Safety Management

Solution Key Alarm Clock Time Management PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Solution Key Alarm Clock Time Management PowerPoint Templates PPT Backgrounds For Slides 0413.Present our Clocks PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Present our Security PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Present our Business PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Download and present our Shapes PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way.Use these PowerPoint slides for presentations relating to Clock and key concept of successful time management, security, success, business, clocks, shapes. The prominent colors used in the PowerPoint template are Red, Black, White.

Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

How To Implement Cloud Collaboration Deployment Of Cloud Project Management Model Pictures PDF
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Deliver an awe inspiring pitch with this creative How To Implement Cloud Collaboration Deployment Of Cloud Project Management Model Pictures PDF bundle. Topics like Data Security, Data Control, Scalability Flexibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
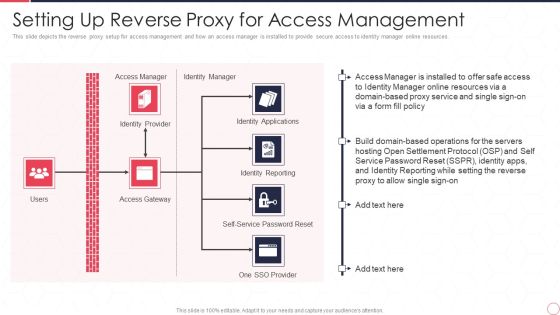
Reverse Proxy Server IT Setting Up Reverse Proxy For Access Management Ppt Ideas Guide PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources. Presenting reverse proxy server it setting up reverse proxy for access management ppt ideas guide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like access manager, identity manager, identity applications, identity reporting, access gateway, identity provider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective IT Risk Management Process Setting Scenario For Security Control Sample PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting effective it risk management process setting scenario for security control sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Apache Hadoop IT Features Of Hadoop Cluster Management Tool Sample PDF
This slide describes the features of the Hadoop cluster management tool, including high availability, work schedule, policies, backup management, security measures, etc.Presenting apache hadoop it features of hadoop cluster management tool sample pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like resource provisioning, performance optimization, provide high availability In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Impact Of Effective Testing And Quality Management Of Devops System Icons PDF Topics PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. This is a impact of effective testing and quality management of devops system icons pdf topics pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud based environment, test data management, procurement and management You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management For Organization Essential Assets Impact Analysis For Effective Threat Rules PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative risk management for organization essential assets impact analysis for effective threat rules pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Project Management Through Agile Approach 6 Steps In Agile Methodology Designs PDF
This slide provides the glimpse about the ten successful strategies for transitioning agile such as management commitment, team empowerment, collaborative culture, embrace agile methods, etc. Presenting project management through agile approach 6 steps in agile methodology designs pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like secure management commitment, empowering the team, embrace agile methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cios Initiative 9 Implementing IT Risk Management Framework Ppt PowerPoint Presentation File Maker PDF
This slide provides information regarding implementation of IT risk management framework with immediate, short term and long term initiatives. Deliver and pitch your topic in the best possible manner with this cios initiative 9 implementing it risk management framework ppt powerpoint presentation file maker pdf. Use them to share invaluable insights on security processes, control environment, enterprise security programand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Apache Hadoop Software Deployment Features Of Hadoop Cluster Management Tool Elements PDF
This slide describes the features of the Hadoop cluster management tool, including high availability, work schedule, policies, backup management, security measures, etc.Presenting Apache Hadoop Software Deployment Features Of Hadoop Cluster Management Tool Elements PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Resource Provisioning, Health Monitoring, Performance Optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Matrix For IT Risk Control Strategies Security Ppt Professional Show PDF
This slide shows the risk management matrix for information technology security which covers the business workflow and technical systems with IT risks and threats such as software security, business controls, control risk modelling, penetration testing, attack modelling, etc. Pitch your topic with ease and precision using this Risk Management Matrix For IT Risk Control Strategies Security Ppt Professional Show PDF. This layout presents information on Corporate Workflow, Technical Systems, Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Functions Management Table Of Content Ppt Model Files PDF
This is a information technology functions management table of content ppt model files pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to infrastructure, asset management process, inventory and condition assessment, deterioration modeling, optimization and decision making, performance and cost functions, interdependence, resiliency and security, contract and workflow management, commissioning new facilities, capital budgeting, metrics and dashboard. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ETL Repository Strategic Implementation Of Cloud Data Management Techniques Mockup PDF
Responding to modern business challenges, you need a new cloud data management strategy that takes an integrated approach to data across its life cycle, combining traditional disciplines of data backup and recovery, data protection, data security, and data management.Presenting ETL Repository Strategic Implementation Of Cloud Data Management Techniques Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Supplemented Snapshots, Replication Necessary, Recoverable Available. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Organizational Assets Security Management Strategy Ppt PowerPoint Presentation Complete Deck With Slides
In business, sometimes the end result can be completely different from what stakeholders visualized. This Organizational Assets Security Management Strategy Ppt PowerPoint Presentation Complete Deck With Slides details the study of enterprise and problem solving as a fundamental area of getting the desired outcomes. Stakeholders need to be convinced of how to proceed and change through this wonderful PPT presentation. The idea guiding this complete deck of twenty two presentation slides is to ensure that dealing with change and unexpected results becomes easy. The area of focus for this change can be customized with the 100 percent editable and customizable nature of each of the slides in our presentation. Download now.

Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF
This slide represents information management objectives in end user computing such as organizing information, maximization of information value, security and protection etc. Presenting Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Organizing Information Utilization, Security And Protection, Business Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Corporate Security And Risk Management Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This corporate security and risk management ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of sixty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Retrieve professionally designed Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incentive Scheme, Referral Partners, Sales Strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance Our Companys Mission Designs PDF
This slide provides the details of our company mission, vision and values to provide unique services to the customers. This is a security information and event management strategies for financial audit and compliance our companys mission designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our mission, our vision, our values. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
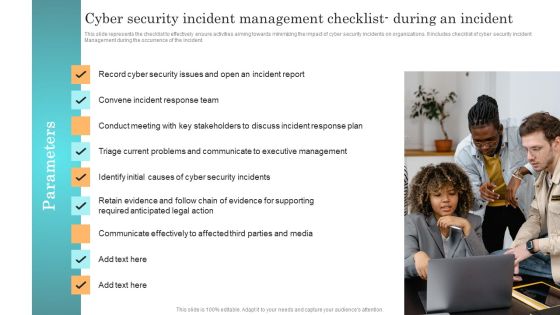
Incident Response Techniques Deployement Cyber Security Incident Management Checklist During An Incident Professional PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident Management during the occurrence of the incident. Create an editable Incident Response Techniques Deployement Cyber Security Incident Management Checklist During An Incident Professional PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Incident Response Techniques Deployement Cyber Security Incident Management Checklist During An Incident Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Enhanced Protection Corporate Event Administration Selecting Suitable Security Incident Management Software Demonstration PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration selecting suitable security incident management software demonstration pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF.

Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF
This slide provides information about enabling online brand protection by tracking incidents per seller, incident per platform and infringements per country. Presenting this PowerPoint presentation, titled Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Are you searching for a CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF from Slidegeeks today.

CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Create an editable CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
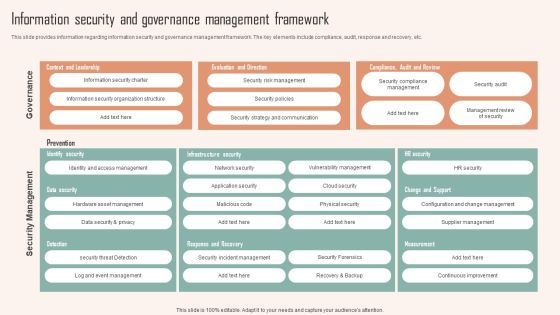
Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
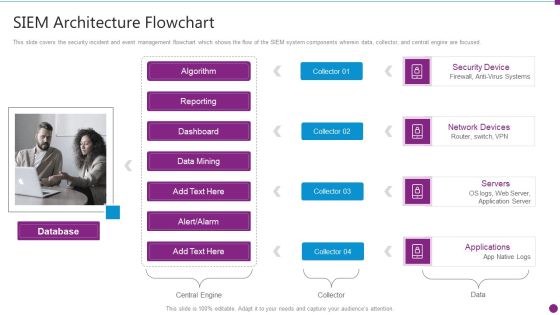
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Flowchart Microsoft PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a security information and event management strategies for financial audit and compliance siem architecture flowchart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Risk Control And Surveillance Project Risk Management Tracking Software Summary PDF
slide provides an overview of project management software used to monitor and track risks. It includes reviews, trials, pricing and features which are automatic risk alerts, a secure database, details reporting and customizable parameters. Presenting this PowerPoint presentation, titled Risk Control And Surveillance Project Risk Management Tracking Software Summary PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Risk Control And Surveillance Project Risk Management Tracking Software Summary PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Risk Control And Surveillance Project Risk Management Tracking Software Summary PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
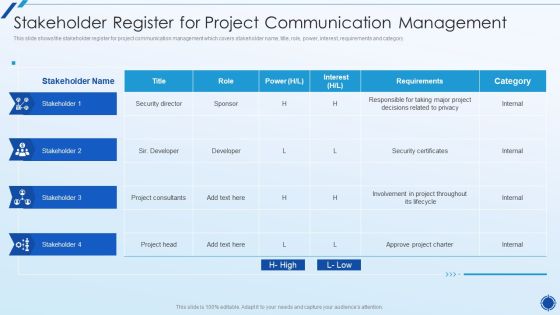
Organizing Action Plan For Successful Project Management Stakeholder Register For Project Pictures PDF
This slide shows the stakeholder register for project communication management which covers stakeholder name, title, role, power, interest, requirements and category.Deliver and pitch your topic in the best possible manner with this organizing action plan for successful project management stakeholder register for project pictures pdf. Use them to share invaluable insights on security certificates, involvement in project throughout, approve project charter and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
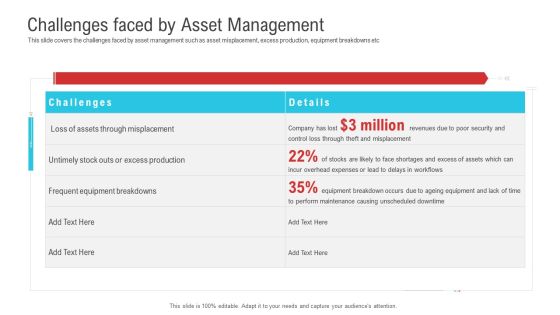
Enterprise System Business Administration Challenges Faced By Asset Management Slides PDF
This slide covers the challenges faced by asset management such as asset misplacement, excess production, equipment breakdowns etc. Deliver an awe-inspiring pitch with this creative enterprise system business administration challenges faced by asset management slides pdf bundle. Topics like equipment breakdown, revenues, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Application Programming Interface Administrative Marketplace Architecture Of API Management Clipart PDF
The figure given below shows the architectural components of API Management Solution. It shows the features that API tool provide include traffic monitoring, API designing and maintenance. Deliver and pitch your topic in the best possible manner with this application programming interface administrative marketplace architecture of api management clipart pdf. Use them to share invaluable insights on analysis, community, mobile applications, security, resource and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Three Customer Relationship Management Strategies To Build Effective Customer In Banking Sector Summary PDF
This slide outlines three CRM techniques to build effective customer strategy in banking industry. It involves strategies such as customer segmentation, provide effective customer service and get banking data secured.Persuade your audience using this Three Customer Relationship Management Strategies To Build Effective Customer In Banking Sector Summary PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Communication, Segmentation, Organizer Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Systems Security And Risk Management Plan Meet Our Team Template PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF. Use them to share invaluable insights on Analysis Progress, Response Progress, Plan Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Tactic For Process Management For IT Roadmap Five Year Designs
We present our cyber security tactic for process management for it roadmap five year designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security tactic for process management for it roadmap five year designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. This CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
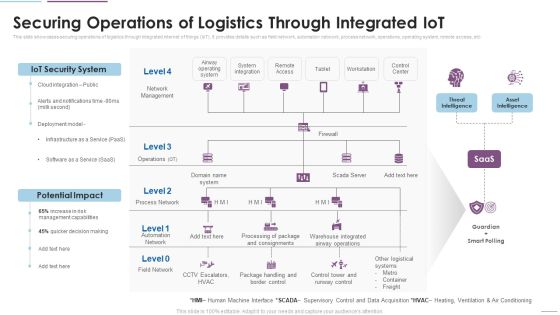
Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. This is a Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IoT Security System, Potential Impact, Network Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ways To Accomplish ISO 27001 Accreditation Current Security Management Capabilities Overview Summary PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Current Security Management Capabilities Overview Summary PDF. Use them to share invaluable insights on Core Functions, Key Enablers, Required Standard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook Senior Management Biographies And Other Details Microsoft PDF
