Safety Management
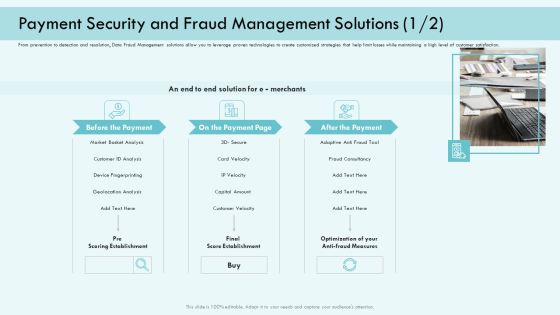
E Payment Transaction System Payment Security And Fraud Management Solutions Analysis Infographics PDF
Presenting E payment transaction system payment security and fraud management solutions analysis infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like market basket analysis, device fingerprinting, customer velocity, optimization of your anti fraud measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
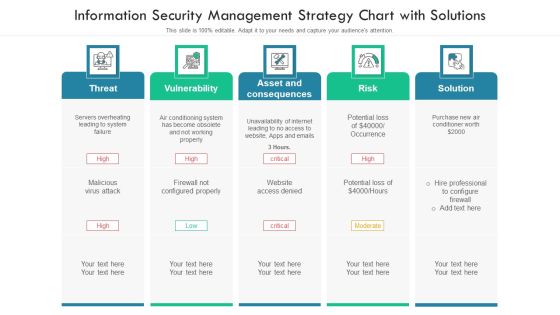
Information Security Management Strategy Chart With Solutions Ppt PowerPoint Presentation File Slides PDF
Persuade your audience using this information security management strategy chart with solutions ppt powerpoint presentation file slides pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including threat, vulnerability, risk, solution. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Guidelines To Create An Advanced Security Management Plan Formats PDF
This is a agenda for guidelines to create an advanced security management plan formats pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Guidelines To Create An Advanced Security Management Plan 30 60 90 Days Plan Rules PDF
Presenting guidelines to create an advanced security management plan 30 60 90 days plan rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Guidelines To Create An Advanced Security Management Plan Meet Our Awesome Team Download PDF
This is a guidelines to create an advanced security management plan meet our awesome team download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like meet our awesome team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Guidelines To Create An Advanced Security Management Plan Post It Notes Professional PDF
Presenting guidelines to create an advanced security management plan post it notes professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail System Maintenance And Monitoring Sample PDF
Presenting security management plan steps in detail system maintenance and monitoring sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like corrective maintenance, adaptive maintenance, perfective maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Implementing Security Management Strategy To Mitigate Risk Post It Notes Topics PDF
This is a implementing security management strategy to mitigate risk post it notes topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Defining Vulnerability Rating With Criteria Summary PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
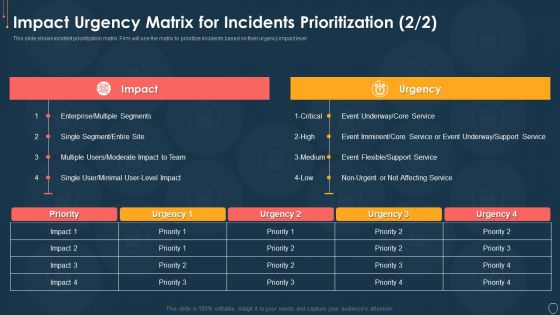
Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Event Topics PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative cyber security risk management plan impact urgency matrix for incidents prioritization event topics pdf bundle. Topics like impact urgency matrix for incidents prioritization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Location Information PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact urgency matrix for incidents prioritization location information pdf. Use them to share invaluable insights on business, location, inconvenient, moderate, preform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan 30 60 90 Days Plan Infographics PDF
This is a cyber security risk management plan 30 60 90 days plan infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Online And Onsite Training Schedule For Employee Elements PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative cyber security risk management plan online and onsite training schedule for employee elements pdf bundle. Topics like position, software name, course type, training mode, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Risk Reporting And Likelihood Elements PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative cyber security risk management plan risk reporting and likelihood elements pdf bundle. Topics like risk encountered, frequency, reported by status, attack scenario, affected asset, likelihood can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Techniques And Strategies To Reduce Security Management Risks Themes PDF
This is a agenda for techniques and strategies to reduce security management risks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like enable organizational, structure and technology, internal and external You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Comparative Assessment Of Various Threat Agents Slides PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management comparative assessment of various threat agents slides pdf. Use them to share invaluable insights on comparative assessment of various threat agents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Determine Several Threat Actors Profile Clipart PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management determine several threat actors profile clipart pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Determine