Gap Analysis Of Security

Cyber Security Incident Management Checklist After An Incident Designs PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. If you are looking for a format to display your unique thoughts, then the professionally designed Cyber Security Incident Management Checklist After An Incident Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cyber Security Incident Management Checklist After An Incident Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Manpower Corporate Security Business Profile Executive Summary Template PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Executive Summary Template PDF bundle. Topics like Total Revenue, Employees, Customers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Incident Management Checklist During An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Security Incident Management Checklist During An Incident Summary PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Icons Slide Implementing Cyber Security Incident Management Graphics PDF
Introducing our well designed Icons Slide Implementing Cyber Security Incident Management Graphics PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Mobile Application Security Architecture For Clients Summary PDF
This slide represents the architecture designed to enable the mobile application safety to gain trust of clients. It includes details related to windows and web applications, smart card resource manager, Bluetooth smart card reader. Pitch your topic with ease and precision using this Mobile Application Security Architecture For Clients Summary PDF. This layout presents information on Windows Applications, Web Applications, Resource Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Infra Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Infra Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of seventeen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF
This slide outlines the overview of 51 percent attack in blockchain technology. The purpose of this slide is to showcase how malicious miners possess control over 51 percent of blockchain blocks, including a before and after use case. Retrieve professionally designed Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps Of Information Security Management System Internal Auditing Structure PDF
The following slide highlights the steps of information security management system internal audit illustrating document review, management review, field review, analysis and reporting to assist the organization to find out the gaps in the security management system Presenting Steps Of Information Security Management System Internal Auditing Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Management Review, Reporting, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

Information Systems Security And Risk Management Plan Comparison Rules PDF
This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Find highly impressive Information Systems Security And Risk Management Plan Comparison Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Information Systems Security And Risk Management Plan Comparison Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Real Time Assessment Of Security Threats Table Of Contents Real Time Assessment Of Security Threats Mockup PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats table of contents real time assessment of security threats mockup pdf bundle. Topics like company overview, challenges and solutions, services offered, siem hosting models, siem architecture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
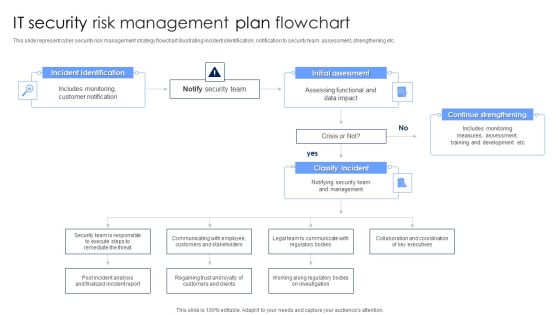
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Project Security Administration IT Pictures PDF
Presenting table of contents for project security administration it pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like project safety management, security centre implementation, budget assessment, dashboard analysis, project management team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
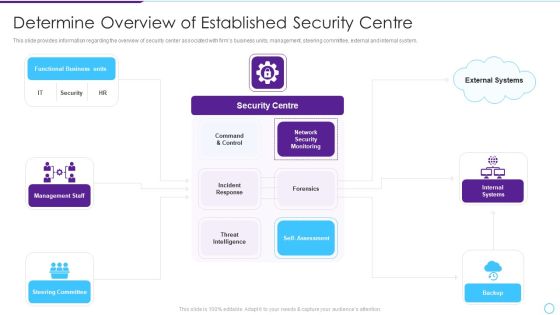
Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functional Business Units, Security Centre, Internal Systems, Self Assessment, Steering Committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF
This slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present like a pro with Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Table Of Contents Organizational Assets Security Management Strategy Information PDF
Find highly impressive Table Of Contents Organizational Assets Security Management Strategy Information PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Organizational Assets Security Management Strategy Information PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents For Workplace Security Management Program Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Workplace Security Management Program Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Workplace Security Management Program Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Timeframe For Incident Management In Security Centre Portrait PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Timeframe For Incident Management In Security Centre Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Information Security Adhere To Strict Compliance Requirements Diagrams PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Adhere To Strict Compliance Requirements Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Adhere To Strict Compliance Requirements Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
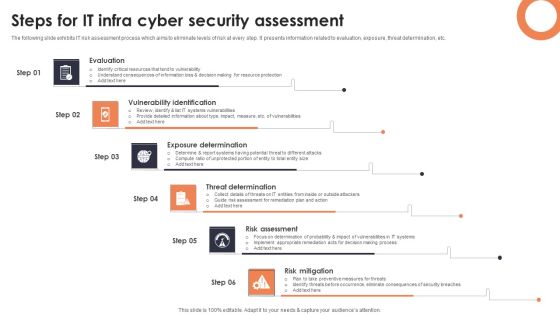
Steps For IT Infra Cyber Security Assessment Background PDF
The following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Presenting Steps For IT Infra Cyber Security Assessment Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Evaluation, Vulnerability Identification, Exposure Determination. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
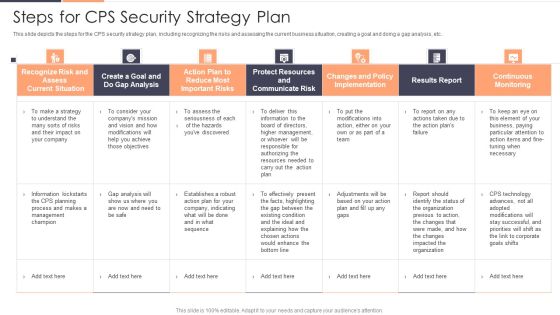
Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF. Use them to share invaluable insights on Recognize Risk, Communicate Risk, Protect Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Highlighting Cyber Security Unawareness Among Employees Summary PDF
The following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Create an editable Data Highlighting Cyber Security Unawareness Among Employees Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Data Highlighting Cyber Security Unawareness Among Employees Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. This Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Vulnerability Administration Plan And Security Services Topics PDF
This slide defines the vulnerability management program and security services based on risk. It includes information related to integrating, assessment planning, analysis and sustainability. Persuade your audience using this Vulnerability Administration Plan And Security Services Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Integrating, Assessment Planning, Analysis And Reporting, Sustainability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Finance Saving Business Security PowerPoint Templates And PowerPoint Themes 1112
We present our Finance Saving Business Security PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, This template with an image of helps you chart the course of your presentation. Use our Success PowerPoint Templates because,Break it all down to Key Result Areas. Use our Future PowerPoint Templates because, You have some exciting plans to spread goodwill among the underprivileged, Expound on your ideas and show to your colleagues how they can help others and in the process increase your Brand value. Use our Business PowerPoint Templates because, Expound on how you plan to gain their confidence and assure them of continued and consistent excellence in quality of service. Use our Finance PowerPoint Templates because, Watch their mental juices begin to flow.Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock, success, future, security, business, finance. The prominent colors used in the PowerPoint template are Blue, Yellow, Black

Information Technology Security Risk Assessment Grid Information PDF
