assessment Of Security Threats SIEM Competitive Advantage Service Structure PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Presenting real time assessment of security threats siem competitive advantage service structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital experience management, service health check, application performance monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats About Our SIEM Company Structure PDF
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. This is a real time assessment of security threats about our siem company structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like about our siem company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Log Management Services Information PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting real time assessment of security threats log management services information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Our Organization SIEM Log Flow Topics PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a real time assessment of security threats our organization siem log flow topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
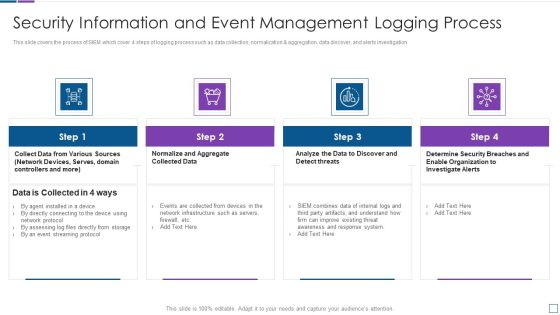
Real Time Assessment Of Security Threats Security Information And Event Management Logging Process Demonstration PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a real time assessment of security threats security information and event management logging process demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats In A Digital Era Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This handling cyber threats in a digital era ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
Handling Cyber Threats Digital Era Categorization Worksheet For Assets Ppt Icon Outline PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting handling cyber threats digital era categorization worksheet for assets ppt icon outline pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like server computer, system location, system accessibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
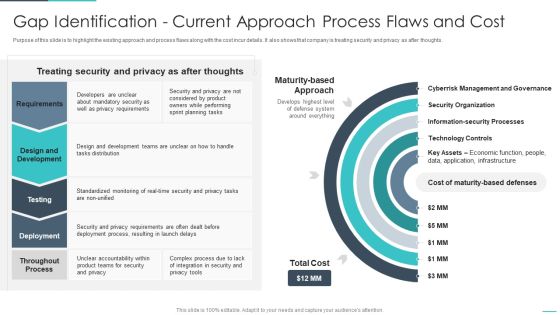
Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Setting Scenario For Cybersecurity Control Ppt Infographics Brochure PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting handling cyber threats digital era setting scenario for cybersecurity control ppt infographics brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Handling Cyber Threats Digital Era Communication Plan For Cyber Breaches Ppt Icon Background Images PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era communication plan for cyber breaches ppt icon background images pdf. Use them to share invaluable insights on communication plan for cyber breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Criticality Assessment Of Identified Assets Ppt Slides Backgrounds PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a handling cyber threats digital era criticality assessment of identified assets ppt slides backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extremely critical, reasonably critical, least critical. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
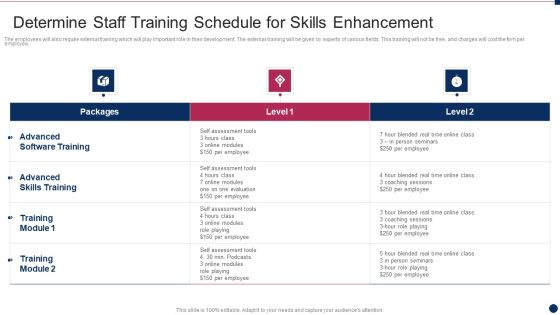
Threat Management At Workplace Determine Staff Training Schedule For Skills Enhancement Graphics Pdf
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver and pitch your topic in the best possible manner with this threat management at workplace determine staff training schedule for skills enhancement graphics pdf. Use them to share invaluable insights on advanced skills training, advanced software training, blended real time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management At Workplace Incident Reporting By Different Departments Download PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Deliver an awe inspiring pitch with this creative threat management at workplace incident reporting by different departments download pdf bundle. Topics like average cost per incident, person involved in the incident, across different departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Roles And Responsibilities To Ensure Work Environment Sample PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a threat management at workplace roles and responsibilities to ensure work environment sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, internal investigations unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Management At Workplace Technological Assessment Of Firm Current Management Structure PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace technological assessment of firm current management structure pdf. Use them to share invaluable insights on service delay rate, average time for client onboarding, successful service requests handling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives For Effective IT Security Threats Administration Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This data safety initiatives for effective it security threats administration ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Cloud Information Security Cloud Security Threats Shared Vulnerabilities Ppt File Influencers PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. This is a Cloud Information Security Cloud Security Threats Shared Vulnerabilities Ppt File Influencers PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure Cloud, Providers Already, Cloud Service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Asset Maintenance Cost Assessment Sheet Clipart PDF
Following slide displays assessment sheet that can be used by members to record overall asset maintenance cost for further analysis. Sections covered in the sheet are onsite solution, initial, monthly and annual cost.This is a IT Threats Response Playbook Asset Maintenance Cost Assessment Sheet Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Servers, Desktop Systems, Onsite Solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.Presenting IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Differential, Incremental, Differential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Categorization Worksheet For System Components Graphics PDF
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information.Presenting IT Threats Response Playbook Categorization Worksheet For System Components Graphics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like System Accessibility, Valuable Information, Organization Boundary. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Evaluation Sheet For Data Backup Activities Sample PDF
Mentioned slide addresses evaluation sheet which can be used for assessing data backup activities. Sections covered in the sheet are backup testing frequency, type of backup solution and responsible person details. Presenting IT Threats Response Playbook Evaluation Sheet For Data Backup Activities Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Archival Data, Virtual Machines, System And Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

