Safety Pyramid

Cloud Information Security Platform As A Service Paas Ppt Portfolio Skills PDF
This slide defines the platform-as-a-service model of cloud security and the various advantages and disadvantages of the PaaS model. Deliver an awe inspiring pitch with this creative Cloud Information Security Platform As A Service Paas Ppt Portfolio Skills PDF bundle. Topics like Service Providers, Business Applications, Considerable Money can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Develop Corporate Cyber Security Risk Mitigation Plan Mode Communication Organization Protection Services Introduction PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan mode communication organization protection services introduction pdf bundle. Topics like communicate medium, weekly calls, monthly catch up, review sessions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
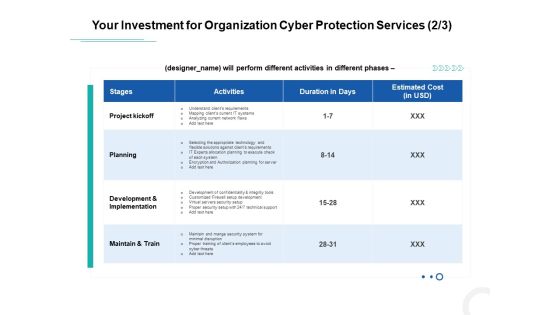
Develop Corporate Cyber Security Risk Mitigation Plan Your Investment For Organization Cyber Protection Service Mockup PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan your investment for organization cyber protection service mockup pdf bundle. Topics like project kickoff, planning, development and implementation, maintain and train can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Civil Infrastructure Designing Services Management 4 Dimensions Of Infrastructure Security Slides PDF
Deliver an awe inspiring pitch with this creative civil infrastructure designing services management 4 dimensions of infrastructure security slides pdf bundle. Topics like applications, data, infrastructure, outsources, employees can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Table Of Contents Ppt PowerPoint Presentation Gallery Influencers PDF
Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Table Of Contents Ppt PowerPoint Presentation Gallery Influencers PDF bundle. Topics like Executive Summary, Business Model, Management Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
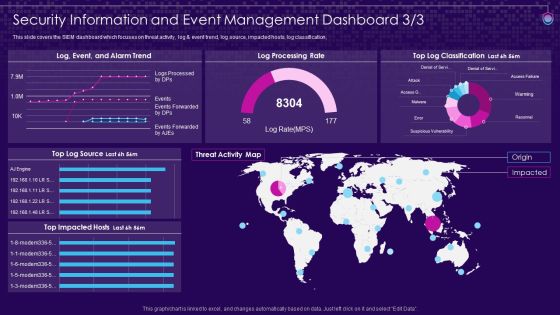
SIEM Services Security Information And Event Management Dashboard Source Ppt Outline Design Inspiration PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative siem services security information and event management dashboard source ppt outline design inspiration pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Service Slides PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Service Slides PDF bundle. Topics like Effects Of Damage, Vulnerability And Possible, Unauthorized Disclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Company Business Model Canvas Designs PDF
This slide highlights the business model of security guard company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Company Business Model Canvas Designs PDF bundle. Topics like Target Market, Customer Relationship, Customer Segments, Cost Structure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Government And Private Sector Clients Clipart PDF
This slide highlights the security company clients from government and private sector which includes offices with location and industries with company name. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Government And Private Sector Clients Clipart PDF bundle. Topics like Government Sector, Private Sector, Treasure Office can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Characteristics Of Document Management Process With Icons Ppt PowerPoint Presentation File Show PDF
Presenting characteristics of document management process with icons ppt powerpoint presentation file show pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including processing, customization, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF
The slide provides a list of companys clients in different sectors manufacturing, construction, financials services, energy. Mining, automobile etc. Along with the service which the company offers to specific client.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF bundle. Topics like Financials Services, Assets Management, Underwriting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Guide For Software Developers Service Agreement For Securing More Clients Mockup PDF
Purpose of this slide is to show service agreement that will assist service managers in gaining the attention on new clients. Sections covered in the agreement are parties, invoices, list of service and signature. Deliver an awe inspiring pitch with this creative guide for software developers service agreement for securing more clients mockup pdf bundle. Topics like service agreement, securing more clients can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Man Under Credit Cards Finance PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with clay model character lying underneath a stack of credit cards

Coins With Growth Success PowerPoint Templates And PowerPoint Backgrounds 1211
Microsoft PowerPoint Template and Background with three coin stacked showing growth

Cloud Based Email Security Market Report Issues Faced By Companies Services Ppt Pictures Slide Portrait PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Deliver an awe inspiring pitch with this creative cloud based email security market report issues faced by companies services ppt pictures slide portrait pdf bundle. Topics like issues faced by companies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Revenue And Net Profit Ppt PowerPoint Presentation Gallery Graphic Images PDF
This slide highlights the revenue and net profit of security guard company through bar graph and tabular format. It covers three years data of revenue, and net profit. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Revenue And Net Profit Ppt PowerPoint Presentation Gallery Graphic Images PDF bundle. Topics like Net Profit, Increase Revenue, 2018 To 2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

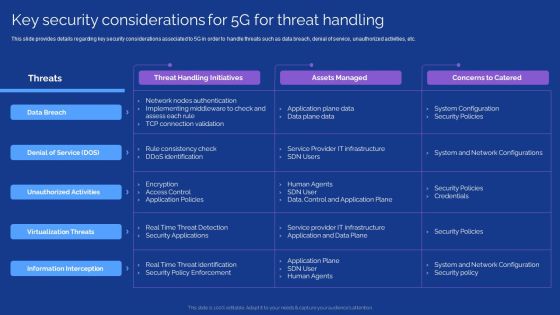
Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF bundle. Topics like Information Interception, Virtualization Threats, Denial Of Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Csr Initiatives And Spending Ppt PowerPoint Presentation Gallery Shapes PDF
This slide highlights the CSR spend distribution by inhouse and partner spend. It also highlights the CSR initiatives that are carbon footprint reduction, labor policies, hunger program, community development and healthcare services. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Csr Initiatives And Spending Ppt PowerPoint Presentation Gallery Shapes PDF bundle. Topics like CSR Total Spend, Hunger Program, Skills Training, Community Development can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Human Resource Services Business Profile Ppt PowerPoint Presentation Complete Deck With Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Security And Human Resource Services Business Profile Ppt PowerPoint Presentation Complete Deck With Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry cant touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has fourty six slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance.

