Information Security Program

Agenda For Cloud Data Security Ideas PDF
This is a Agenda For Cloud Data Security Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Responsibilities And Service, Organizations, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Hybrid Cloud Security Solutions Rules PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy This is a Hybrid Cloud Security Solutions Rules PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Redundancy, Categorization Of Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Malware Attacks Sample PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Security Threats Malware Attacks Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technology, Targets, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
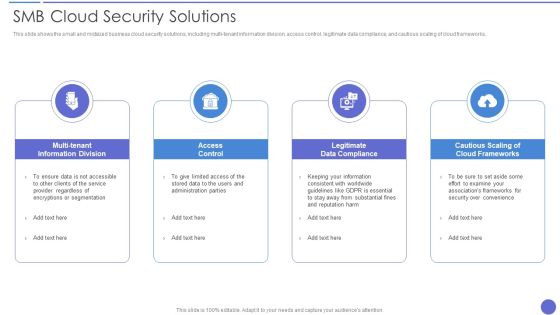
Smb Cloud Security Solutions Download PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. This is a Smb Cloud Security Solutions Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Legitimate Data Compliance, Cloud Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system. This is a What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Developing, Essential Strategy, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
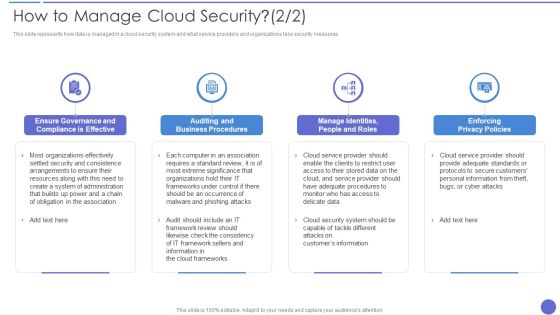
How To Manage Cloud Security Topics PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. This is a How To Manage Cloud Security Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enforcing Privacy Policies, Auditing And Business Procedures, Organizations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
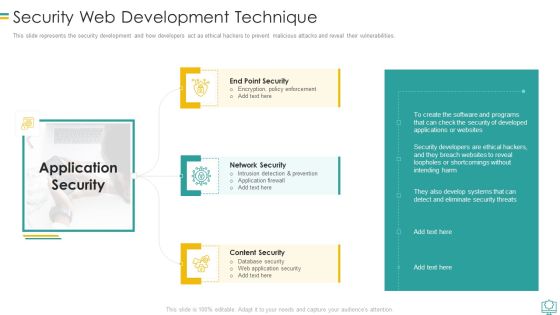
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
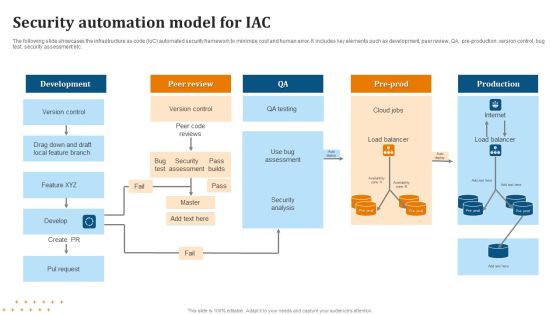
Security Automation Model For IAC Summary PDF
Pitch your topic with ease and precision using this Security Automation Model For IAC Summary PDF. This layout presents information on Security Automation, Model For IAC . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

How Does Cloud Security Work Download PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a How Does Cloud Security Work Download PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Encryption Methods, Secure Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Data Encryption Professional PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Presenting Cloud Security Checklist Data Encryption Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protect Keys, Encrypted Data, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Shared Vulnerabilities Graphics PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. This is a Cloud Security Threats Shared Vulnerabilities Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Could, Organizations, Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
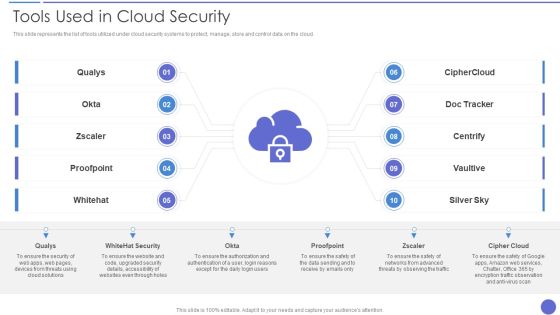
Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Compliance Violations Demonstration PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state. This is a Cloud Security Threats Compliance Violations Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Businesses, Organizations, Authentication Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
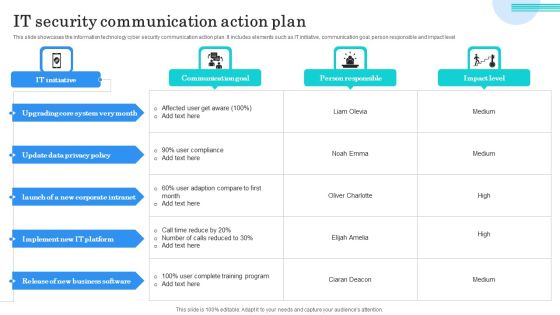
IT Security Communication Action Plan Portrait PDF
This slide showcases the information technology cyber security communication action plan. It includes elements such as IT initiative, communication goal, person responsible and impact level. Showcasing this set of slides titled IT Security Communication Action Plan Portrait PDF. The topics addressed in these templates are Upgrading Core System, Update Data Privacy, Implement IT Platform. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Cloud Security Assessment Infographics PDF
Presenting Agenda For Cloud Security Assessment Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
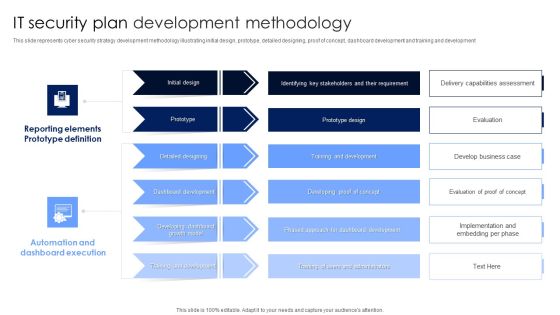
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
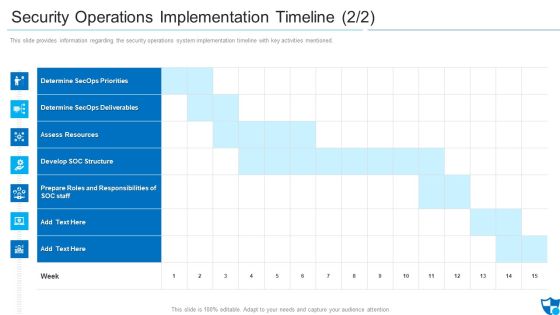
Security Operations Implementation Timeline Assess Diagrams PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned.Deliver and pitch your topic in the best possible manner with this security operations implementation timeline assess diagrams pdf. Use them to share invaluable insights on determine secops priorities, determine secops deliverables, assess resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
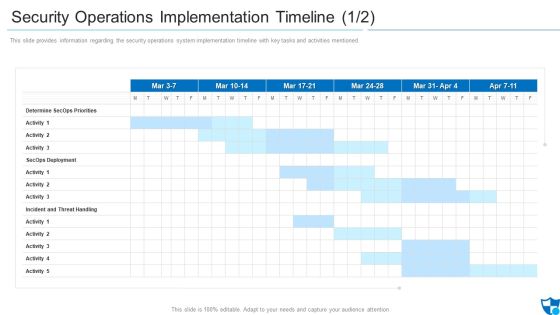
Security Operations Implementation Timeline Priorities Introduction PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned.Deliver an awe inspiring pitch with this creative security operations implementation timeline priorities introduction pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
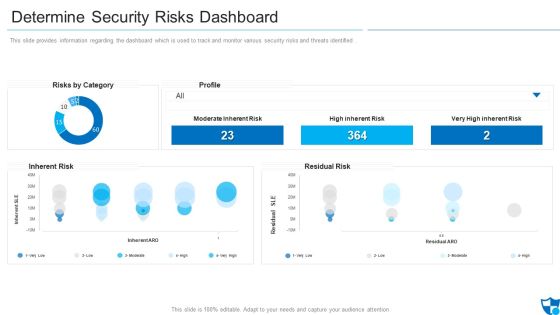
Determine Security Risks Dashboard Introduction PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified.Deliver and pitch your topic in the best possible manner with this determine security risks dashboard introduction pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management System Microsoft PDF
The following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Pitch your topic with ease and precision using this cyber security risk management system microsoft pdf. This layout presents information on mapping threats, threat containment and remediation, identify management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Digital Transformation Purpose Sample PDF
The slide shows a modern security transformation agenda for securing business with advanced information security. It also highlights vision, strategies and service lines of technology advancement. Persuade your audience using this Cyber Security Digital Transformation Purpose Sample PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Agenda, Vision, Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Segmentation Of Cloud Security Responsibilities Icons PDF
