Safety Improvement Plan
Three Key Points With Text Holders Ppt PowerPoint Presentation Show Format
Presenting this set of slides with name three key points with text holders ppt powerpoint presentation show format. This is a three stage process. The stages in this process are key considerations, business, growth strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
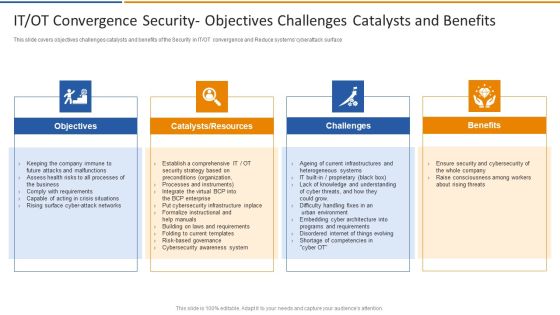
IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts, Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. This is a Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Case Undersubscription, Interested Investors, Normal Subscription You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
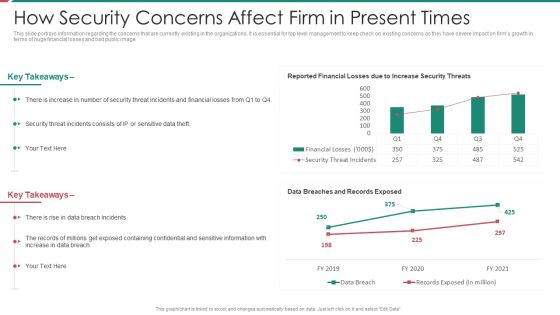
Security And Process Integration How Security Concerns Affect Firm In Present Times Microsoft PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative security and process integration how security concerns affect firm in present times microsoft pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Categories Of Load Balancer What Kind Of Traffic Can Load Balancers Handle Ideas PDF
This slide describes the kinds of traffic that a load balancer can handle such as hypertext transfer protocol, hypertext transfer protocol secure, transmission control protocol and user datagram protocol. Presenting categories of load balancer what kind of traffic can load balancers handle ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like some load balancers have recently introduced functionality, https balancing is similar to http balancing, requests are routed using normal http methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Governance Risk Management And Compliance Services Overview Introduction PDF
Mentioned slide outlines various governance, risk and compliance GRC services offered by third party to a company. The key services mentioned in the slide are vulnerability response, risk management, security incident response, internal audit management, compliance management etc. Presenting Governance Risk Management And Compliance Services Overview Introduction PDF to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including Threat Detection, Risk Management, Security Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Strategies To Mitigate Cyber Security Risks Dashboard Incident Tracking Ppt Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard incident tracking ppt model pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, disable untrusted microsoft office macros, user application hardening, multi factor authentication, daily backup important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Control Techniques For Real Estate Project Workers Injuries Incurred At Construction Site Infographics PDF
Find highly impressive Security Control Techniques For Real Estate Project Workers Injuries Incurred At Construction Site Infographics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Control Techniques For Real Estate Project Workers Injuries Incurred At Construction Site Infographics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cyber Security Implementation Framework Critical Business Functions Recovery Priorities Elements PDF
Presenting this set of slides with name cyber security implementation framework critical business functions recovery priorities elements pdf. This is a one stage process. The stages in this process are department, priorities, maximum allowable downtime, critical. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Information Technology Security Awareness Training For Staff Ppt Slide PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Presenting it security information technology security awareness training for staff ppt slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like senior executives, developers, front line staff, it teams, project managers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Security Information security Awareness Training For Staff Ppt PowerPoint Presentation Gallery Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this info security information security awareness training for staff ppt powerpoint presentation gallery template pdf. Use them to share invaluable insights on senior executives, project managers, it teams, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Savings And Investment For House Real Estate PowerPoint Templates And PowerPoint Themes 1112
