Information Security Program
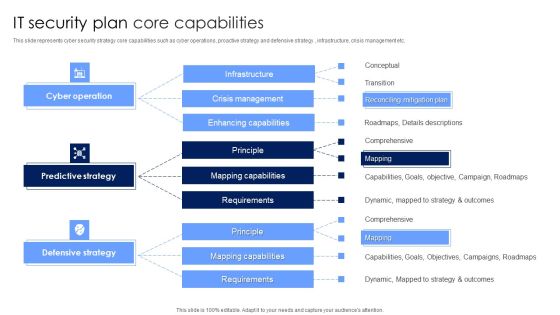
IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
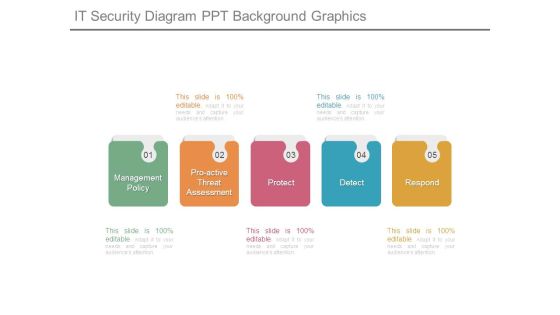
It Security Diagram Ppt Background Graphics
This is a it security diagram ppt background graphics. This is a five stage process. The stages in this process are management policy, proactive threat assessment, protect, detect, respond.
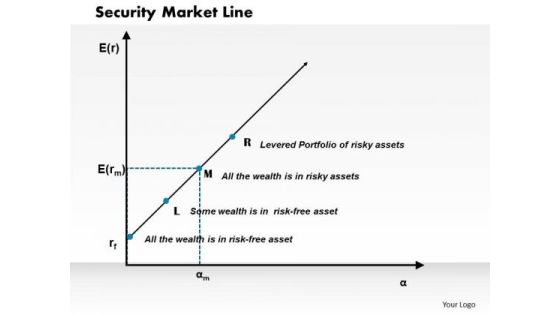
Business Framework Security Market Line PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

