Safety Pyramid

Security And Process Integration Various Technologies For Effective Secops Process Clipart PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a security and process integration various technologies for effective secops process clipart pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ensuring Nutrition Value Through Our Valuable Partners Food Security Excellence Ppt Layouts Visuals PDF
This slide provides information regarding the valuable partners associated to firm in order to render nutrition value to customers. This is a ensuring nutrition value through our valuable partners food security excellence ppt layouts visuals pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our filed partners, resource partners, advocacy partners, technical collaboration partners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
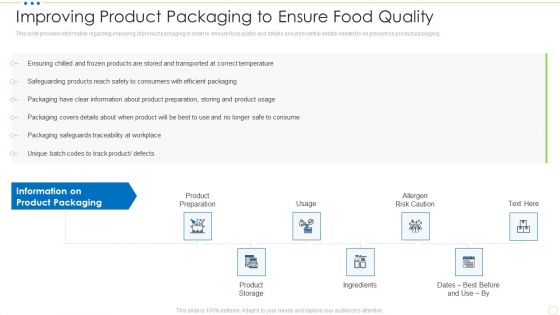
Improving Product Packaging To Ensure Food Quality Food Security Excellence Ppt Slides Template PDF
This slide provides information regarding improving of product packaging in order to ensure food quality and details about essential details needed to be present on product packaging. Presenting improving product packaging to ensure food quality food security excellence ppt slides template pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like product preparation, product storage, usage, ingredients, allergen risk caution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Project Security Administration IT Addressing Frequent Communication For Project Quality Management Icons PDF
This slide provides information regarding meetings that held in order to keep consistent quality entire project. These meetings are held on quarterly, annual basis. Presenting project security administration it addressing frequent communication for project quality management icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like executive, leaders, coordinators, initiation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Ensuring Vital Records Maintenance Topics PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization ensuring vital records maintenance topics pdf. Use them to share invaluable insights on ensuring vital records maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secured Video Hosting Platform Investor Capital Funding Solutions Provided By Online Video Hosting Platform Introduction PDF
This slide caters details about solutions rendered by video hosting platform in order to solve issues by providing platform to upload videos and video conversion for accessibility. Presenting secured video hosting platform investor capital funding solutions provided by online video hosting platform introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like solutions provided by online video hosting platform. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Evaluating Financial Practices In Firm Graphics PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. This is a corporate security and risk management evaluating financial practices in firm graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluating financial practices in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in sixty four slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Use this Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
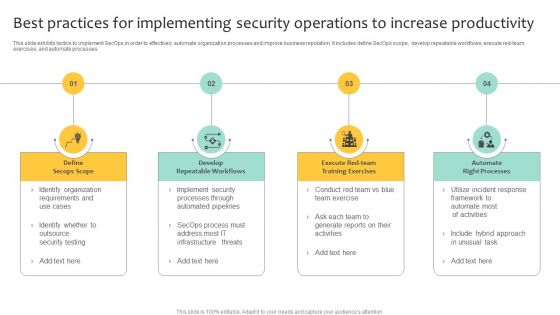
Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF
This slide exhibits tactics to implement SecOps in order to effectively automate organization processes and improve business reputation. It includes define SecOps scope, develop repeatable workflows, execute red-team exercises, and automate processes. Presenting Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Develop Repeatable Workflows, Automate Right Processes, Define Secops Scope. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Increasing Information Security Awareness In Company Using Various Techniques Complete Deck
Use this Increasing Information Security Awareness In Company Using Various Techniques Complete Deck to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in fifteen slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
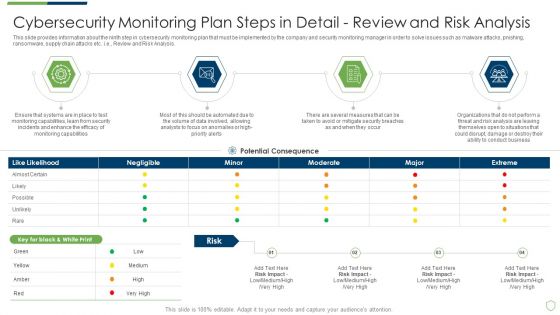
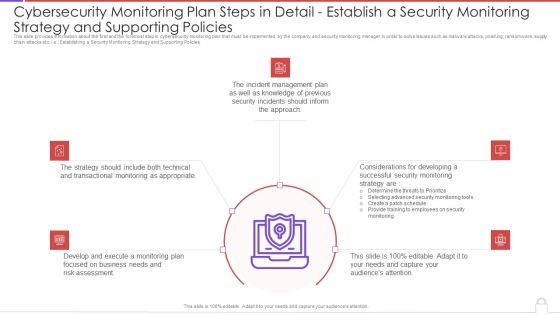
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
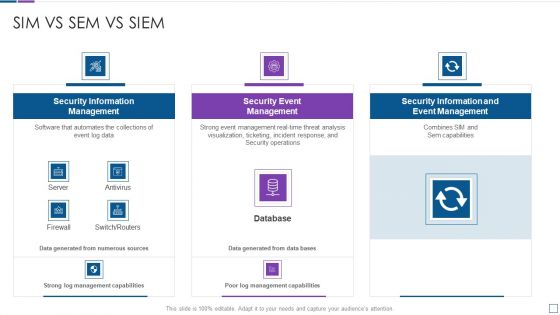
Real Time Assessment Of Security Threats Sim Vs Sem Vs SIEM Diagrams PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats sim vs sem vs siem diagrams pdf bundle. Topics like security information management, security event management, security information and event management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Issues Addressed By Dcaas Elements PDF
This slide brings forth various issues which are addressed by data service centers to provide users a solution in order to improve current business performance. The various issues addressed are data management, hyper converged infrastructure, data security and file storage. Presenting Issues Addressed By Dcaas Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Management, Data Security, Converged Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Guidelines To Create An Advanced Security Management Plan Table Of Contents Pictures PDF
