Gap Analysis Of Security
Internet Security Threat Analysis Plan With Icons Ppt PowerPoint Presentation Ideas Influencers PDF
Pitch your topic with ease and precision using this internet security threat analysis plan with icons ppt powerpoint presentation ideas influencers pdf. This layout presents information on inspect, preliminary assessment, extended assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
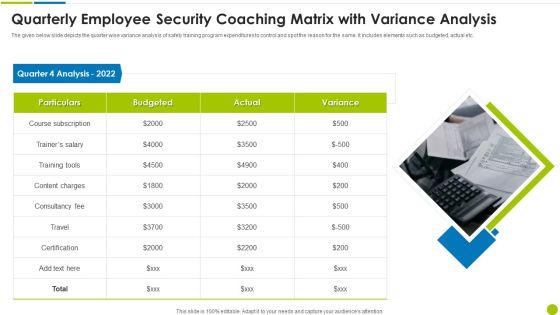
Quarterly Employee Security Coaching Matrix With Variance Analysis Ppt Styles Design Ideas PDF
The given below slide depicts the quarter wise variance analysis of safety training program expenditures to control and spot the reason for the same. It includes elements such as budgeted, actual etc. Presenting quarterly employee security coaching matrix with variance analysis ppt styles design ideas pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including particulars, quarter 4 analysis 2022, consultancy fee, content charges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
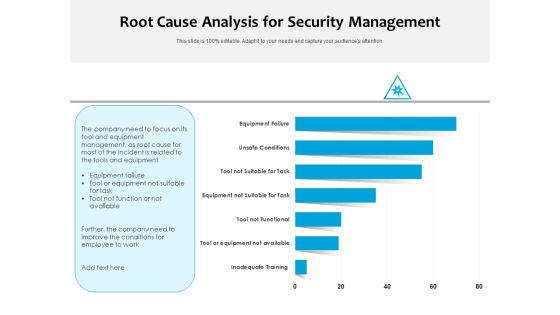
Root Cause Analysis For Security Management Ppt PowerPoint Presentation Slides Grid PDF
Pitch your topic with ease and precision using this root cause analysis for security management ppt powerpoint presentation slides grid pdf. This layout presents information on inadequate training, tool or equipment not available, tool not functional, equipment not suitable for task, tool not suitable for task, unsafe conditions, equipment failure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Online Settlement Revolution Payment Security And Fraud Management Solutions Analysis Ppt Slides File Formats PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions analysis ppt slides file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like before the payment, on the payment page, after the payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Half Yearly Information Technology Security Roadmap For Continuous Threat Analysis Rules
Presenting the half yearly information technology security roadmap for continuous threat analysis rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Information Technology Security Roadmap For Continuous Threat Analysis Microsoft
Presenting the six months information technology security roadmap for continuous threat analysis microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
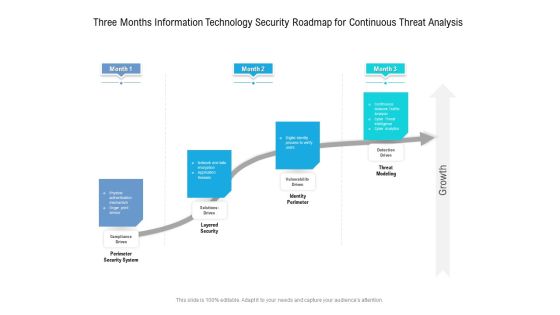
Three Months Information Technology Security Roadmap For Continuous Threat Analysis Professional
Presenting the three months information technology security roadmap for continuous threat analysis professional. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Impact Analysis Overall Food Quality Improvement Food Security Excellence Ppt Gallery Graphics Template PDF
This slide provides information regarding the overall impact of quality improvement. As with quality enhancement, occurrence of defects has reduced, leading to reduction in cost of quality, increased customer satisfaction, etc. Deliver an awe inspiring pitch with this creative impact analysis overall food quality improvement food security excellence ppt gallery graphics template pdf bundle. Topics like cost, customer satisfaction, defect occurrence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre-designed and impeccable Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
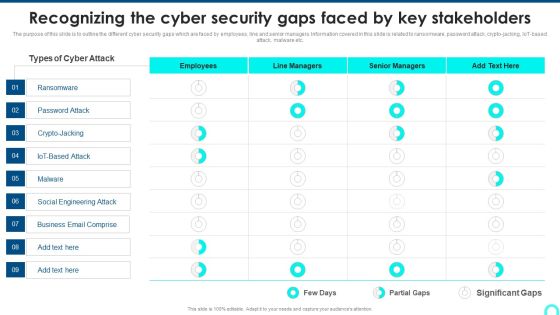
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Deliver and pitch your topic in the best possible manner with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF. Use them to share invaluable insights on Ransomware, Engineering Attack, Email Comprise and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategies To Overcome Cyber Security Workforce Shortage To Address Demand And Supply Gaps Topics PDF
