Safety Performance

Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
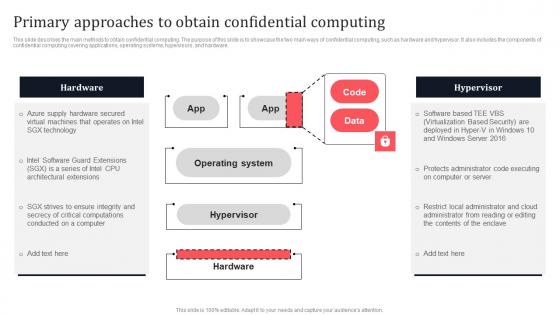
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
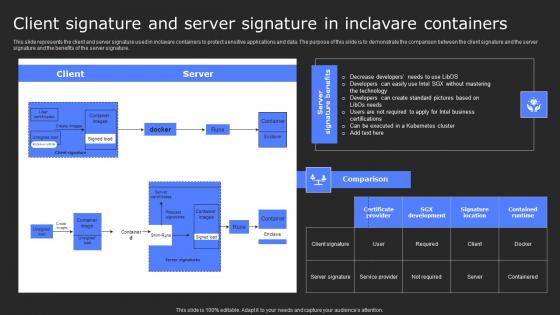
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Infographics PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks current security monitoring infographics pdf bundle. Topics like monitoring, service, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
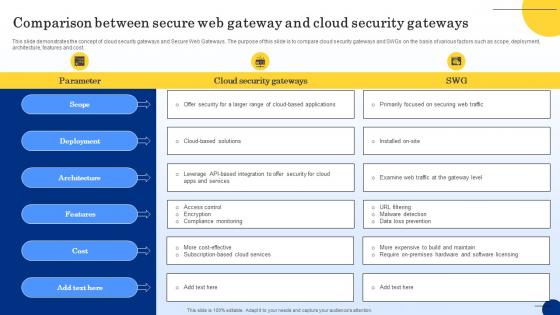
Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
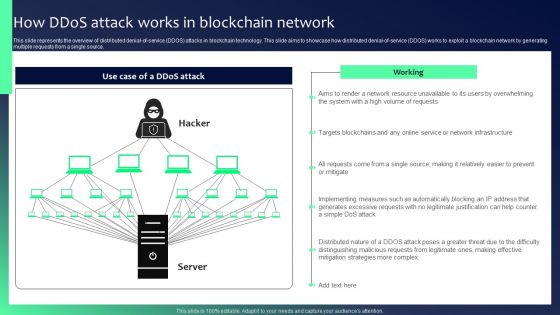
Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
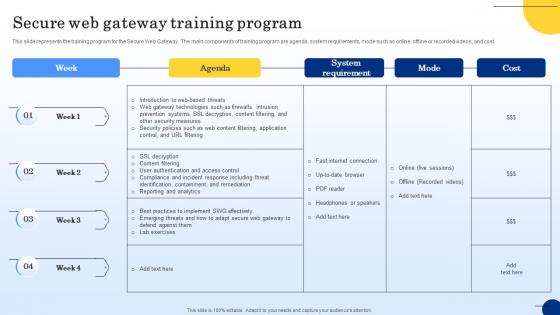
Secure Web Gateway Training Program Web Threat Protection System
This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Secure Web Gateway Training Program Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
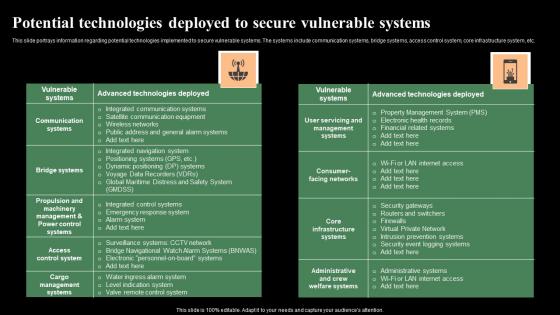
Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
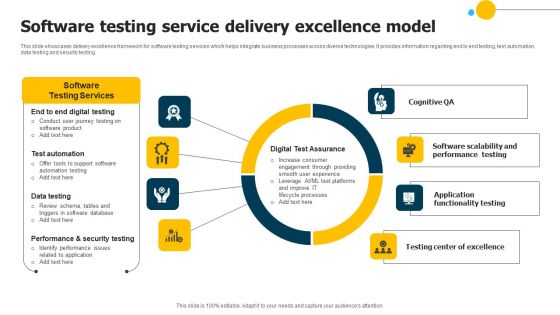
Software Testing Service Delivery Excellence Model Mockup PDF
This slide showcases delivery excellence framework for software testing services which helps integrate business processes across diverse technologies. It provides information regarding end to end testing, test automation, data testing and security testing. Showcasing this set of slides titled Software Testing Service Delivery Excellence Model Mockup PDF. The topics addressed in these templates are Performance Testing, Digital Test Assurance, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Management Strategic Model Inspiration PDF
The following slide showcases a framework presenting strategy development and implementation phase in information security governance. It includes key components such as organizational structure, value delivery, strategic alignment, resource optimization, performance measurement, etc. Presenting Information Security Management Strategic Model Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Value Delivery, Key Insights, Organizational Structure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Service Desk Incident Management Framework Digitalization Of Service Desk Administration Ppt File Design Inspiration PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Service Desk Incident Management Framework Digitalization Of Service Desk Administration Ppt File Design Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
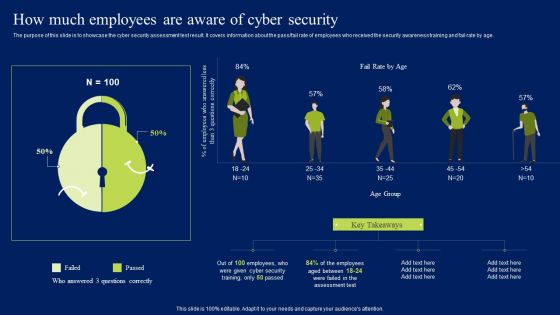
How Much Employees Are Aware Of Cyber Security Ppt Ideas Portrait PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. How Much Employees Are Aware Of Cyber Security Ppt Ideas Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Workforce Security Realization Coaching Plan Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a workforce security realization coaching plan security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
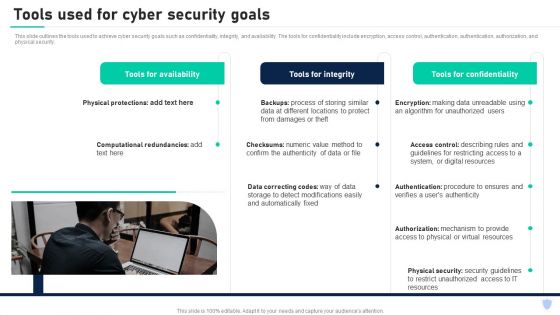
Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
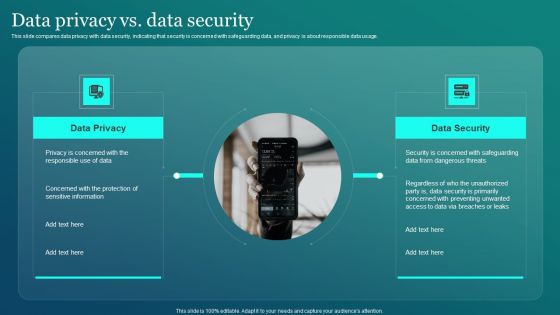
Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Data Privacy Vs Data Security Ppt PowerPoint Presentation File Infographic Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
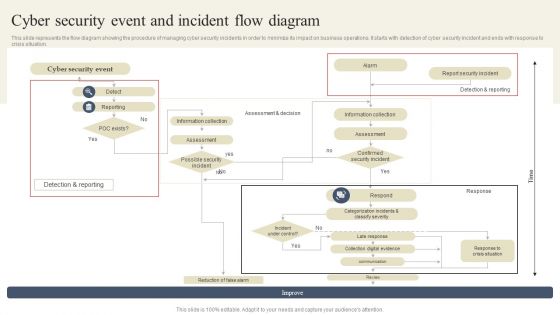
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
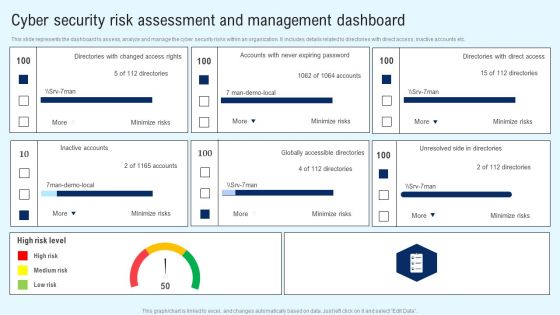
Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Cyber Security Risk Assessment And Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Architecture Of Google Cloud Service Platform Professional PDF
This slide showcases google cloud platform service architecture. This further includes operational excellence, security, privacy, and compliance, reliability, cost optimization and performance optimization. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Architecture Of Google Cloud Service Platform Professional PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Building Trust With IoT Security IoT Based Edge Computing Three Layer Architecture IoT SS V
This slide showcases edge computing architecture that helps in improving performance and reduce latency through real time data processing. It includes three layers such as cloud layer, edge layer, and device layer. Welcome to our selection of the Building Trust With IoT Security IoT Based Edge Computing Three Layer Architecture IoT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
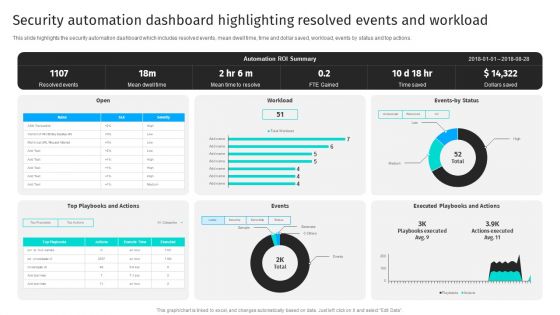
Security Automation Dashboard Highlighting Resolved Events And Workload Portrait PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security Automation Dashboard Highlighting Resolved Events And Workload Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
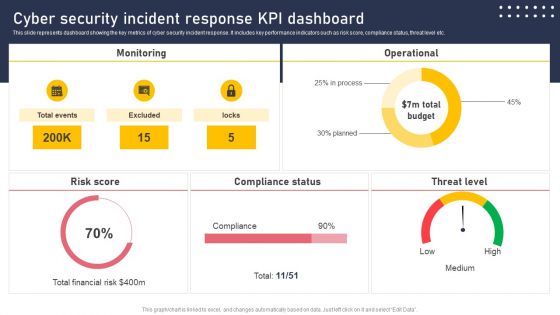
Cyber Security Incident Response KPI Dashboard Microsoft PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Slidegeeks has constructed Cyber Security Incident Response KPI Dashboard Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
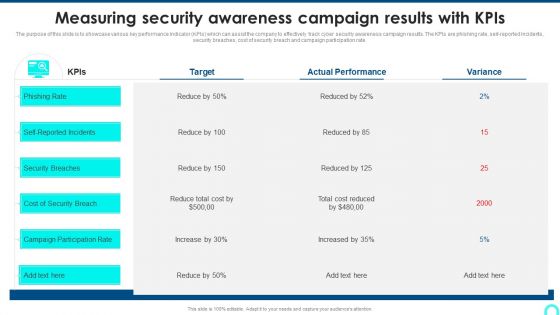
Measuring Security Awareness Campaign Results With Kpis Template PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self reported incidents, security breaches, cost of security breach and campaign participation rateDeliver an awe inspiring pitch with this creative Measuring Security Awareness Campaign Results With Kpis Template PDF bundle. Topics like Security Breaches, Cost Of Security, Campaign Participation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Common Pitfalls For Adopting SOA Architecture Ppt PowerPoint Presentation Gallery Format Ideas PDF
This slide illustrates commonly occurred pitfalls in Service Oriented Architecture SOA. It includes building SOA as traditional architectures, not planning for transition, etc. Persuade your audience using this Common Pitfalls For Adopting SOA Architecture Ppt PowerPoint Presentation Gallery Format Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Not Standardizing SOA, Not Accounting, SOA Performance Requirements, SOA Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Data Breach Prevention Recognition Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a data breach prevention recognition security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Staff Learning Security Awareness Tracking Kpis Demonstration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a organizational network staff learning security awareness tracking kpis demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.