Program Evaluation Templates Bundle Security Checklist Ppt Outline Graphics Tutorials PDF
Deliver and pitch your topic in the best possible manner with this program evaluation templates bundle security checklist ppt outline graphics tutorials pdf. Use them to share invaluable insights on project it project, human threats, general threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
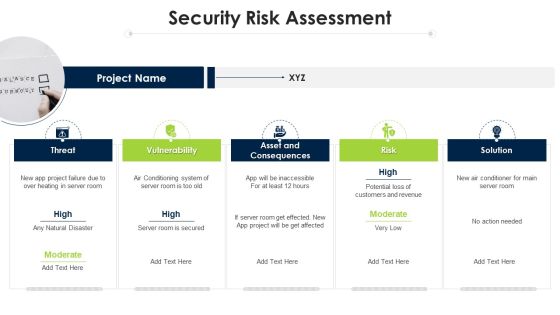
Program Evaluation Templates Bundle Security Risk Assessment Ppt Infographic Template Brochure PDF
This is a program evaluation templates bundle security risk assessment ppt infographic template brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like solution, risk, asset and consequences, vulnerability, threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
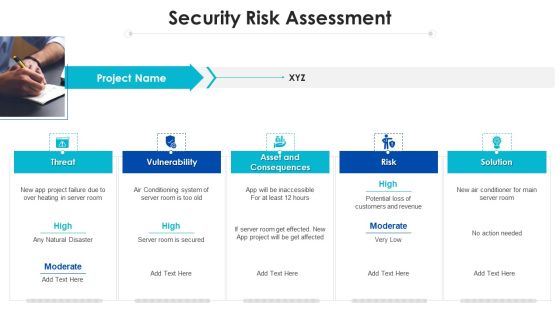
Project Assessment Templates Bundle Security Risk Assessment Ppt Infographic Template Guide PDF
This is a Project Assessment Templates Bundle Security Risk Assessment Ppt Infographic Template Guide PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Threat, Asset Consequences, Risk Solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
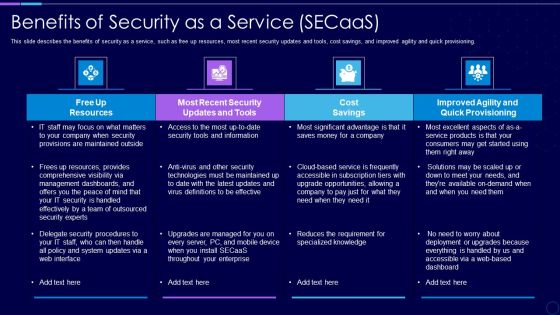
Everything As A Service Xaas For Cloud Computing IT Benefits Of Security As A Service Clipart PDF
This slide describes the benefits of security as a service, such as free up resources, most recent security updates and tools, cost savings, and improved agility and quick provisioning. Deliver an awe inspiring pitch with this creative everything as a service xaas for cloud computing it benefits of security as a service clipart pdf bundle. Topics like cost savings, security, resources, dashboards can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Risk Management For Organization Essential Assets Determine Threat Management Team Icons PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting risk management for organization essential assets determine threat management team icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat management head, security manager, public affair advisor, legal advisor, medical advisor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Stack Of Dollar Coins Under Umbrella Business PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Stack Of Dollar Coins Under Umbrella Business PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Umbrellas PowerPoint Templates because you should once Tap the ingenuity of our PowerPoint Templates and Slides. They are programmed to succeed. Download and present our Money PowerPoint Templates because It will get your audience in sync. Download and present our Marketing PowerPoint Templates because It will get your audience in sync. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Use these PowerPoint slides for presentations relating to Piles of golden coins under an umbrella, money, umbrellas, marketing, signs, security . The prominent colors used in the PowerPoint template are Black, Yellow, Brown. We assure you our Stack Of Dollar Coins Under Umbrella Business PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our coins PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Presenters tell us our Stack Of Dollar Coins Under Umbrella Business PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by professionals Professionals tell us our umbrellas PowerPoint templates and PPT Slides will get their audience's attention. The feedback we get is that our Stack Of Dollar Coins Under Umbrella Business PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by professionals PowerPoint presentation experts tell us our umbrellas PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Stock Photo 3d Dollars Stack With Unlocked Lock And Keys PowerPoint Slide
This power point template has been designed with graphic of dollars and lock. We have used open lock with keys, in this image dollars are used to show finance while lock and key are used to display security concept. Use this image in your business and finance related presentations.

Secure Your Business Mails PowerPoint Templates Ppt Backgrounds For Slides 0713
Our Secure Your Business Mails PowerPoint Templates PPT Backgrounds For Slides will will follow the drill. They accomplish the task assigned to them. Do the drill with our Security PowerPoint Templates. Your ideas will march ahead. Place the orders with your thoughts. Our People PowerPoint Templates know the drill.
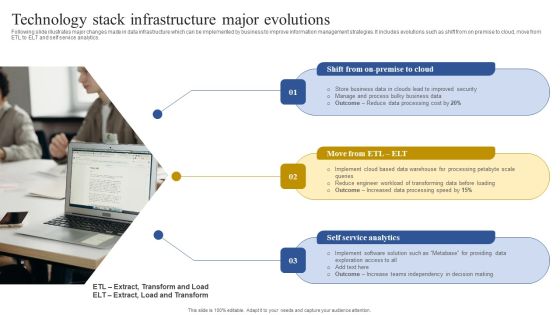
Technology Stack Infrastructure Major Evolutions Download PDF
Following slide illustrates major changes made in data infrastructure which can be implemented by business to improve information management strategies. It includes evolutions such as shift from on premise to cloud, move from ETL to ELT and self service analytics. Persuade your audience using this Technology Stack Infrastructure Major Evolutions Download PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Business Data, Improved Security, Processing Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Develop Corporate Cyber Security Risk Mitigation Plan Case Study For Organization Cyber Protection Services Themes PDF Sample PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan case study for organization cyber protection services themes pdf sample pdf bundle. Topics like problem, results, our solution, low cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Icons PDF
Deliver an awe inspiring pitch with this creative case study 4 improving patient security and reducing risk of violence icons pdf bundle. Topics like power management, white space management, building management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
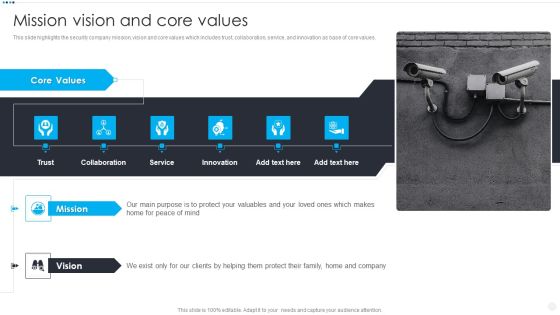
Smart Home Security Solutions Company Profile Mission Vision And Core Values Rules PDF
This slide highlights the security company mission, vision and core values which includes trust, collaboration, service, and innovation as base of core values. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Mission Vision And Core Values Rules PDF bundle. Topics like Core Values Trust, Collaboration Service Innovation, Mission Vision Mind can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Product Development Business Drivers Employee Ranking System Themes PDF
The purpose of this slide is to analyze the various business drivers by comparing the relative importance of each driver against the other drivers. This includes shortening market rate, global competition, mass customization, secure product, and maximizing profitability. Pitch your topic with ease and precision using this Product Development Business Drivers Employee Ranking System Themes PDF. This layout presents information on Maximize Profitability, Secure Product, Global Competition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF
This slide covers cyber security incident response process flowchart. It involves relationship between technical actions coordinator, incident manager, supporting actions coordinator and business owner. Presenting Managing Cyber Security Incident Response Process Flowchart Ppt Templates PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Technical Actions Coordinator, Incident Manager, Supporting Actions Coordinator. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF
This slide covers cyber security incident response lifecycle model. It involves stages such as prepare, identify, eradicate, contain and recover. Persuade your audience using this Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare, Identify, Contain, Communication, Eradicate, Lessons Learned. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
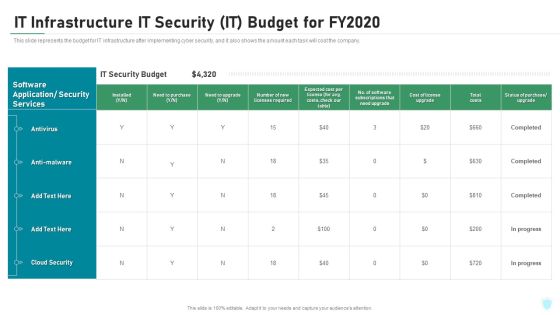
IT Infrastructure IT Security IT Budget For Fy2020 Ppt Ideas Elements PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative it infrastructure it security it budget for fy2020 ppt ideas elements pdf bundle. Topics like cloud security, costs, software application, security services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT IT Infrastructure Cyber Security Budget Pictures PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it it infrastructure cyber security budget pictures pdf bundle. Topics like data security, infrastructure protections, access management, security service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