This slide covers different techniques to overcome cyber workforce shortage. It includes expanding talent pool, identifying existing talent, re-train staff and introduce innovations to reduce demand. Persuade your audience using this Strategies To Overcome Cyber Security Workforce Shortage To Address Demand And Supply Gaps Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expand Talent Pool, Identify Existing Talent, Re Train Existing Staff. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Risk Management Assessment Checklist Brochure PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver and pitch your topic in the best possible manner with this security risk management assessment checklist brochure pdf. Use them to share invaluable insights on security, management, requirements, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Security Management System Auditing Brochure PDF
The following slide highlights the information security management system audit process illustrating information security system details, information collection, statement o applicability review, audit scope, risk management analysis, gap analysis, business continuity and contingency plan review, mitigation strategy and compliance audit activities PresentingInformation Security Management System Auditing Brochure PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Risk Management Analysis, Information Collection, Mitigation Strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

Information Security Management Best Practices Themes PDF
This slide presents various best practices for information security governance to effectively manage and mitigate IT risks. It includes key practices such as reflect business objectives, develop and enforce security program, embrace organizations culture, etc. Presenting Information Security Management Best Practices Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Reflect Business Objectives, Spend Resources Effectively, Embrace Organizations Culture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
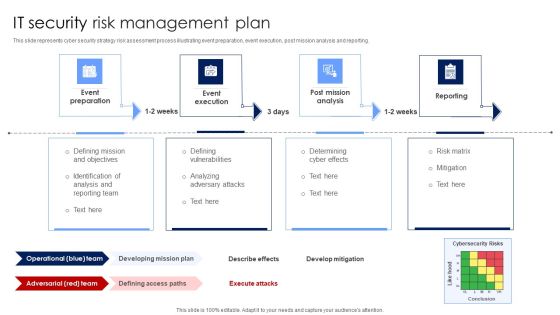
IT Security Risk Management Plan Mockup PDF
This slide represents cyber security strategy risk assessment process illustrating event preparation, event execution, post mission analysis and reporting. Presenting IT Security Risk Management Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Post Mission Analysis, Reporting, Event Execution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Patch Management Template Presentation Images
This is a security patch management template presentation images. This is a six stage process. The stages in this process are testing, architecture, quality assurance, analysis, design, synthesis.
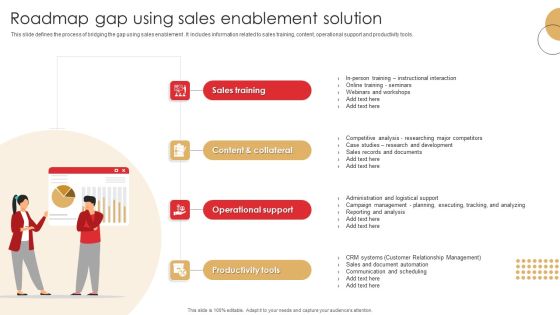
Roadmap Gap Using Sales Enablement Solution Graphics PDF
This slide defines the process of bridging the gap using sales enablement . It includes information related to sales training, content, operational support and productivity tools.Presenting Roadmap Gap Using Sales Enablement Solution Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Operational Support, Productivity Tools, Content Collateral. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
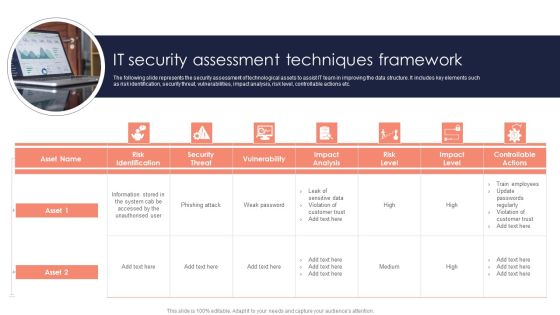
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
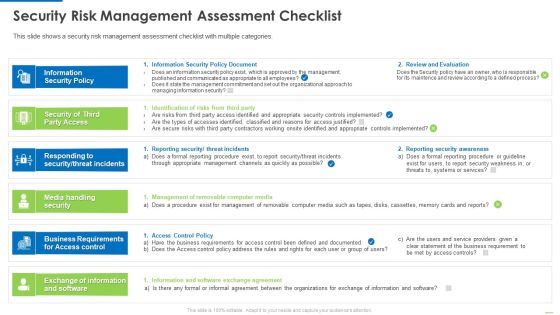
Security Risk Management Assessment Checklist Inspiration PDF
This is a security risk management assessment checklist inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security policy, security of third party access, media handling security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Risk Management Assessment Checklist Structure PDF
Presenting security risk management assessment checklist structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, media handling security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Consulting Sample Diagram Powerpoint Images
This is a security management consulting sample diagram powerpoint images. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.

Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Risk Assessment Sample Diagram Ppt Sample
This is a security risk assessment sample diagram ppt sample. This is a four stage process. The stages in this process are identify, document, decide, evaluate, review.

Information Security Risk Management Form Guidelines PDF
This slide shows information security risk acceptance form which contains accountable person details, risk acceptance summary, acceptance advantages, justification, advice, etc. This can benefit cyber security department in careful review prior to the acceptance of major risks involved. Pitch your topic with ease and precision using this Information Security Risk Management Form Guidelines PDF. This layout presents information on Risk Modification, Risk Acceptance, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this impact of effective security management information pdf. Use them to share invaluable insights on malicious codes prevented, unauthorized ip addresses ports and traffic, security incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Management System Microsoft PDF
The following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Pitch your topic with ease and precision using this cyber security risk management system microsoft pdf. This layout presents information on mapping threats, threat containment and remediation, identify management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
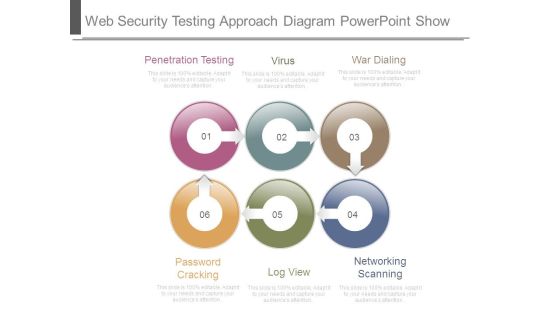
Web Security Testing Approach Diagram Powerpoint Show
This is a web security testing approach diagram powerpoint show. This is a six stage process. The stages in this process are penetration testing, virus, war dialing, password cracking, log view, networking scanning.

RPA Discovery Procedure Security Steps Brochure PDF
Following slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Presenting RPA Discovery Procedure Security Steps Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Bot Actions Accountability, Avoid Errors And Fraud, Secure Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Network Security Assessment Flowchart Structure PDF
This slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Showcasing this set of slides titled Digital Network Security Assessment Flowchart Structure PDF. The topics addressed in these templates are Account Holder, Information Leak, Network Service Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Of Supply Project Assessment Ppt Slides
This is a security of supply project assessment ppt slides. This is a four stage process. The stages in this process are project assessment, technical resilience, technical aspects, losses variation.
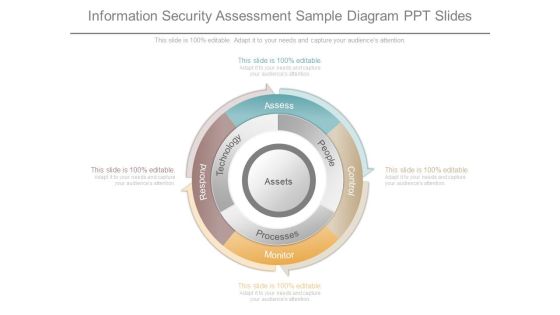
Information Security Assessment Sample Diagram Ppt Slides
This is a information security assessment sample diagram ppt slides. This is a four stage process. The stages in this process are assess, people, processes, technology, respond, monitor, control.

Security Assessment Services Sample Diagram Powerpoint Image
This is a security assessment services sample diagram powerpoint image. This is a six stage process. The stages in this process are define scope, agree start date, configuration review, vulnerability scanning, penetration testing, configuration review.