Deliver an awe inspiring pitch with this creative guidelines to create an advanced security management plan table of contents pictures pdf bundle. Topics like essential elements, security management challenges, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF bundle. Topics like Security Awareness, Current Assessment, Security Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Demonstration PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan. Presenting Security management plan steps in detail data backup and data loss recovery plan demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security management plan steps in detail - data backup and data loss recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
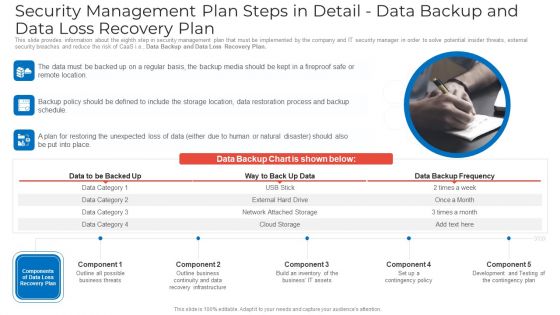
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Email Security Market Report Key Players Ppt Ideas Slides PDF
A comparative analysis of the key players if E-Mail Security Industry are displayed in this slide. Deliver an awe inspiring pitch with this creative cloud based email security market report key players ppt ideas slides pdf bundle. Topics like key players can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
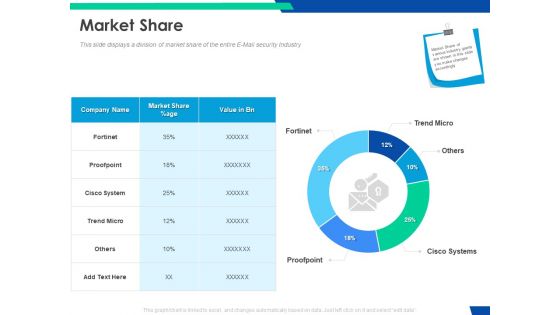
Cloud Based Email Security Market Report Market Share Ppt File Background PDF
This slide displays a division of market share of the entire E Mail security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report market share ppt file background pdf bundle. Topics like market share can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financial Losses To The Organizations Due To Security Issues Themes PDF
Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues themes pdf bundle. Topics like financial losses to the organizations due to security issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Environments Best Suited For Efficient And Secure Supply Chains Information PDF
Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains information pdf bundle. Topics like environments best suited for efficient and secure supply chains can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
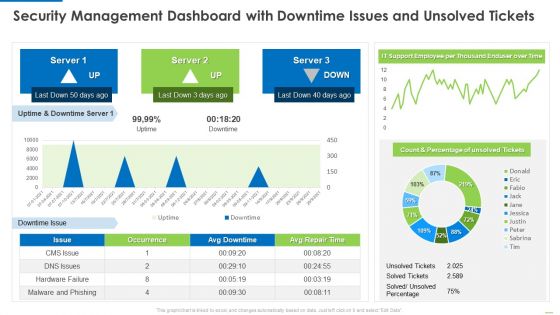
Security Management Dashboard With Downtime Issues And Unsolved Tickets Introduction PDF
Deliver an awe inspiring pitch with this creative Security management dashboard with downtime issues and unsolved tickets introduction pdf bundle. Topics like security management dashboard with downtime issues and unsolved tickets can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Inspiration PDF
Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control inspiration pdf bundle. Topics like deploying remote access, provides a secure connection, requirement for additional can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Introduction PDF
Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate introduction pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Developing Firm Security Strategy Plan Information PDF
Deliver an awe inspiring pitch with this creative table of contents for developing firm security strategy plan information pdf bundle. Topics like implementing, security, management, corporate, governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
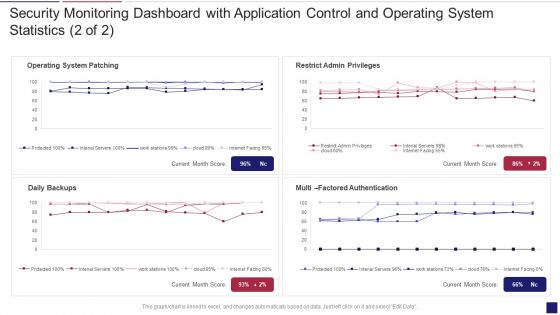
Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Operating Designs PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
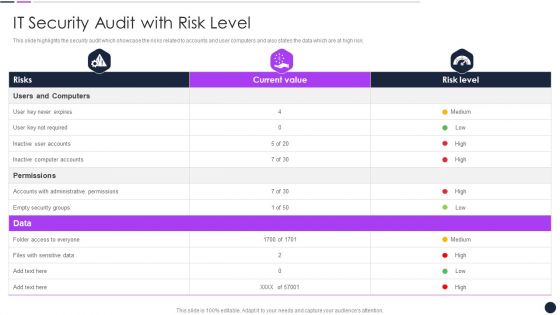
Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF
Deliver an awe inspiring pitch with this creative Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF bundle. Topics like Inactive Computer, Administrative Permissions, Security Groups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

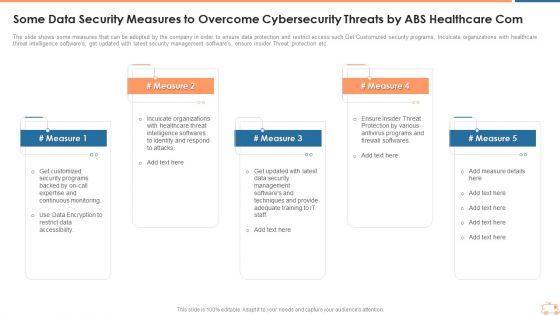
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
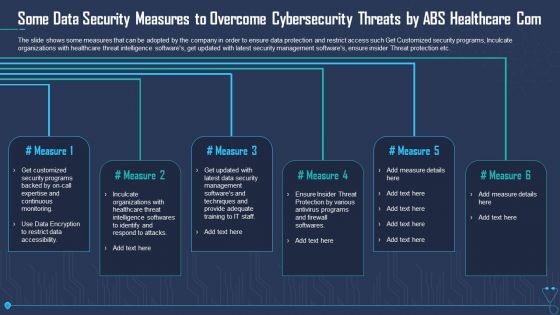
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
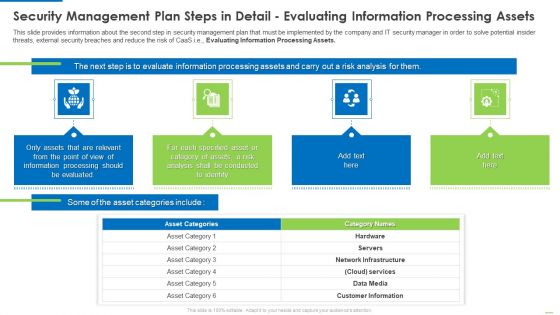
Security Management Plan Steps In Detail Evaluating Information Processing Assets Summary PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e.Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processing should be evaluated, conducted to identify, category of assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Summary PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. Presenting security management plan steps in detail system maintenance and monitoring summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like types of system maintenance, installation costs, types of system monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

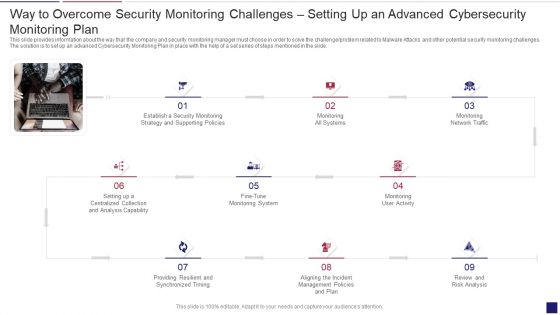
Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Template PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge or problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a way to overcome security monitoring challenges setting up an advanced cybersecurity template pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like establish security, monitoring strategy, supporting policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
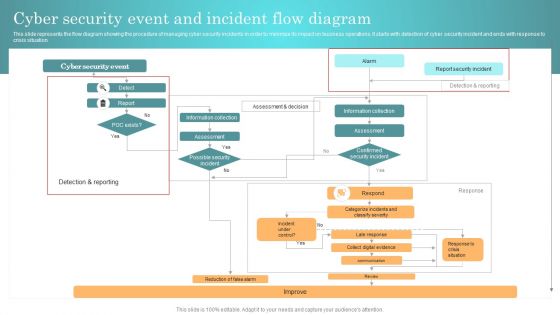
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Retrieve professionally designed Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
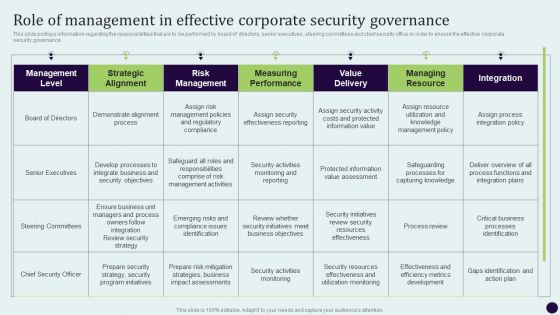
Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Slidegeeks is here to make your presentations a breeze with Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
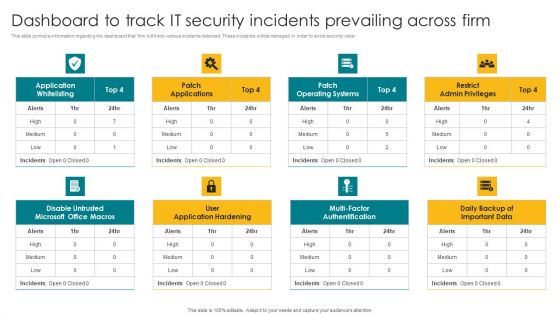
Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF.

Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF today and make your presentation stand out from the rest
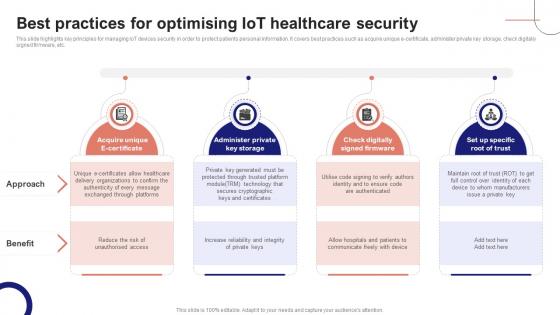
IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
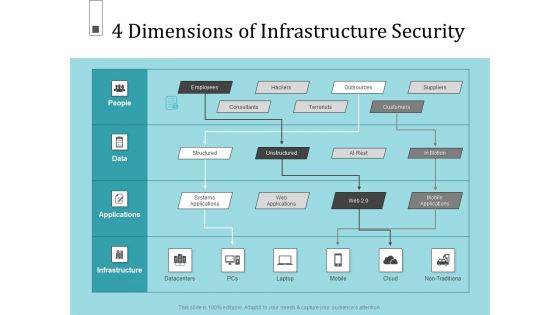
Infrastructure Project Management In Construction 4 Dimensions Of Infrastructure Security Information PDF
Deliver an awe inspiring pitch with this creative infrastructure project management in construction 4 dimensions of infrastructure security information pdf. bundle. Topics like consultants, terrorists, structured, systems applications, suppliers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Engineering And Industrial Facility Management 4 Dimensions Of Infrastructure Security Graphics PDF
Deliver an awe inspiring pitch with this creative construction engineering and industrial facility management 4 dimensions of infrastructure security graphics pdf bundle. Topics like structured, unstructured, systems applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
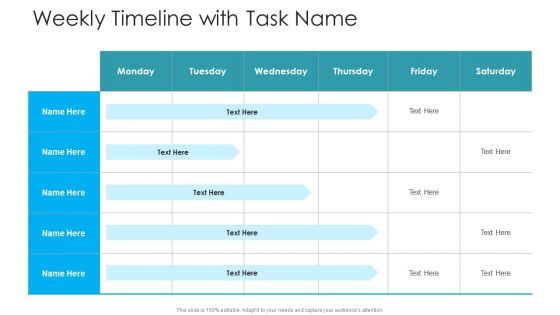
Weekly Timeline With Task Name Hacking Prevention Awareness Training For IT Security Download PDF
Deliver an awe inspiring pitch with this creative weekly timeline with task name hacking prevention awareness training for it security download pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slides For Case Competition Overpower The Obstacle Of Cyber Security In Medicare Microsoft PDF
Deliver an awe inspiring pitch with this creative icons slides for case competition overpower the obstacle of cyber security in medicare microsoft pdf bundle. Topics like Icons can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financial Losses To The Organizations Due To Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues mockup pdf bundle. Topics like physical theft of a data carrying device, malware attacks, insider misuse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Landscape Architecture Planning And Management 4 Dimensions Of Infrastructure Security Sample PDF
Deliver an awe inspiring pitch with this creative landscape architecture planning and management 4 dimensions of infrastructure security sample pdf bundle. Topics like people, data, applications, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
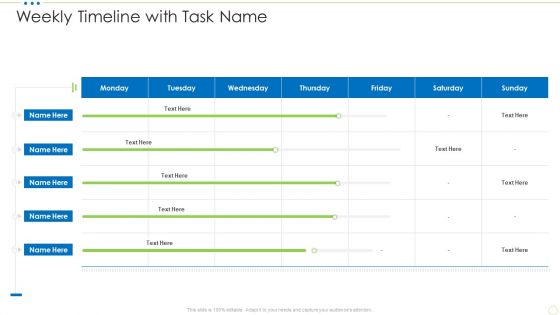
Weekly Timeline With Task Name Food Security Excellence Ppt Ideas Professional PDF
Deliver an awe inspiring pitch with this creative weekly timeline with task name food security excellence ppt ideas professional pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways Through Which Security Data Can Be Compromised And Measures To Deal With Them Designs PDF
Deliver an awe inspiring pitch with this creative ways through which security data can be compromised and measures to deal with them designs pdf bundle. Topics like attack description, ways to mitigate attack, program and implement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Weekly Timeline With Task Name Clipart PDF
Deliver an awe inspiring pitch with this creative developing firm security strategy plan weekly timeline with task name clipart pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Secured Video Hosting Platform Investor Capital Funding Table Of Content Pictures PDF
Deliver an awe inspiring pitch with this creative secured video hosting platform investor capital funding table of content pictures pdf bundle. Topics like sales and distribution, online video platform, revenue generation, future initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Table Of Content Secured Video Hosting Platform Investor Capital Funding Icons PDF
Deliver an awe inspiring pitch with this creative table of content secured video hosting platform investor capital funding icons pdf bundle. Topics like online video hosting platform overview, growth potential of online video platform market, addressing purpose defining brand and culture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
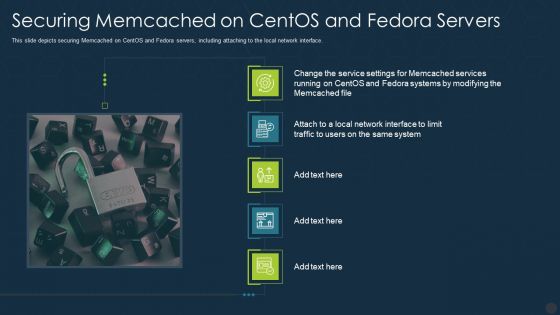
Securing Memcached On Centos And Fedora Servers Ppt Infographics Show PDF
Deliver an awe inspiring pitch with this creative securing memcached on centos and fedora servers ppt infographics show pdf bundle. Topics like system, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
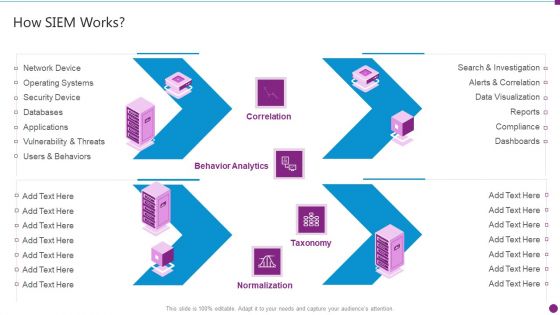
Security Information And Event Management Strategies For Financial Audit And Compliance How SIEM Works Clipart PDF
Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance how siem works clipart pdf bundle. Topics like behavior analytics, correlation, taxonomy, normalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Impact Assessment Matrix Formats PDF
Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Assessment Matrix Formats PDF bundle. Topics like Financial, Reputation, Regulatory, Operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Risk Based Procedures To IT Security Slides PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Risk Based Procedures To IT Security Slides PDF bundle. Topics like Gap Identification, Business Priorities, Digitization Levels can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
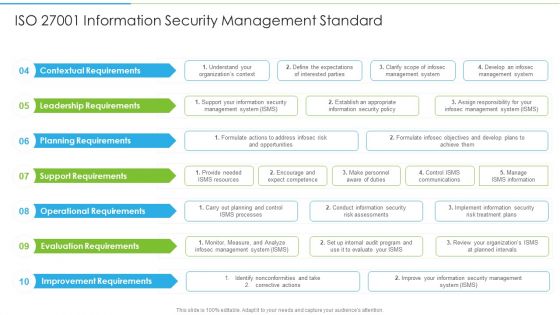
Ways To Accomplish ISO 27001 Accreditation ISO 27001 Information Security Management Infographics PDF
Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation ISO 27001 Information Security Management Infographics PDF bundle. Topics like Contextual Requirements, Leadership Requirements, Planning Requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Data Security Zero Trust Policy And Why You Should Embrace It Microsoft PDF
Deliver an awe inspiring pitch with this creative Cloud Data Security Zero Trust Policy And Why You Should Embrace It Microsoft PDF bundle. Topics like Authentication, Device Validation, Restrict Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
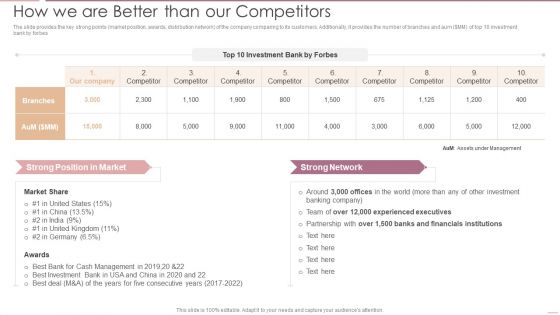
Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF
Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF bundle. Topics like Experienced Executives, Financials Institutions, Cash Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
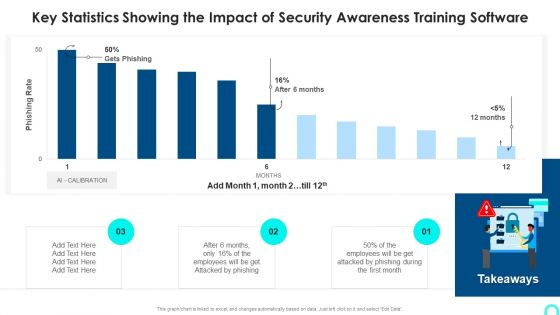
Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF
Deliver an awe inspiring pitch with this creative Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF bundle. Topics like Attacked Phishing, Employees Will, Phishing During can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
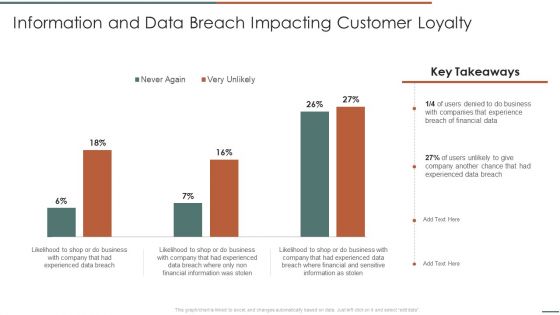
Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF
Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF bundle. Topics like Companies Experience, Financial Information, Breach Of Financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
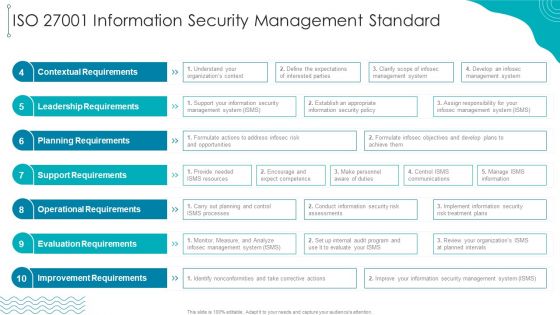
ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF
Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF bundle. Topics like Leadership Requirements, Contextual Requirements, Planning Requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Table Of Contents For Mobile Device Security Management In Organization Icons PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Mobile Device Security Management In Organization Icons PDF bundle. Topics like Analysing Current, Management Workplace, Management Systemcan be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
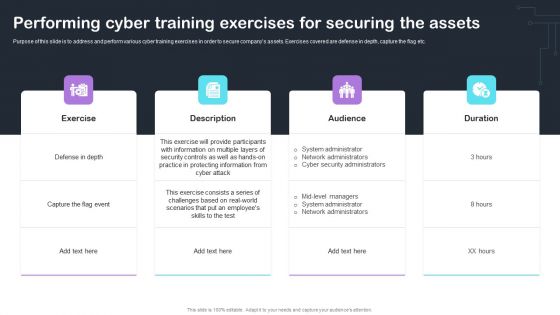
Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
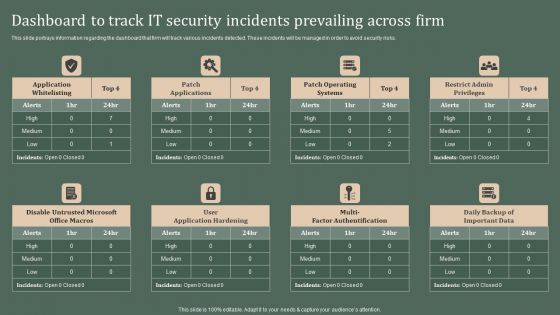
Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

How Aviation Industry Coping With COVID 19 Pandemic Aviation Security Incident Report Template PDF
This slide portrays aviation security incident report. It include five sections namely incident details, category security incident, incident assessment, aircraft information and incident description.Deliver an awe inspiring pitch with this creative how aviation industry coping with COVID 19 pandemic aviation security incident report template pdf. bundle. Topics like suspicious activity and items, aircraft information, category security incident, incident assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Essential Elements To Be Included In A Security Management Plan Elements PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan elements pdf bundle. Topics like risk, organization, security, systems, data communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Securing Our Data With CRM Designing And Deployment Ppt PowerPoint Presentation Icon Example File PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an awe inspiring pitch with this creative securing our data with crm designing and deployment ppt powerpoint presentation icon example file pdf bundle. Topics like crm data security, ip restriction, data storage and failover, communication protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF bundle. Topics like Traditional It Security, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
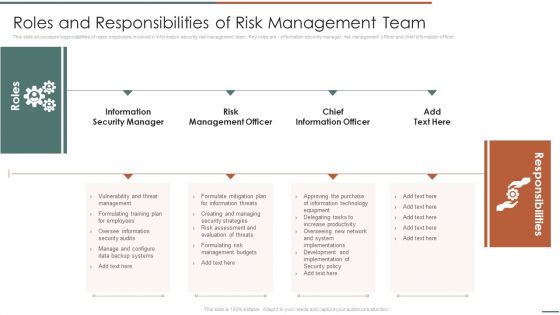
Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF bundle. Topics like Information Security Manager, Risk Management, Chief Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an awe inspiring pitch with this creative Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF bundle. Topics like Security And Compliance, Factor Authentication, Security Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
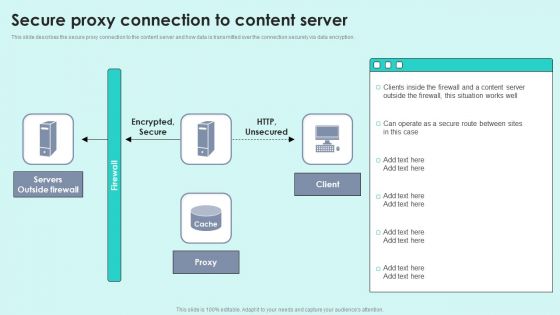
Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
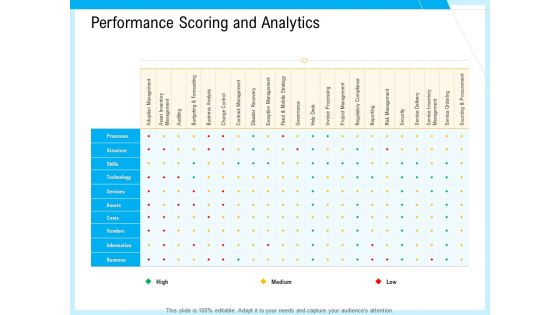
IT And Cloud Facilities Management Performance Scoring And Analytics Ppt Inspiration Design Ideas PDF
Deliver an awe-inspiring pitch with this creative it and cloud facilities management performance scoring and analytics ppt inspiration design ideas pdf bundle. Topics like processes, structure, technology, vendors, adoption management, security, project management, service delivery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
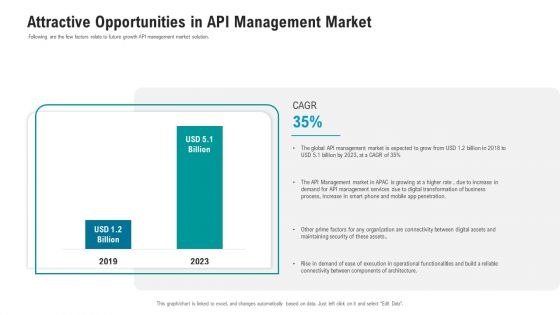
API Ecosystem Attractive Opportunities In API Management Market Infographics PDF