Cyber Security Threat Dashboard With KPI Metrics Icons PDF
This slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Showcasing this set of slides titled Cyber Security Threat Dashboard With KPI Metrics Icons PDF. The topics addressed in these templates are Cyber Security Threat Dashboard, Kpi Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Running Cyber Security Awareness Campaign For Employees Background PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Running Cyber Security Awareness Campaign For Employees Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Securing Operations Of Logistics Through Integrated Iot Structure PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Securing Operations Of Logistics Through Integrated Iot Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF
This slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Security Track Record Of Our Company Themes PDF
This slide highlights our past track record as a data privacy provider company and outlines that we promise 100 percent client satisfaction. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Track Record Of Our Company Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
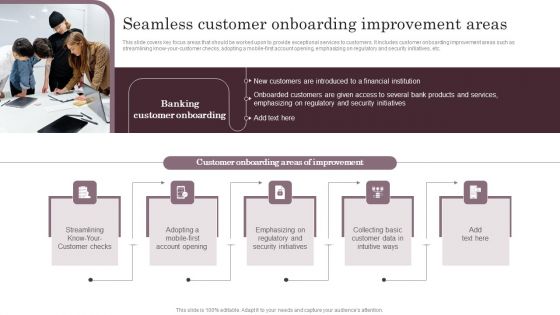
Omnichannel Services Solution In Financial Sector Seamless Customer Onboarding Graphics PDF
This slide covers key focus areas that should be worked upon to provide exceptional services to customers. It includes customer onboarding improvement areas such as streamlining know-your-customer checks, adopting a mobile-first account opening, emphasizing on regulatory and security initiatives, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Omnichannel Services Solution In Financial Sector Seamless Customer Onboarding Graphics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Devops Deployment And Transformation Services Advisory Solution For System Operations As A People Problem Professional PDF
This slide covers the solution of the problems faced by the clients such as monitoring, containers, metrics, analytics, logs, performance security etc. Elevate your presentations with our intuitive Devops Deployment And Transformation Services Advisory Solution For System Operations As A People Problem Professional PDF template. Whether youre delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percenteditable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression.
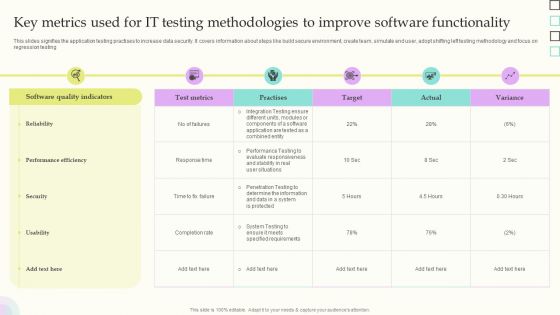
Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF
This slides signifies the application testing practises to increase data security. It covers information about steps like build secure environment, create team, simulate end user, adopt shifting left testing methodology and focus on regression testing. Showcasing this set of slides titled Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF. The topics addressed in these templates are Software Quality Indicators, Reliability, Performance Efficiency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring Security Awareness Campaign Icons PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring Security Awareness Campaign Icons PDF from Slidegeeks and deliver a wonderful presentation.
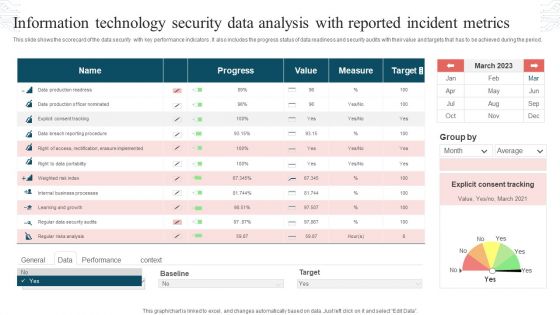
Information Technology Security Data Analysis With Reported Incident Metrics Rules PDF
This slide shows the scorecard of the data security with key performance indicators. It also includes the progress status of data readiness and security audits with their value and targets that has to be achieved during the period. Pitch your topic with ease and precision using this Information Technology Security Data Analysis With Reported Incident Metrics Rules PDF. This layout presents information on Progress, Value, Measure, Target. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF
The following slide showcases best practices to secure IOT gateway that are device establishment, establishing strong identity and provide identity to ecosystem. Presenting Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Performance Metrics For Project Management Office, Requirement Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
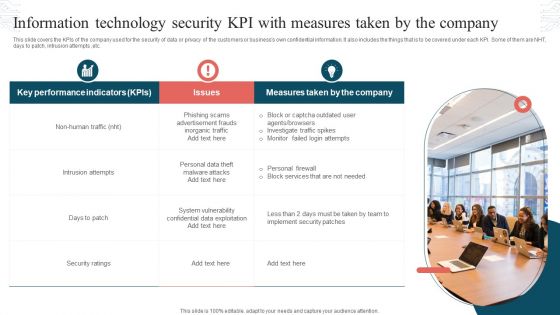
Information Technology Security KPI With Measures Taken By The Company Formats PDF
This slide covers the KPIs of the company used for the security of data or privacy of the customers or businesss own confidential information. It also includes the things that is to be covered under each KPI. Some of them are NHT, days to patch, intrusion attempts ,etc. Presenting Information Technology Security KPI With Measures Taken By The Company Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Key Performance Indicators, Measures Taken, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Web Gateway SWG Importance For Businesses Ppt Professional Graphics PDF
This slide outlines the importance of secure web gateways to businesses. The purpose of this slide is to demonstrate the need for SWGs for companies to protect their critical data and applications from malicious activities and actors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Secure Web Gateway SWG Importance For Businesses Ppt Professional Graphics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational
This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Several Financial Scenarios And Signs Posing As Threat Pictures PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting corporate security and risk management addressing several financial scenarios and signs posing as threat pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like profitability, liquidity, employees, financial performance . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Evaluating Financial Practices In Firm Graphics PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. This is a corporate security and risk management evaluating financial practices in firm graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluating financial practices in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

KYC Transaction Monitoring System For Business Security Ppt PowerPoint Presentation Complete Deck With Slides
Incorporate this KYC Transaction Monitoring System For Business Security Ppt PowerPoint Presentation Complete Deck With Slides to define the objectives of business performance and how to drive results. List goals and outline a plan to achieve all your enterprise targets using this well crafted complete deck in seventy slides. Walk your audience through the key objectives of your business set-up, especially for customers and inspire them to work with diligence using this predesigned presentation template. Download now with the added assurance of a 100 percent customizable and editable product.