Savings And Investment For House Real Estate PowerPoint Templates And PowerPoint Themes 1112-Use our Money PowerPoint Templates because; demonstrate how you think out of the box. Use our Security PowerPoint Templates because, to achieve sure shot success they need to come together at the right time, place and manner. Use our Success PowerPoint Templates because; Get your listeners to put on their thinking caps. Use our Business PowerPoint Templates because; Draw on its universal impact to highlight the similarities with your organizational structure and plan. Use our Future PowerPoint Templates because, our template will help pinpoint their viability.-Savings And Investment For House Real Estate PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Savings and investment, Money, Real estate, Finance, Future, Sales

KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Want to ace your presentation in front of a live audience Our KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

IT Security Half Yearly Strategic Timeline Diagrams
Introducing our it security half yearly strategic timeline diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Security Strategic Half Yearly Functional Timeline Designs
Introducing our security strategic half yearly functional timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Integrating Data Privacy System Five Data Privacy Rules Ppt Outline Show PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integrating Data Privacy System Five Data Privacy Rules Ppt Outline Show PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Project Context For Partnership Proposal Ppt PowerPoint Presentation Professional Backgrounds
Presenting this set of slides with name project context for partnership proposal ppt powerpoint presentation professional backgrounds. This is a five stage process. The stages in this process are specialized, development, services, business, it infrastructure, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Cover Letter For Company Online Database Security Proposal Designs PDF
Presenting this set of slides with name best data security software cover letter for company online database security proposal designs pdf. This is a one stage process. The stages in this process are cover letter, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IP Addressing Scheme Summary For Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary IP Addressing Scheme Summary For Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this IP Addressing Scheme Summary For Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.

Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Create an editable Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Impact Of Employing Digital Payments Strategy In Events And Venues Ppt Styles Layout Ideas PDF
This slide showcases the benefits of using cashless payments for events and venues to ensure better management. It includes benefits such as revenue growth, queue reduction, security, sales insight and vendor management etc. Presenting Impact Of Employing Digital Payments Strategy In Events And Venues Ppt Styles Layout Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Revenue Growth, Queues Reduction, Safe And Secure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
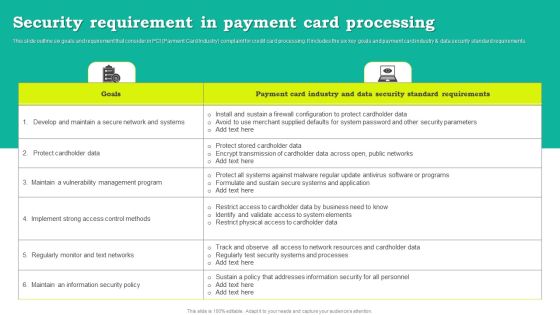
Security Requirement In Payment Card Processing Download PDF
This slide outline six goals and requirement that consider in PCI Payment Card Industry complaint for credit card processing. It includes the six key goals and payment card industry and data security standard requirements. Showcasing this set of slides titled Security Requirement In Payment Card Processing Download PDF. The topics addressed in these templates are Goals, Payment Card Industry, Data Security Standard Requirements. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
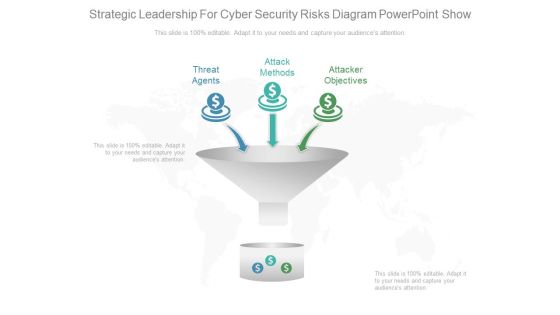
Strategic Leadership For Cyber Security Risks Diagram Powerpoint Show
This is a strategic leadership for cyber security risks diagram powerpoint show. This is a three stage process. The stages in this process are threat agents, attack methods, attacker objectives.
