Safety Improvement Plan

Collateral Documents Granting Security Ppt PowerPoint Presentation Summary Graphic Tips
Presenting this set of slides with name collateral documents granting security ppt powerpoint presentation summary graphic tips. This is a three stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Collateral Security Papers Icon Ppt PowerPoint Presentation Styles Background
Presenting this set of slides with name collateral security papers icon ppt powerpoint presentation styles background. This is a one stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Loan And Security Agreement Ppt PowerPoint Presentation Icon Images
Presenting this set of slides with name loan and security agreement ppt powerpoint presentation icon images. This is a one stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF
This slide depicts the risk evaluation dashboard for data privacy based on audits with open findings, GDPR processing per region, control and measure trends, average response time. There are so many reasons you need a Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

4 Strategies For Governance Risk Management And Compliance Inspiration PDF
Mentioned slide outlines key strategies which can be carry out by organization for governance, risk and compliance GRC. Appointing chief risk officer, creating risk oversight committee, building a risk culture and investing in the right technology are some of the best practices which will assist company to mitigate IT and security risks. Presenting 4 Strategies For Governance Risk Management And Compliance Inspiration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Appoint Chief, Risk Officer, Create Risk, Oversight Committee, Build Risk Culture, Invest, Technology And Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comprehensive Guide For Multi Level Impact Of Network Marketing Software On Direct Rules PDF
This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation. Create an editable Comprehensive Guide For Multi Level Impact Of Network Marketing Software On Direct Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Comprehensive Guide For Multi Level Impact Of Network Marketing Software On Direct Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cloud Computing Application Security Architecture Checklist Template PDF
The slide shows course of action for application security control and management. It includes understanding responsibility model, focusing on design andarchitect, testing, managing control, regulating and compliance needs, user training and monitoring and optimizing. Showcasing this set of slides titled Cloud Computing Application Security Architecture Checklist Template PDF. The topics addressed in these templates are Data Classification Accountability, Client Point Protection, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Implementation Framework Backup Maintenance Developing Alternate Sites Ppt PowerPoint Presentation Model Images PDF
Presenting this set of slides with name cyber security implementation framework backup maintenance developing alternate sites ppt powerpoint presentation model images pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Software Defined Networking Development Strategies Use Cases Of Software Defined Networking SDN Ideas PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Software Defined Networking Development Strategies Use Cases Of Software Defined Networking SDN Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Software Defined Networking Development Strategies Use Cases Of Software Defined Networking SDN Ideas PDF today and make your presentation stand out from the rest.

KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
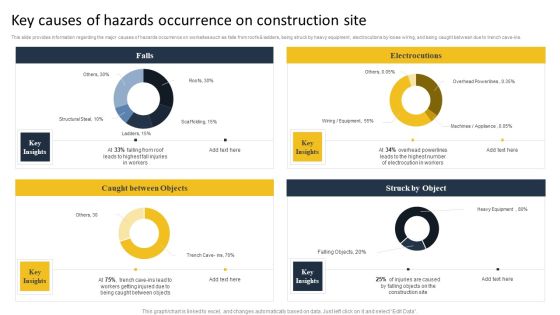
Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF
This slide provides information regarding the major causes of hazards occurrence on worksites such as falls from roofs AND ladders, being struck by heavy equipment, electrocutions by loose wiring, and being caught between due to trench cave-ins. Find a pre designed and impeccable Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for. Download the template from Slidegeeks today and give a unique touch to your presentation.