Threat Scenario Analysis Formats PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative corporate security and risk management determine threat scenario analysis formats pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Incident Reporting By Different Departments Template PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Deliver an awe inspiring pitch with this creative corporate security and risk management incident reporting by different departments template pdf bundle. Topics like incident reporting by different departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Financial Performance Tracking Dashboard Introduction PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an awe inspiring pitch with this creative corporate security and risk management financial performance tracking dashboard introduction pdf bundle. Topics like revenue and expense trends, receivables analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
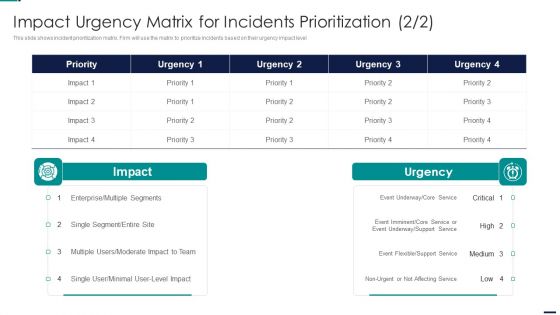
Impact Urgency Matrix For Incidents Risk Management Model For Data Security Pictures PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative Impact Urgency Matrix For Incidents Risk Management Model For Data Security Pictures PDF bundle. Topics like Priority, Multiple Segments, Enterprise, Moderate Impact to Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF bundle. Topics like High System Wide, Medium Multiple Users, Low Single User, Inconvenient can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF bundle. Topics like Course Type, Training Mode, Training Duration, Employee can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF bundle. Topics like Risk Encountered, Frequency, Attack Scenario, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
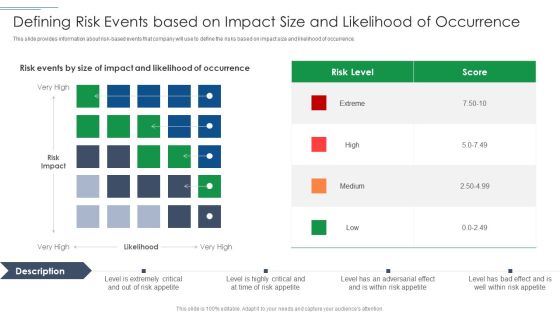
IT Security Risk Management Approach Introduction Defining Risk Events Based On Impact Size Demonstration PDF
This slide provides information about risk based events that company will use to define the risks based on impact size and likelihood of occurrence. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Defining Risk Events Based On Impact Size Demonstration PDF bundle. Topics like Risk Level, Defining Risk Events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Encountered Risks Summary And Their Impact Assessment Professional PDF
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Encountered Risks Summary And Their Impact Assessment Professional PDF. Use them to share invaluable insights on Moderate Inherent Risk, Risks By Category, Financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
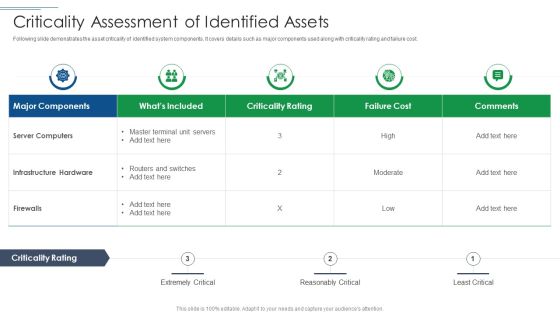
IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF bundle. Topics like Server Computers, Infrastructure Hardware, Failure Cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Information Systems Security And Risk Management Plan Our Mission Infographics PDF
The Information Systems Security And Risk Management Plan Our Mission Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizational Assets Security Management Strategy Critical Business Functions Recovery Priorities Template PDF
After the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. There are so many reasons you need a Organizational Assets Security Management Strategy Critical Business Functions Recovery Priorities Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Desktop Security Management Elements Of Computer Security Disaster Recovery Planning Guidelines PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting desktop security management elements of computer security disaster recovery planning guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, resources, financial budget, strategies, plans. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security End User Education Background PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a desktop security management elements of computer security end user education background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, opportunities, security, organization, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execution Of ICT Strategic Plan Role Of Technology In Effective Staff Management Download PDF
This slide represents role of technology in workforce management. It includes innovation, upgraded workspace, error-free work discourse, and security. The Execution Of ICT Strategic Plan Role Of Technology In Effective Staff Management Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

IT Policies And Procedures Password Creation And Management Policy Diagrams PDF
This slide depicts the password creation and management policy that explains how to create, implement, and review a defined procedure for establishing, updating, and maintaining strong and secure passwords. Slidegeeks has constructed IT Policies And Procedures Password Creation And Management Policy Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