The slide provides the name and designation of senior management teams CEO, CFO, department head etc. Of the company. It also covers brief information about their work experience, prior industry experience and education. This is a Investment Banking Security Underwriting Pitchbook Senior Management Biographies And Other Details Microsoft PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Industry Experience, Designation, Education You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
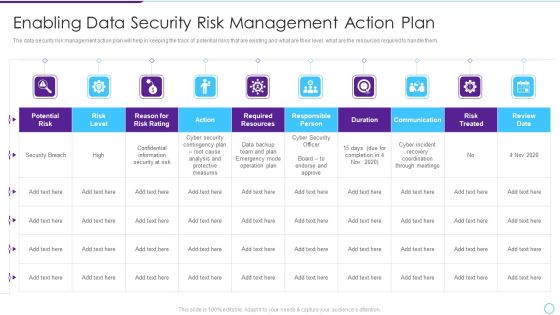
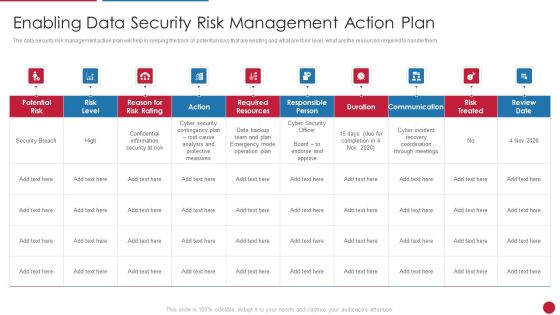
Enabling Data Security Risk Management Action Plan Ppt Slides Icon PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative enabling data security risk management action plan ppt slides icon pdf bundle. Topics like risk, security, information, measures, analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
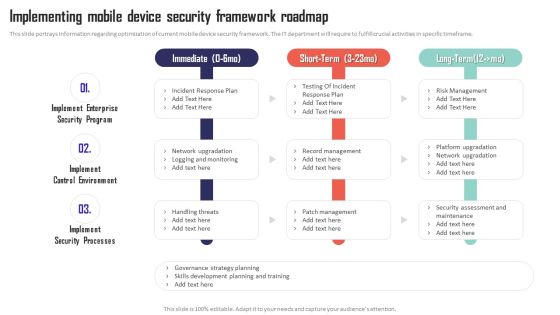
Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Get a simple yet stunning designed Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
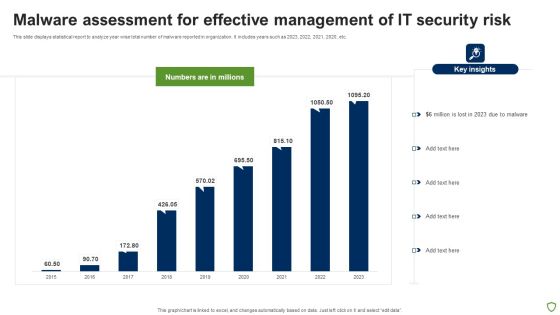
Malware Assessment For Effective Management Of IT Security Risk Portrait PDF
This slide displays statistical report to analyze year wise total number of malware reported in organization. It includes years such as 2023, 2022, 2021, 2020, etc. Showcasing this set of slides titled Malware Assessment For Effective Management Of IT Security Risk Portrait PDF. The topics addressed in these templates are Malware Assessment For Effective, Management IT Security Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Techniques And Strategies To Reduce Security Management Risks Security Detail System Maintenance And Monitoring Mockup PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. This is a techniques and strategies to reduce security management risks security detail system maintenance and monitoring mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perfective maintenance, corrective maintenance, perfective maintenance You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cios Methodologies To Improve IT Spending Cios Initiative 9 Implementing IT Risk Management Framework Themes PDF
This slide provides information regarding implementation of IT risk management framework with immediate, short term and long-term initiatives. Deliver and pitch your topic in the best possible manner with this Cios Methodologies To Improve IT Spending Cios Initiative 9 Implementing IT Risk Management Framework Themes PDF Use them to share invaluable insights on Implement Enterprise, Control Environment, Security Processes and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cios Value Optimization Cios Initiative 9 Implementing IT Risk Management Framework Summary PDF
This slide provides information regarding implementation of IT risk management framework with immediate, short term and long-term initiatives. Deliver and pitch your topic in the best possible manner with this Cios Value Optimization Cios Initiative 9 Implementing IT Risk Management Framework Summary PDF. Use them to share invaluable insights on Implement Enterprise, Security Program, Implement Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Improved Digital Expenditure Cios Initiative 9 Implementing IT Risk Management Framework Pictures PDF
This slide provides information regarding implementation of IT risk management framework with immediate, short term and long-term initiatives. Deliver and pitch your topic in the best possible manner with this Improved Digital Expenditure Cios Initiative 9 Implementing IT Risk Management Framework Pictures PDF. Use them to share invaluable insights on Implement Enterprise, Control Environment, Implement Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Evolving BI Infrastructure Enabling Data Security Risk Management Action Plan Background PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative evolving bi infrastructure enabling data security risk management action plan background pdf bundle. Topics like potential risk, risk level, action, duration, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF bundle. Topics like Potential Risk, Risk Level, Action, Risk Treated, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
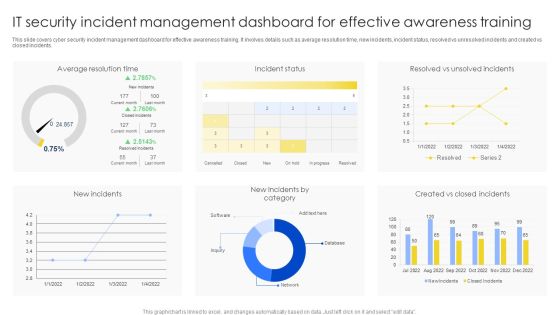
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Want to ace your presentation in front of a live audience Our Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

 Home
Home