Information Security Compliance Dashboard Of Data Security Ppt Icon Vector PDF
This slide depicts the data security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative information security compliance dashboard of data security ppt icon vector pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
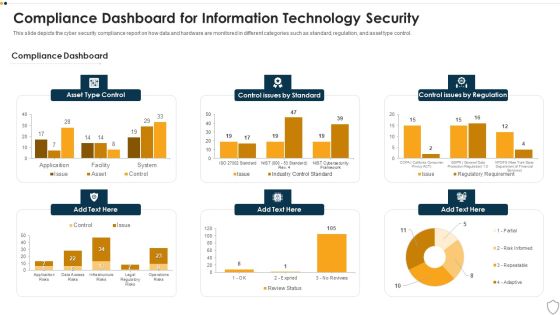
IT Security Compliance Dashboard For Information Technology Security Ppt Slides Brochure PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative it security compliance dashboard for information technology security ppt slides brochure pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Website Programming IT Benefits Of Content Management System In Web Technology Formats PDF
This slide represents the benefits of using a Content Management System in the organization, and it provides features such as on-page SEO, teams collaboration, template making, security, and analytics. This is a website programming it benefits of content management system in web technology formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like seo, collaboration, templates, security, analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5 Kpis To Monitor And Track Network Service Assessment Information PDF
Mentioned slide outlines various kpis which can be used by IT reps to monitor network performance. The kpis mentioned in the template are latency, network jitter, packet loss, throughput and mean opinion score. It also covers information about objective, strategies implemented and actual performance of each kpis. Showcasing this set of slides titled 5 Kpis To Monitor And Track Network Service Assessment Information PDF. The topics addressed in these templates are Strategies Implemented, Network Security, Quality. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Risk Assessment On Effective IT Service Excellence Designs PDF
This slide signifies the bar graph comparison on growth and benefits provided by IT services. It includes various assistance like cost control, cyber security risk, data analytics and anti virus protection. Showcasing this set of slides titled Comparative Risk Assessment On Effective IT Service Excellence Designs PDF. The topics addressed in these templates are Software Management, Incident Management, Release Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Impact On Organization After Implementing Information Security Strategy Ppt PowerPoint Presentation Gallery Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information security strategy ppt powerpoint presentation gallery deck pdf. Use them to share invaluable insights on system misconfiguration, phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Standing Out From Crowd Business PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Standing Out From Crowd Business PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Use our Business PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download and present our Signs PowerPoint Templates because You have a driving passion to excel in your field. Our PowerPoint Templates and Slides will prove ideal vehicles for your ideas. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process.Use these PowerPoint slides for presentations relating to Stand out of a crowd, business, umbrellas, marketing, signs, security. The prominent colors used in the PowerPoint template are Red, Gray, Black. We assure you our Standing Out From Crowd Business PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our umbrellas PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Presenters tell us our Standing Out From Crowd Business PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Professionals tell us our of PowerPoint templates and PPT Slides are designed by a team of presentation professionals. The feedback we get is that our Standing Out From Crowd Business PowerPoint Templates PPT Backgrounds For Slides 0113 will help you be quick off the draw. Just enter your specific text and see your points hit home. PowerPoint presentation experts tell us our of PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words.

Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF
This slide provides information regarding ITIL process areas in terms of service strategy and service design and associated sequential activities. Deliver an awe inspiring pitch with this creative Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF bundle. Topics like Sequential Activities Processes, Strategy Management Execution, Sequential Activities Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF. Use them to share invaluable insights on Revenue Increased, Increased In Last, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Dashboard For Threat Tracking In IT Security IT Ppt Outline Examples PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative dashboard for threat tracking in it security it ppt outline examples pdf bundle. Topics like monthly threat status, threats by owners, risk by threats, current risk status, threats based on role, threat report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Strategy Role Of Chief Information Security Officer Rules PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. This is a information technology strategy role of chief information security officer rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information, stay informed, monthly reports. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
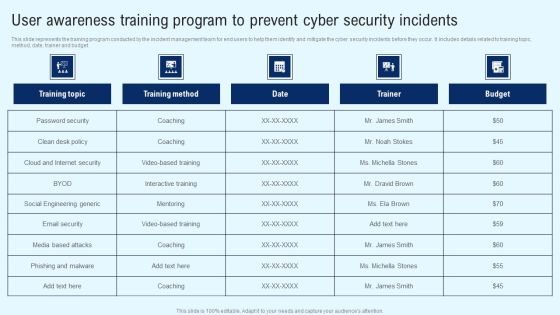
Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Information Technology Job Progression Matrix With Functions Graphics PDF
This slide presents IT career matrix that highlights departmental roles and their required certifications, helpful in determining their importance for organisations. It includes departments such as systems and infrastructure, network security and software development. Showcasing this set of slides titled Information Technology Job Progression Matrix With Functions Graphics PDF. The topics addressed in these templates are Systems And Infrastructure, Network Security, Software Development. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating.Presenting Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Customer Database, Product Database, Sales Records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Business Diagram Folders In Circular Flow Presentation Template
Our above slide contains graphics of data folders in circular flow. It helps to display concepts like data storage and exchange of information. Use this diagram to impart more clarity to data and to create more sound impact on viewers.