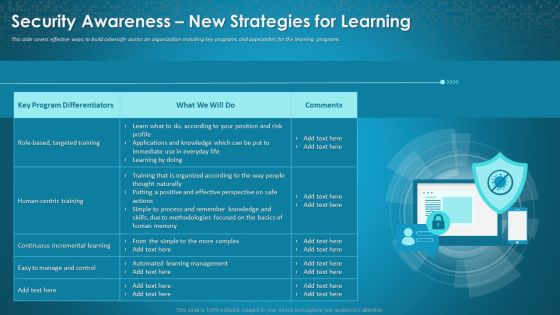
Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Organizational Network Staff Learning Security Awareness New Strategies For Learning Rules PDF
This slide cover effective way to build cybersafe across on organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness new strategies for learning rules pdf bundle. Topics like human centric training, manage and control, targeted training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Prepare And Deploy Strong IT Policies Ppt PowerPoint Presentation File Model PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative info security prepare and deploy strong it policies ppt powerpoint presentation file model pdf bundle. Topics like build strong, it policies, data sharing, access data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
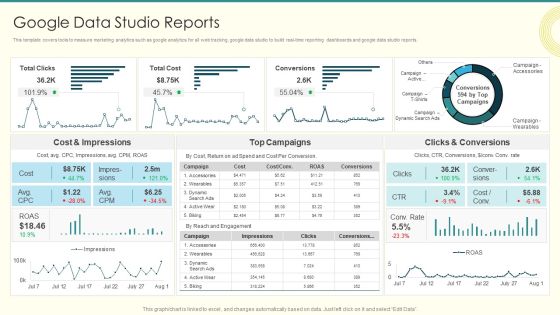
Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF bundle. Topics like Impressions, Clicks Conversions, Cost Impressions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF
This template covers working of Facebooks machine learning or algorithms to filter through a massive amount of data and generate a list of qualified, cold prospects.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF bundle. Topics like Interests Activity, Common Builds, Target Customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness Deliver an awe inspiring pitch with this creative case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like building management, security management, security effectiveness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity IT Infrastructure Electronic Information Security Budget For FY2020 Ppt Infographics Graphics Download PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative cybersecurity it infrastructure electronic information security budget for fy2020 ppt infographics graphics download pdf bundle. Topics like required, application, security services, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF bundle. Topics like Monitoring, Bluestone Security, Launched Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Business Strategy Abstract 3d Globe With Golden Chains International Security Photos
Place The Orders With Your Thoughts. Our internet business strategy abstract 3d globe with golden chains international security photos Powerpoint Templates Know The Drill.
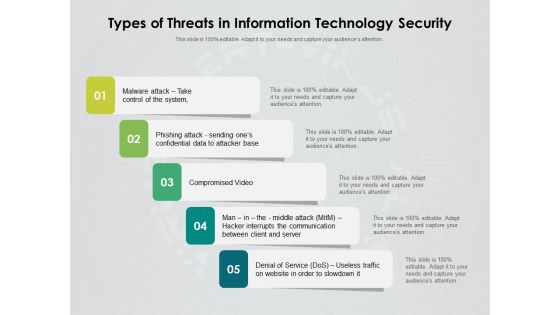
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prepare Data Backup For Sensitive Information IT Security IT Ppt Infographics Clipart PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Deliver an awe inspiring pitch with this creative prepare data backup for sensitive information it security it ppt infographics clipart pdf bundle. Topics like manipulation, secure, disasters, cloud services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Prepare Data Backup For Sensitive Information Download PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Deliver an awe inspiring pitch with this creative desktop security management prepare data backup for sensitive information download pdf bundle. Topics like information, secure, service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Mission Vision And Core Values Demonstration PDF
This slide highlights the security company mission, vision and core values which includes trust, collaboration, service, and innovation as base of core values.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Mission Vision And Core Values Demonstration PDF bundle. Topics like Peace Of Mind, Collaboration, Innovation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
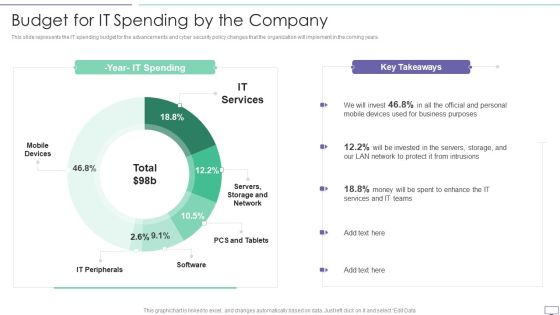
IT Security Hacker Budget For IT Spending By The Company Download PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years.Deliver an awe inspiring pitch with this creative IT Security Hacker Budget For IT Spending By The Company Download PDF bundle. Topics like Business Purposes, Protect Intrusions, Services Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Addressing Employee Crisis Prevention Inspiration PDF
The crisis management team should assist employees so that they can avoid the crisis before it hits. The firm should ensure that employee behave loyally and lawfully, refraining from any kind of misconduct. Deliver an awe inspiring pitch with this creative developing firm security strategy plan addressing employee crisis prevention inspiration pdf bundle. Topics like services, communication mode, frequency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF bundle. Topics like Operations Status Tool, Management Services Managed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
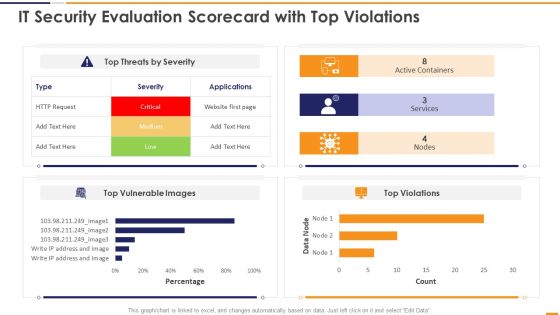
IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF bundle. Topics like Top Threats Severity, Active Containers Services, Top Vulnerable Images can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Addressing The Companies Digitization Levels By Sectors Clipart PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Addressing The Companies Digitization Levels By Sectors Clipart PDF bundle. Topics like Overall Digitization, Professional Services, Business Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Infographics PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks current security monitoring infographics pdf bundle. Topics like monitoring, service, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
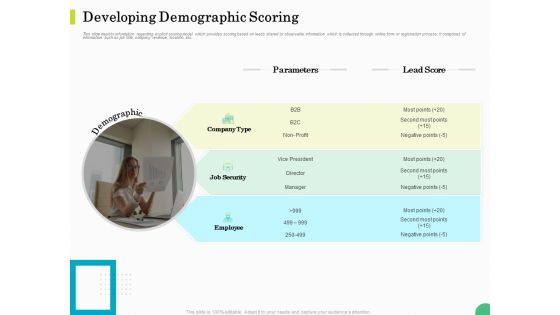
Evaluating Rank Prospects Developing Demographic Scoring Ppt Layouts Objects PDF
This slide depicts information regarding explicit scoring model which provides scoring based on leads shared or observable information which is collected through online form or registration process. It comprises of information such as job title, company revenue, location, etc. Presenting evaluating rank prospects developing demographic scoring ppt layouts objects pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like parameters, lead score, job security, employee, demographic. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Employee Ranking System Of Prescribed Drugs Attributes Demonstration PDF
The purpose of this slide is to analyze the various business drivers by comparing the relative importance of each driver against the other drivers. This includes shortening market rate, global competition, mass customization, secure product, and maximizing profitability. Persuade your audience using this Employee Ranking System Of Prescribed Drugs Attributes Demonstration PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Benefits, Interaction, Formulization. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. This modern and well arranged Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF bundle. Topics like Virtualization Threats, Information Interception, Unauthorized Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financing Catalogue For Security Underwriting Agreement Major Investment Banking Deals In Last Summary PDF
The slide provides the top five deals by profit amount of the company in last five years. It comprises, year, client name, deal type and brief information about all the five deals. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement major investment banking deals in last summary pdf bundle. Topics like automobile, financials services, healthcare, construction can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financing Catalogue For Security Underwriting Agreement IPO Deals Count In Different Sectors Diagrams PDF
The slide provides the graph of number of IPO deals by sector which the company has handled in last five years. It also covers key facts CAGR growth, raised amount etc. related to IPO deals of the company. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement ipo deals count in different sectors diagrams pdf bundle. Topics like manufacturing, financial services, automobile, food and beverages can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
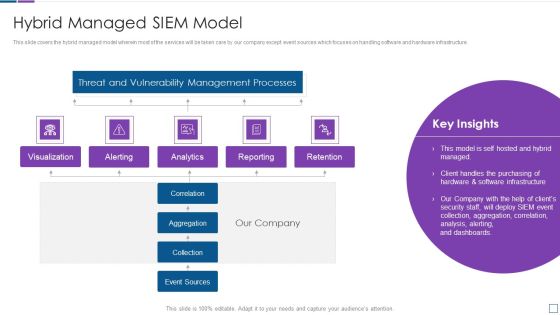
Real Time Assessment Of Security Threats Hybrid Managed SIEM Model Brochure PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative real time assessment of security threats hybrid managed siem model brochure pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Components To Enhance Processes Ppt PowerPoint Presentation Complete With Slides
This content ready template on Cyber Security Components To Enhance Processes Ppt PowerPoint Presentation Complete With Slides has all the details you need to mention in a presentation. The template also emphasizes critical business service details and charges as a separate package. You can customize each slide of this forteen part complete deck into creative bundles and turn your business visitors into customers. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download with a click below and gain instant access to this handy preset.

