AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Caution
Caution
Mitigation Strategies For Operational Threat Post It Notes Ppt Visual Aids Inspiration PDF
This is a mitigation strategies for operational threat post it notes ppt visual aids inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
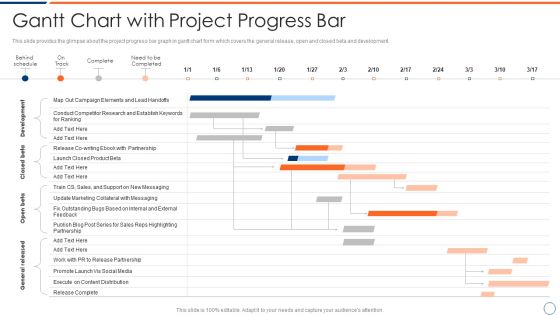
How To Intensify Project Threats Gantt Chart With Project Progress Bar Elements PDF
This slide provides the glimpse about the project progress bar graph in gantt chart form which covers the general release, open and closed beta and development. Deliver an awe inspiring pitch with this creative how to intensify project threats gantt chart with project progress bar elements pdf bundle. Topics like development, closed beta, open beta, general released. can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
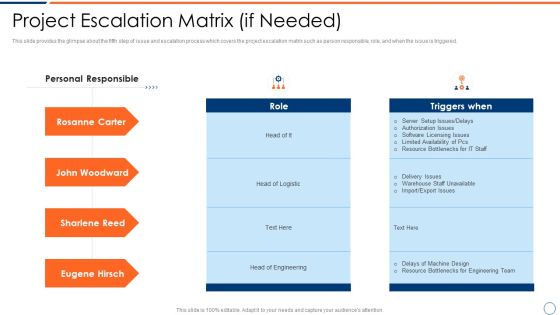
How To Intensify Project Threats Project Escalation Matrix If Needed Introduction PDF
This slide provides the glimpse about the fifth step of issue and escalation process which covers the project escalation matrix such as person responsible, role, and when the issue is triggered. Deliver an awe inspiring pitch with this creative how to intensify project threats project escalation matrix if needed introduction pdf bundle. Topics like project escalation matrix if needed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
How To Intensify Project Threats Project Performance Tracking And Reporting Structure PDF
This slide provides the glimpse about the fourth step of issue and escalation process which covers the project name, start and finish, work duration, costs, etc. Deliver an awe inspiring pitch with this creative how to intensify project threats project performance tracking and reporting structure pdf bundle. Topics like project name, start and finish, work duration, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
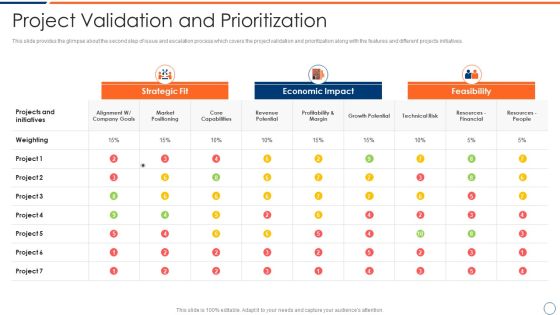
How To Intensify Project Threats Project Validation And Prioritization Brochure PDF
This slide provides the glimpse about the second step of issue and escalation process which covers the project validation and prioritization along with the features and different projects initiatives. Deliver and pitch your topic in the best possible manner with this how to intensify project threats project validation and prioritization brochure pdf. Use them to share invaluable insights on strategic fit, economic impact, feasibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How To Intensify Project Threats Escalation Procedure Work Instruction Elements PDF
This is a how to intensify project threats escalation procedure work instruction elements pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like level of notification, level of on site support, coverage hours that machine is down. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
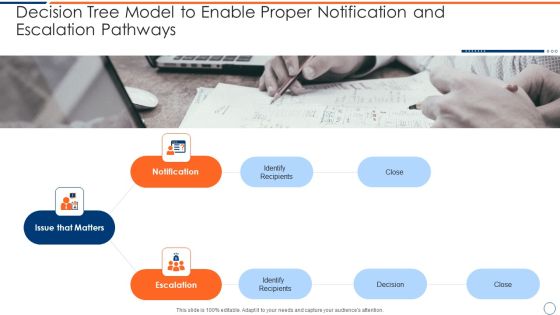
How To Intensify Project Threats Decision Tree Model To Enable Proper Notification Topics PDF
Presenting how to intensify project threats decision tree model to enable proper notification topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like issue that matters, notification, escalation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Intensify Project Threats Delay And Over Run Cost In The Projects Topics PDF