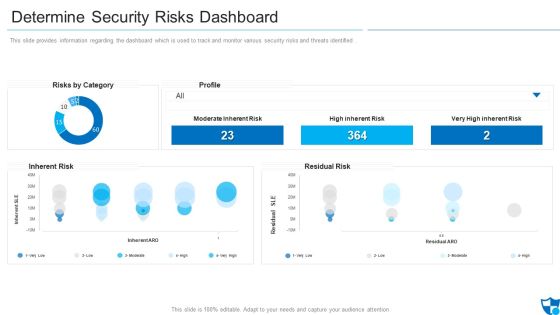
Determine Security Risks Dashboard Introduction PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified.Deliver and pitch your topic in the best possible manner with this determine security risks dashboard introduction pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
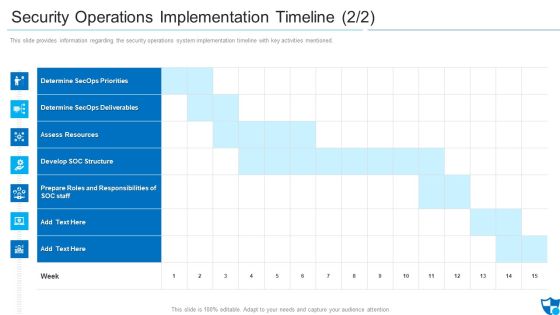
Security Operations Implementation Timeline Assess Diagrams PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned.Deliver and pitch your topic in the best possible manner with this security operations implementation timeline assess diagrams pdf. Use them to share invaluable insights on determine secops priorities, determine secops deliverables, assess resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
It Security Diagram Ppt Background Graphics
This is a it security diagram ppt background graphics. This is a five stage process. The stages in this process are management policy, proactive threat assessment, protect, detect, respond.
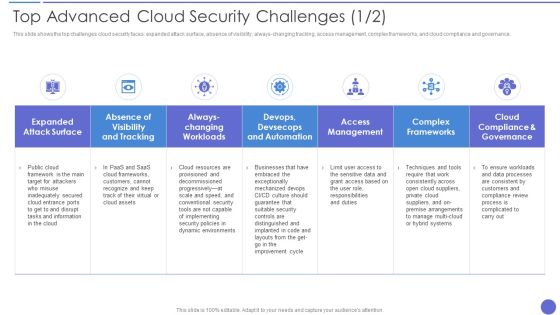
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
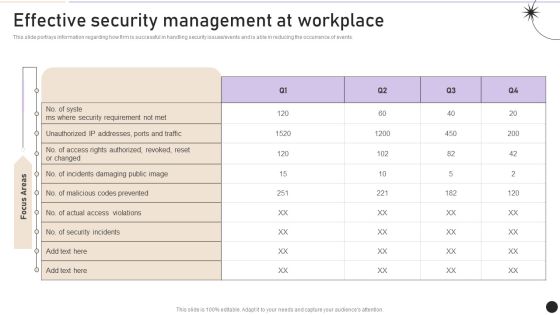
Effective Security Management At Workplace Designs PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present like a pro with Effective Security Management At Workplace Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information Security Management Strategic Model Inspiration PDF
The following slide showcases a framework presenting strategy development and implementation phase in information security governance. It includes key components such as organizational structure, value delivery, strategic alignment, resource optimization, performance measurement, etc. Presenting Information Security Management Strategic Model Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Value Delivery, Key Insights, Organizational Structure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda For Cloud Security Assessment Infographics PDF
Presenting Agenda For Cloud Security Assessment Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
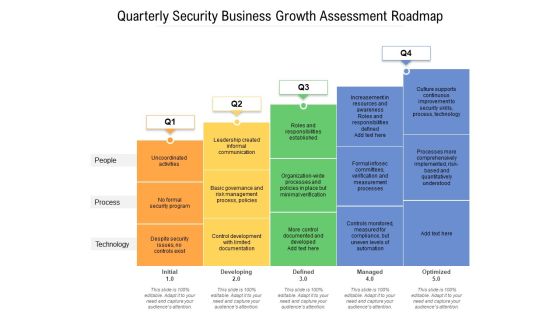
Quarterly Security Business Growth Assessment Roadmap Infographics
Presenting our jaw-dropping quarterly security business growth assessment roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
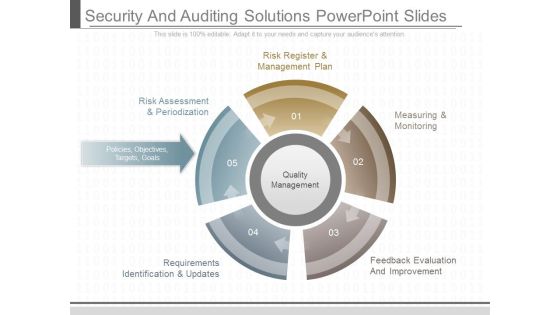
Security And Auditing Solutions Powerpoint Slides
This is a security and auditing solutions powerpoint slides. This is a five stage process. The stages in this process are risk register and management plan, risk assessment and periodization, policies objectives targets goals, requirements identification and updates, measuring and monitoring, feedback evaluation and improvement, quality management.