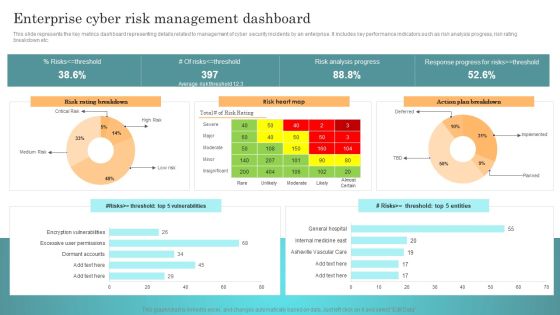
Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Find highly impressive Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Enable Data Centre Management Through Hyper Converged Infrastructure Ppt PowerPoint Presentation File Inspiration PDF
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Find highly impressive Enable Data Centre Management Through Hyper Converged Infrastructure Ppt PowerPoint Presentation File Inspiration PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Enable Data Centre Management Through Hyper Converged Infrastructure Ppt PowerPoint Presentation File Inspiration PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Personal Care Company Profile Management Team Ppt PowerPoint Presentation Gallery Icons PDF
This slide shows the management team of our company which includes chief executive officer, vice president, chief technology officer and senior marketing executive with experience, responsibilities and specialization. Presenting Personal Care Company Profile Management Team Ppt PowerPoint Presentation Gallery Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Corporate Decisions, Cosmetics Industry, Information Security, Data Collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Roles And Responsibilities To Ensure Work Professional PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a corporate security and risk management roles and responsibilities to ensure work professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, unit supervisor manager responsibilities, internal investigations unit responsibilities, human resources responsibilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deployment Of Cloud Project Management Model Ppt PowerPoint Presentation File Infographics PDF
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Deployment Of Cloud Project Management Model Ppt PowerPoint Presentation File Infographics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF
This slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present like a pro with Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Key Features And Benefits Of Cloud Project Management Ppt PowerPoint Presentation File Layouts PDF
The following slide depicts major features and benefits of cloud based project management. It provides details about reliability, integration, collaboration, secure backup, free monthly trials, remote team support, etc. Get a simple yet stunning designed Key Features And Benefits Of Cloud Project Management Ppt PowerPoint Presentation File Layouts PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Key Features And Benefits Of Cloud Project Management Ppt PowerPoint Presentation File Layouts PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Risk Management Plan Introducing Information Security Risk Assessment Process Workflow Elements PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a cyber security risk management plan introducing information security risk assessment process workflow elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like characterize system, identify vulnerabilities, identify threats, recommend remediation measures, analyze risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Risk Management Approach Introduction Kpi Dashboard To Track Security Risk Events Icons PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Kpi Dashboard To Track Security Risk Events Icons PDF. Use them to share invaluable insights on System Technology Risk, Governance Risk, Security Risk Events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF. Use them to share invaluable insights on Rating Breakdown, Vulnerabilities, Response Progress and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ensuring Checklist For Mobile Security Deployment Business Mobile Device Security Management Sample PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Ensuring Checklist For Mobile Security Deployment Business Mobile Device Security Management Sample PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Project Security Administration IT Budget For Effective Project Management At Workplace Themes PDF
Firm has prepared a budget for managing projects effectively by optimizing various functional areas across workplace. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative project security administration it budget for effective project management at workplace themes pdf bundle. Topics like functional area, software, implement duration, cost of implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Systems Security And Risk Management Plan Mitigation Strategies To Tackle Information Security Threats Information PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Systems Security And Risk Management Plan Mitigation Strategies To Tackle Information Security Threats Information PDF from Slidegeeks and deliver a wonderful presentation.