Cyber Security Tools And Techniques Ppt PowerPoint Presentation Styles Vector
Presenting this set of slides with name cyber security tools and techniques ppt powerpoint presentation styles vector. This is a eight stage process. The stages in this process are fairly and lawfully processed, processed for limited purposes, adequate, relevant and not excessive, accurate and up to data, not kept for longer than necessary, processed in line with data subjects rights, secure, protected in international transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
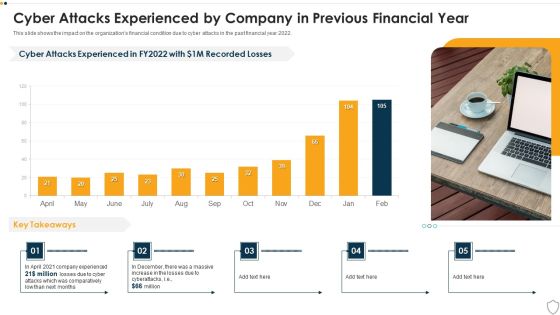
IT Security Cyber Attacks Experienced By Company In Previous Financial Year Ppt Outline Gallery PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver and pitch your topic in the best possible manner with this it security cyber attacks experienced by company in previous financial year ppt outline gallery pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
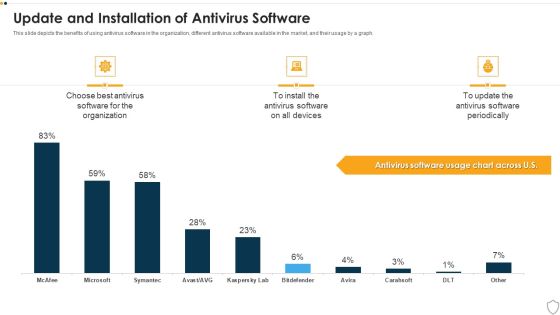
IT Security Update And Installation Of Antivirus Software Ppt Outline Sample PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this it security update and installation of antivirus software ppt outline sample pdf. Use them to share invaluable insights on update and installation of antivirus software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Best Practices Cloud Computing Security IT Ppt Portfolio Master Slide PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an awe inspiring pitch with this creative cloud security best practices cloud computing security it ppt portfolio master slide pdf bundle. Topics like cloud protection, cloud utilization and risk, authentication process, security policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Years Workplace Security Recognition Training Program Roadmap Diagrams
Presenting our jaw-dropping five years workplace security recognition training program roadmap diagrams. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Quarterly Workplace Security Recognition Training Program Roadmap Mockup
Presenting our jaw-dropping quarterly workplace security recognition training program roadmap mockup. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Six Months Workplace Security Recognition Training Program Roadmap Slides
Presenting our jaw-dropping six months workplace security recognition training program roadmap slides. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
Three Months Workplace Security Recognition Training Program Roadmap Microsoft
Presenting our jaw-dropping three months workplace security recognition training program roadmap microsoft. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IPO Process Layout For Network Security Issues Ppt PowerPoint Presentation Outline Graphics Template PDF
Persuade your audience using this ipo process layout for network security issues ppt powerpoint presentation outline graphics template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including processing, output, input. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. There are so many reasons you need a IT Risk Management Framework To Manage Security Threats Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

 Home
Home