Cyber Security Network Development Timeline Download PDF
The following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice. Presenting Cyber Security Network Development Timeline Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Establish, Analyse, Practice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Ppt PowerPoint Presentation Complete Deck
Incorporate this Information Security Ppt PowerPoint Presentation Complete Deck to define the objectives of business performance and how to drive results. List goals and outline a plan to achieve all your enterprise targets using this well-crafted complete deck in sixty four slides. Walk your audience through the key objectives of your business set-up, especially for customers and inspire them to work with diligence using this predesigned presentation template. Download now with the added assurance of a 100 percent customizable and editable product.

Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

IT Security Six Months Strategic Timeline Portrait
Presenting the it security six months strategic timeline portrait. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Security Strategic Six Months Functional Timeline Clipart
Presenting the security strategic six months functional timeline clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF
This slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF bundle. Topics like Awareness And Training, Protective Technology, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF. Use them to share invaluable insights on Monitory Services, Company Shareholding, Extensive Customization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF. Use them to share invaluable insights on Dynamic Environments, Resources Are Provisioned, Access Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Surveillance Company Profile Security Company Business Model Designs PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Security Company Business Model Designs PDF bundle. Topics like Target Market, Revenue Stream, Cost Structure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Security Company Business Model Mockup PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Business Model Mockup PDF bundle. Topics like Revenue Stream, Customer Relationship, Customer Segments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Security Company Executive Summary Formats PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Executive Summary Formats PDF bundle. Topics like Company Shareholding, Customization Options, Raymond Michael can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
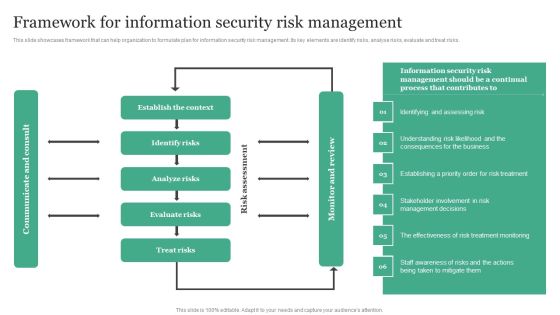
Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF can be your best option for delivering a presentation. Represent everything in detail using Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Find highly impressive Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
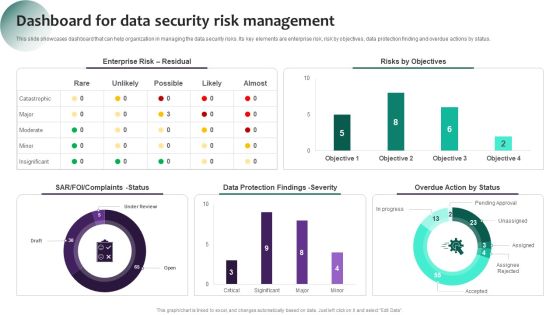
Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. If you are looking for a format to display your unique thoughts, then the professionally designed Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security Automation To Analyze And Mitigate Cyberthreats Enterprise Network It Security Inspiration PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Security Automation To Analyze And Mitigate Cyberthreats Enterprise Network It Security Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Security Awareness Program Timeline Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This is a security awareness program timeline hacking prevention awareness training for it security professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perform, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Agenda Of Real Time Assessment Of Security Threats Designs PDF