Artificial Intelligence Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Deliver an awe inspiring pitch with this creative artificial intelligence playbook stage five security breach readiness checklist topics pdf bundle. Topics like questions related, security breach readiness, each organizational procedure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF
This slide depicts the real-world applications of the metaverse, including in-game assets, self-identity authentication, an incentive for creators, and control over real estate assets by blockchain. Deliver an awe inspiring pitch with this creative Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF bundle. Topics like Avoiding Fraud, Avatars Identities, Securely Retain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Implementation Framework Dashboard Ppt Gallery Template PDF
Presenting this set of slides with name cyber security implementation framework dashboard ppt gallery template pdf. This is a three stage process. The stages in this process are minimum, medium, maximum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Financial Ppt Slides Good PDF
Presenting this set of slides with name cyber security implementation framework financial ppt slides good pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
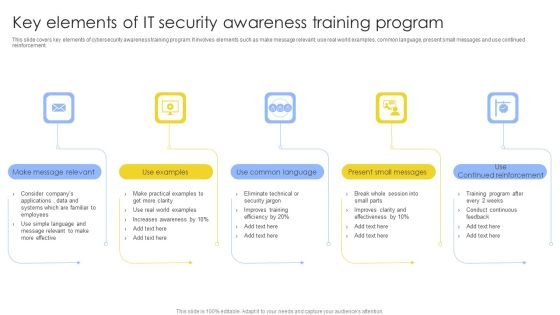
Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF
This slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Presenting Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Make Message Relevant, Use Examples, Use Common Language. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Control Techniques For Real Estate Project Solution To Overcome Construction Site Poor Guidelines PDF
Present like a pro with Security Control Techniques For Real Estate Project Solution To Overcome Construction Site Poor Guidelines PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Different Categories Of Data Centers Types Of Data Centers Colocation Data Centers Topics PDF
This slide shows the one from different types of data centers that is colocation data centers that provide services to organizations, including cooling, bandwidth, and security. Take your projects to the next level with our ultimate collection of Different Categories Of Data Centers Types Of Data Centers Colocation Data Centers Topics PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
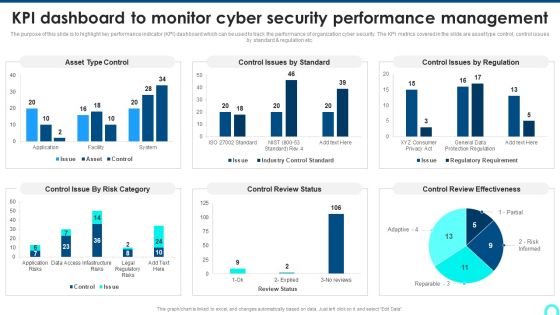
KPI Dashboard To Monitor Cyber Security Performance Management Background PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc.Deliver and pitch your topic in the best possible manner with this KPI Dashboard To Monitor Cyber Security Performance Management Background PDF. Use them to share invaluable insights on Control Issue, Control Review, Review Effectiveness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Key Security Controls To Be Addressed In The Program Ppt Infographics Samples PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Presenting handling cyber threats digital era key security controls to be addressed in the program ppt infographics samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prevents attacks, limits extent of attacks, data recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deployment Of Omnichannel Banking Solutions Introduction To Branchless Banking In Next Generation Diagrams PDF
This slide covers introduction to branchless banking services offered by banking sector. The purpose of this template is to provide an overview on benefits of using branchless banking services. It includes advantages such as supporting multiple transactions, advanced payment security, contactless payment solutions along with categories covering digital wallets, IVR bill payments, API bill payments and credit card bills. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deployment Of Omnichannel Banking Solutions Introduction To Branchless Banking In Next Generation Diagrams PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cyber Security Threat Dashboard With KPI Metrics Icons PDF
This slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Showcasing this set of slides titled Cyber Security Threat Dashboard With KPI Metrics Icons PDF. The topics addressed in these templates are Cyber Security Threat Dashboard, Kpi Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Implementation Framework Amount Spent On Cyber Fraud Settlements Ppt PowerPoint Presentation Summary Introduction PDF
Presenting this set of slides with name cyber security implementation framework amount spent on cyber fraud settlements ppt powerpoint presentation summary introduction pdf. This is a one stage process. The stages in this process are focus areas, settlements, amount, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Budget For Effective Cybersecurity Management Ppt PowerPoint Presentation Layouts Vector PDF
Presenting this set of slides with name cyber security implementation framework budget for effective cybersecurity management ppt powerpoint presentation layouts vector pdf. This is a one stage process. The stages in this process are functional area, software, implement duration, cost implementation, incident management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Risk Assessment Matrix Ppt PowerPoint Presentation Visual Aids Backgrounds PDF