This slide provides the glimpse about the delay and over run project costs graph wherein the number of projects has been monitored, along with delayed projects and cost overrun. Deliver an awe inspiring pitch with this creative how to intensify project threats delay and over run cost in the projects topics pdf bundle. Topics like monitored, delayed projects, cost overrun can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
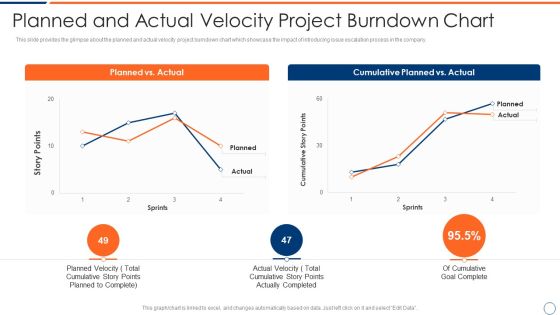
How To Intensify Project Threats Planned And Actual Velocity Project Burndown Chart Summary PDF
This slide provides the glimpse about the planned and actual velocity project burndown chart which showcase the impact of introducing issue escalation process in the company. Deliver an awe inspiring pitch with this creative how to intensify project threats planned and actual velocity project burndown chart summary pdf bundle. Topics like planned vs actual, cumulative planned vs actual can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Budget For Effective Threat Management At Workplace Structure PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative cyber security administration in organization budget for effective threat management at workplace structure pdf bundle. Topics like incident management, onboarding, process, release can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Table Of Contents Sample PDF
Presenting solution evaluation criteria assessment and threat impact matrix table of contents sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like analysis, management, requirements, organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
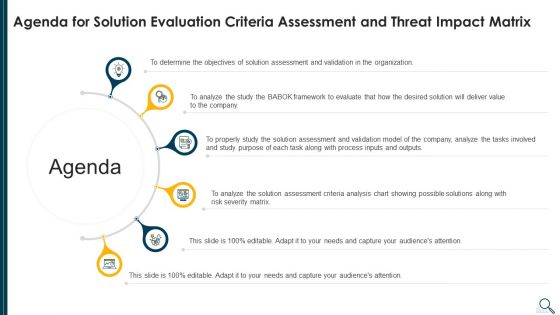
Agenda For Solution Evaluation Criteria Assessment And Threat Impact Matrix Summary PDF
This is a agenda for solution evaluation criteria assessment and threat impact matrix summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like analyze, determine, organization, value, severity matrix. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Model Graphics PDF
This slide shows the details on tasks involved in allocate requirements stage of solution assessment and validation along with the categories of requirements. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix solution assessment and validation model graphics pdf bundle. Topics like allocate requirements categories, allocate requirements description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
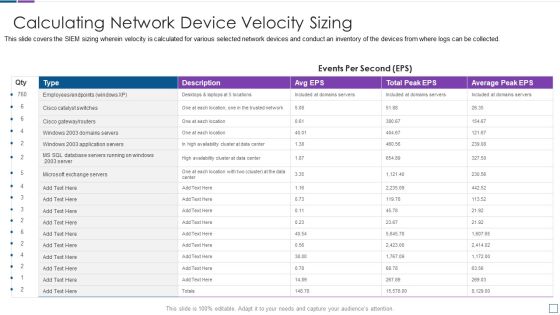
Real Time Assessment Of Security Threats Calculating Network Device Velocity Sizing Portrait PDF
This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Deliver an awe inspiring pitch with this creative real time assessment of security threats calculating network device velocity sizing portrait pdf bundle. Topics like calculating network device velocity sizing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
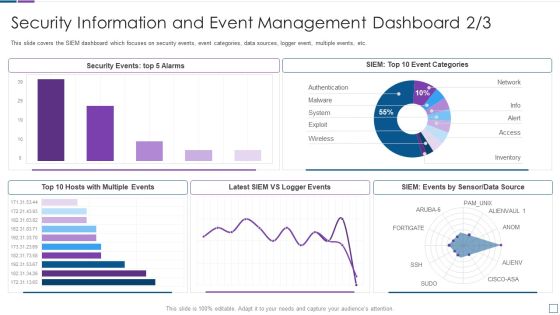
Real Time Assessment Of Security Threats Security Information And Event Management Dashboard Infographics PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative real time assessment of security threats security information and event management dashboard infographics pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
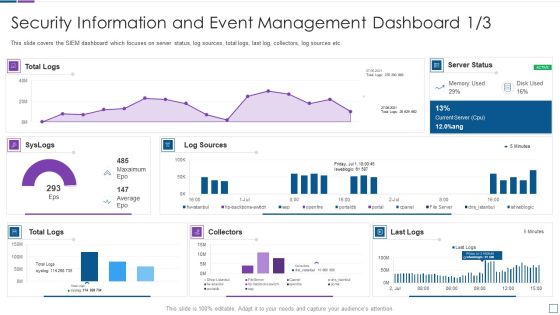
Real Time Assessment Of Security Threats Security Information And Event Management Microsoft PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats security information and event management microsoft pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Real Time Assessment Of Security Threats Various SIEM Cost Plans Offered By Our Company Topics PDF