Following are the few factors relate to future growth API management market solution. Deliver an awe inspiring pitch with this creative api ecosystem attractive opportunities in api management market infographics pdf bundle. Topics like management market, services, process, organization, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition The ROI Of Security Awareness Training Brochure PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver an awe-inspiring pitch with this creative data breach prevention recognition the roi of security awareness training brochure pdf bundle. Topics like the roi of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Communication Plan General Format Hacking Prevention Awareness Training For IT Security Download PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe inspiring pitch with this creative communication plan general format hacking prevention awareness training for it security download pdf bundle. Topics like security awareness, communication, organizations, frequency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Security Awareness Staff Learning Communication Plan General Format Infographics PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning communication plan general format infographics pdf bundle. Topics like communication, security awareness, organizations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
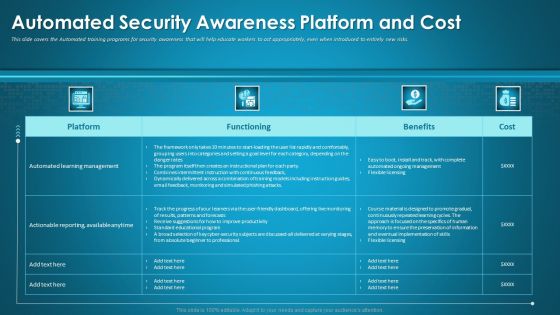
Organizational Network Staff Learning Automated Security Awareness Platform And Cost Introduction PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative organizational network staff learning automated security awareness platform and cost introduction pdf bundle. Topics like automated security awareness platform and cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
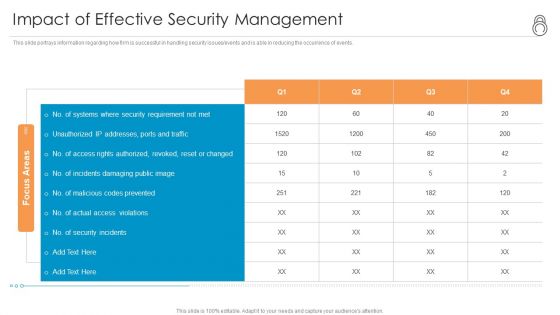
Enhanced Protection Corporate Event Administration Impact Of Effective Security Management Brochure PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration impact of effective security management brochure pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
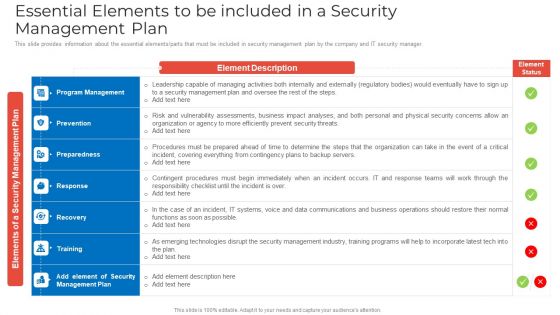
Essential Elements To Be Included In A Security Management Plan Rules PDF
This slide provides information about the essential elements parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan rules pdf bundle. Topics like program management, prevention, preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Current Potential Challenges Faced By Firm Designs PDF
This slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Deliver an awe inspiring pitch with this creative developing firm security strategy plan current potential challenges faced by firm designs pdf bundle. Topics like security, financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

International Organization Standardization 270001 Dashboard For Information Security Risk Management Pictures PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parcent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative international organization standardization 270001 dashboard for information security risk management pictures pdf bundle. Topics like dashboard for information security risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Timeline For The Implementation Of Electronic Information Security Ppt Infographic Template Information PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative cybersecurity timeline for the implementation of electronic information security ppt infographic template information pdf bundle. Topics like security documentation, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Compliance Dashboard Of Electronic Information Security Ppt Outline Graphic Tips PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative cybersecurity compliance dashboard of electronic information security ppt outline graphic tips pdf bundle. Topics like compliance dashboard of electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Essential Elements To Be Included Pictures PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks essential elements to be included pictures pdfc bundle. Topics like program management, preparedness, contingent procedures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Impact Analysis For Effective Threat Management Slides PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative corporate security and risk management impact analysis for effective threat management slides pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Information And Event Management Strategies For Financial Audit And Compliance Companys Enhanced Features Portrait PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance companys enhanced features portrait pdf bundle. Topics like main features, additional features, security monitoring, advanced threat detection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
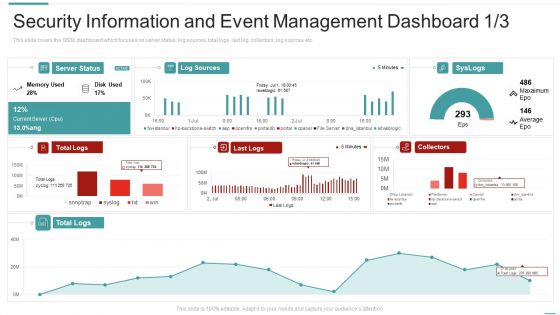
Risk Recognition Automation Security Information And Event Management Dashboard Ppt Model Elements PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard ppt model elements pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
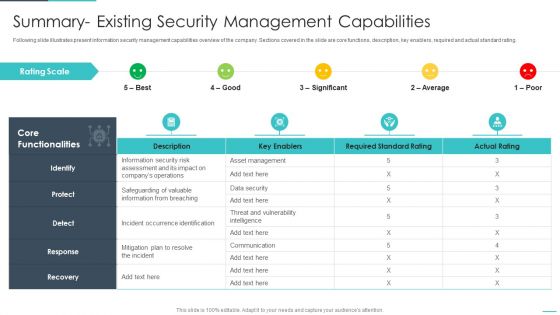