The following slide depicts the analysis of IT security to prevent loss of confidentiality and integrity. The matrix constitutes of elements such as risk, likelihood, its impact and overall threat level. Persuade your audience using this Information Technology Security Risk Assessment Grid Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Loss Of Privacy, System Integrity, Loss Of Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How Much Employees Are Aware Of Cyber Security Introduction PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age.This is a How Much Employees Are Aware Of Cyber Security Introduction PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Questions Correctly, Employees Answered, Employees Between. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
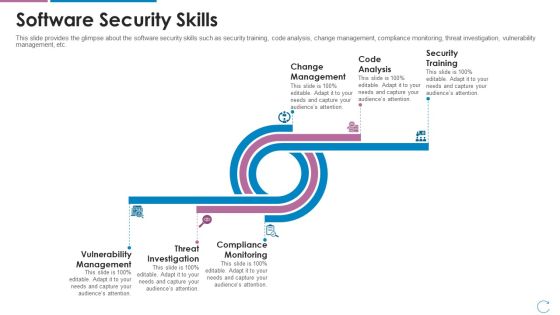
Devops Team Capabilities IT Software Security Skills Ppt Deck PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Deliver an awe inspiring pitch with this creative devops team capabilities it software security skills ppt deck pdf bundle. Topics like change management, code analysis, security training, vulnerability management, threat investigation, compliance monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
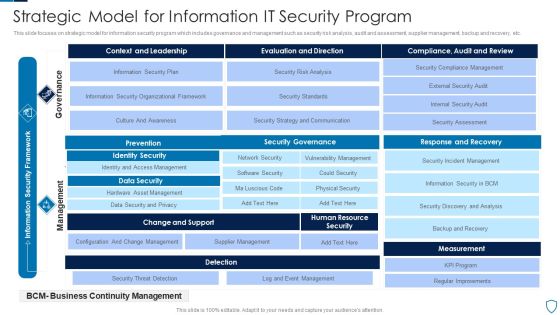
Strategic Model For Information IT Security Program Slides PDF
This slide focuses on strategic model for information security program which includes governance and management such as security risk analysis, audit and assessment, supplier management, backup and recovery, etc.Showcasing this set of slides titled Strategic Model For Information IT Security Program Slides PDF The topics addressed in these templates are Prevention, Identity Security, Data Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Operations Management Skills Software Security Skills Pictures PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Presenting operations management skills software security skills pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security System Auditing And Risk Assessment Elements PDF
The following slide highlights the information security system audit and risk assessment illustrating key headings which includes security risk assessment, security auditing, security incident monitoring, security incident response Persuade your audience using this Information Security System Auditing And Risk Assessment Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Risk Assessment, Security Auditing, Security Incident Monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Smart Phone Security Key Aspects For Growing Revenue Icons PDF
This slide shows every aspect of phone security model that should be considered while framing security policy for organization. It include aspects such as compliance security, product security and infrastructure security etc. Presenting Smart Phone Security Key Aspects For Growing Revenue Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Compliance Security, Product Security, Infrastructure Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
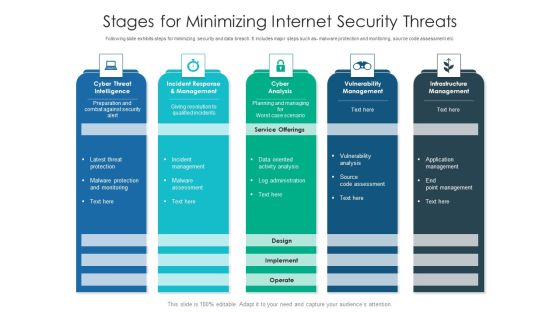
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Companys Data Safety Recognition Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative companys data safety recognition security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
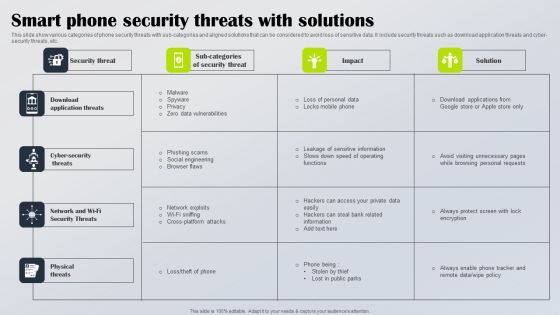
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Components Of Data Security Management Framework Pictures PDF
This slide showcases a framework highlighting key areas covered in data security governance to manage business information. It includes key components such as quality, knowledge, ownership, accessibility and security. Presenting Key Components Of Data Security Management Framework Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Ownership, Accessibility, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
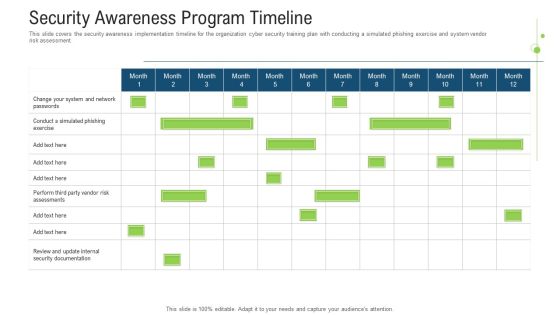
Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Cloud Security Assessment Cont Background PDF
This is a Table Of Contents For Cloud Security Assessment Cont Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Security Responsibilities, Security Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Security Assessment Ideas PDF
Presenting Table Of Contents For Cloud Security Assessment Ideas PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Cloud Security, Security Different, Security Is Important. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essential Measures For Business Cyber Security Assessment Plan Rules PDF