Cybersecurity Risk Scorecard Information Security Risk Rating Scorecard With Customer Order Slides PDF
This is a cybersecurity risk scorecard information security risk rating scorecard with customer order slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security risk rating scorecard with customer order. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Marketing Key Challenges Of Cloud Services Ppt PowerPoint Presentation Styles Graphics Template PDF
Deliver an awe-inspiring pitch with this creative cloud based marketing key challenges of cloud services ppt powerpoint presentation styles graphics template pdf bundle. Topics like building private cloud, performance, managing multiple clouds, compliance, governance, control, lack resources, expertise, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Importance Of Secure Ecommerce Payment Systems Deploying Ecommerce Order Management Software Rules PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc.This modern and well-arranged Importance Of Secure Ecommerce Payment Systems Deploying Ecommerce Order Management Software Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Designing And Deployment Securing Our Data With CRM Ppt PowerPoint Presentation File Backgrounds PDF
This slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. This is a designing and deployment securing our data with crm ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like crm data security model, security model, profile based security, record sharing, group based security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stock Photo Dollar Bundles Safe With Lock And Chain Image Graphics For PowerPoint Slide
This image slide displays dollar bundle locked with chain. Use this image, in your PowerPoint presentations to express views on financial security and monetary savings. This image slide will enhance the quality of your presentations.

Flowchart For Security Orchestration And Automation System Icons PDF
The following slide highlights conceptual digitization of security systems flowchart. It includes components such as SOAR platform, orchestration process, unification, automation, detection, analysis, respond, security tool etc. Persuade your audience using this Flowchart For Security Orchestration And Automation System Icons PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Automation, Orchestration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Secure Server Access Ppt PowerPoint Presentation Icon Show Cpb
Presenting this set of slides with name secure server access ppt powerpoint presentation icon show cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure server access to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
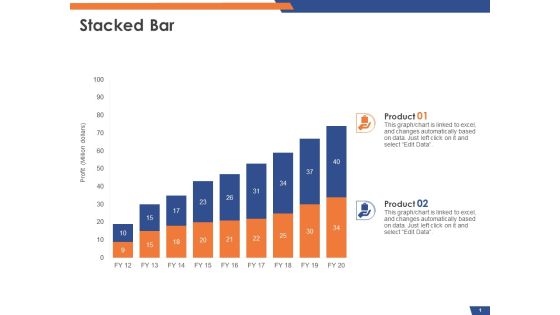
Email Security Market Research Report Stacked Bar Ppt Styles Slide PDF
Presenting this set of slides with name email security market research report stacked bar ppt styles slide pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Stacked Bar Ppt Ideas Infographics PDF
Presenting this set of slides with name global cloud based email security market stacked bar ppt ideas infographics pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
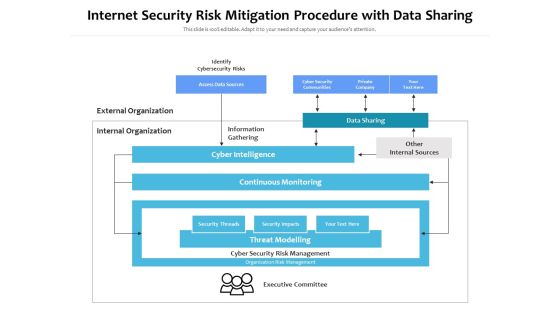
Internet Security Risk Mitigation Procedure With Data Sharing Ppt PowerPoint Presentation Pictures Show PDF
Persuade your audience using this internet security risk mitigation procedure with data sharing ppt powerpoint presentation pictures show pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including identify cybersecurity risks, external organization, internal organization, information gathering, data sharing, other internal sources, cyber intelligence, continuous monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
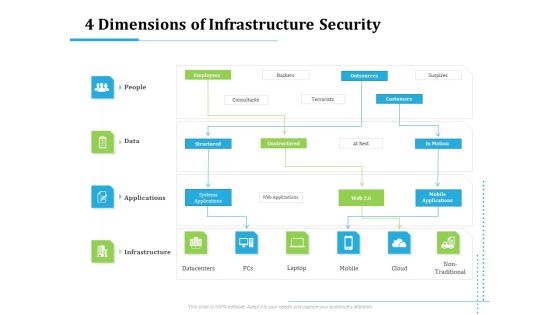
Information Technology Functions Management 4 Dimensions Of Infrastructure Security Ppt Slides Structure PDF
Presenting information technology functions management 4 dimensions of infrastructure security ppt slides structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, data, applications, infrastructure, datacentres, mobile, cloud, non traditional. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Utilizing Infrastructure Management Using Latest Methods 4 Dimensions Of Infrastructure Security Introduction PDF
Presenting utilizing infrastructure management using latest methods 4 dimensions of infrastructure security introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, data, applications, infrastructure, datacentres, mobile, cloud, non traditional. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Intelligence Framework For Application Consumption Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like power management, building management, security management, security effectiveness, global supervision can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Buying A Home Real Estate Business PowerPoint Templates And PowerPoint Themes 1012
Buying A Home Real Estate BusinessPowerPoint Templates And PowerPoint Themes 1012-The above template displays a diagram of a 3d house with a golden key and stack of gold coins. This image represents the concept of buying a home, real estate. Adjust the above image in your PPT presentations to visually support your content in your Real Estate and Financial PPT slideshows. It signifies development, investment, success, treasure and wealth. Add charm and personality to your presentations with our attractive template.-Buying A Home Real Estate BusinessPowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Keys for buying new home, sales, business, security, real estate, metaphor

Protect Your Money Form Market Risks PowerPoint Templates Ppt Backgrounds For Slides 0513
Our Protect Your Money Form Market Risks PowerPoint Templates PPT Backgrounds For Slides will will follow the drill. They accomplish the task assigned to them. Do the drill with our umbrellas PowerPoint Templates. Your ideas will march ahead. Place the orders with your thoughts. Our security PowerPoint Templates know the drill.