Handling Cyber Threats Digital Era Summary Existing Security Management Capabilities Ppt File Demonstration PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative handling cyber threats digital era summary existing security management capabilities ppt file demonstration pdf bundle. Topics like summary existing security management capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Checklist For Effectively Managing Asset Security Ppt Slides Example File PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative handling cyber threats digital era checklist for effectively managing asset security ppt slides example file pdf bundle. Topics like checklist for effectively managing asset security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing Information Technology Security 30 Days Plan Ppt Professional Examples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 30 days plan ppt professional examples pdf bundle. Topics like managing information technology security 30 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing Information Technology Security 60 Days Ppt Infographic Template Samples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 60 days ppt infographic template samples pdf bundle. Topics like managing information technology security 60 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline For The Implementation Of Information Technology Security Ppt Portfolio Slideshow PDF
This slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of information technology security ppt portfolio slideshow pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Requirement Of Information Technology Security In Different Sectors Ppt Ideas Shapes PDF
This slide depicts the requirement of network security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with requirement of information technology security in different sectors ppt ideas shapes pdf bundle. Topics like requirement of information technology security in different sectors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Impact Analysis For Effective Threat Management In Securing Structure PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative threat management at workplace impact analysis for effective threat management in securing structure pdf bundle. Topics like security incidents, incidents damaging public image, actual access violations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
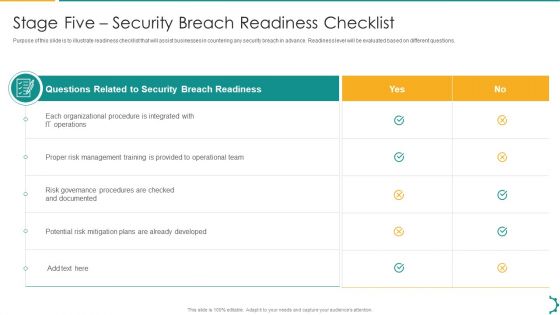
Artificial Intelligence Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Deliver an awe inspiring pitch with this creative artificial intelligence playbook stage five security breach readiness checklist topics pdf bundle. Topics like questions related, security breach readiness, each organizational procedure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
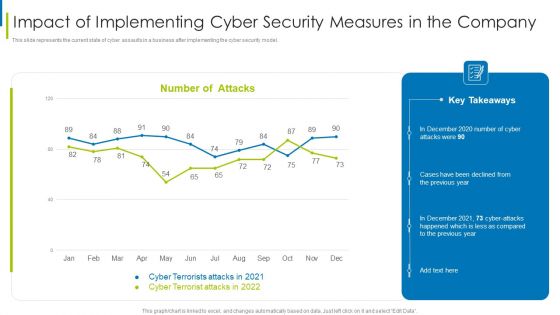
Cyber Terrorism Assault Impact Of Implementing Cyber Security Measures In The Company Professional PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model.Deliver an awe inspiring pitch with this creative cyber terrorism assault impact of implementing cyber security measures in the company professional pdf bundle. Topics like impact of implementing cyber security measures in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
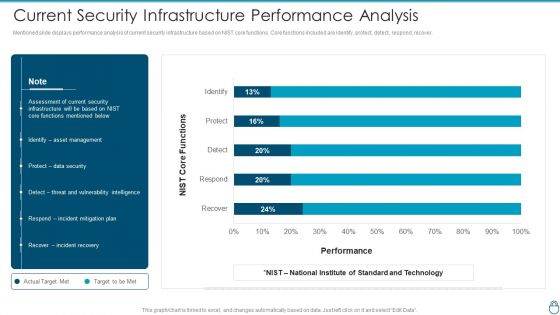
Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF
Mentioned slide displays a five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF bundle. Topics like Assess Security, Gap Analysis, Gap Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
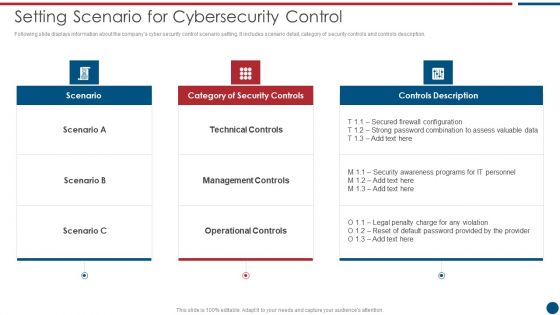
Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
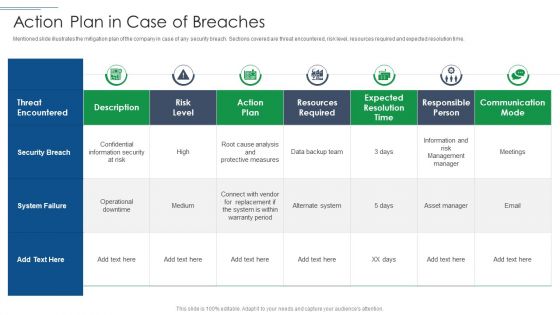
IT Security Risk Management Approach Introduction Action Plan In Case Of Breaches Demonstration PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Action Plan In Case Of Breaches Demonstration PDF bundle. Topics like Security Breach, System Failure, Risk Level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

What Are The Benefits Of A Cloud Security System Background PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. Deliver an awe inspiring pitch with this creative What Are The Benefits Of A Cloud Security System Background PDF bundle. Topics like Openness, Efficient Recovery, No Hardware Required can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
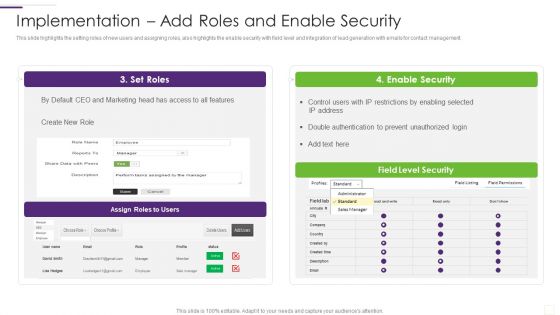
CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF bundle. Topics like Enable Security, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk.Deliver an awe inspiring pitch with this creative Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF bundle. Topics like Administrative Permissions, Empty Security, Computer Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
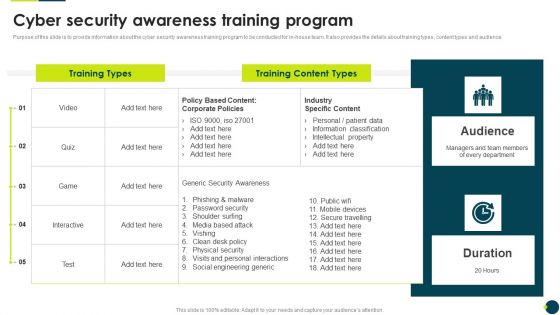
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
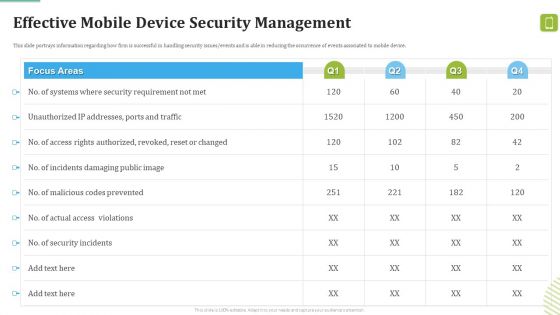
MDM Strategies At Office Effective Mobile Device Security Management Ideas PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Effective Mobile Device Security Management Ideas PDF bundle. Topics like Incidents Damaging, Security Incidents, Malicious Codes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
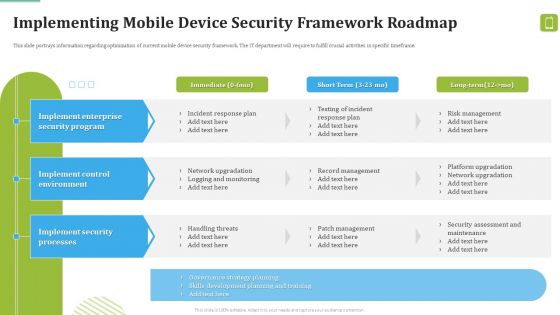
MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF bundle. Topics like Security, Employees Rules And Regulations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112
We present our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because,You too have got the framework of your companys growth in place. Use our Success PowerPoint Templates because, You can Transmit this concern to your staff using our helpful slides. Use our Puzzles or jigsaws PowerPoint Templates because,We all know that alphabetical order is a time honoured concept. Use our Shapes PowerPoint Templates because,you can put it up there for all to see. Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Key chain tied with puzzle piece, business, success, puzzles or jigsaws, shapes, marketing. The prominent colors used in the PowerPoint template are Yellow, Black, Red

Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Slidegeeks is here to make your presentations a breeze with Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V
This slide represents the case study of Hyundai Venue Take On The City Campaign in order to provide understanding of real life use of venue marketing. It includes details related to challenges, strategy implemented and results of Hyundai venue Take on the city campaign. Present like a pro with Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
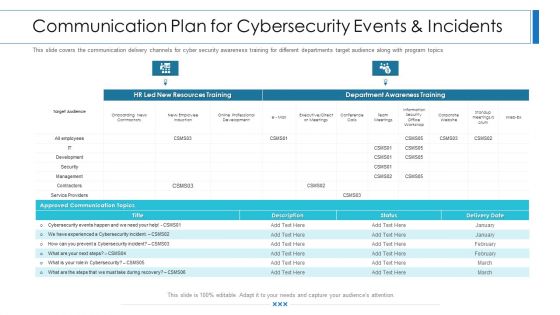
Workforce Security Realization Coaching Plan Communication Plan For Cybersecurity Events And Incidents Graphics PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan communication plan for cybersecurity events and incidents graphics pdf bundle. Topics like resources training, department awareness training, approved communication topics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workforce Security Realization Coaching Plan Organization Impact Metrics Behaviours Infographics PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization impact metrics behaviours infographics pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Automated Security Awareness Platform And Cost Slides PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative data breach prevention recognition automated security awareness platform and cost slides pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effect After Implementing Cyber Risk Security Awareness Program Ppt Layouts Visuals PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Deliver an awe-inspiring pitch with this creative effect after implementing cyber risk security awareness program ppt layouts visuals pdf bundle. Topics like mobile, sales department, accounts department, financial, computer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Security Awareness Staff Learning Organization Impact Metrics Behaviours Portrait PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning organization impact metrics behaviours portrait pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Contingency Plan For Threat Handling Clipart PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative information and technology security operations contingency plan for threat handling clipart pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Impact Of Successful Implementation Of Secops System Slides PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Deliver an awe inspiring pitch with this creative security functioning centre impact of successful implementation of secops system slides pdf bundle. Topics like security analyst productivity, threat, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
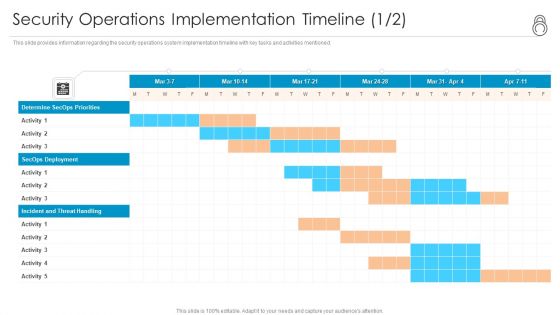
Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Activity Template PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration security operations implementation timeline activity template pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Contingency Plan For Threat Handling Template PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative security and process integration contingency plan for threat handling template pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
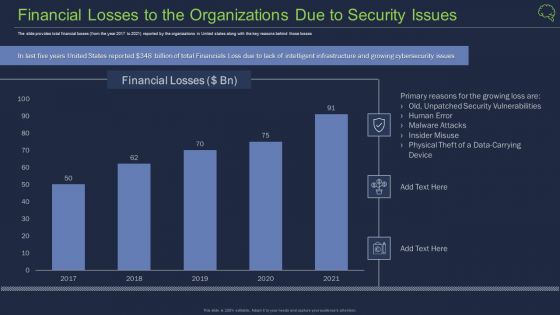
Financial Losses To The Organizations Due To Security Issues Ppt Background PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues ppt background pdf bundle. Topics like financial losses to the organizations due to security issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Environments Best Suited For Efficient And Secure Supply Chains Ppt Show Example PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains ppt show example pdf bundle. Topics like efficient supply chains, operations strategy, inventory investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Environments Best Suited For Efficient And Secure Supply Chains Topics PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe-inspiring pitch with this creative environments best suited for efficient and secure supply chains topics pdf bundle. Topics like factor, efficient supply chains, responsible supply chains can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Requirement Of IT Security IT In Different Sectors Ppt Inspiration Deck PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative requirement of it security it in different sectors ppt inspiration deck pdf bundle. Topics like corporate, financial, organizations, process, computers, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Environments Best Suited For Efficient And Secure Supply Chains Template PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains template pdf bundle. Topics like inventory investment, strategy, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
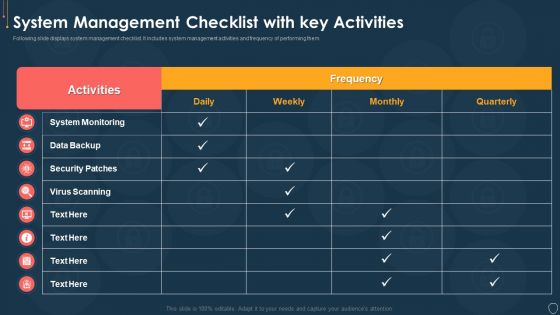