Internet Security Incident Analysis Report Template PDF
This slide exhibits security data breach incident report. It includes multiple steps such as- report the number of personal data record lost, analyze the possible effects of personal data breaches and so on. Showcasing this set of slides titled internet security incident analysis report template pdf. The topics addressed in these templates are data breach details, consequences, measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
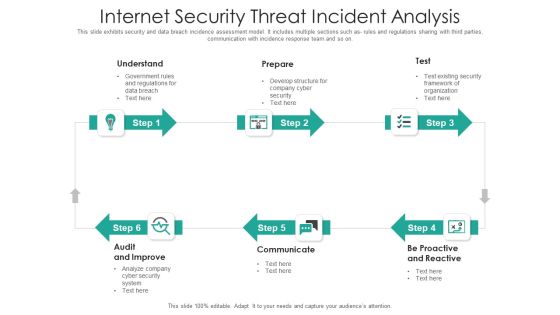
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
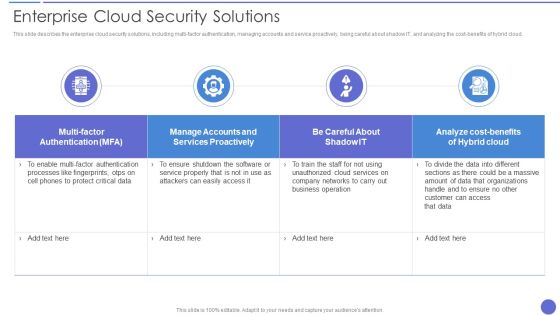
Enterprise Cloud Security Solutions Professional PDF
This slide describes the enterprise cloud security solutions, including multi factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost benefits of hybrid cloud. Deliver an awe inspiring pitch with this creative Enterprise Cloud Security Solutions Professional PDF bundle. Topics like Services Proactively, Analyze Cost Benefits, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Encryption Ppt PowerPoint Presentation Layouts Cpb
Presenting this set of slides with name security encryption ppt powerpoint presentation layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like security encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
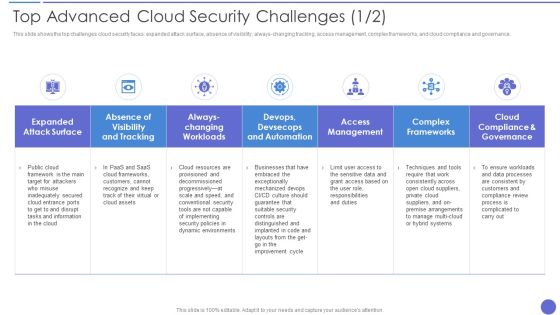
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
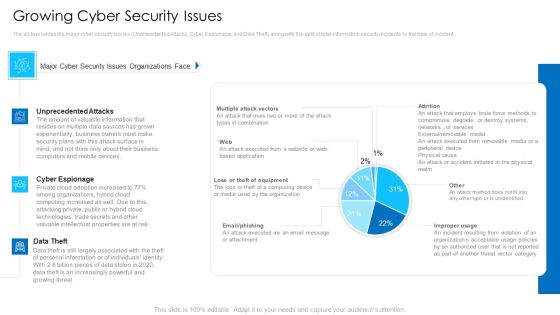
Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Growing Cyber Security Issues Portrait PDF
Deliver and pitch your topic in the best possible manner with this growing cyber security issues portrait pdf. Use them to share invaluable insights on unprecedented attacks, cyber espionage, data theft and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Five Years Strategic Timeline Icons
We present our it security five years strategic timeline icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched it security five years strategic timeline icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Icons Slide For IT Security Designs PDF
Download our innovative and attention grabbing icons slide for it security designs pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Cyber Security Network Development Timeline Download PDF
The following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice. Presenting Cyber Security Network Development Timeline Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Establish, Analyse, Practice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Five Year Strategic Timeline Demonstration
We present our cyber security five year strategic timeline demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security five year strategic timeline demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Strategic Five Year Functional Timeline Graphics
We present our security strategic five year functional timeline graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched security strategic five year functional timeline graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Initiatives Protecting Recruitment Process Elements PDF
This slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Slidegeeks is here to make your presentations a breeze with Security Initiatives Protecting Recruitment Process Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Security Incident Handling Checklist Elements PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Take your projects to the next level with our ultimate collection of Cyber Security Incident Handling Checklist Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Organizational Security Solutions Quotes Ppt Model PDF
Deliver an awe inspiring pitch with this creative organizational security solutions quotes ppt model pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Half Yearly Strategic Timeline Diagrams
Introducing our it security half yearly strategic timeline diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
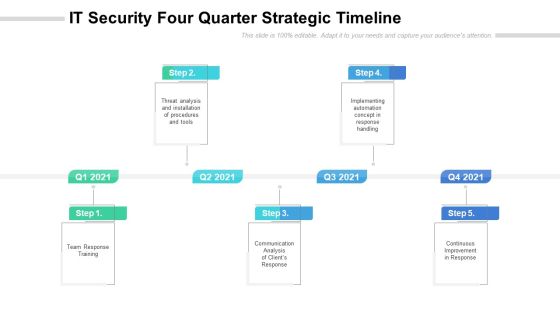
IT Security Four Quarter Strategic Timeline Slides
Presenting our innovatively structured it security four quarter strategic timeline slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

IT Security Three Months Strategic Timeline Portrait
Presenting our jaw dropping it security three months strategic timeline portrait. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
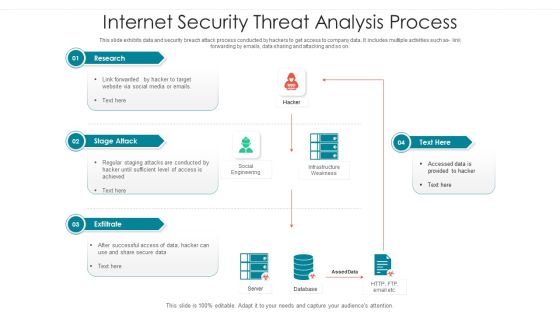
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
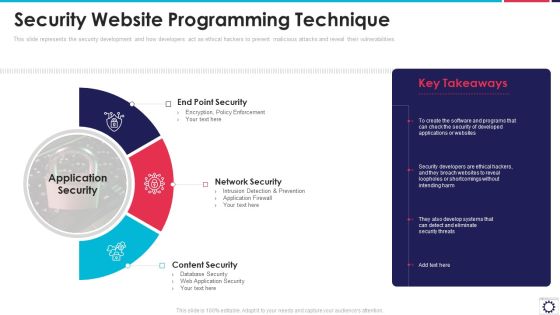
Website Programming IT Security Website Programming Technique Ppt PowerPoint Presentation File Infographics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Presenting website programming it security website programming technique ppt powerpoint presentation file infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like end point security, network security, content security, application security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
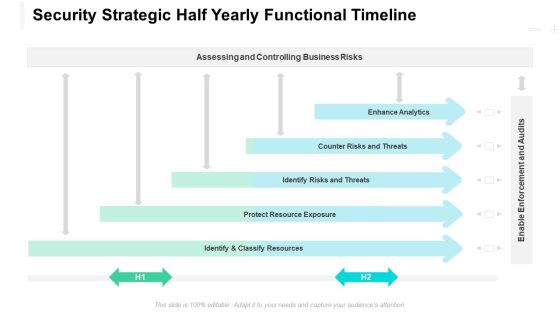
Security Strategic Half Yearly Functional Timeline Designs
Introducing our security strategic half yearly functional timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Half Yearly Strategic Timeline Icons
Presenting our innovatively structured cyber security half yearly strategic timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Security Strategic Four Quarter Functional Timeline Icons
Presenting our innovatively structured security strategic four quarter functional timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Incident Response Lifecycle Diagrams PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Incident Response Lifecycle Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