Money Growth Depends On Time PowerPoint Templates Ppt Backgrounds For Slides 0613
Our Money Growth Depends On Time PowerPoint Templates PPT Backgrounds For Slides will will follow the drill. They accomplish the task assigned to them. Do the drill with our Security PowerPoint Templates. Your ideas will march ahead. Place the orders with your thoughts. Our Clocks PowerPoint Templates know the drill.

Secured Video Hosting Platform Investor Capital Funding Addressing Diverse Client Profiles For Online Video Platform Pictures PDF
This slide caters details about diversified client profiles and base have potential to cater services from online video platform. Deliver an awe inspiring pitch with this creative secured video hosting platform investor capital funding addressing diverse client profiles for online video platform pictures pdf bundle. Topics like technology, finance and insurance, media and entertainment, it and communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Yellow Folder With Lock Security PowerPoint Templates And PowerPoint Themes 1112
We present our Yellow Folder With Lock Security PowerPoint Templates And PowerPoint Themes 1112.Use our Symbol PowerPoint Templates because, Coincidentally it always points to the top. Use our Computer PowerPoint Templates because, The alphabetical order is a time honoured concept. Use our Technology PowerPoint Templates because, Explain the relevance of the different layers and stages in getting downto your core competence, ability and desired result. Use our Security PowerPoint Templates because, Illustrate your plans on using the many social media modes available to inform soceity at large of the benefits of your product. Use our Business PowerPoint Templates because, Set out the goals and your plan of action for them.Use these PowerPoint slides for presentations relating to Yellow folder and lock Symbol Computer Technology Security Business. The prominent colors used in the PowerPoint template are Yellow, White, Black

Success Key For Top Position PowerPoint Templates Ppt Backgrounds For Slides 0713
Our Success Key For Top Position PowerPoint Templates PPT Backgrounds For Slides 0713 will will follow the drill. They accomplish the task assigned to them. Do the drill with our magnifier glasses PowerPoint Templates. Your ideas will march ahead. Place the orders with your thoughts. Our people PowerPoint Templates know the drill.

Program Evaluation Templates Bundle Data Conversion Strategy Ppt Portfolio Example Topics PDF
Presenting program evaluation templates bundle data conversion strategy ppt portfolio example topics pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like recovery plan, security concerns, approach of data, project. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
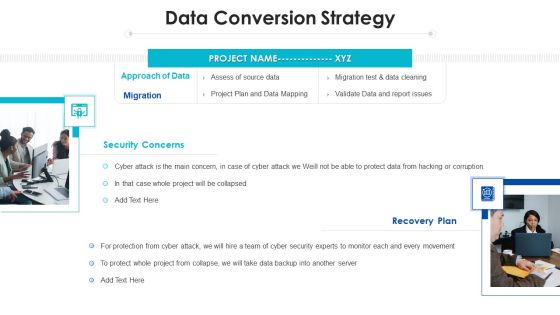
Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF
Presenting Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Approach Data, Recovery Plan, Cyber Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
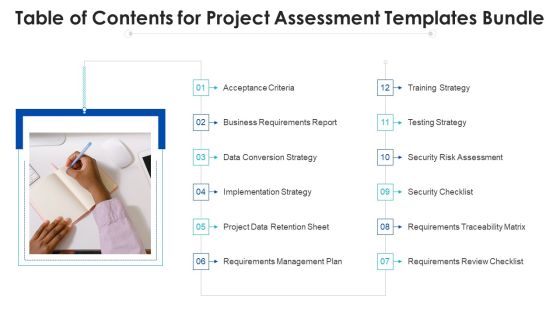
Table Of Contents For Project Assessment Templates Bundle Ppt Model Templates PDF
This is a Table Of Contents For Project Assessment Templates Bundle Ppt Model Templates PDF template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Acceptance Criteria, Implementation Strategy, Security Checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Consumer Service Strategy Project Deliverables And People Displayed In RACI Matrix Topics PDF
This slide provides information regarding the RACI matrix that is used during customer relationship transformation process with important project deliverables involved and key people involved. Deliver an awe inspiring pitch with this creative Consumer Service Strategy Project Deliverables And People Displayed In RACI Matrix Topics PDF bundle. Topics like Crm Goals Prioritizing, Risk And Security Management, Crm Team Building can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Defining Vulnerability Rating With Criteria Summary PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
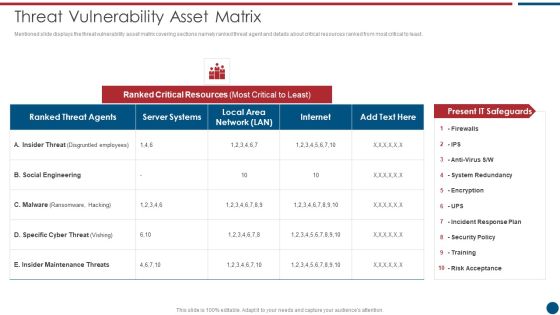
Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF bundle. Topics like Ranked Critical, Server Systems, Social Engineering can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cost Of Education Savings Future PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Cost Of Education Savings Future PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Education PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds. Use our Future PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Present our Science PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Use our Security PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Download our Success PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place.Use these PowerPoint slides for presentations relating to Piggy bank over a stack of colorful books, education, future, science, security, success. The prominent colors used in the PowerPoint template are Yellow, Red, White.
Casino Chip Icon Gambling PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Casino Chip Icon Gambling PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Money PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds. Use our Success PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience. Use our Security PowerPoint Templates because You should Kick up a storm with our PowerPoint Templates and Slides. The heads of your listeners will swirl with your ideas. Download and present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas.Use these PowerPoint slides for presentations relating to Casino chips in stack, Money, Finance, Business, Success, Security. The prominent colors used in the PowerPoint template are Red, Blue, Green.