This slide demonstrates the safety measures in a business security plan that helps in decreasing the frequency of security threats data hacks, information breaches etc. The measures include handy backups, multi layer security, protective software, and employee training. Presenting Essential Measures For Business Cyber Security Assessment Plan Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

3 Months Roadmap For Implementing Smart Phone Security Information PDF
This slide shows quarterly roadmap for building and implementing security framework in organization to identify and remove potential threats from operations. It include stage such as get buy-in, frame security timeline, etc. Presenting 3 Months Roadmap For Implementing Smart Phone Security Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Get Buy In, Frames Security Baseline, Implement Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
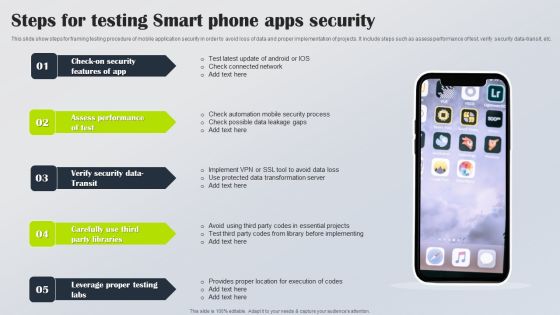
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
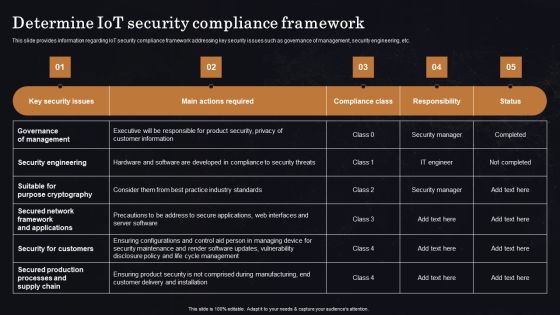
Determine Iot Security Compliance Framework Ppt Professional Vector PDF
This slide provides information regarding IoT security compliance framework addressing key security issues such as governance of management, security engineering, etc. Get a simple yet stunning designed Determine Iot Security Compliance Framework Ppt Professional Vector PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Iot Security Compliance Framework Ppt Professional Vector PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
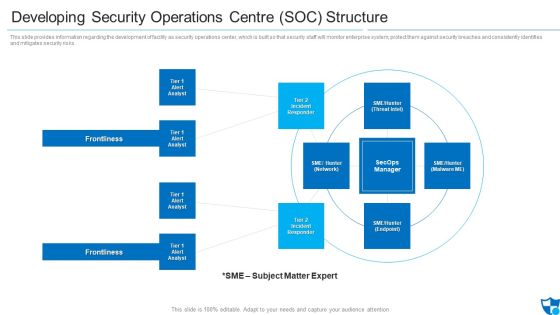
Developing Security Operations Centre SOC Structure Microsoft PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting developing security operations centre soc structure microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident responder, tier 2 incident responder, frontlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Estimated Security Management Plan Critical Success Factors Microsoft PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors microsoft pdf. Use them to share invaluable insights on estimated security management plan critical success factors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Security Management Plan Critical Success Factors Designs PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors designs pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current State Of Security Automation With Projected Development Slides PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF
This slide covers strategies for efficient cyber security incident management. It involves strategies such as create incident management plan and team, conduct regular training and conduct post incident analysis. Presenting Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Incident Management Plan, Create Incident, Response Team, Conduct Regular Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
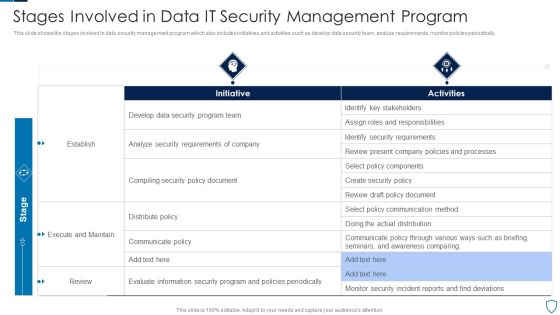
Stages Involved In Data IT Security Management Program Diagrams PDF
This slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically.Pitch your topic with ease and precision using this Stages Involved In Data IT Security Management Program Diagrams PDF This layout presents information on Identify Stakeholders, Security Requirements, Execute Maintain It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
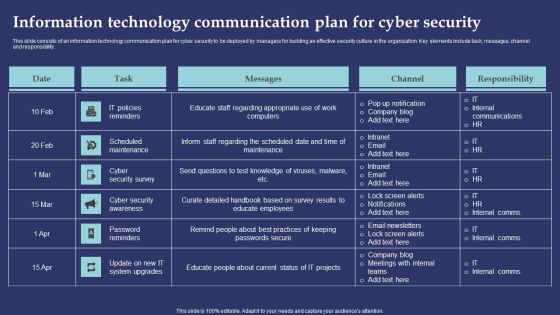
Information Technology Communication Plan For Cyber Security Information PDF
This slide consists of an information technology communication plan for cyber security to be deployed by managers for building an effective security culture in the organization. Key elements include task, messages, channel and responsibility. Showcasing this set of slides titled Information Technology Communication Plan For Cyber Security Information PDF. The topics addressed in these templates are IT Policies Reminders, Scheduled Maintenance, Cyber Security Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Desktop Security Management Detail Impact Computer Designs PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this desktop security management detail impact computer designs pdf. Use them to share invaluable insights on detail impact computer security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Certified Information Systems Security Professional Cissp Details Pictures PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications.Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional Cissp Details Pictures PDF bundle. Topics like Security Specialist, Certified Information, Certifying Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