IT Security Six Months Strategic Timeline Portrait
Presenting the it security six months strategic timeline portrait. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Security Strategic Six Months Functional Timeline Clipart
Presenting the security strategic six months functional timeline clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Computer Security Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this Computer Security Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Model Business PowerPoint Templates Security Plan Slides
We present our model business powerpoint templates security plan Slides.Download our Marketing PowerPoint Templates because you should Experience excellence with our PowerPoint Templates and Slides. They will take your breath away. Download our Circle Charts PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Download our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download and present our Business PowerPoint Templates because It will get your audience in sync. Download and present our Shapes PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown.Use these PowerPoint slides for presentations relating to arrow, blue, chart, chevron, circle, circular, diagram, graphic, green, hub, icon, illustration, isometric, pie, pieces, process, purple, red, round, set, slices, stages, vector, wheel, yellow. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.

Sold Personal Data Security PowerPoint Template 0910
3d illustration of a red Sold sticker with curled ends stuck to a large orange fingerprint on a red surface

Binary Internet Security PowerPoint Template 1110
Graphic depicting binary data escaping through a keyhole

Digital Files Security PowerPoint Template 1110
3d illustration of transparent binary and html data revolving around an open file folder

IT Security Ppt PowerPoint Presentation Complete Deck
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty one slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Poste It Notes Clipart PDF
This is a Executing security management program to mitigate threats and safeguard confidential organizational data poste it notes clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poste it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data 30 60 90 Days Plan Brochure PDF
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data 30 60 90 days plan brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Ppt PowerPoint Presentation Complete Deck
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourtytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Certified Data Professional Program Collection Of Information Technology Certifications Mockup PDF
This slide covers the CDP course details such as CDP Benefits, Who should become CDP, salary expectations, International Standards for CDP Program etc. This is a certified data professional program collection of information technology certifications mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security requirements, information system, benefits, strategic, Risk assessment . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security IT Security Awareness Training For Staff Ppt Styles Infographic Template PDF
This slide represents the network security awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this information technology security awareness training for staff ppt slides guidelines pdf. Use them to share invaluable insights on information technology security awareness training for staff and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. This is a Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Provide Safe Environment, Safeguard Environment, Campus Patrolling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Tools Used In Cloud Security Cloud Computing Security IT Ppt Background Images PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a tools used in cloud security cloud computing security it ppt background images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like silver sky, centrify, doc tracker, proofpoint, whitehat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Computer Security Awareness Training For Staff Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative desktop security management computer security awareness training for staff template pdf bundle. Topics like project managers, developers, senior executives, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Safety Escort Service, Executive Protection, Special Event Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Find highly impressive Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
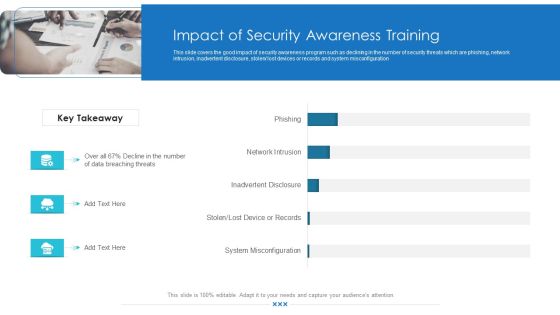
Workforce Security Realization Coaching Plan Impact Of Security Awareness Training Pictures PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan impact of security awareness training pictures pdf bundle. Topics like impact of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home