This slide shows cloud security responsibilities based on service type, namely Software as a Service SaaS, Platform as a service PaaS, Infrastructure as a Service IaaS. Presenting Segmentation Of Cloud Security Responsibilities Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cloud Security Responsibilities, Segmentation, Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Networking Elements PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting Cloud Security Checklist Networking Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Network, Encrypt Critical Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Threats Revenue Losses Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Security Threats Revenue Losses Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organizations, Revenue, Investing Money. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Risks Or Threats Brochure PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Security Risks Or Threats Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Malware Attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Employee Security Awareness Training Budget Sample PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status Presenting employee security awareness training budget sample pdf. to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like build and maintain a secure network and systems, protect cardholder data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Web Acceleration Security Software Example Of Ppt
This is a web acceleration security software example of ppt. This is a four stage process. The stages in this process are web acceleration, security software, shopping carts, data services.

Data Storage Security Management Icon Professional PDF
Presenting Data Storage Security Management Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Storage, Security, Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
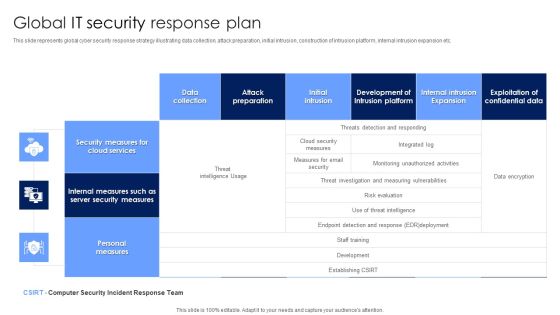
Global IT Security Response Plan Diagrams PDF
This slide represents global cyber security response strategy illustrating data collection, attack preparation, initial intrusion, construction of intrusion platform, internal intrusion expansion etc. Showcasing this set of slides titled Global IT Security Response Plan Diagrams PDF. The topics addressed in these templates are Security Measures, Cloud Services, Personal Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
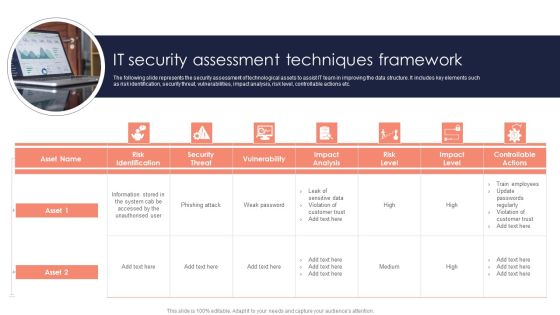
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Data Protection Security Mechanism Portrait PDF
This slide exhibits broad categories in data protection which are traditional data protection, data security and privacy. It further includes data retention, backup, preventing data loss, risk monitoring, data governance, third party contracts, etc.Showcasing this set of slides titled Business Data Protection Security Mechanism Portrait PDF. The topics addressed in these templates are Data Retention, Physical Infrastructure, Date Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon For Functional Technology Security Elements PDF