Presenting this set of slides with name cyber security implementation framework risk assessment matrix ppt powerpoint presentation visual aids backgrounds pdf. This is a one stage process. The stages in this process are insignificant, minor, catastrophic, serious. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, iot-based attack, malware etc. Do you know about Slidesgeeks Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
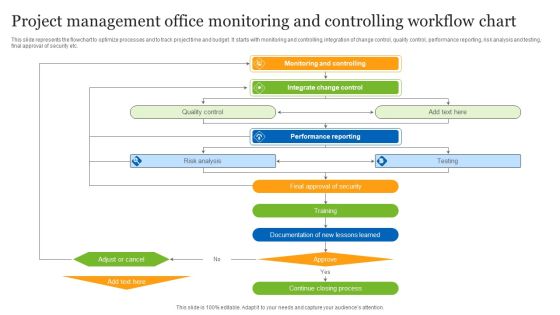
Project Management Office Monitoring And Controlling Workflow Chart Ppt Slides Mockup PDF
This slide represents the flowchart to optimize processes and to track project time and budget. It starts with monitoring and controlling, integration of change control, quality control, performance reporting, risk analysis and testing, final approval of security etc. Presenting Project Management Office Monitoring And Controlling Workflow Chart Ppt Slides Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Monitoring And Controlling, Integrate Change Control, Performance Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF can be your best option for delivering a presentation. Represent everything in detail using Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF bundle. Topics like Consumers, Implements Applications, Outlines Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
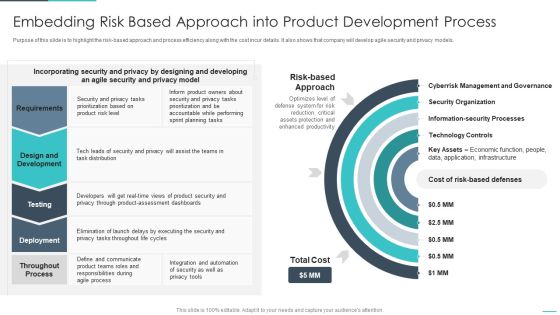
Handling Cyber Threats Digital Era Embedding Risk Based Approach Into Product Ppt Gallery Designs PDF
Purpose of this slide is to highlight the risk-based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative handling cyber threats digital era embedding risk based approach into product ppt gallery designs pdf bundle. Topics like embedding risk based approach into product development process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Optimizing Digital Marketing Strategy Create Effective And Privacy Safe Marketing Actions Diagrams PDF
This template covers techniques companies can follow to ensure secure and effective marketing efforts. It includes approaches such as making marketing actions memorable, meaningful, and manageable. Slidegeeks is here to make your presentations a breeze with Optimizing Digital Marketing Strategy Create Effective And Privacy Safe Marketing Actions Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Developing Business Analytics Framework Timeframe For Incident Management In Security Centre Demonstration PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this Developing Business Analytics Framework Timeframe For Incident Management In Security Centre Demonstration PDF Use them to share invaluable insights on Incident Categorization, Incident Prioritization, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Operations Certifications And Training Courses For IT Professionals Topics PDF
This slide exhibits training courses for security operations administrators to enhance their cyber threat management skills. It includes elements such as course, course outline, rating, pricing, frequency, and mode of training. Showcasing this set of slides titled Security Operations Certifications And Training Courses For IT Professionals Topics PDF. The topics addressed in these templates are Security Operations, Fundamental, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Confidential Computing System Technology Confidential Computing Use Cases And Ecosystem Demonstration PDF
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Retrieve professionally designed Confidential Computing System Technology Confidential Computing Use Cases And Ecosystem Demonstration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Consultancy Services Company Profile Our Management Team Topics PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting IT Consultancy Services Company Profile Our Management Team Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Operational Leadership, Corporate Decisions, Organize Meetings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
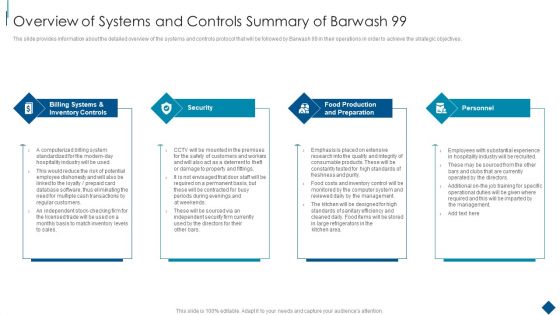
Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Billing Systems Inventory, Controls Security Personnel, Food Production Preparation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Lake Architecture How To Decide If You Need A Data Lake Information PDF
This slide depicts the key pointers to help to understand organizations if they need to maintain a data lake for critical business information and perform analytics on that data. Deliver an awe inspiring pitch with this creative Data Lake Architecture How To Decide If You Need A Data Lake Information PDF bundle. Topics like Make Data Administration Easier, Accelerate Analytics, Enhance Security And Governance, Businesses Depend can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF
This slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
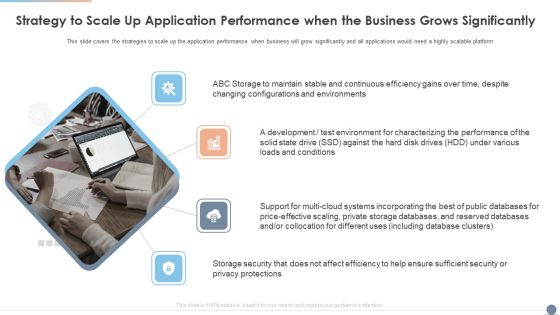
Strategy To Scale Up Application Performance When The Business Grows Significantly Designs PDF
This slide covers the strategies to scale up the application performance when business will grow significantly and all applications would need a highly scalable platform. This is a Strategy To Scale Up Application Performance When The Business Grows Significantly Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Environments, Development, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF.