This is a real time assessment of security threats agenda of real time assessment of security threats designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of real time assessment of security threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting enhanced protection corporate event administration role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Cyber Security Risk Management Plan Introducing Information Security Risk Assessment Process Workflow Elements PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a cyber security risk management plan introducing information security risk assessment process workflow elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like characterize system, identify vulnerabilities, identify threats, recommend remediation measures, analyze risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
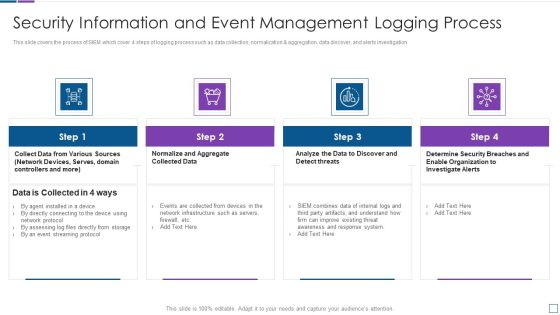
Real Time Assessment Of Security Threats Security Information And Event Management Logging Process Demonstration PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a real time assessment of security threats security information and event management logging process demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks has constructed Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Information Systems Security And Risk Management Plan Current Information Security Issues Faced By Organization Rules PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Information Systems Security And Risk Management Plan Current Information Security Issues Faced By Organization Rules PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
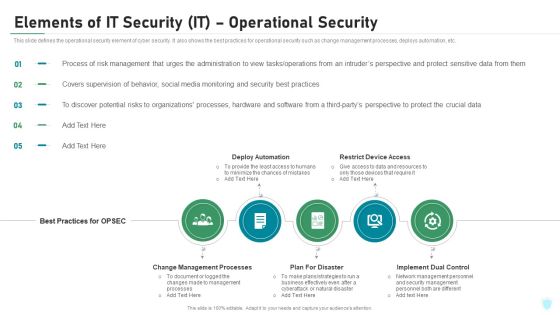
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Information Security Main Steps Of Operational Security Ppt Inspiration Show PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting information security main steps of operational security ppt inspiration show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like sensitive information, potential threats, analyze security, assessment of risks, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
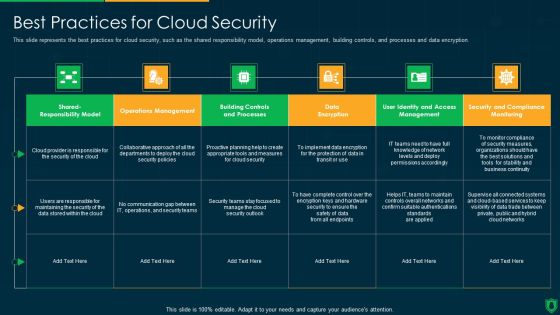
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Estimated Security Management Plan Information PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks estimated security management plan information pdf Use them to share invaluable insights on security incidents level, security implementation, overall security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.This is a Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Security, Internet Security, Endpoint Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Security Information And Event Management Services Information PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting real time assessment of security threats security information and event management services information pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Technology Security Operations Developing Security Operations Centre SOC Structure Slides PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting information and technology security operations developing security operations centre soc structure slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
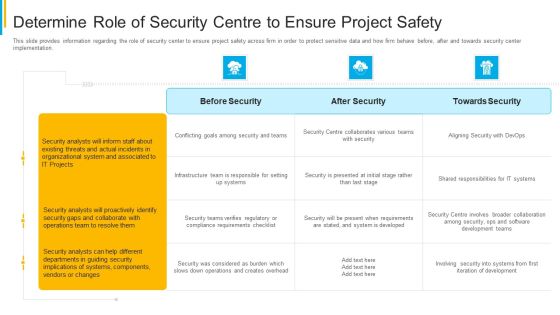
Project Security Administration IT Determine Role Of Security Centre To Ensure Project Safety Microsoft PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this project security administration it determine role of security centre to ensure project safety microsoft pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