Security Operations Framework To Monitor Security Threats Demonstration PDF
This slide display security operations threat detection and eradication process in order to increase security at all stages of development. It includes new security incident, response to threat, root cause analysis, etc. Pitch your topic with ease and precision using this Security Operations Framework To Monitor Security Threats Demonstration PDF. This layout presents information on Execute Mitigation, Develop, Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Managed IT Services Pricing Model IT Service Roadmap Ppt Summary Grid PDF
This slide covers service roadmap for 4 quarters including milestones such as monitoring, support and remediation, management and advertising, and security. Deliver an awe-inspiring pitch with this creative managed it services pricing model it service roadmap ppt summary grid pdf bundle. Topics like monitoring, support and remediation, management, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Help On Web Internet PowerPoint Templates And PowerPoint Themes 1112
We present our Help On Web Internet PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, Bullet-point your thoughts and ideas to profitably accomplish every step of every stage along the way. Use our Computer PowerPoint Templates because, Trigger their minds with your interesting ideas. Use our Internet PowerPoint Templates because, Listen to ideas and thoughts. Use our Business PowerPoint Templates because, The alphabetical order is a time honoured concept. Use our Success PowerPoint Templates because, Your foot is on the pedal and your company is purring along smoothly.Use these PowerPoint slides for presentations relating to Help on web internet, security, computer, internet, business, success. The prominent colors used in the PowerPoint template are Red, Orange, White

Golden Key Chain With Earth Globe PowerPoint Templates And PowerPoint Themes 1112
We present our Golden Key Chain With Earth Globe PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, The alphabetical order is a time honoured concept. Use our Success PowerPoint Templates because, Individual components well researched and understood in their place. Use our Globe PowerPoint Templates because, Decorate it with your well wrapped ideas and colourful thoughts. Use our Spheres PowerPoint Templates because, Creating a winner is your passion and dream. Use our Business PowerPoint Templates because, Employ the right colours for your brilliant ideas.Use these PowerPoint slides for presentations relating to Key from the world, security, success, spheres, business, globe. The prominent colors used in the PowerPoint template are Yellow, Blue light, White
Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Find highly impressive Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
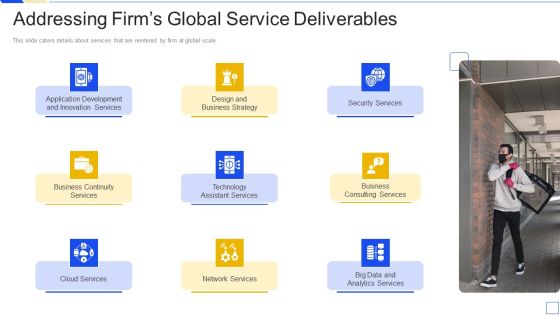
Service Marketing Fundraising Addressing Firms Global Service Deliverables Portrait PDF
This slide caters details about services that are rendered by firm at global scale. Deliver an awe inspiring pitch with this creative service marketing fundraising addressing firms global service deliverables portrait pdf bundle. Topics like business continuity services, technology assistant services, business consulting services, security services, network services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Security Of Employees Devices Microsoft PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Deliver an awe inspiring pitch with this creative desktop security management security of employees devices microsoft pdf bundle. Topics like security of employees devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Homeland Security Review Powerpoint Slide Inspiration
This is a homeland security review powerpoint slide inspiration. This is a four stage process. The stages in this process are national security strategy, critical infrastructure and climate, homeland security review, execute order.