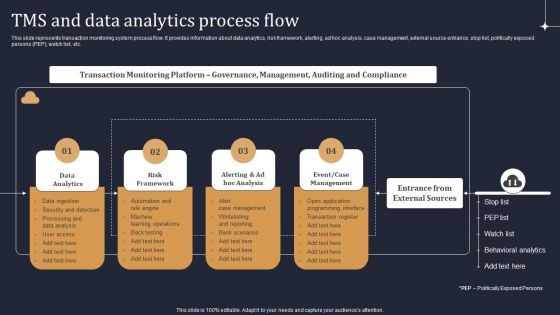
KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF
The following slide represents training program for transaction monitoring and anti money laundering AML. It provides information about certification, assessment, compatibility, surveillance, operational efficiency, escalation, unusual transactions, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
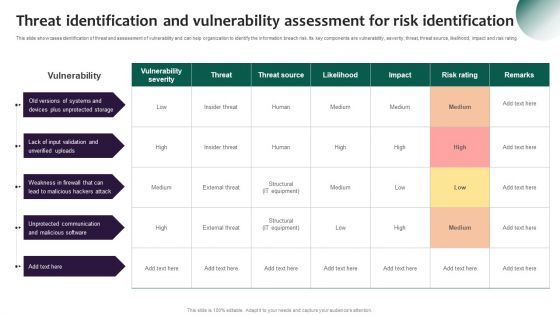
Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Select Tools To Reduce Cyber Security Failure Ppt PowerPoint Presentation File Show PDF
The following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Select Tools To Reduce Cyber Security Failure Ppt PowerPoint Presentation File Show PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
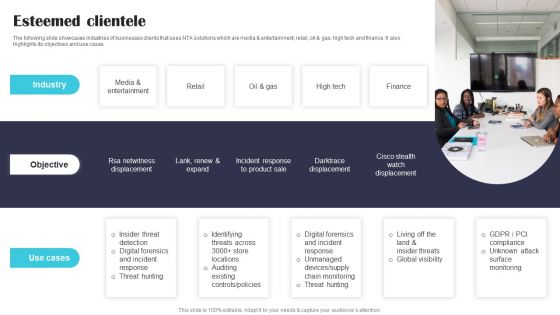
Security Software Company Investor Funding Pitch Deck Esteemed Clientele Themes PDF
The following slide showcases industries of businesses clients that uses NTA solutions which are media and entertainment, retail, oil and gas, high tech and finance. It also highlights its objectives and use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Security Software Company Investor Funding Pitch Deck Esteemed Clientele Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
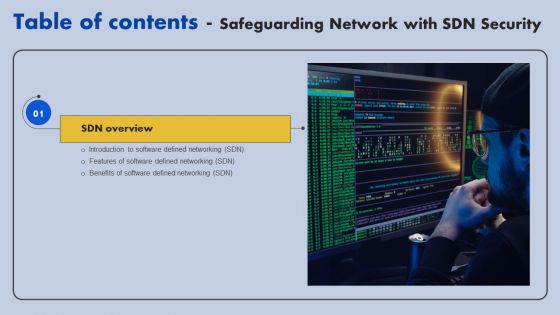
Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Series Of Cyber Security Attacks Against Ukraine 2022 Does Ukraine And Russia Cyber Warfare Kill People Guidelines PDF
This slide describes if ukraine and russia cyber warfare is killing people and german cybersecurity expert matthias schulze said people have died due to misinformation efforts in earlier conflicts. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Does Ukraine And Russia Cyber Warfare Kill People Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
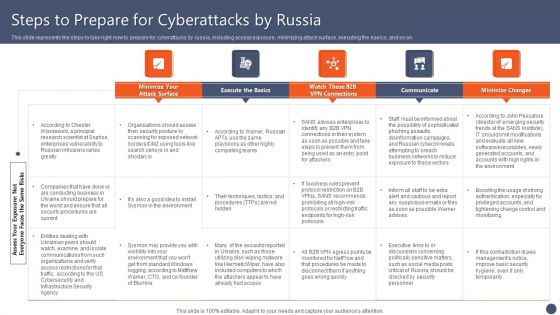
Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Pros And Cons Of Private Blockchain Different Architectures Of Blockchain Inspiration Pdf
This slide represents the Pros and Cons of the private blockchain framework based on factors such as speed, flexibility, trust building, and security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Pros And Cons Of Private Blockchain Different Architectures Of Blockchain Inspiration Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Cloud Computing Icon For Data Storage Demonstration PDF
This slide contains challenges that reduces efficiency of cloud computing services. It includes five points security, cost management, control expertise, performance challenges and network dependency.Persuade your audience using this Cloud Computing Icon For Data Storage Demonstration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Computing Icon, Data Storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Value Proposition For Business Owners Ringcaptcha Capital Funding Pitch Deck Infographics PDF
This slide mentions various benefits owners can gain from using security services offered. Key benefits include competitor analysis, reduced accidental signups, verified comments and checking into accounts. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Value Proposition For Business Owners Ringcaptcha Capital Funding Pitch Deck Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
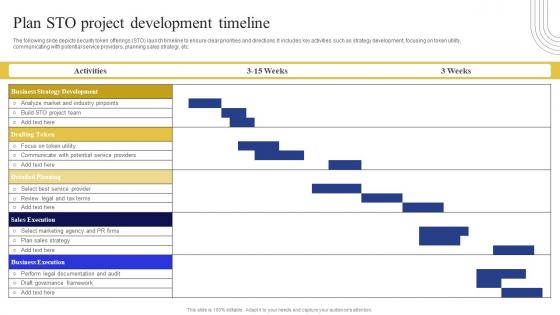
Plan Sto Project Development Timeline Exploring Investment Opportunities Themes Pdf
The following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Plan Sto Project Development Timeline Exploring Investment Opportunities Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

QA Modification For Product Quality Development And Consumer Satisfaction Implement Code Quality Brochure PDF
This slide shows the details about Code Quality Measurements Approach for Effective QA Transformation along with details on Software Quality Indicators and Test Metrics such as Reliability, Security, Testability, Rate of Delivery etc. Presenting qa modification for product quality development and consumer satisfaction implement code quality brochure pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like reliability, performance efficiency, security, maintainability, rate of delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Successful Quality Assurance Transition Techniques To Enhance Product Quality Implement Code Quality Measurements Formats PDF
This slide shows the details about Code Quality Measurements Approach for Effective QA Transformation along with details on Software Quality Indicators and Test Metrics such as Reliability, Security, Testability, Rate of Delivery etc. This is a successful quality assurance transition techniques to enhance product quality implement code quality measurements formats pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reliability, performance efficiency, security, maintainability, rate of delivery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
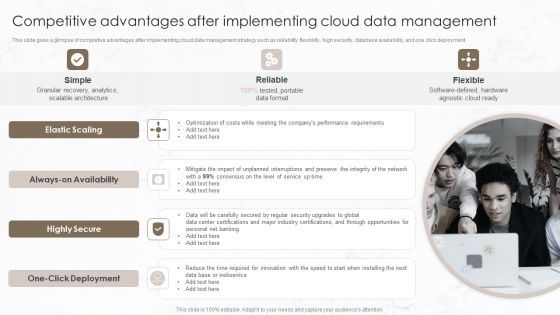
Competitive Advantages After Implementing Cloud Data Management Pictures PDF
This slide gives a glimpse of completive advantages after implementing cloud data management strategy such as reliability, flexibility, high security, database availability, and one click deployment. This is a Competitive Advantages After Implementing Cloud Data Management Pictures PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Elastic Scaling, Highly Secure, Performance Requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management For Improving IT Operations Ensuring Checklist For Mobile Sample PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Mobile Device Management For Improving IT Operations Ensuring Checklist For Mobile Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Multiple IOT Technology Usage Areas Sample PDF
The following slide provides the multiple usage areas of IoT technology that helps to understand the applicability of IoT technology for performance management. Major areas of development are manufacturing, healthcare, retail, security, and transportation. Presenting Multiple IOT Technology Usage Areas Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Health Care, Retail, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
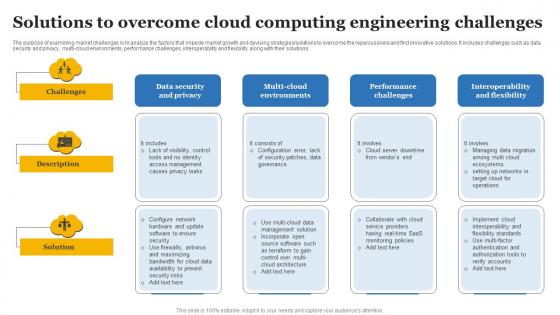
Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf
The purpose of examining market challenges is to analyze the factors that impede market growth and devising strategies solutions to overcome the repercussions and find innovative solutions. It includes challenges such as data security and privacy, multi-cloud environments, performance challenges, interoperability and flexibility along with their solutions. Pitch your topic with ease and precision using this Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf This layout presents information on Data Security And Privacy, Multi Cloud Environments It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Zero Trust Model Case Study Intellectual Property Protection
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Case Study Intellectual Property Protection will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing
The purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
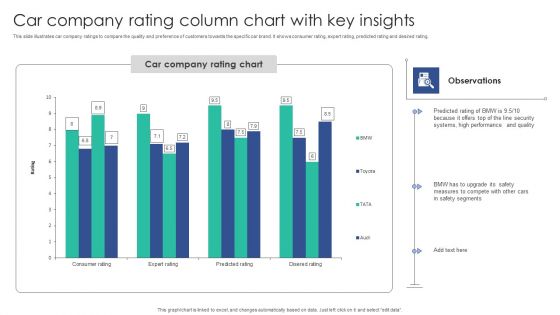
Car Company Rating Column Chart With Key Insights Structure PDF
This slide illustrates car company ratings to compare the quality and preference of customers towards the specific car brand. It shows consumer rating, expert rating, predicted rating and desired rating.Showcasing this set of slides titled Car Company Rating Column Chart With Key Insights Structure PDF. The topics addressed in these templates are Performance Quality, Top Security, Predicted Rating. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF
This slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti-phishing, data discovery, and packet-level visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Technology Functions Management Table Of Content Ppt Model Files PDF
This is a information technology functions management table of content ppt model files pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to infrastructure, asset management process, inventory and condition assessment, deterioration modeling, optimization and decision making, performance and cost functions, interdependence, resiliency and security, contract and workflow management, commissioning new facilities, capital budgeting, metrics and dashboard. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manufacturing Operation Quality Improvement Practices Tools Templates Key Risks Category In Supplier Elements PDF
Purpose of the following slide is to displays the key risk in supplier relationship management as it highlights the identify value, capture value, secure value etc. This is a manufacturing operation quality improvement practices tools templates key risks category in supplier elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like srm, performance management, contract management, risk management, strategic sourcing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Function Of Quality Assurance In Devops IT Impact Of Effective Testing And Quality Management Of Devops System Formats PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. This is a function of quality assurance in devops it impact of effective testing and quality management of devops system formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merging of teams, performance and quality metrics, development collaboration You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
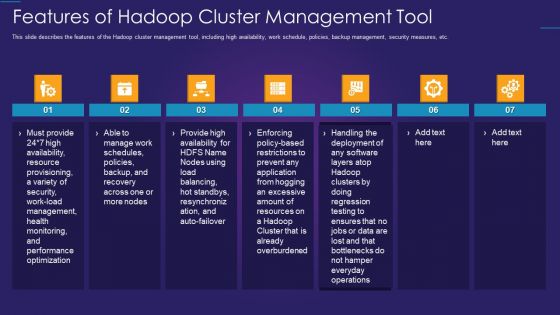
Apache Hadoop IT Features Of Hadoop Cluster Management Tool Sample PDF
This slide describes the features of the Hadoop cluster management tool, including high availability, work schedule, policies, backup management, security measures, etc.Presenting apache hadoop it features of hadoop cluster management tool sample pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like resource provisioning, performance optimization, provide high availability In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deliver Efficiency Innovation Challenges Associated With User Experience Team Themes PDF
This slide represents metrics used to measure product team performance that covers product stickiness and usage, feature adoption and retention, net promoter score, product delivery predictability, etc. Deliver an awe inspiring pitch with this creative Deliver Efficiency Innovation Challenges Associated With User Experience Team Themes PDF bundle. Topics like Product Development Procedure, Value Achieving Objectives, Securing Resources And Budget, Experience And Research Value can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Deploying Quality Assurance QA Transformation Implement Code Quality Measurements Guidelines PDF
This slide shows the details about Code Quality Measurements Approach for Effective QA Transformation along with details on Software Quality Indicators and Test Metrics such as Reliability, Security, Testability, Rate of Delivery etc.This is a Deploying Quality Assurance QA Transformation Implement Code Quality Measurements Guidelines PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Performance Efficiency, Maintainability, Reliability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
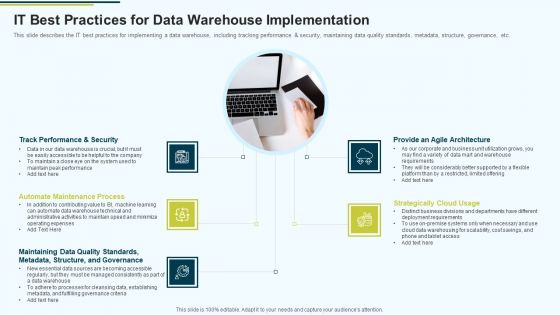
MIS IT Best Practices For Data Warehouse Implementation Ppt PowerPoint Presentation Pictures Infographics PDF
This slide describes the IT best practices for implementing a data warehouse, including tracking performance and security, maintaining data quality standards, metadata, structure, governance, etc.Presenting MIS IT Best Practices For Data Warehouse Implementation Ppt PowerPoint Presentation Pictures Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Provide An Agile Architecture, Strategically Cloud Usage, Maintaining Data Quality In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Warehouse Implementation IT Best Practices For Data Warehouse Implementation Elements PDF
This slide describes the IT best practices for implementing a data warehouse, including tracking performance security, maintaining data quality standards, metadata, structure, governance, etc.This is a Data Warehouse Implementation IT Best Practices For Data Warehouse Implementation Elements PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automate Maintenance, Metadata Structure, Agile Architecture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Apache Hadoop Software Deployment Features Of Hadoop Cluster Management Tool Elements PDF
This slide describes the features of the Hadoop cluster management tool, including high availability, work schedule, policies, backup management, security measures, etc.Presenting Apache Hadoop Software Deployment Features Of Hadoop Cluster Management Tool Elements PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Resource Provisioning, Health Monitoring, Performance Optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
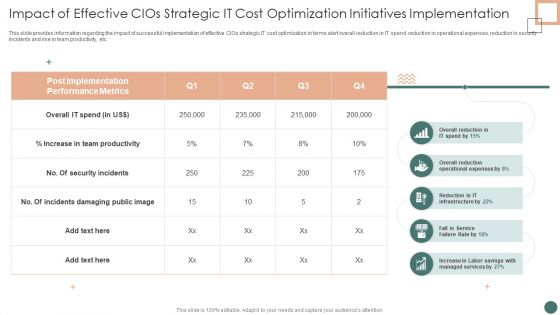
Improved Digital Expenditure Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Ideas PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. Deliver an awe inspiring pitch with this creative Improved Digital Expenditure Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Ideas PDF bundle. Topics like Post Implementation, Performance Metrics, Incidents Damaging can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Supply Chain Management Analyzing Impact Of Blockchain Iot On Major Kpis Inspiration PDF
This slide showcases impact analysis of blockchain internet of things IoT on key performance indicators KPIs. It provides information about efficiency, security, risk, costs, business models, revenue resources, etc. Deliver an awe inspiring pitch with this creative Supply Chain Management Analyzing Impact Of Blockchain Iot On Major Kpis Inspiration PDF bundle. Topics like Managements Feedback, Post IoT Implementation, Opportunities For New can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Demonstration PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. Deliver and pitch your topic in the best possible manner with this Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Demonstration PDF. Use them to share invaluable insights on Performance Metrics, Post Implementation, Team Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Event Streaming Technology And Platform Comparative Assessment Table Portrait PDF
The purpose of this slide is to highlight technology comparison that can support firm event-driven architecture. Comparison is made on the basis of hybrid cloud, multi-cloud, dedicated VPC, IoT, open standards, high performance etc. Showcasing this set of slides titled Event Streaming Technology And Platform Comparative Assessment Table Portrait PDF. The topics addressed in these templates are Hybrid Cloud, Dedicated VPC, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
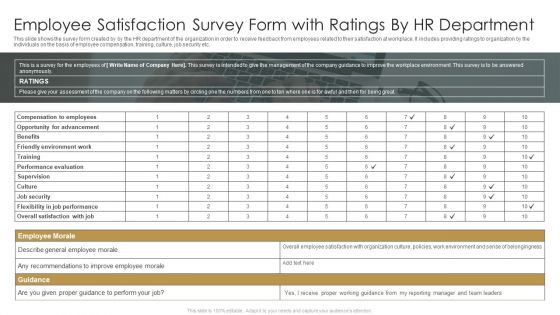
Employee Satisfaction Survey Form With Ratings By HR Department Ppt Infographic Template Topics PDF