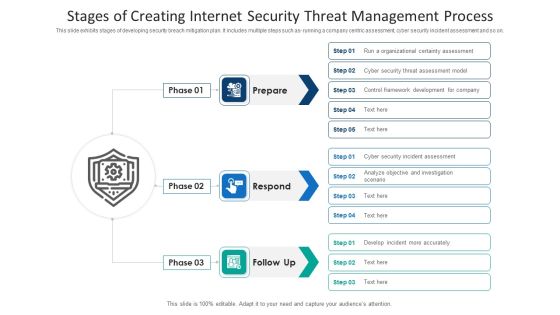
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF
This slide covers prioritization matrix for cyber security based on risk, cost, value and efforts. It includes actions such as recommendations to analyst, security solution designing, security tools selection, team trainings, etc.Presenting Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Tool Recommendations, Design Process, Team Trainings. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Cyber Security Assessment Protection Icon Ideas PDF
Presenting Business Cyber Security Assessment Protection Icon Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Protection Icon, Business Cyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Security Assessment Report Icon Demonstration PDF
Presenting Information Technology Security Assessment Report Icon Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Technology Security, Assessment Report Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Assessment Of Security Awareness Online Courses Background PDF
Deliver an awe inspiring pitch with this creative Comparative Assessment Of Security Awareness Online Courses Background PDF bundle. Topics like Internet Security, Intermediate, Awareness Course can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents Cyber Safety Incident Management Security Microsoft PDF
This is a table of contents cyber safety incident management security microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current scenario assessment, handling cyber threats to secure digital assets, ensuring physical security, securing firm from natural calamity threats . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying SDN System Software Defined Networking And Security Mockup PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Deploying SDN System Software Defined Networking And Security Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF
The following slide showcases comparison of different cloud infrastructure securities which provides continuous monitoring and support for improvement and better management of security. It presents information related to Microsoft defender, identity manager, etc. Showcasing this set of slides titled Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF. The topics addressed in these templates are Software, Services, Security Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Security Risk Impact And Probability Assessment Inspiration PDF
This slide defines the risk impact and likelihood assessment in cyber security. It includes information related to creating awareness in top management regarding technical, commercial, and branding damages deriving from suffering a cyber-attack. Showcasing this set of slides titled Cyber Security Risk Impact And Probability Assessment Inspiration PDF. The topics addressed in these templates are Business Continuity, Restoring Cost, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Latest Trends For Mobile Smart Phone Security Icons PDF
This slide shows current trends for securing mobile phone against potential cyber attacks and loss of sensitive data. It include trends such as rise in security automation, increasing threat modelling and SAST-DAST integration etc qPresenting Latest Trends For Mobile Smart Phone Security Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increasing Security, SAST DAST Integration, Increasing Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Incident Management Checklist After An Incident Elements PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Explore a selection of the finest Cyber Security Incident Management Checklist After An Incident Elements PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cyber Security Incident Management Checklist After An Incident Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Comparative Assessment Of Hotel Protection And Security Solutions Mockup PDF