Connected Devices Network Technology Stack Layers With Growth Rate Rules PDF
This slide provide insights about various technological layers of IoT to determine business growth opportunities in future. It includes technological layers such as services, IoT application and analytics, identify and security, IoT backbone, communication and connected devices. Showcasing this set of slides titled Connected Devices Network Technology Stack Layers With Growth Rate Rules PDF. The topics addressed in these templates are Technology Layers, Description, Market Size. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizational Security Solutions Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative organizational security solutions impact of effective security management information pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
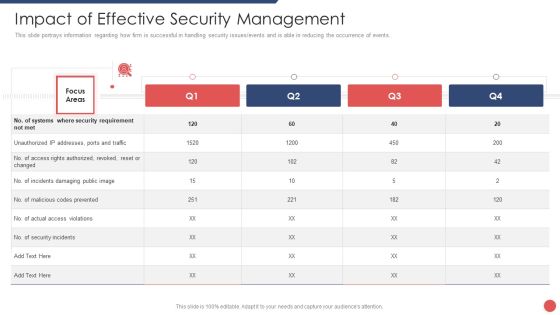
Security Functioning Centre Impact Of Effective Security Management Brochure PDF
This slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative security functioning centre impact of effective security management brochure pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Why Cloud Security Is Important Pictures PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Why Cloud Security Is Important Pictures PDF bundle. Topics like Centralized Security, Cost Effective, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Security Operations Implementation Timeline Activity Background PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative organizational security solutions security operations implementation timeline activity background pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Determine Security Risks Dashboard Pictures PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified . Deliver an awe inspiring pitch with this creative security functioning centre determine security risks dashboard pictures pdf bundle. Topics like inherent risk, residual risk, profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
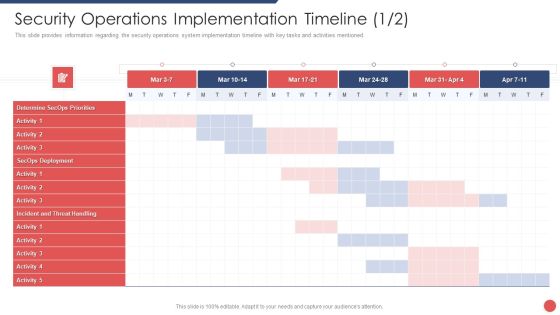
Security Functioning Centre Security Operations Implementation Timeline Mar Portrait PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative security functioning centre security operations implementation timeline mar portrait pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security functioning centre assessment of security maturity spectrum slides pdf bundle. Topics like security mature, operational efficiency, security capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
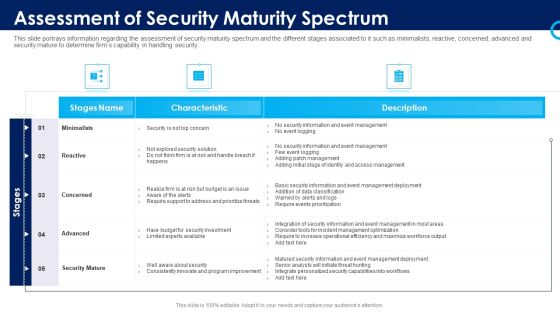
Organizational Security Solutions Assessment Of Security Maturity Spectrum Rules PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative organizational security solutions assessment of security maturity spectrum rules pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF
The following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF today and make your presentation stand out from the rest.
Key Features For Effective Business Management 4 Dimensions Of Infrastructure Security Ppt Icon Gridlines PDF
Presenting this set of slides with name key features for effective business management 4 dimensions of infrastructure security ppt icon gridlines pdf. This is a four stage process. The stages in this process are people, data, applications, infrastructure, mobile applications, suspires, outsources, systems applications, cloud. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Developing Firm Security Strategy Plan Addressing Performance Indicators To Determine Security Standards Structure PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Deliver an awe inspiring pitch with this creative developing firm security strategy plan addressing performance indicators to determine security standards structure pdf bundle. Topics like incidents, offender management, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Major Reasons For Poor Security Guidelines PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks major reasons for poor security guidelines pdf bundle. Topics like outdated software, lack of proper protection, another dangerous aspect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
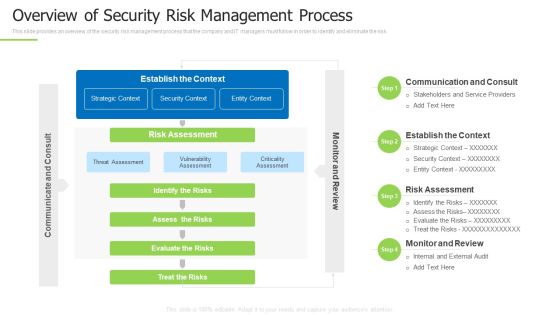
Techniques And Strategies To Reduce Security Management Risks Overview Of Security Risk Background PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks overview of security risk background pdf bundle. Topics like identify the risks, strategic context, vulnerability assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF. Use them to share invaluable insights on Vulnerability Ranking, High, LOW, MEDIUM, Attack Organization, Occurrence Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Summary PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative cyber stacks experienced by the company in previous financial year ppt summary pdf bundle. Topics like cyber stacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Digital Technology Adoption In Banking Industry Case Competition Most Important Portrait PDF
This slide shows the significant technological areas which the company needs to adopt along with their requirement percentage. Key areas include establishing digital capabilities, manage client security, building modern workplace, etc. Deliver an awe inspiring pitch with this creative Digital Technology Adoption In Banking Industry Case Competition Most Important Portrait PDF bundle. Topics like Adopt Cloud Services, Build Modern Workplace, Manage Client Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Three Stages Of Financial Health Governance Ppt PowerPoint Presentation Gallery Graphics Example PDF
Presenting three stages of financial health governance ppt powerpoint presentation gallery graphics example pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including housing security, food security, energy security, financial health. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Services Best Practices Marketing Plan Agenda Cloud Services Competitive Landscape Guidelines PDF
Deliver an awe inspiring pitch with this creative cloud services best practices marketing plan agenda cloud services competitive landscape guidelines pdf bundle. Topics like security framework, pricing transparency, hybrid cloud expertise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Services Best Practices Marketing Plan Agenda Key Challenges Of Cloud Services Background PDF
Deliver an awe inspiring pitch with this creative cloud services best practices marketing plan agenda key challenges of cloud services background pdf bundle. Topics like performance, security, governance, resource, clouds can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
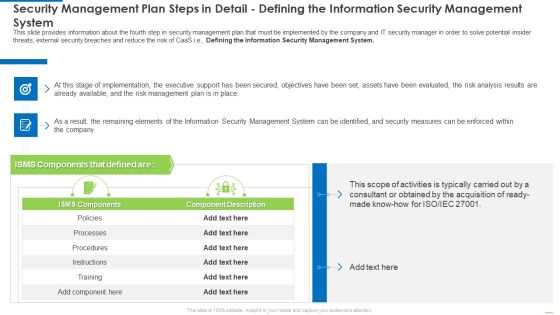
Security Management Plan Steps In Detail Defining The Information Security Management System Diagrams PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system diagrams pdf bundle. Topics like security management plan steps in detail - defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Sample PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system sample pdf bundle. Topics like security management plan steps in detail defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Characteristics Of Software As A Service Saas Pictures PDF
Deliver an awe inspiring pitch with this creative mesh computing technology hybrid private public iaas paas saas workplan characteristics of software as a service saas pictures pdf bundle. Topics like high availability, elastic infrastructure, data security, application security, automated provisioning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Developing Firm Security Strategy Plan Role Of Management In Effective Corporate Security Governance Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an awe inspiring pitch with this creative developing firm security strategy plan role of management in effective corporate security governance slides pdf bundle. Topics like strategic alignment, risk management, measuring performance, value delivery, managing resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
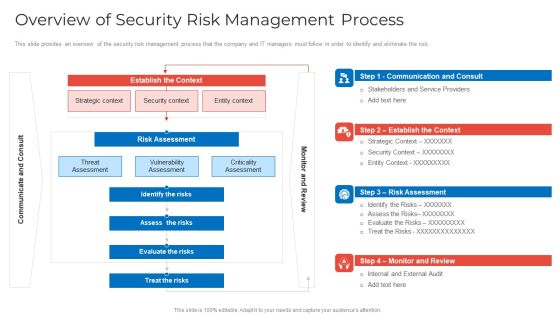
Implementing Security Management Strategy To Mitigate Risk Overview Of Security Risk Management Process Pictures PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative implementing security management strategy to mitigate risk overview of security risk management process pictures pdf bundle. Topics like identify the risks, assess the risks, evaluate the risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Executing Advance Data Analytics At Workspace Determine Role Of Security Centre In Firm Sample PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. This is a executing advance data analytics at workspace determine role of security centre in firm sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine role of security centre in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Housing Mortgage Additional Benefits For Home Loan Proposal Ppt Slides Background PDF
Deliver an awe inspiring pitch with this creative housing mortgage additional benefits for home loan proposal ppt slides background pdf bundle. Topics like credit cards, easy security investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
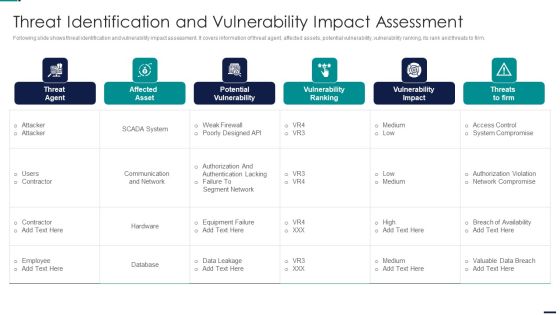
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Civil Infrastructure Designing Services Management It Infrastructure Optimization Pictures PDF
Deliver an awe inspiring pitch with this creative civil infrastructure designing services management it infrastructure optimization pictures pdf bundle. Topics like management, security, process, service, customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
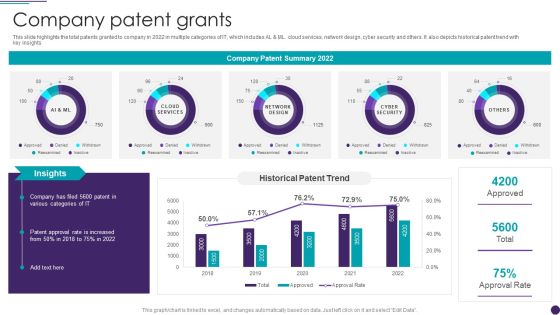
IT Services Business Profile Company Patent Grants Infographics PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative IT Services Business Profile Company Patent Grants Infographics PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Service Models IT Disadvantages Of Iaas Cloud Computing Layer Rules PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. Deliver an awe inspiring pitch with this creative cloud computing service models it disadvantages of iaas cloud computing layer rules pdf bundle. Topics like security, maintenance and upgrade, interoperability issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Support Services Management IT Infrastructure Optimization Ppt Pictures Brochure PDF
Deliver an awe inspiring pitch with this creative support services management it infrastructure optimization ppt pictures brochure pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Planning And Budgeting Sample Of Ppt Presentation
This is a planning and budgeting sample of ppt presentation. This is a eight stage process. The stages in this process are planning and budgeting, promoting stability and order, motivating and inspiring, aligning people, establishing direction, promoting change, controlling and problem solving, organizing and staffing.

Stock Photo Unlocked Money With Key For Security Concept PowerPoint Slide
This image slide displays unlocked money security concept with key. This image slide has been designed with dollar bundle locked with padlock and key. This image slide may be used in your presentations to express views on finance, savings, protection and accounting business finance. Create professional presentations using this image slide.