This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an awe inspiring pitch with this creative real time assessment of security threats various siem cost plans offered by our company topics pdf bundle. Topics like annual costs of tools, annual cost of personnel, one time cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats Log Management Services Metrics Slides PDF
This is a real time assessment of security threats log management services metrics slides pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configurations, log management, metrics, virtualization, databases. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats How SIEM Works Inspiration PDF
Presenting real time assessment of security threats how siem works inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like correlation, behavior analytics, taxonomy, normalization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
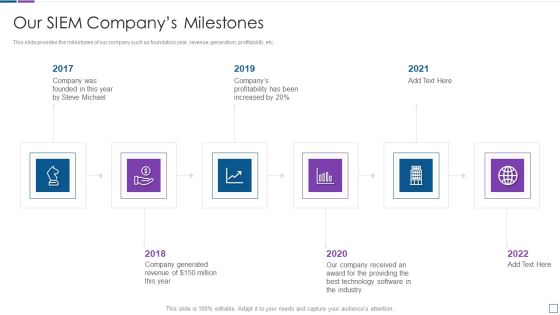
Real Time Assessment Of Security Threats Our SIEM Companys Milestones Slides PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. Presenting real time assessment of security threats our siem companys milestones slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like our siem companys milestones. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
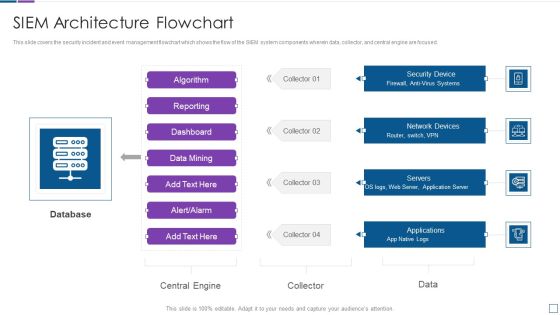
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
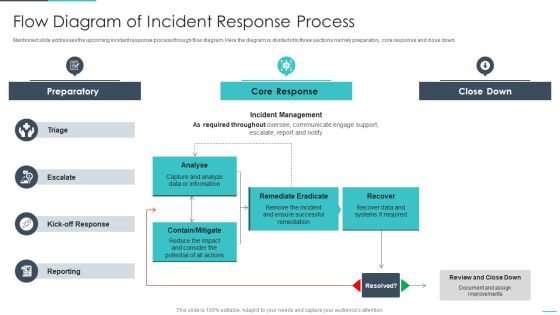
Handling Cyber Threats Digital Era Flow Diagram Of Incident Response Process Ppt Infographics Inspiration PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative handling cyber threats digital era flow diagram of incident response process ppt infographics inspiration pdf bundle. Topics like preparatory, remediate eradicate, analyse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Security Lifecycle Ppt Summary Brochure PDF
This is a handling cyber threats digital era security lifecycle ppt summary brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
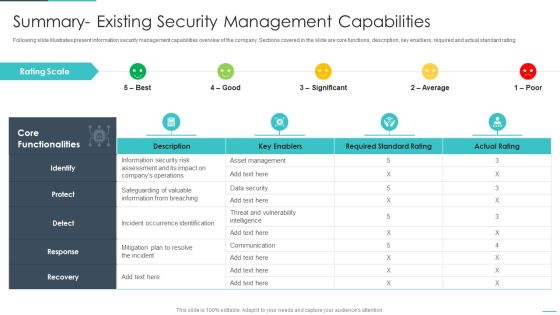
Handling Cyber Threats Digital Era Summary Existing Security Management Capabilities Ppt File Demonstration PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative handling cyber threats digital era summary existing security management capabilities ppt file demonstration pdf bundle. Topics like summary existing security management capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
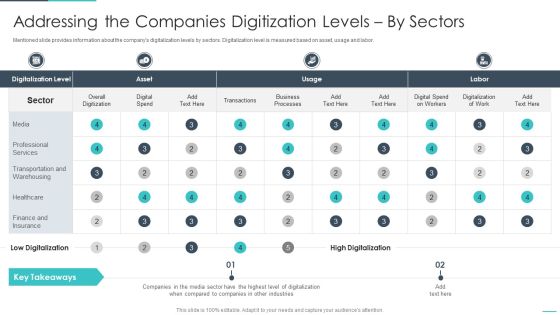
Handling Cyber Threats Digital Era Addressing The Companies Digitization Ppt Portfolio Smartart PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver and pitch your topic in the best possible manner with this andling cyber threats digital era addressing the companies digitization ppt portfolio smartart pdf. Use them to share invaluable insights on addressing the companies digitization levels by sectors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Checklist For Effectively Managing Asset Security Ppt Slides Example File PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative handling cyber threats digital era checklist for effectively managing asset security ppt slides example file pdf bundle. Topics like checklist for effectively managing asset security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
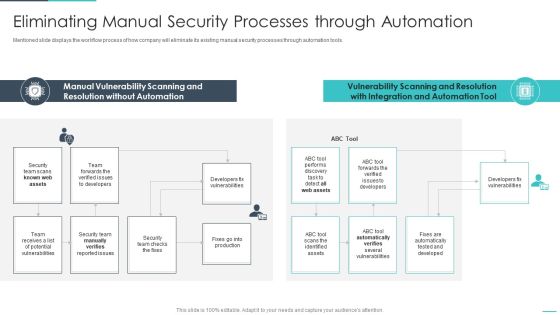
