Executive Summary Security

Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.Slidegeeks has constructed Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF
The following slide represents the common types of cyber threats. It includes malware, phishing, password attacks, drive by downloads, man in the middle and denial of service attacks. Persuade your audience using this Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Malware Through, Phishing Through, Password Attacks Through. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
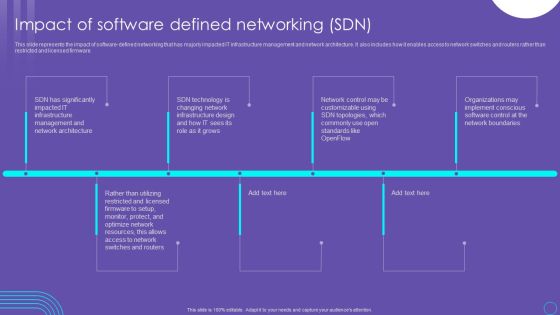
SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF
This slide represents the impact of software defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF from Slidegeeks and deliver a wonderful presentation.
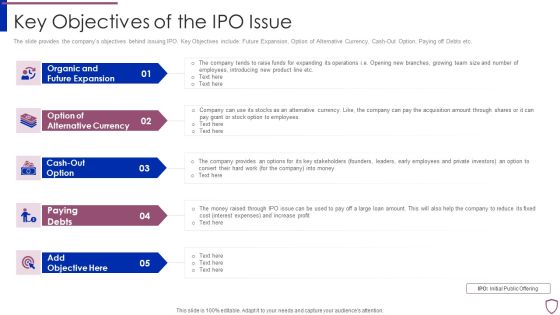
Financing Catalogue For Security Underwriting Agreement Key Objectives Of The IPO Issue Mockup PDF
The slide provides the companys objectives behind issuing IPO. Key Objectives include Future Expansion, Option of Alternative Currency, Cash-Out Option, Paying off Debts etc. Presenting financing catalogue for security underwriting agreement key objectives of the ipo issue mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organic and future expansion, option of alternative currency, cash out option, paying debts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Determine Staff Training Schedule For Skills Enhancement Formats PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting project security administration it determine staff training schedule for skills enhancement formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Three Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Sample
Presenting our jaw dropping three months enterprise it automation machinery road mapping with security and compliance sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Security Governance Procedure Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured security governance procedure management plan ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Weaknesses Of Russian Cyber Cell Pictures PDF
This slide represents the weaknesses of russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Series Of Cyber Security Attacks Against Ukraine 2022 Weaknesses Of Russian Cyber Cell Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Phishing Scams And Attacks Assessment And Cyber Security Training Inspiration PDF
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies To Overcome Cyber Security Workforce Shortage To Address Demand And Supply Gaps Topics PDF
This slide covers different techniques to overcome cyber workforce shortage. It includes expanding talent pool, identifying existing talent, re-train staff and introduce innovations to reduce demand. Persuade your audience using this Strategies To Overcome Cyber Security Workforce Shortage To Address Demand And Supply Gaps Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expand Talent Pool, Identify Existing Talent, Re Train Existing Staff. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Financing Catalogue For Security Underwriting Agreement Geographic Presence Map Of The Company Template PDF
The slide provides the geographic presence of the company along with the number of offices in each country in which the has presence. Presenting financing catalogue for security underwriting agreement geographic presence map of the company template pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like geographic presence map of the company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating.Presenting Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Customer Database, Product Database, Sales Records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF
The following slide depicts impact of advanced transaction monitoring system. It provides information about surveillance, behaviors, patterns, transactions, fraudulent transactions, money laundering, false positives, efficiency, etc. Boost your pitch with our creative KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
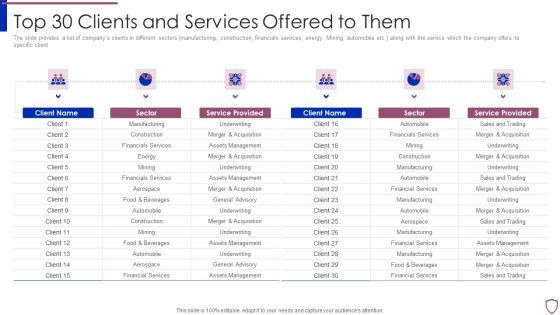
Financing Catalogue For Security Underwriting Agreement Top 30 Clients And Services Offered Structure PDF