This slide shows the survey form created by by the HR department of the organization in order to receive feedback from employees related to their satisfaction at workplace. It includes providing ratings to organization by the individuals on the basis of employee compensation, training, culture, job security etc. Pitch your topic with ease and precision using this Employee Satisfaction Survey Form With Ratings By HR Department Ppt Infographic Template Topics PDF. This layout presents information on Compensation To Employees, Opportunity For Advancement, Performance Evaluation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
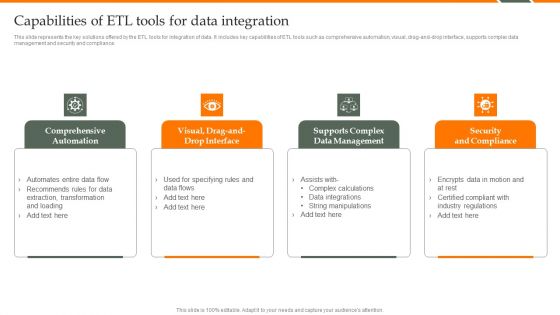
Human Resource Analytics Capabilities Of ETL Tools For Data Integration Microsoft PDF
This slide represents the key solutions offered by the ETL tools for integration of data. It includes key capabilities of ETL tools such as comprehensive automation, visual, drag-and-drop interface, supports complex data management and security and compliance. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Human Resource Analytics Capabilities Of ETL Tools For Data Integration Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Guide To Mergers And Acquisitions Information Technology Due Diligence Checklist Template PDF
Mentioned slide showcases due diligence checklist to measure IT infrastructure health of the target company. Here the health is monitored based on infrastructure availability, telecom system, data analytics, security and compliance. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Guide To Mergers And Acquisitions Information Technology Due Diligence Checklist Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Digital Twin Tech IT Checklist To Implement Digital Twin Technology Summary PDF
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Digital Twin Tech IT Checklist To Implement Digital Twin Technology Summary PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
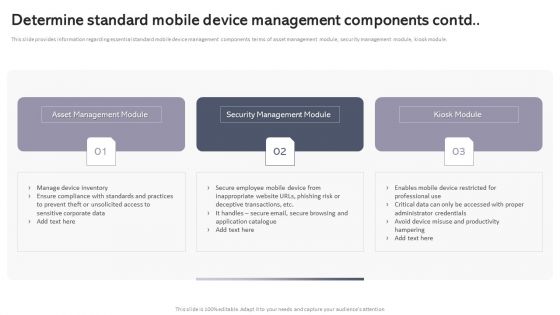
Workplace Portable Device Monitoring And Administration Determine Standard Mobile Device Management Components Contd Mockup PDF
This slide provides information regarding essential standard mobile device management components terms of asset management module, security management module, kiosk module. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Workplace Portable Device Monitoring And Administration Determine Standard Mobile Device Management Components Contd Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Website Audit To Increase Conversion Rate Different Areas Of Website SEO Audit Demonstration PDF
This slide highlights the areas of website audit which includes security audit, performance audit, code audit, website theme audit, UX or UI audit and website architecture audit. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Website Audit To Increase Conversion Rate Different Areas Of Website SEO Audit Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
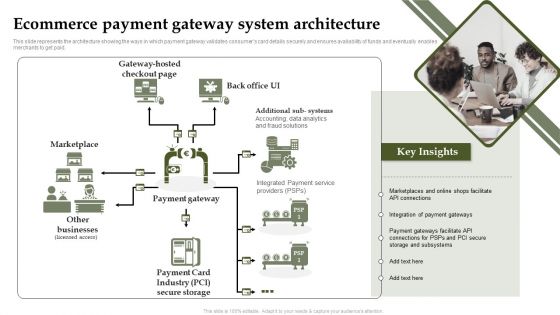
Analyzing And Deploying Effective CMS Ecommerce Payment Gateway System Architecture Background PDF
This slide represents the architecture showing the ways in which payment gateway validates consumers card details securely and ensures availability of funds and eventually enables merchants to get paid. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Analyzing And Deploying Effective CMS Ecommerce Payment Gateway System Architecture Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
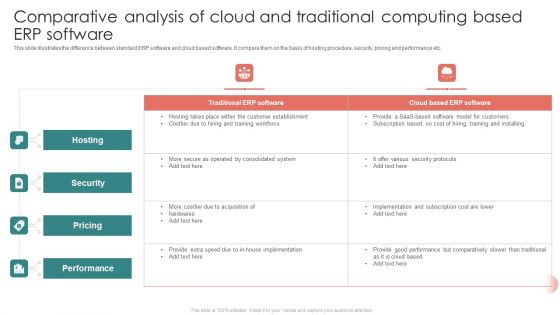
Comparative Analysis Of Cloud And Traditional Computing Based Erp Software Demonstration PDF
This slide illustrates the difference between standard ERP software and cloud based software. It compare them on the basis of hosting procedure, security, pricing and performance etc.Pitch your topic with ease and precision using this Comparative Analysis Of Cloud And Traditional Computing Based Erp Software Demonstration PDF. This layout presents information on Subscription Based, Operated Consolidated, House Implementation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Transaction Monitoring Transaction Monitoring Tools Market Insights Information PDF
This slide showcases market analysis of transaction monitoring tools industry. It provides details about retail, government, transaction security threats, manufacturing industry, know your customer KYC compliance, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Transaction Monitoring Transaction Monitoring Tools Market Insights Information PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
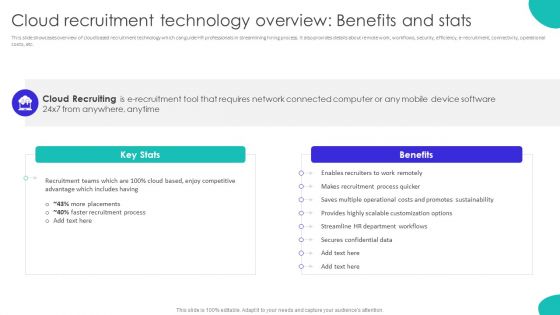
Improving Technology Based Cloud Recruitment Technology Overview Benefits And Stats Slides PDF
This slide showcases overview of cloud based recruitment technology which can guide HR professionals in streamlining hiring process. It also provides details about remote work, workflows, security, efficiency, e-recruitment, connectivity, operational costs, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Improving Technology Based Cloud Recruitment Technology Overview Benefits And Stats Slides PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
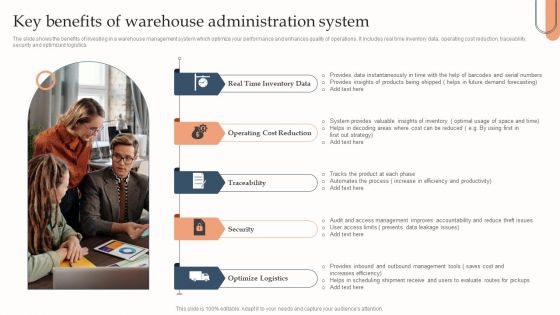
Key Benefits Of Warehouse Administration System Clipart PDF
The slide shows the benefits of investing in a warehouse management system which optimize your performance and enhances quality of operations. It includes real time inventory data, operating cost reduction, traceability,security and optimized logistics.Persuade your audience using this Key Benefits Of Warehouse Administration System Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Time Inventory Data, Operating Cost Reduction, Optimize Logistics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Tactics For Incorporating OT And IT With The Latest PI System Enterprise Technical Challenges Sample PDF
This slide covers technical challenges such as environmental, compatibility, skills shortage and security in enterprise while making IT OT convergence. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Tactics For Incorporating OT And IT With The Latest PI System Enterprise Technical Challenges Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Checklist For Website Quality Assurance Testing Ppt Layouts Background Images PDF
The slide showcases a checklist which can help you efficiently carryout your website qa process. it covers documentation, functional, usability, ui, compatibility, beta, mobile-friendly, change related, security and performance testing. Presenting Checklist For Website Quality Assurance Testing Ppt Layouts Background Images PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Beta Testing, Mobile Friendly Testing, Change Related Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
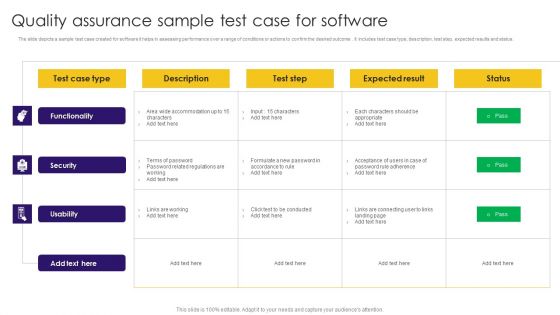
Quality Assurance Sample Test Case For Software Ppt Show Summary PDF
The slide depicts a sample test case created for software it helps in assessing performance over a range of conditions or actions to confirm the desired outcome. it includes test case type, description, test step, expected results and status. Pitch your topic with ease and precision using this Quality Assurance Sample Test Case For Software Ppt Show Summary PDF. This layout presents information on Functionality, Security, Usability, Test Case Type. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Optimizing Production Process Major Impact Of Smart Factory On Enterprises Template PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee and asset security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Optimizing Production Process Major Impact Of Smart Factory On Enterprises Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
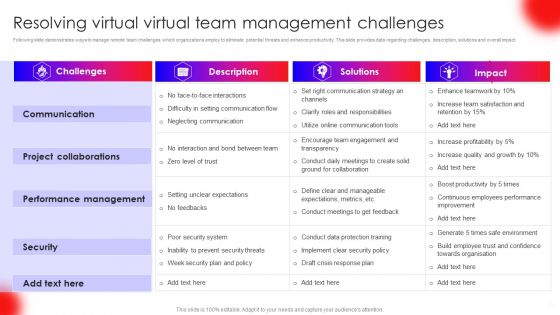
Resolving Virtual Virtual Team Management Challenges Rules PDF