Handling Cyber Threats Digital Era Eliminating Manual Security Processes Ppt Show Influencers PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era eliminating manual security processes ppt show influencers pdf. Use them to share invaluable insights on eliminating manual security processes through automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Introducing New Incidents Logging Process Ppt Slides Graphic Images PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver an awe inspiring pitch with this creative handling cyber threats digital era introducing new incidents logging process ppt slides graphic images pdf bundle. Topics like introducing new incidents logging process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Determining The Priority Requirements Ppt Outline Visual Aids PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative handling cyber threats digital era determining the priority requirements ppt outline visual aids pdf bundle. Topics like determining the priority requirements for buying iot products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Addressing Critical Business Functions Recovery Priorities Formats Pdf
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver an awe inspiring pitch with this creative threat management at workplace addressing critical business functions recovery priorities formats pdf bundle. Topics like priorities, department, maximum allowable downtime can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives For Effective IT Security Threats Administration Table Of Contents Themes PDF
Presenting data safety initiatives for effective it security threats administration table of contents themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like global market insights, gap identification, defining business priorities, about security program, companies digitization levels. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF
This is a Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF. Use them to share invaluable insights on Provide Integration, Responsible Support, Assess The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF. Use them to share invaluable insights on Master Terminal, Extremely Critical, Reasonably Critical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF
This slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF bundle. Topics like Conference Meeting, Incident Information, Various Departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Information Technology Threat Mitigation Methods Measures Diagrams PDF
Presenting Table Of Contents For Information Technology Threat Mitigation Methods Measures Diagrams PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like IT Technical Control Measures, Technical Security, System Vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ready To Eat Food Market Analysis General Mills Threats Graphics PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Ready To Eat Food Market Analysis General Mills Threats Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF
Find a pre designed and impeccable Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Project Manager Project Team Ppt PowerPoint Presentation Gallery Format Ideas
This is a project manager project team ppt powerpoint presentation gallery format ideas. The topics discussed in this diagram are business, management, marketing, compare. This is a completely editable PowerPoint presentation, and is available for immediate download.