The slide provides a list of companys clients in different sectors manufacturing, construction, financials services, energy. Mining, automobile etc. along with the service which the company offers to specific client. Presenting financing catalogue for security underwriting agreement top 30 clients and services offered structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like manufacturing, financials services, construction, automobile. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF
This slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification. Persuade your audience using this Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Supply Chain, Electronic Health Records, Safety Access, Staff Verification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Protection Phishing, Protection Against In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF
This slide shows latest trends and landscape for insider threats. It provides details such as data vulnerable to attacks, enablers of threat, IT assets vulnerable to insider risks, undetected threats, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF. The topics addressed in these templates are Phishing Attempts, Unlock Devices, Unsecured Wifi Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Real Time Assessment Of Security Threats Our Companys Mission Vision And Values Rules PDF
This slide provides the details of our company mission, vision and values to provide unique services to the customers. Presenting real time assessment of security threats our companys mission vision and values rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like our mission, our vision, our values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Half Yearly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Inspiration
Introducing our half yearly enterprise it automation machinery road mapping with security and compliance inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Assessment Matrix Of Cyber Risks IT Security IT Ppt Ideas Display PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting assessment matrix of cyber risks it security it ppt ideas display pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like industrial, multifamily, data center, retail, health care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Dispose Data And Equipment Properly Ppt Infographics Styles PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information security dispose data and equipment properly ppt infographics styles pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Prepare Data Backup For Sensitive Information Ppt Portfolio Slide Download PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Presenting it security prepare data backup for sensitive information ppt portfolio slide download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prepare data backup for sensitive information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
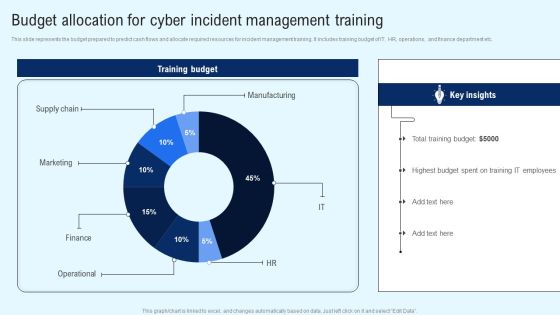
Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Find a pre designed and impeccable Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
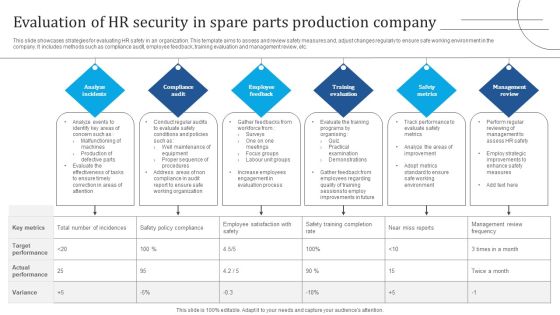
Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF
This slide showcases strategies for evaluating HR safety in an organization. This template aims to assess and review safety measures and, adjust changes regularly to ensure safe working environment in the company. It includes methods such as compliance audit, employee feedback, training evaluation and management review, etc. Presenting Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Analyze Incidents, Compliance Audit, Employee Feedback. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
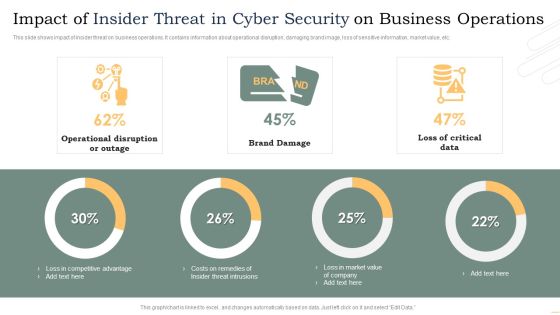
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF
This slide covers KPI dashboard to assess training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Pitch your topic with ease and precision using this Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF. This layout presents information on Major Training Course, Major Satisfactory, Training Course. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. Retrieve professionally designed KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
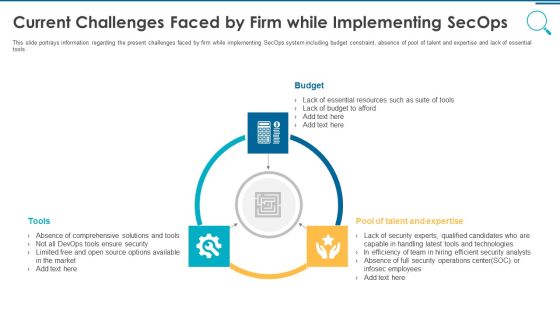
Information And Technology Security Operations Current Challenges Faced By Firm While Implementing Secops Slides PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting information and technology security operations current challenges faced by firm while implementing secops slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Security Solutions Current Challenges Faced By Firm While Implementing Secops Topics PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting organizational security solutions current challenges faced by firm while implementing secops topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