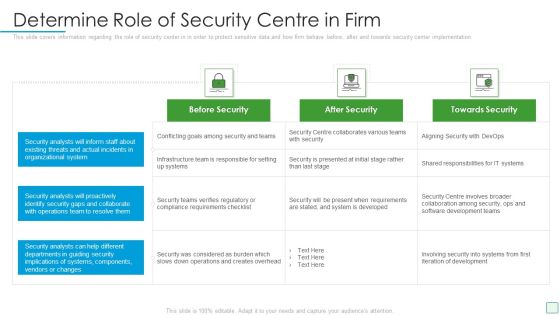
Developing Firm Security Strategy Plan Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan determine role of security centre in firm graphics pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
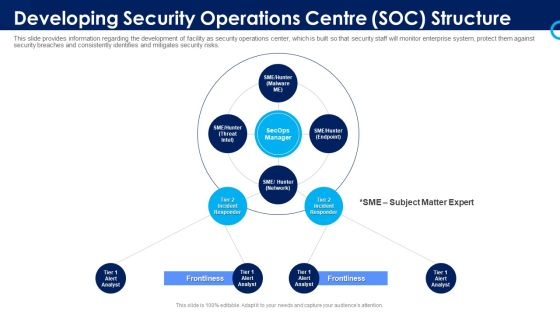
Organizational Security Solutions Developing Security Operations Centre SOC Structure Introduction PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting organizational security solutions developing security operations centre soc structure introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
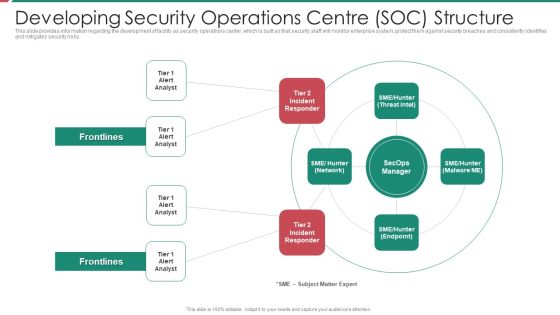
Security And Process Integration Developing Security Operations Centre SOC Structure Inspiration PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting security and process integration developing security operations centre soc structure inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
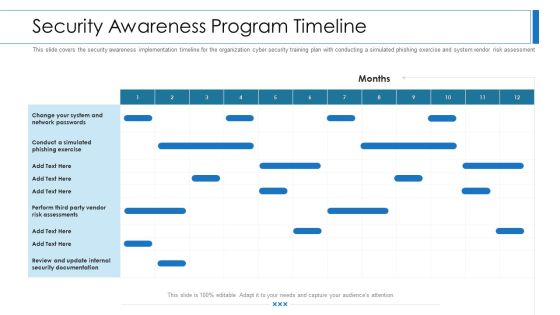
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
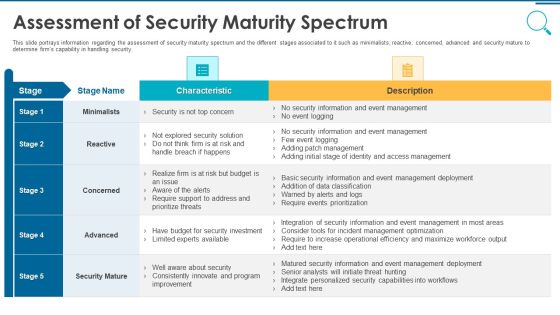
Information And Technology Security Operations Assessment Of Security Maturity Spectrum Template PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative information and technology security operations assessment of security maturity spectrum template pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Risk Management Assessment Checklist Demonstration PDF
This slide shows a security risk management assessment checklist with multiple categories.Presenting techniques and strategies to reduce security management risks security risk management assessment checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, responding to security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security and process integration assessment of security maturity spectrum slides pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Developing Security Operations Centre SOC Structure Guidelines PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Deliver and pitch your topic in the best possible manner with this security functioning centre developing security operations centre soc structure guidelines pdf. Use them to share invaluable insights on incident responder, analyst, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Why Cloud Security Is Important Cloud Computing Security IT Ppt Slides Graphics Template PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver and pitch your topic in the best possible manner with this why cloud security is important cloud computing security it ppt slides graphics template pdf. Use them to share invaluable insights on centralized security, cost effective, diminished administration, reliability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF. Use them to share invaluable insights on Efficient Recovery, Hardware Required, Efficient Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
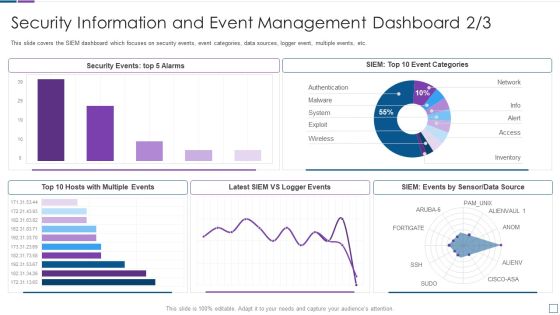
Real Time Assessment Of Security Threats Security Information And Event Management Dashboard Infographics PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative real time assessment of security threats security information and event management dashboard infographics pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Present like a pro with Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