Presenting icon for functional technology security elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including icon for functional technology security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

What Is Cloud Security Guidelines PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Deliver an awe inspiring pitch with this creative What Is Cloud Security Guidelines PDF bundle. Topics like Computing Systems, Protocols, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Risk Management Assessment Checklist Brochure PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver and pitch your topic in the best possible manner with this security risk management assessment checklist brochure pdf. Use them to share invaluable insights on security, management, requirements, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
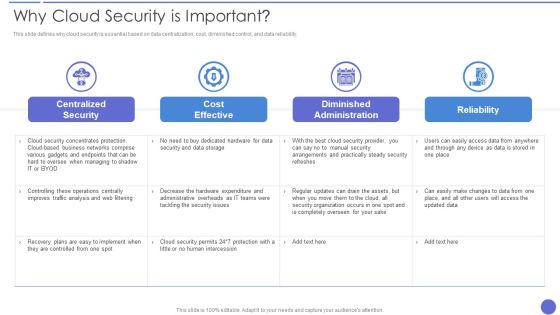
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Payment Card Security Processing Icon Portrait PDF
Presenting Payment Card Security Processing Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Payment Card Security, Processing Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
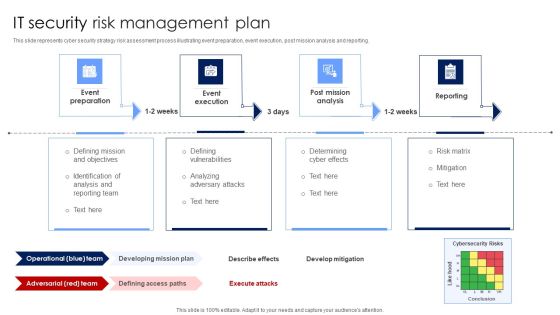
IT Security Risk Management Plan Mockup PDF
This slide represents cyber security strategy risk assessment process illustrating event preparation, event execution, post mission analysis and reporting. Presenting IT Security Risk Management Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Post Mission Analysis, Reporting, Event Execution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
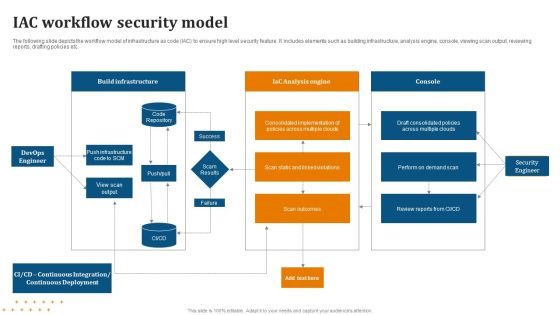
IAC Workflow Security Model Diagrams PDF
Showcasing this set of slides titled IAC Workflow Security Model Diagrams PDF. The topics addressed in these templates are Workflow, Security Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computer Safety And Security Icon Infographics PDF
Persuade your audience using this Computer Safety And Security Icon Infographics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Computer Safety, Security Icon Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Native Application Security PPT Template
This Cloud Native Application Security PPT Template is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This seventy two slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.

KPI Dashboard Metrics Security Icon Download PDF
Persuade your audience using this KPI Dashboard Metrics Security Icon Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Dashboard, Metrics Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

RPA Discovery Procedure Security Steps Brochure PDF
Following slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Presenting RPA Discovery Procedure Security Steps Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Bot Actions Accountability, Avoid Errors And Fraud, Secure Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home