This slide covers comparative assessment of hotel safety and security solutions. It involves parameters of comparison such as anti slip solution, fire retarder, anti theft, test alarms and cost involved. Persuade your audience using this Comparative Assessment Of Hotel Protection And Security Solutions Mockup PDF This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Comparative Assessment, Hotel Protection, Security Solutions Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Main Steps Of Operational Security Ppt Ideas Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a main steps of operational security ppt ideas summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential threats, analyze security holes and vulnerabilities, assessment of risks, implementation of appropriate countermeasures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF
This slide presents a cyber security and information technology communication plan flowchart to be implemented by managers to safeguard information technology assets and raise awareness regarding the plans. Major elements covered are incident identification, notifying the security team, incident assessment, etc. Presenting Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Incident Identification, Initial Incident Assessment, Continue Training Team Strengthening. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
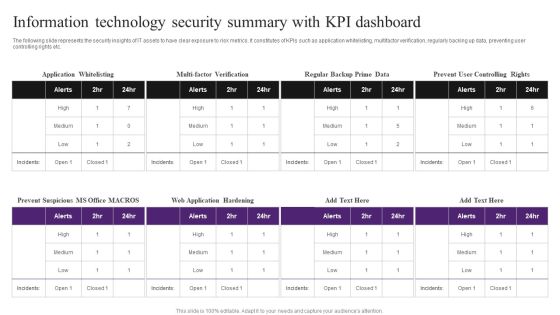
Information Technology Security Summary With KPI Dashboard Inspiration PDF
The following slide represents the security insights of IT assets to have clear exposure to risk metrics. It constitutes of KPIs such as application whitelisting, multifactor verification, regularly backing up data, preventing user controlling rights etc. Pitch your topic with ease and precision using this Information Technology Security Summary With KPI Dashboard Inspiration PDF. This layout presents information on Information Technology Security, Summary With KPI Dashboard. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Certified Information Systems Security Professional Cissp Examination Details Topics PDF
Presenting Certified Information Systems Security Professional Cissp Examination Details Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Software Development, Security Assessment, Communications And Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF
The following slide shows dashboard of CPM cyber security program management which helps to access high value assets and check threats , risks and policies on one platform. It includes current threat postures, risks, policy, service breakdown, assets by category and their control issues. Pitch your topic with ease and precision using this Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF. This layout presents information on Cyber Security, Program Management Dashboard, Kpi Metrics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

5 Step Approach In IT Security Plan Framework Designs PDF
This slide represents 5 step approach in cyber security strategy framework such as identifying, protecting, detecting, responding and recovering that are been adopted by various organization. Presenting 5 Step Approach In IT Security Plan Framework Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Management Risk Plan Ppt Outline Designs PDF
This slide showcases cyber security issues and action plan to mitigate the risks as per their priority. Risks are prioritized based on their confidentiality, integrity and availability. Pitch your topic with ease and precision using this Cyber Security Management Risk Plan Ppt Outline Designs PDF. This layout presents information on Risk Mitigation Plan, Risk, Confidentiality. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
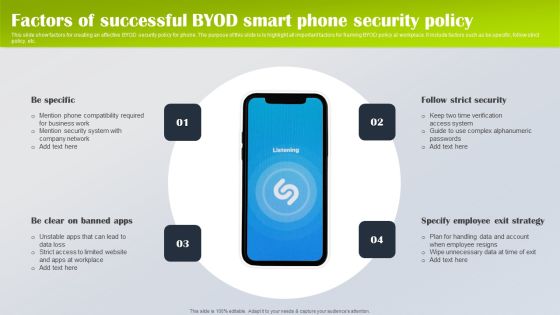
Factors Of Successful Byod Smart Phone Security Policy Designs PDF
This slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting Factors Of Successful Byod Smart Phone Security Policy Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Be Specific, Specify Employee Exit Strategy, Follow Strict Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Incident Escalation Communication Plan Flowchart Structure PDF