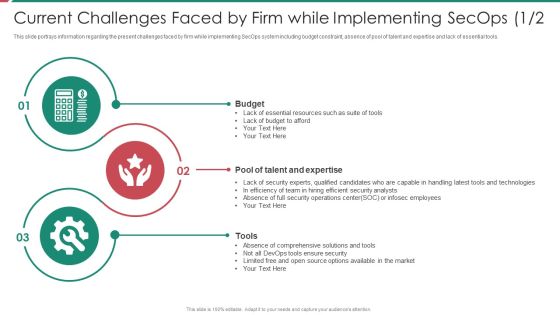
Security And Process Integration Current Challenges Faced By Firm While Implementing Secops Budget Ideas PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting security and process integration current challenges faced by firm while implementing secops budget ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget, tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Current Challenges Faced By Firm While Implementing Secops Tools Clipart PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting security and process integration current challenges faced by firm while implementing secops tools clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget, tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF
This template covers account based marketing strategy such as create content that provide value to the customers. It also depicts that Different types of target accounts require additional content focuses.Presenting Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Competitors Customers, Strategic Importance, Different. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF
template covers guidelines to drive unpaid traffic with Search engine optimization. It also depicts that SEO is the process of optimizing webpages so that they rank higher in search engines.Presenting Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Relevant Information, Inbound Outbound, Engage Positively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF
This template covers search engine optimization guidelines to optimal title length for title tag and to write meta description displayed on the SERPs . Presenting Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Currently Limited, Typically Displays, Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF
This template covers the use of automated software for email marketing. It also depicts that email marketing platforms engage allows users to create multiple sales flow with combination of manual and automated emails and phone calls.Presenting Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Combination Manual, Leads Prioritize, Identify Most. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF
This template covers email marketing strategy such as use of automation email sequences for customers at all different stages in their customer journey . Presenting Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Past Customers, Existing Customers, Assist Businesses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Financing Catalogue For Security Underwriting Agreement Share Allocation Process Clipart PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. Presenting financing catalogue for security underwriting agreement share allocation process clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like in case undersubscription, in case of oversubscription. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF
The slide provides POST IPO dividend distribution policy of the company which covers the type and different ways methods of dividend payment.Presenting Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Stable Dividend, Dividend Payment, General Meeting In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF
The slide provides the companys objectives behind issuing IPO. Key objectives include future expansion, option of alternative currency, cash out option, paying off debts etc. Presenting Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Expansion, Alternative Currency, Paying Debts In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
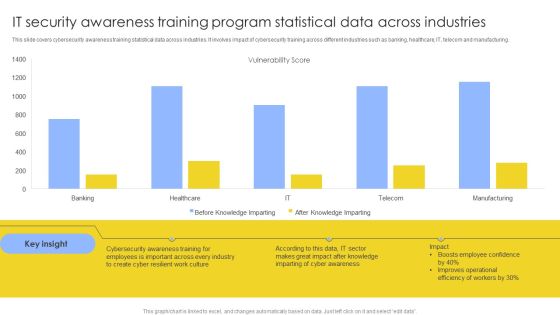
IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF
This slide covers cybersecurity awareness training statistical data across industries. It involves impact of cybersecurity training across different industries such as banking, healthcare, IT, telecom and manufacturing. Showcasing this set of slides titled IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF. The topics addressed in these templates are Vulnerability Score, Cyber Awareness, Improves Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. Find a pre-designed and impeccable Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

 Home
Home