Overview Of Security Risk Management Process Formats PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative overview of security risk management process formats pdf bundle. Topics like strategic context, vulnerability assessment, security context, risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Growth Guidelines PDF
This slide portrays information regarding the dashboard that firm will track various security incidents detected. These incidents will be managed in order to avoid security risks. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan security incidents tracking dashboard growth guidelines pdf. Use them to share invaluable insights on number of open security incidents, open security incidents by age, average age of open security incidents, security incident backlog growth and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Defining The Information Security Management System Mockup PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system mockup pdf. Use them to share invaluable insights on implementation, management plan, security management, security measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Stock Photo Pile Of Dollars Chained And Locked PowerPoint Slide
This image displays dollar bundles locked in chains. Use this image slide, in your PowerPoint presentations to express views on financial security and monetary savings. This image will enhance the quality of your presentations.
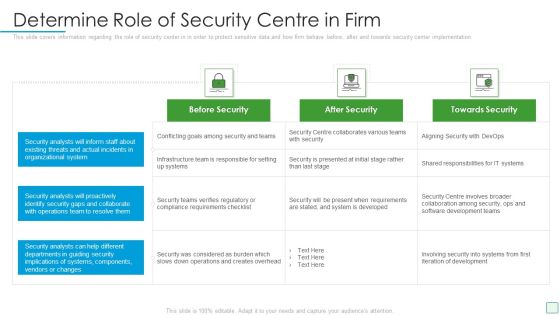
Developing Firm Security Strategy Plan Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan determine role of security centre in firm graphics pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Defining The Information Security Management System Summary PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system summary pdf Use them to share invaluable insights on instructions, processes, implementation, the executive and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Detail Risk Assessment And Analysis Template PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks security detail risk assessment and analysis template pdf Use them to share invaluable insights on security breach, perform a threat, several measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions Quotes Ppt Model PDF
Deliver an awe inspiring pitch with this creative organizational security solutions quotes ppt model pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
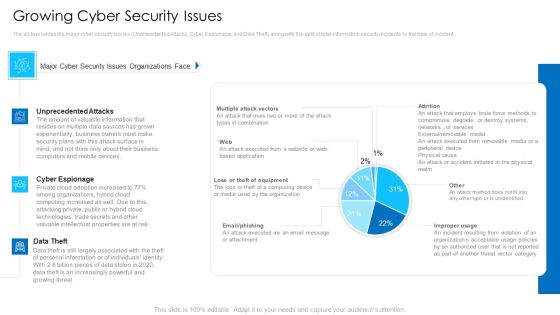
Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
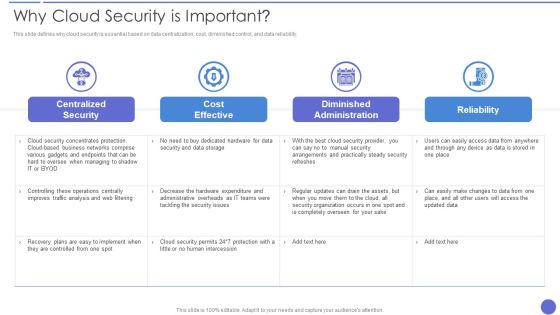
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Developing Firm Security Strategy Plan Addressing Performance Indicators To Determine Security Standards Contd Themes PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of staff and customer satisfaction, financial and staff. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan addressing performance indicators to determine security standards contd themes pdf. Use them to share invaluable insights on staff and customer satisfaction, financial, staff and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Contd Brochure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Presenting developing firm security strategy plan information security process to manage firms sensitive data contd brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like firewall audit checklist, vpn configuration, penetrating testing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Alerts Graphics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Presenting developing firm security strategy plan security incidents tracking dashboard alerts graphics pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like application whitelisting, patch applications, patch operating systems, restrict admin privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Contd Graphics PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Deliver and pitch your topic in the best possible manner with this project security administration it information security process to manage firms sensitive data contd graphics pdf. Use them to share invaluable insights on firewall audit checklist, vpn configuration, penetrating testing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
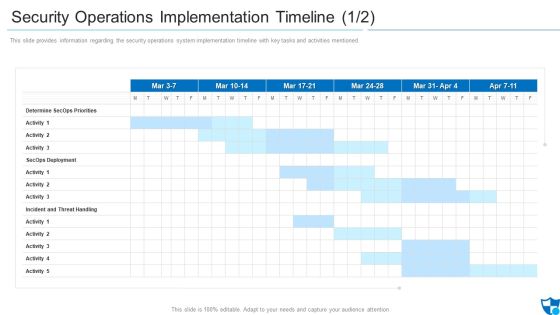
Security Operations Implementation Timeline Priorities Introduction PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned.Deliver an awe inspiring pitch with this creative security operations implementation timeline priorities introduction pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
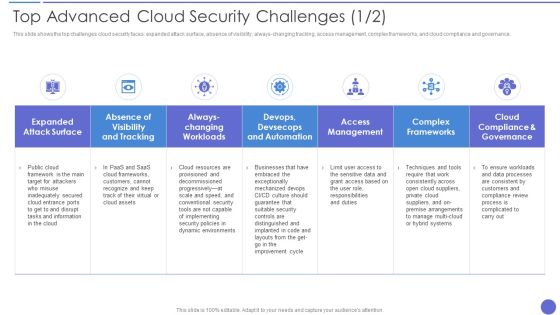
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Remote Summary PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management plan steps in detail remote summary pdf bundle. Topics like requirement for additional, remote access control, control security status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Process PowerPoint Templates Business Weak Broken Chains And Links Ropes Ppt Slides
Business Process PowerPoint Templates Business Weak Broken Chains And Links Ropes PPT Slides- At times, however, there is a crucial aspect that requires extra attention. Illustrate your chain of ideas focusing on that aspect or resource in order to enhance the quality of your product.-Business Process PowerPoint Templates Business Weak Broken Chains And Links Ropes PPT Slides-This template can be used for presentations relating to Analysing, Broken, Chain, Colour, Curiosity, Discovery, Equipment, Examining, Exploration, Eyesight, Focus, Glass, Handle, Horizontal, Isolated, Large, Lens, Link, Looking, Loupe, Magnification, Magnifying, Mystery, Nobody, Object, Optical, Photography, Reading, Research, Science, Scrutiny, Searching
Business Process PowerPoint Templates Business Weak Links And Chains Ppt Slides
Business Process PowerPoint Templates Business Weak Links and Chains PPT Slides-Chain reactions and the element of teamwork add value to your efforts. At times, however, there is a crucial aspect that requires extra attention. Illustrate your chain of ideas focusing on that aspect or resource in order to enhance the quality of your product.-Business Process PowerPoint Templates Business Weak Links and Chains PPT Slides-This template can be used for presentations relating to Analysing, Broken, Chain, Colour, Curiosity, Discovery, Equipment, Examining, Exploration, Eyesight, Focus, Glass, Handle, Horizontal, Isolated, Large, Lens, Link, Looking, Loupe, Magnification, Magnifying, Mystery, Nobody, Object, Optical, Photography, Reading, Research, Science, Scrutiny, Searching

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps Portrait PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Adopting Access Controls. This is a techniques and strategies to reduce security management risks security management plan steps portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like suggested coverage, security risk management, estimated security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Email Security Market Report Cyber Security Market Overview Ppt Infographics Format PDF
This slide shows a brief overview of the entire Cyber security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report cyber security market overview ppt infographics format pdf bundle. Topics like cyber security market overview can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Detail System Maintenance And Monitoring Mockup PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. This is a techniques and strategies to reduce security management risks security detail system maintenance and monitoring mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perfective maintenance, corrective maintenance, perfective maintenance You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Inspiration PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a techniques and strategies to reduce security management risks security management plan steps in detail inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like effective implementation, consistent with the organizational, represent the business You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Email Security Market Report KPI Dashboard For E Mail Security Ppt Slides Microsoft PDF
Deliver an awe inspiring pitch with this creative cloud based email security market report kpi dashboard for e mail security ppt slides microsoft pdf bundle. Topics like kpi dashboard for e mail security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home