Information Analysis And BI Playbook Requirement Of Data Management In BI Projects Brochure PDF
This slide covers the reasons for data management in an organisation such as minimizing the data movement and attention to data security Present like a pro with Information Analysis And BI Playbook Requirement Of Data Management In BI Projects Brochure PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Key Business Account Management And Planning Defining Customer Needs And Wants To Provide Brochure PDF
This slide provides glimpse about understanding customers on the basis of their needs, wants, and fears for key account planning and management. It includes needs such as reliable, secure, scalable technology solutions, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Business Account Management And Planning Defining Customer Needs And Wants To Provide Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Desktop Security Management Dashboard For Threat Tracking In Computer Security Guidelines PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative desktop security management dashboard for threat tracking in computer security guidelines pdf bundle. Topics like threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
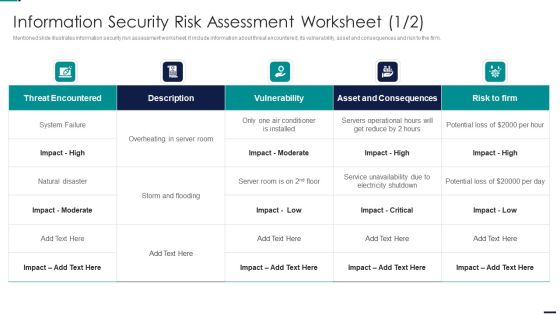
Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF. Use them to share invaluable insights on Threat Encountered, Vulnerability, Asset And Consequences, Risk To Firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. This Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
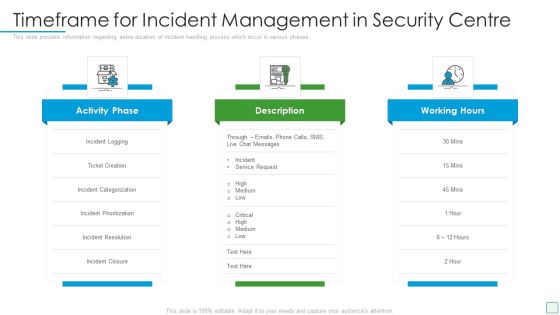
Developing Firm Security Strategy Plan Timeframe For Incident Management In Security Centre Download PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting developing firm security strategy plan timeframe for incident management in security centre download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Contract Framework In Blockchain Technology For Digital Asset Management Ideas PDF
This slide showcase smart contract framework for digital asset management to optimize assets transfer process with technology evolution. It includes buyer seller, blockchain network topology and arbitrator. Presenting Smart Contract Framework In Blockchain Technology For Digital Asset Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Blockchain Network, Security, Capital. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Benefits Of Block Chain Technology In Supply Chain Management Introduction PDF
This slide covers advantages of block chain for effective supply chain management . It includes transparency, scalability, security, eliminating fraud and ability to interoperate.Persuade your audience using this Benefits Of Block Chain Technology In Supply Chain Management Introduction PDF This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Transparency, Eliminating Fraud, Ability To Interoperate Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Effective Business Project Risk Mitigation Plan Project Risk Management Tracking Software Information PDF
This slide provides an overview of project management software used to monitor and track risks. It includes reviews, trials, pricing and features which are automatic risk alerts, a secure database, details reporting and customizable parameters. There are so many reasons you need a Effective Business Project Risk Mitigation Plan Project Risk Management Tracking Software Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

 Home
Home