Post Implementation Challenges And Risks Of Saas Program Ppt PowerPoint Presentation File Graphics PDF
The following slide highlights the post implementation challenges and risks of SaaS platform illustrating key headings which includes control issues, version control, hard to switch and security issues. Presenting post implementation challenges and risks of saas program ppt powerpoint presentation file graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including control issues, version controls, hard to switch, security issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Cloud Based Email Security Market Table Of Contents Formats PDF
Presenting this set of slides with name global cloud based email security market table of contents formats pdf. This is a eight stage process. The stages in this process are market introduction, market dynamics, market by segments, market competition analysis, market forecasting and projections, issues faced by companies, porter 5 force model. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.

Critical Violations Security Dashboard With KPI Metrics Graphics PDF
This slide shows dashboard of security to mitigate violation by prioritizing KPIs. It includes application control, operating systems, restrict admin privileges, multi factor authentication and backup of important data. Showcasing this set of slides titled Critical Violations Security Dashboard With KPI Metrics Graphics PDF. The topics addressed in these templates are Risk Model, Application Components, Technologies Overview. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Charts For Portfolio Evaluation Techniques Example Ppt Presentation
This is a charts for portfolio evaluation techniques example ppt presentation. This is a five stage process. The stages in this process are peso govt debt securities, foreign govt debt securities, peso corporate debt securities, dollar corporate debt securities, equity.

International Security Market Highlights Ppt PowerPoint Presentation File Graphics Example
This is a international security market highlights ppt powerpoint presentation file graphics example. This is a three stage process. The stages in this process are location, information, geography, management, strategy.

International Security Market Highlights Ppt PowerPoint Presentation Professional Model
This is a international security market highlights ppt powerpoint presentation professional model. This is a three stage process. The stages in this process are location, information, geography, management, strategy.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Checklist Of Security Risk Analysis Vector Icon Ppt PowerPoint Presentation File Elements PDF
Persuade your audience using this checklist of security risk analysis vector icon ppt powerpoint presentation file elements pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including checklist of security risk analysis vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Audit System Events Ppt PowerPoint Presentation Tips
This is a audit system events ppt powerpoint presentation tips. This is a five stage process. The stages in this process are windows settings, local policies, computer configuration, security settings, audit policy.
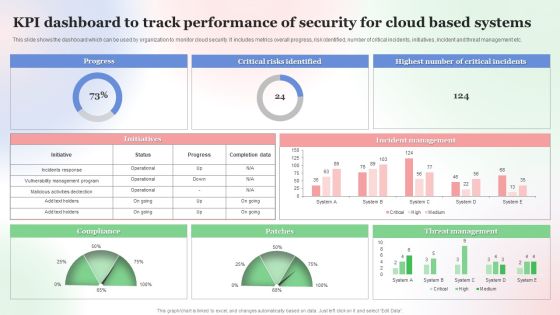
KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Secured Digital Currency Transaction Half Yearly Roadmap Portrait
Introducing our secured digital currency transaction half yearly roadmap portrait. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Five Year Data Sharing Security Network Career Roadmap Clipart
Introducing our five year data sharing security network career roadmap clipart. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

 Home
Home