Following slide demonstrates ways to manage remote team challenges which organizations employ to eliminate potential threats and enhance productivity. This slide provides data regarding challenges, description, solutions and overall impact. Pitch your topic with ease and precision using this Resolving Virtual Virtual Team Management Challenges Rules PDF. This layout presents information on Communication, Project Collaborations, Performance Management, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
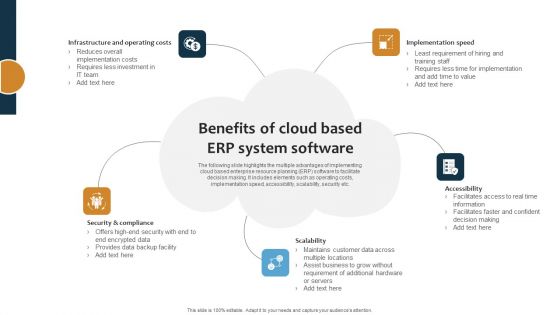
Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF
The following slide highlights the multiple advantages of implementing cloud based enterprise resource planning ERP software to facilitate decision making. It includes elements such as operating costs, implementation speed, accessibility, scalability, security etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
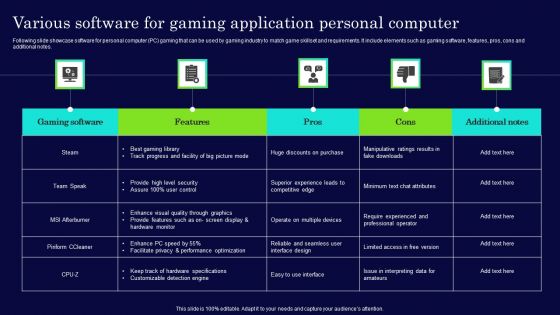
Various Software For Gaming Application Personal Computer Summary PDF
Following slide showcase software for personal computer PC gaming that can be used by gaming industry to match game skillset and requirements. It include elements such as gaming software, features, pros, cons and additional notes. Showcasing this set of slides titled Various Software For Gaming Application Personal Computer Summary PDF. The topics addressed in these templates are Team Speak, Performance Optimization, Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
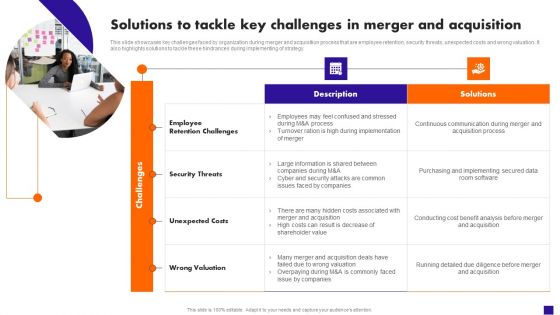
Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF
This slide showcases key challenges faced by organization during merger and acquisition process that are employee retention, security threats, unexpected costs and wrong valuation. It also highlights solutions to tackle these hindrances during implementing of strategy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Multi Level Marketing Company Outline Our Unique Selling Proposition USP Themes PDF
This slide highlights the Yashbiz company unique selling proposition which includes more than 80 products, secure shopping, 100 percent delivery and paid shipping. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Multi Level Marketing Company Outline Our Unique Selling Proposition USP Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Consumption Based Pricing Model Challenges In Recurring Business Model Slides PDF
The purpose of the following slide is to show multiple challenges that the company can face while implementing a recurring revenue model , these challenges can be customer management, payment security and invoicing. Make sure to capture your audiences attention in your business displays with our gratis customizable Consumption Based Pricing Model Business Performance Dashboard Demonstration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

IT Reducing Costs And Management Tips Importance Of IT Strategy In Delivering Value To Stakeholders Pictures PDF
This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. IT Reducing Costs And Management Tips Importance Of IT Strategy In Delivering Value To Stakeholders Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
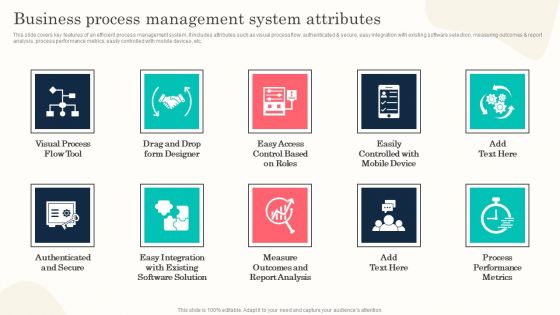
Business Process Management System Attributes Formats PDF
This slide covers key features of an efficient process management system. It includes attributes such as visual process flow, authenticated and secure, easy integration with existing software selection, measuring outcomes and report analysis, process performance metrics, easily controlled with mobile devices, etc. There are so many reasons you need a Business Process Management System Attributes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
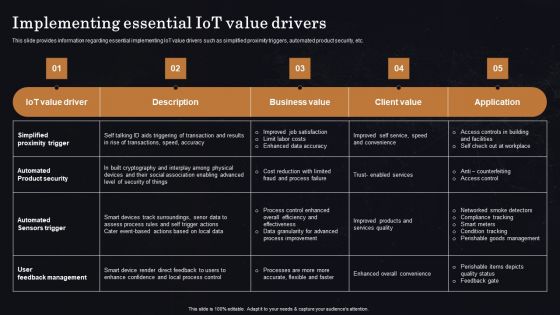
Implementing Essential Iot Value Drivers Ppt Inspiration Design Templates PDF
This slide provides information regarding essential implementing IoT value drivers such as simplified proximity triggers, automated product security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Essential Iot Value Drivers Ppt Inspiration Design Templates PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Impact Of Cybersecurity Incidents On Organization Microsoft PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Impact Of Cybersecurity Incidents On Organization Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Major Reasons For Not Automating Manual Tasksoptimizing Business Processes Through Automation Infographics PDF
The following slide outlines different reasons due to which the organization is not implementing process automation at workplace. The key reasons highlighted in the slide are higher cost, security concern and no formal training. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Major Reasons For Not Automating Manual Tasksoptimizing Business Processes Through Automation Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
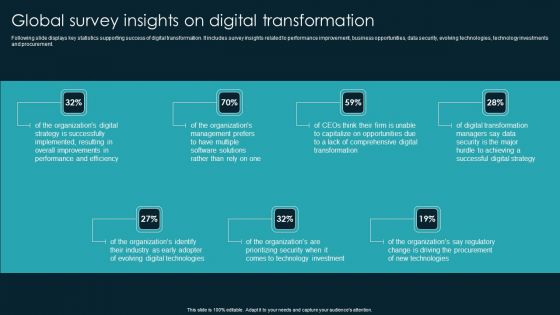
Global Survey Insights On Digital Transformation Icons PDF

Iot Integration In Manufacturing Digital Twin Technology Supply Chain Management Slides PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Iot Integration In Manufacturing Digital Twin Technology Supply Chain Management Slides PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Intelligent Process Automation IPA Machine Learning Applications In Different Areas Icons PDF
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Intelligent Process Automation IPA Machine Learning Applications In Different Areas Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
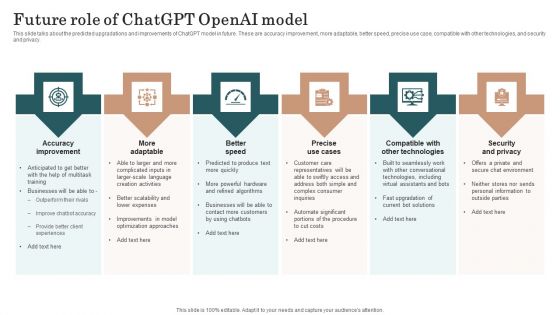
Chatgpt Incorporation Into Web Apps Future Role Of Chatgpt Openai Model Topics PDF
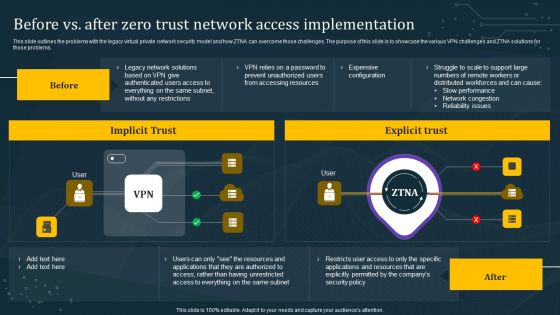
Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comparison Between CASB And Data Loss Prevention DLP Ppt PowerPoint Presentation File Portfolio PDF
This slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Comparison Between CASB And Data Loss Prevention DLP Ppt PowerPoint Presentation File Portfolio PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
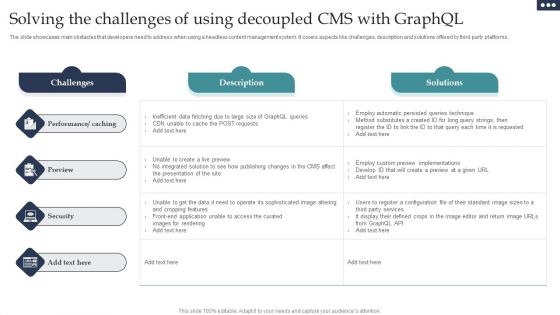
Solving The Challenges Of Using Decoupled CMS With Graphql Portrait PDF
The slide showcases main obstacles that developers need to address when using a headless content management system. It covers aspects like challenges, description and solutions offered by third party platforms. Showcasing this set of slides titled Solving The Challenges Of Using Decoupled CMS With Graphql Portrait PDF. The topics addressed in these templates are Performance Caching, Preview, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
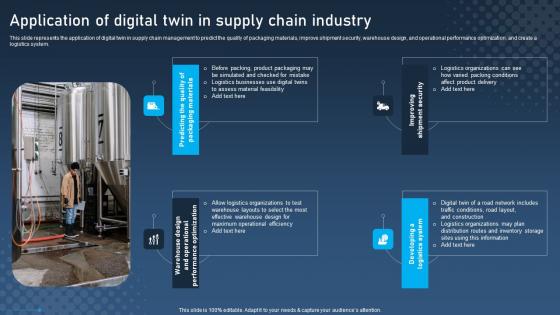
Application Of Digital Twin In Supply Chain Digital Twins For Enhanced Industrial Download Pdf
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Want to ace your presentation in front of a live audience Our Application Of Digital Twin In Supply Chain Digital Twins For Enhanced Industrial Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
Bluetooth Low Energy Ble Maximizing Efficiency With Asset Tracking Solutions Formats Pdf
This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Bluetooth Low Energy Ble Maximizing Efficiency With Asset Tracking Solutions Formats Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
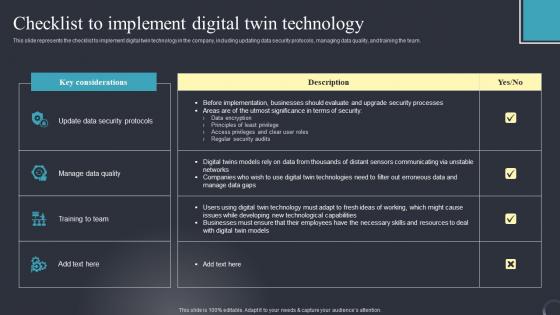
Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Company Introduction Paubox Capital Funding Pitch Deck Mockup Pdf
This slide covers a company overview of email security enterprise. It includes information such as foundation date, company status, employee count, headquarters, website, and industry. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Company Introduction Paubox Capital Funding Pitch Deck Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