This slide illustrates a flow chart of the cyber security incident escalation communication plan to manage an attack and minimize the impact. It includes elements such as security team, incident identifier vendor notification etc. Presenting IT Security Incident Escalation Communication Plan Flowchart Structure PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Identifier, Vendor Notification, Website Gets Crashed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How Security Concerns Affect Firm In Present Times Pictures PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative how security concerns affect firm in present times pictures pdf bundle. Topics like reported financial losses due to increase security threats, data breaches and records exposed, security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
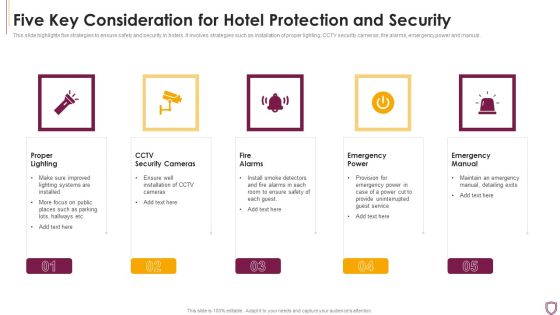
Five Key Consideration For Hotel Protection And Security Infographics PDF
This slide highlights five strategies to ensure safety and security in hotels. It involves strategies such as installation of proper lighting, CCTV security cameras, fire alarms, emergency power and manual.Presenting Five Key Consideration For Hotel Protection And Security Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Emergency Power, Emergency Manual, Proper Lighting This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
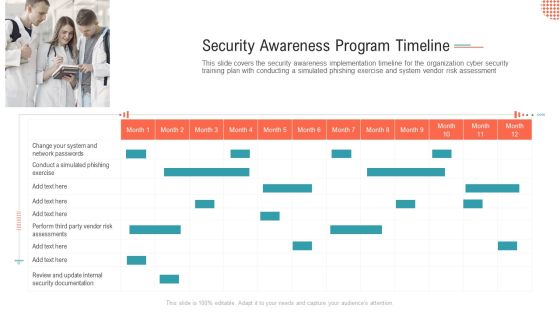
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
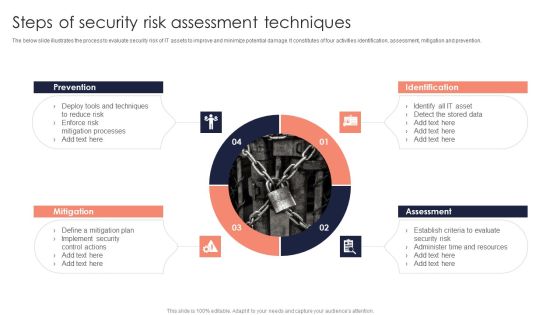
Steps Of Security Risk Assessment Techniques Introduction PDF
The below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Showcasing this set of slides titled Steps Of Security Risk Assessment Techniques Introduction PDF. The topics addressed in these templates are Prevention, Identification, Assessment, Mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Service Assessment Icon To Track Network Security Information PDF
Persuade your audience using this Service Assessment Icon To Track Network Security Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Service Assessment Icon To Track Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Unified Security Management Ppt Template Example Of Ppt Presentation
This is a unified security management ppt template example of ppt presentation. This is a four stage process. The stages in this process are assess the network, find threats, data loss prevention, gateway anti virus.
Overview Of Security Risk Management Process Demonstration PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver and pitch your topic in the best possible manner with this Overview of security risk management process demonstration pdf. Use them to share invaluable insights on identify the risks, assess the risks, evaluate the risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Strategic Planning Process For CPS Ppt Slides Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver and pitch your topic in the best possible manner with this Security Strategic Planning Process For CPS Ppt Slides Icons PDF. Use them to share invaluable insights on Business Strategy, Technology Roadmap, Environmental Trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.
Scads Network Security Assessment Ppt PowerPoint Presentation Icon Deck Cpb
Presenting this set of slides with name scads network security assessment ppt powerpoint presentation icon deck cpb. This is an editable Powerpoint five stages graphic that deals with topics like scads network security assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Security Training Program Frameworks Ppt Outline Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks ppt outline layout ideas pdf. Use them to share invaluable insights on requirements, metrics, systems security, materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Software As A Service Saas Formats PDF
This slide describes the software as a service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Software As A Service Saas Formats PDF bundle. Topics like Disadvantages, Installing Any Software, Service Providers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determine Role Of Security Centre In Firm Designs PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Determine Role Of Security Centre In Firm Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Determine Role Of Security Centre In Firm Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

 Home
Home