IT Security Main Principle Of Information Security Ppt Model Designs Download PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative information technology security main principle of information security ppt infographic template information pdf bundle. Topics like main principle of information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Effective Security Management At Workplace Structure PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan effective security management at workplace structure pdf. Use them to share invaluable insights on effective security management at workplace and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

What Is Cloud Security Cloud Computing Security IT Ppt File Graphics PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Presenting what is cloud security cloud computing security it ppt file graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, technologies, protocols, business, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
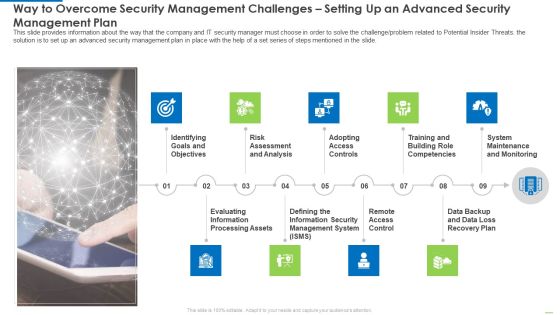
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Introduction PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment and analysis, adopting access controls, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
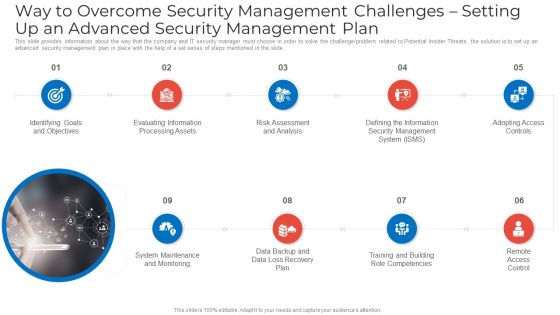
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Microsoft PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. Presenting way to overcome security management challenges setting up an advanced security management plan microsoft pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, risk assessment and analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
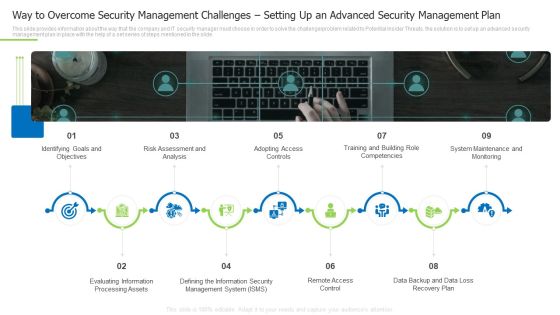
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Rules PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan rules pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Elements Of Information Technology Security Operational Security Ppt Icon Guidelines PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a elements of information technology security operational security ppt icon guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process, sensitive, management, administration, operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance.This is a Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Access Control, Centre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Checklist Policies And Procedures Background PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Presenting Cloud Security Assessment Cloud Security Checklist Policies And Procedures Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Security Solutions, Security Procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
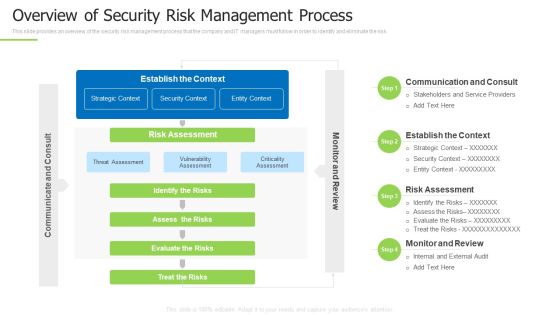
Techniques And Strategies To Reduce Security Management Risks Overview Of Security Risk Background PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks overview of security risk background pdf bundle. Topics like identify the risks, strategic context, vulnerability assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain.Find highly impressive Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
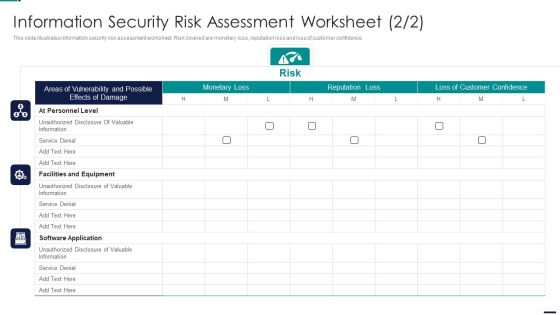
Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF. Use them to share invaluable insights on Facilities And Equipment, Software Application, At Personnel Level, Monetary Loss, Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.This is a Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Business Continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF.

Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Service Graphics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security risk assessment worksheet service graphics pdf. Use them to share invaluable insights on monetary loss, reputation loss, loss of customer confidence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF bundle. Topics like Phishing Attacks, Cross Attack, Security Vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home