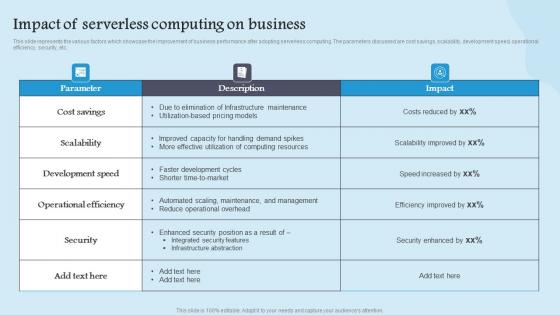
Impact Serverless Computing Role Serverless Computing Modern Technology Information Pdf
This slide represents the various factors which showcase the improvement of business performance after adopting serverless computing. The parameters discussed are cost savings, scalability, development speed, operational efficiency, security, etc. Find a pre designed and impeccable Impact Serverless Computing Role Serverless Computing Modern Technology Information Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
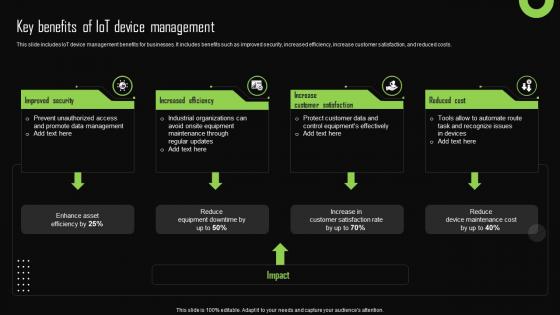
Key Benefits Of Iot Device Management Iot Device Management Designs Pdf
This slide includes IoT device management benefits for businesses. It includes benefits such as improved security, increased efficiency, increase customer satisfaction, and reduced costs. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Benefits Of Iot Device Management Iot Device Management Designs Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
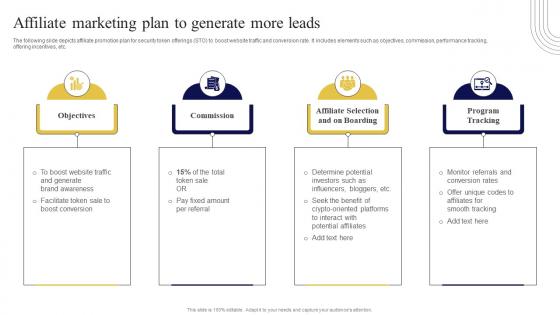
Affiliate Marketing Plan To Generate Exploring Investment Opportunities Diagrams Pdf
The following slide depicts affiliate promotion plan for security token offerings STO to boost website traffic and conversion rate. It includes elements such as objectives, commission, performance tracking, offering incentives, etc. Find a pre-designed and impeccable Affiliate Marketing Plan To Generate Exploring Investment Opportunities Diagrams Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf
The following slide illustrates major roles and responsibilities of security token offerings team to ensure successful launch. It includes elements such as technical officer, community manager, engineers, developers, founder, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
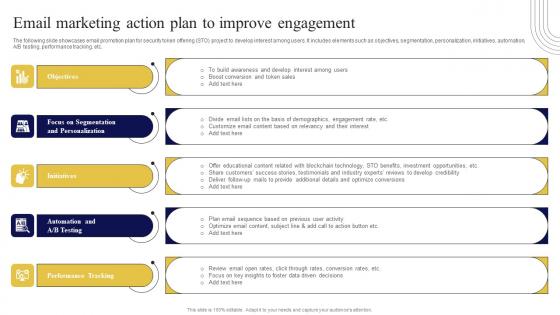
Email Marketing Action Plan To Improve Exploring Investment Opportunities Infographics Pdf
The following slide showcases email promotion plan for security token offering STO project to develop interest among users. It includes elements such as objectives, segmentation, personalization, initiatives, automation, A B testing, performance tracking, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Email Marketing Action Plan To Improve Exploring Investment Opportunities Infographics Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Strategic Content Marketing Plan To Engage Exploring Investment Opportunities Themes Pdf
The following slide illustrates content marketing action plan for security token offerings STO to maximize reach. It includes elements such as objectives, target audience, content strategy, create blogs, determine areas of improvement, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Strategic Content Marketing Plan To Engage Exploring Investment Opportunities Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Bluetooth Low Energy Ble Asset Tracking Technique RFID Solutions For Asset Traceability Mockup Pdf
This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Bluetooth Low Energy Ble Asset Tracking Technique RFID Solutions For Asset Traceability Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Deploying An Efficient Organizational Structure Childcare Business Plan Download Pdf
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Deploying An Efficient Organizational Structure Childcare Business Plan Download Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Deploying An Efficient Organizational Structure For Childcare Business Plan Structure Pdf
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Deploying An Efficient Organizational Structure For Childcare Business Plan Structure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
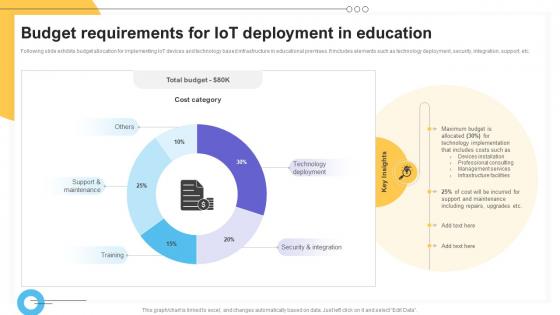
Budget Requirements For IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V
Following slide exhibits budget allocation for implementing IoT devices and technology based infrastructure in educational premises. It includes elements such as technology deployment, security, integration, support, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Budget Requirements For IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Challenges For Entrepreneurs In Crypto Exchange Complete Roadmap To Blockchain BCT SS V
This slide covers issues faced by entrepreneurs in trading with cryptocurrency exchanges. It includes challenges such as website security, latest knowledge about business trends and technology, updating exchange business with multiple currency trading with description and solutions to overcome the risks and problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Challenges For Entrepreneurs In Crypto Exchange Complete Roadmap To Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Overview Of Decentralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers brief summary of decentralized crypto exchanges with ways to operate by users. It also includes benefits such as faster and cheaper transactions, secure, integration with hardware wallets, users control funds, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Decentralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media
This slide showcases the Considerations while using Social Media Analytics tools. The purpose of this slide is to highlight the points of consideration such as language, customization, recourse, data security, and protection, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
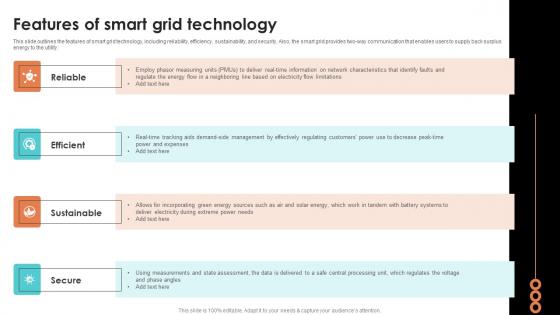
Features Of Smart Grid Technology Smart Grid Working
This slide outlines the features of smart grid technology, including reliability, efficiency, sustainability, and security. Also, the smart grid provides two way communication that enables users to supply back surplus energy to the utility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Features Of Smart Grid Technology Smart Grid Working will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
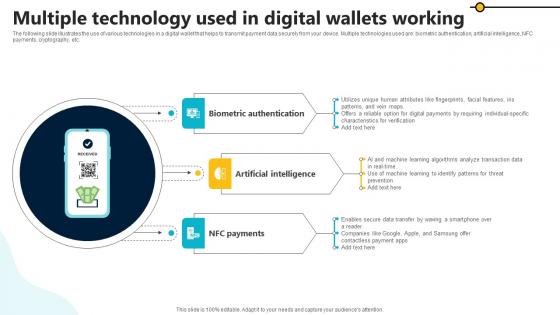
Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V
The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comprehensive Look At Blockchain Skills Required To Become Blockchain BCT SS V
This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comprehensive Look At Blockchain Skills Required To Become Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Quality Assurance Testing Checklist For Effective Data Migration From On Premises
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. The Quality Assurance Testing Checklist For Effective Data Migration From On Premises is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Types Of Cloud Migration Testing Methods Data Migration From On Premises
This slide showcases various cloud migration testing models used to analyze application performance such as system, security, recovery testing. Take your projects to the next level with our ultimate collection of Types Of Cloud Migration Testing Methods Data Migration From On Premises. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Seamless Integration The Power Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
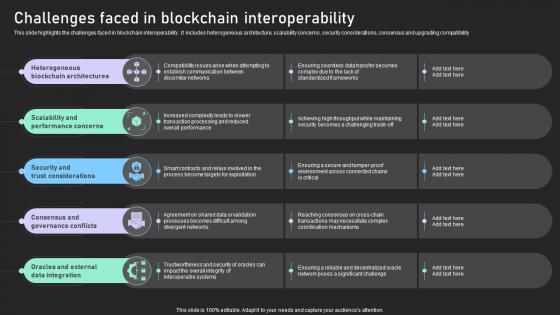
Understanding Various Blockchain Challenges Faced In Blockchain Interoperability BCT SS V
This slide highlights the challenges faced in blockchain interoperability . It includes heterogeneous architecture, scalability concerns, security considerations, consensus and upgrading compatibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Understanding Various Blockchain Challenges Faced In Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Related And Unrelated Business Steps For Successful Business Diversification Strategy SS V