Cyber Security Risk Management Plan System Management Checklist With Key Activities Structure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative cyber security risk management plan system management checklist with key activities structure pdf bundle. Topics like system monitoring, data backup, security patches, virus scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Using System Categorization Sheet For Asset Identification Template PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information. Deliver an awe inspiring pitch with this creative cyber security risk management plan using system categorization sheet for asset identification template pdf bundle. Topics like location, accessibility, organization, access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
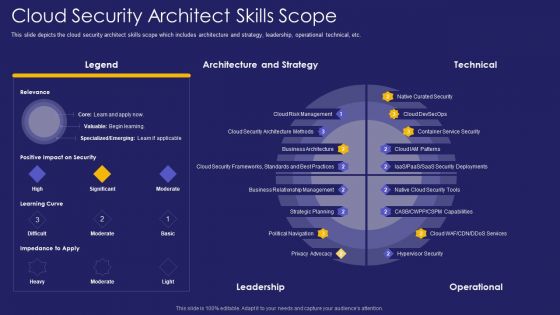
Role IT Team Digital Transformation Cloud Security Architect Skills Scope Rules PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative role it team digital transformation cloud security architect skills scope rules pdf bundle. Topics like architecture, strategy, leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Shift Capital Fundraising Pitch Deck Details About Shifts Secure Storage Facility Formats PDF
This slide provides information about the storage facility at Shift and some details regarding the hub. Deliver an awe inspiring pitch with this creative shift capital fundraising pitch deck details about shifts secure storage facility formats pdf bundle. Topics like our secure storage facility, the hub can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
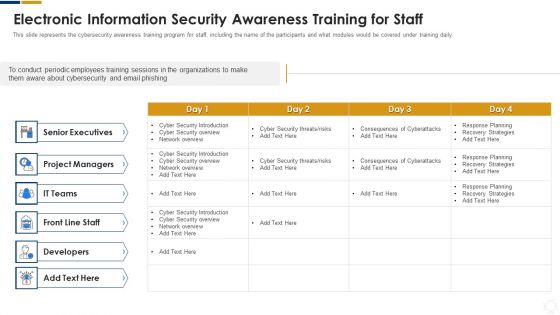
Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
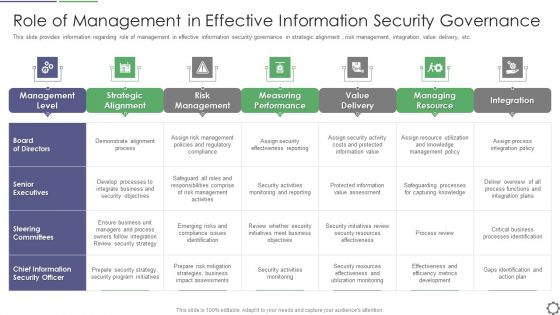
Role Of Management In Effective Information Security Governance Ppt PowerPoint Presentation File Rules PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative role of management in effective information security governance ppt powerpoint presentation file rules pdf bundle. Topics like management level, strategic alignment, risk management, measuring performance, value delivery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Introducing Information Security Risk Designs PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an awe inspiring pitch with this creative effective it risk management process information security risk assessment formats pdf bundle. Topics like system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
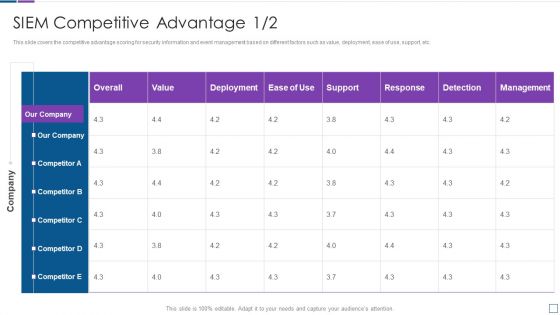
Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
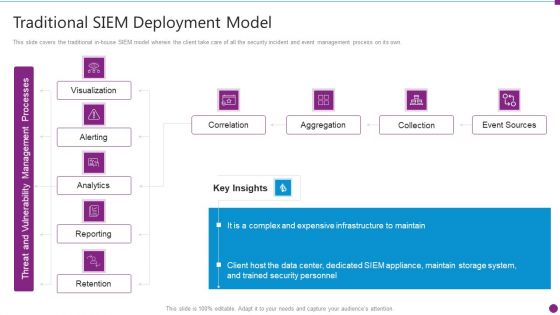
Security Information And Event Management Strategies For Financial Audit And Compliance Traditional SIEM Deployment Guidelines PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance traditional siem deployment guidelines pdf bundle. Topics like correlation, aggregation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Recognition Automation Security Information And Event Management Dashboard Activity Ppt Styles Influencers PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard activity ppt styles influencers pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
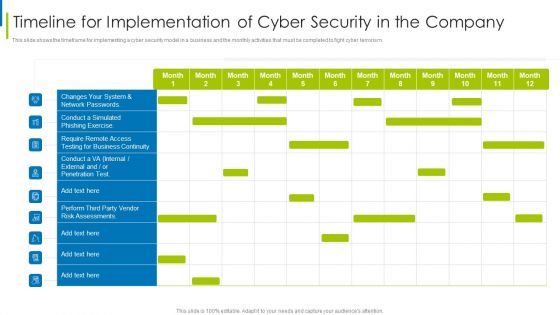
Cyber Terrorism Assault Timeline For Implementation Of Cyber Security In The Company Sample PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism.Deliver an awe inspiring pitch with this creative cyber terrorism assault timeline for implementation of cyber security in the company sample pdf bundle. Topics like require remote access, testing for business continuity, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF bundle. Topics like System Monitoring, Data Backup, Security Patches, Virus Scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc.Deliver an awe inspiring pitch with this creative Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF bundle. Topics like Architecture And Strategy, Technical, Leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
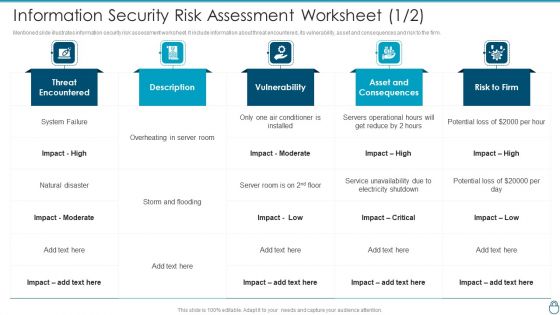
Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF bundle. Topics like Minimum Contract Period, Activation Fee Hidden, Customer Retention Mobile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
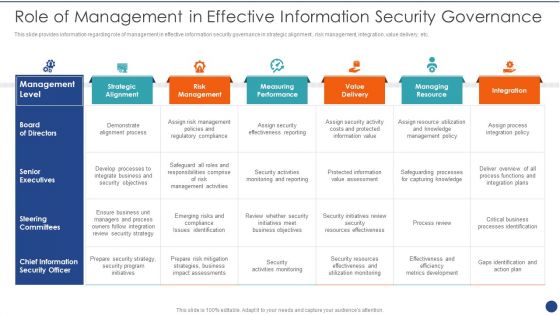
Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Management Level, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF bundle. Topics like Risk Heat, Action Plan, Risk Rating Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF bundle. Topics like Risk Management, Measuring Performance, Managing Resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
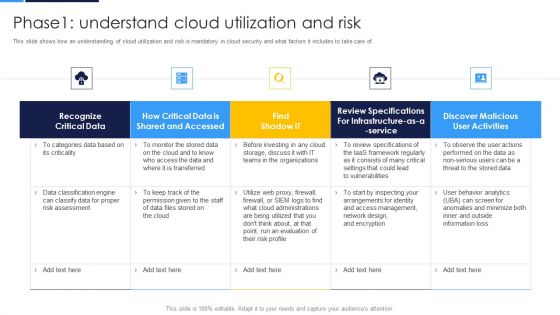
Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF bundle. Topics like Shared And Accessed, Risk Assessment, Review Specifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF bundle. Topics like Restrictions By Enabling, Prevent Unauthorized, Double Authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
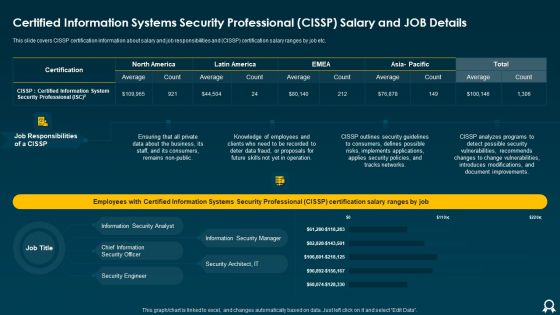
Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF bundle. Topics like Average, Tracks Networks, Applies Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
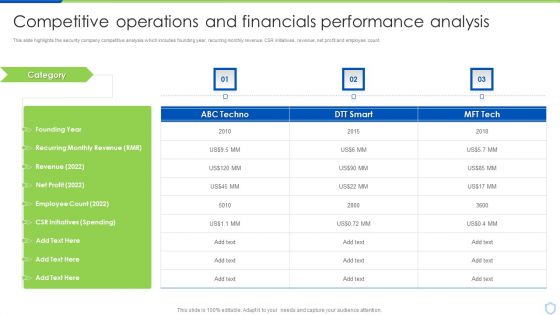
Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF bundle. Topics like Employee Count, Recurring Revenue, Spending can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
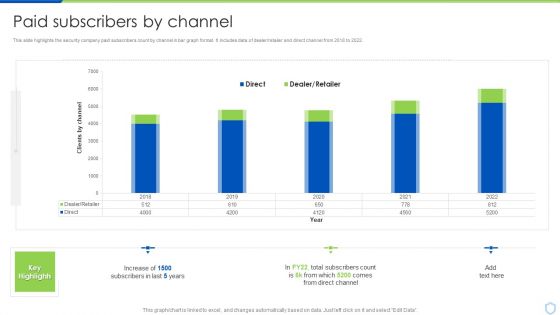
Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF bundle. Topics like Direct Channel, Subscribers In Last, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home