Internal Control Management Goals And Techniques Overview Of The Components Of An Effective Internal Control System Introduction PDF
This slide provides an overview of the various interrelated components that are included in an internal control system such as control environment, risk assessment, communication, monitoring etc. This is also known as Internal Control System Framework. Presenting Internal Control Management Goals And Techniques Overview Of The Components Of An Effective Internal Control System Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Risk Assessment, Control Activities, Information And Communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Assessment Powerpoint Slide Background
This is a risk assessment powerpoint slide background. This is a four stage process. The stages in this process are financial position today, financial objectives, risk assessment, financial plan.
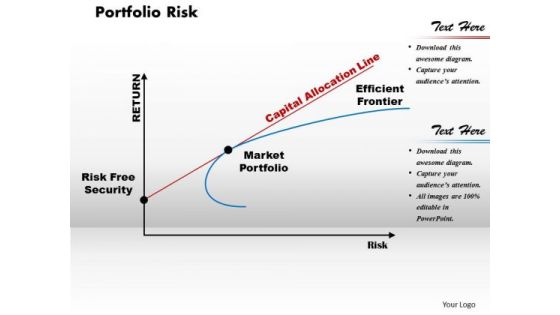
Portfolio Risk Business PowerPoint Presentation
Draw On The Experience Of Our Portfolio Risk Business Powerpoint Presentation Powerpoint Templates. They Imbibe From Past Masters.

Risk Based Methodology Quality Risk Reduction Plan Sample PDF
This slide covers risk control and reduction plan including work area or objectives, action taken, indicators to measure, timeframe and responsible department. The Risk Based Methodology Quality Risk Reduction Plan Sample PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Risk Based Methodology Risk Tolerance Capacity Information PDF
This slide covers Estimate Risk tolerance level of the stakeholders based on ordinal scale, cardinal scale, cost, schedule, scope and quality. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Risk Based Methodology Risk Tolerance Capacity Information PDF from Slidegeeks and deliver a wonderful presentation.

Risk Analysis Decision Tree To Analyze Procurement Risks Designs PDF
This slide provides an overview of the decision tree diagram created to determine the suitable supplier and risk involved. It further includes key takeaways that include the reasons for selecting the supplier. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Risk Analysis Decision Tree To Analyze Procurement Risks Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Risk Identification Swot Analysis Procurement Risk Identification Sample PDF
This slide provides an overview of the SWOT analysis conducted to understand the strengths and determine areas of improvement. Major strengths covered are skilled workforce and good vendor network. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Risk Identification Swot Analysis Procurement Risk Identification Sample PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Risk Identification Swot Analysis Procurement Risk Identification Sample PDF today and make your presentation stand out from the rest.

Risk Assessment Key Steps To Perform Risk Analysis Download PDF
This slide provides an overview of the risk analysis process. Major steps covered are identifying risks and uncertainty, estimating impact, developing an analysis model, analyzing results and implementing solutions. Present like a pro with Risk Assessment Key Steps To Perform Risk Analysis Download PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Project Manager Project Team Ppt PowerPoint Presentation Ideas Elements
This is a project manager project team ppt powerpoint presentation ideas elements. This is a five stage process. The stages in this process are marketing, business, management, compare.