This slide showcases process that can help organization to formulate business diversification strategy. Its key steps are establish supportive corporate centre, select capable division managers, performance measures, secure competitive advantage, align corporate culture and set incentives. There are so many reasons you need a Related And Unrelated Business Steps For Successful Business Diversification Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
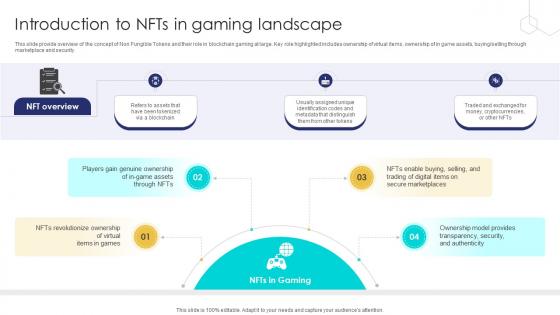
Unlocking The Potential Of Introduction To Nfts In Gaming Landscape BCT SS V
This slide provide overview of the concept of Non Fungible Tokens and their role in blockchain gaming at large. Key role highlighted includes ownership of virtual items, ownership of in game assets, buying or selling through marketplace and security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Unlocking The Potential Of Introduction To Nfts In Gaming Landscape BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
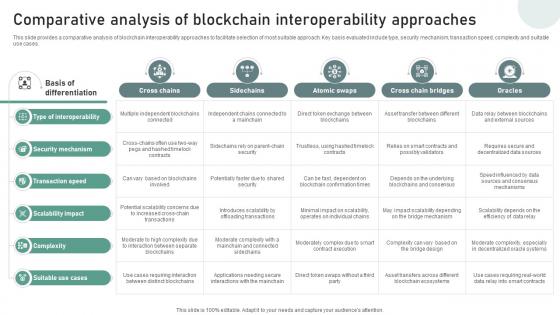
Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V
This slide provides a comparative analysis of blockchain interoperability approaches to facilitate selection of most suitable approach. Key basis evaluated include type, security mechanism, transaction speed, complexity and suitable use cases. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Bridging Blockchains A Deep Comparative Analysis Of Blockchain Interoperability BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. Boost your pitch with our creative Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Effective Data Migration Types Of Cloud Migration Testing Methods
This slide showcases various cloud migration testing models used to analyze application performance such as system, security, recovery testing. Get a simple yet stunning designed Effective Data Migration Types Of Cloud Migration Testing Methods. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Effective Data Migration Types Of Cloud Migration Testing Methods can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
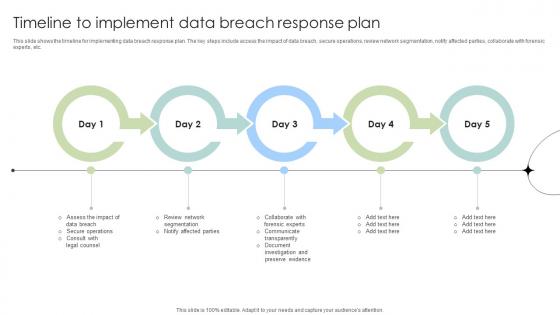
Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses
This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
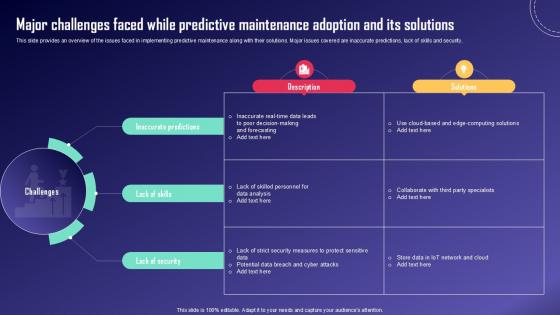
Major Challenges Faced While IoT Fleet Monitoring Ppt Template IoT SS V
This slide provides an overview of the issues faced in implementing predictive maintenance along with their solutions. Major issues covered are inaccurate predictions, lack of skills and security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Major Challenges Faced While IoT Fleet Monitoring Ppt Template IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
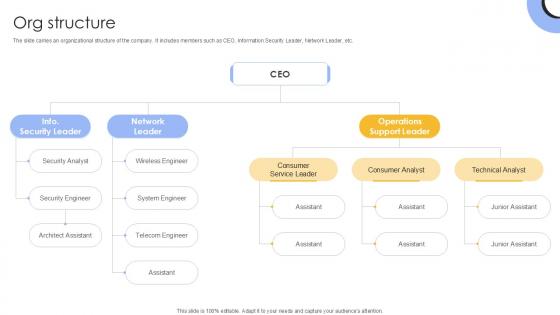
Org Structure Investment Company Investor Funding Elevator Ppt Presentation
The slide carries an organizational structure of the company. It includes members such as CEO, Information Security Leader, Network Leader, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Org Structure Investment Company Investor Funding Elevator Ppt Presentation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Steps To Drive Sustainable Governance For Devsecops Role Of Devsecops Ppt Sample
This slide discusses the approach to developing a sustainable governance model for DevSecOps. The purpose of this slide is to go through various aspects to drive scalable governance these include role and responsibility, policies and procedures, security automation, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Drive Sustainable Governance For Devsecops Role Of Devsecops Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Challenges And Solutions In Web Application Development PPT Template SS
This slide presents solutions to challenges faced during web application development helpful in streamlining process, increasing accuracy and making customer experience better. It includes user interface and user experience, scalability, performance and security that are highly important aspects to focus upon. There are so many reasons you need a Challenges And Solutions In Web Application Development PPT Template SS. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Checklist For Implementing Harnessing The World Of Ethical Ppt Example
This slide represents the checklist for implementing application security testing components such as coverage, low false positive, exploitability, code visibility, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Implementing Harnessing The World Of Ethical Ppt Example will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Process Of Disaster Recovery Planning IT Security IT Ppt Outline Example Introduction PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a process of disaster recovery planning it security it ppt outline example introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data collection, plan testing, approval, perform risk analysis, prioritize procedures and operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
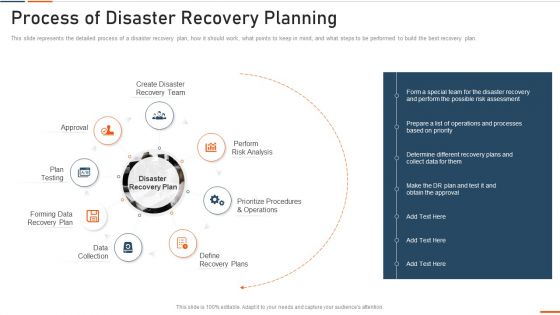
Information Technology Security Process Of Disaster Recovery Planning Ppt Portfolio Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information technology security process of disaster recovery planning ppt portfolio summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like approval, plan testing, recovery plan, data collection, perform . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
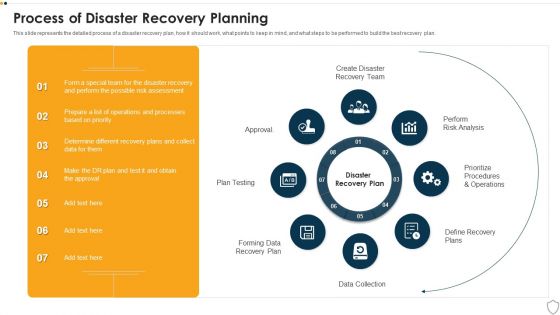
IT Security Process Of Disaster Recovery Planning Ppt Portfolio Microsoft PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting it security process of disaster recovery planning ppt portfolio microsoft pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like plan testing, perform risk analysis, data collection, prioritize procedures and operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
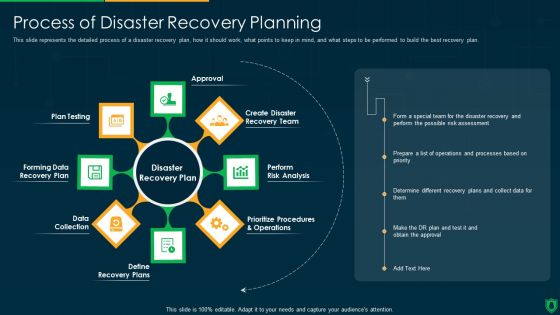
Info Security Process Of Disaster Recovery Planning Ppt PowerPoint Presentation File Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a info security process of disaster recovery planning ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like approval, perform risk analysis, define recovery plans, data collection, forming data recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf
This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc. Create an editable Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
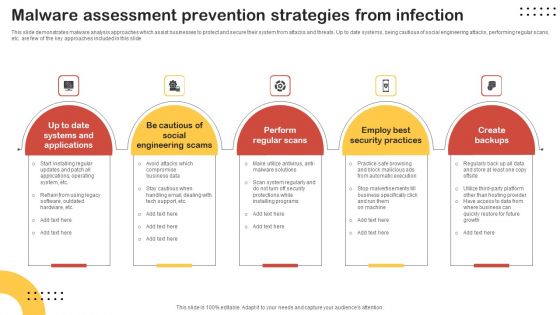
Malware Assessment Prevention Strategies From Infection Topics PDF
This slide demonstrates malware analysis approaches which assist businesses to protect and secure their system from attacks and threats. Up to date systems, being cautious of social engineering attacks, performing regular scans, etc. are few of the key approaches included in this slide. Presenting Malware Assessment Prevention Strategies From Infection Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Perform Regular Scans, Employ Best Security Practices, Create Backups. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
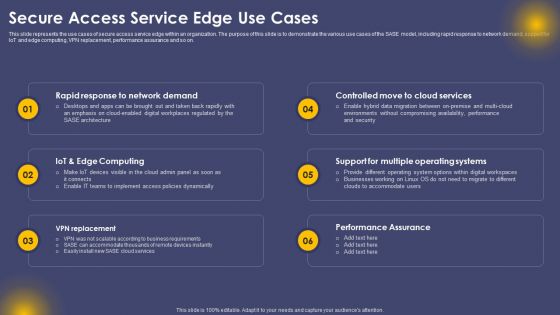
Secure Access Service Edge Use Cases Ppt Outline Images PDF
This slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Explore a selection of the finest Secure Access Service Edge Use Cases Ppt Outline Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Secure Access Service Edge Use Cases Ppt Outline Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V
This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
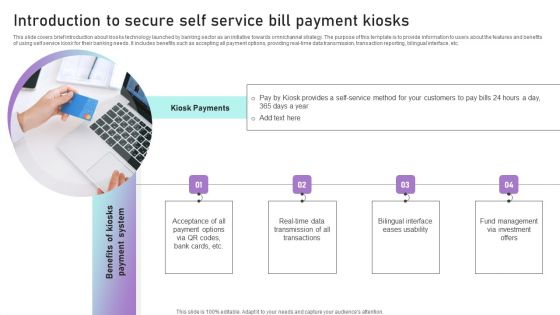
Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V
This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

 Home
Home