Executive Summary Security

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
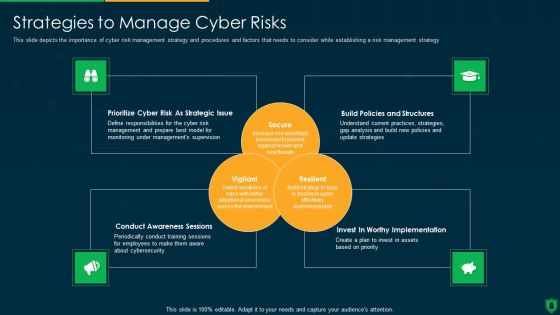
Info Security Strategies To Manage Cyber Risks Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a info security strategies to manage cyber risks ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prioritize cyber risk as strategic issue, build policies and structures, conduct awareness sessions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Workplace Health And Employee Security Coaching Matrix Ppt Slides Guide PDF
The following slide showcases the type of training required and recommended to the specific employee according to their operations. The matrix also includes the training legends such as one representing hazard communication program, two electricity safety program etc. Pitch your topic with ease and precision using this workplace health and employee security coaching matrix ppt slides guide pdf. This layout presents information on employee, operate, electrical apparatus, supervise others. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
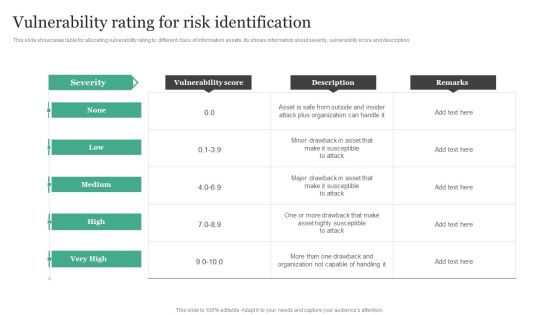
Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF
Retrieve professionally designed Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
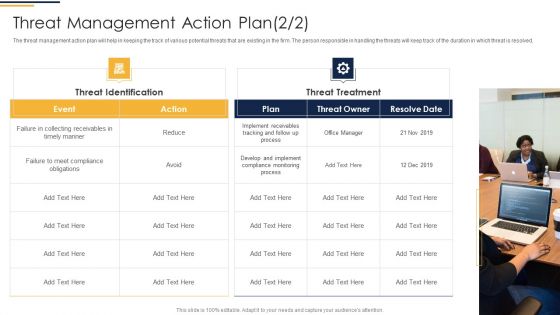
Corporate Security And Risk Management Threat Management Action Plan Introduction PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this corporate security and risk management threat management action plan introduction pdf. Use them to share invaluable insights on potential risk, risk level, action, duration, risk treated and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF. Use them to share invaluable insights on Sprint Report, Product Report, Delivery Method and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Use this Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Determine Incident Reporting By Mobile Devices Departments Mobile Device Security Management Topics PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Deliver and pitch your topic in the best possible manner with this Determine Incident Reporting By Mobile Devices Departments Mobile Device Security Management Topics PDF. Use them to share invaluable insights on Person Involved, Average Cost, Department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Technology Security Operations Secops Staff Training Plan With Cost Introduction PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative information and technology security operations secops staff training plan with cost introduction pdf bundle. Topics like management, vulnerability, business, training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Contingency Plan For Cyber Threat Handling Structure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Presenting corporate security and risk management contingency plan for cyber threat handling structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like contingency solutions, contingency considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
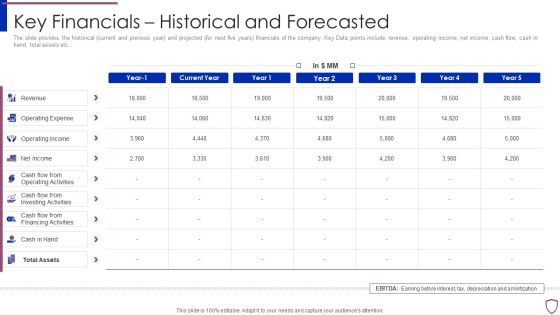
Financing Catalogue For Security Underwriting Agreement Key Financials Historical And Forecasted Template PDF
The slide provides the historical current and previous year and projected for next five years financials of the company. Key Data points include revenue, operating income, net income, cash flow, cash in hand, total assets etc. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement key financials historical and forecasted template pdf bundle. Topics like revenue, operating expense, operating income, net income, cash flow from operating activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
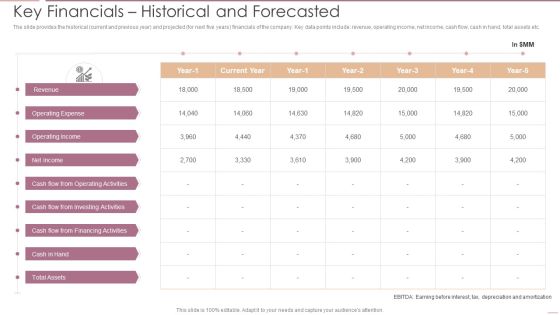
Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF
The slide provides the historical current and previous year and projected for next five year financials of the company. Key data points include revenue, operating income, net income, cash flow, cash in hand, total assets etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF bundle. Topics like Operating Expense, Operating Income, Operating Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF
This template covers the email marketing strategy to leverage the in house email database for email automation, customer retargeting and audience creation. Presenting Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Communications Towards, Automated Messages, Social Platforms. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
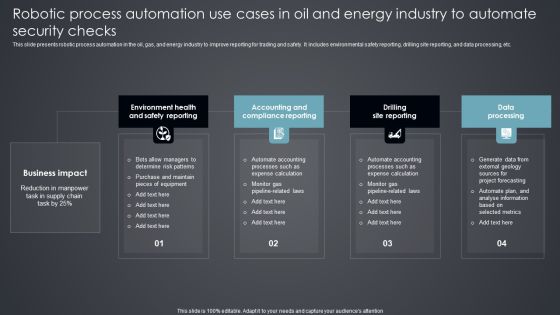
Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF
This slide presents robotic process automation in the oil, gas, and energy industry to improve reporting for trading and safety. It includes environmental safety reporting, drilling site reporting, and data processing, etc. Presenting Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Environment Health, Accounting Compliance Reporting, Drilling Site Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Corporate Security And Risk Management Technological Assessment Of Firm Current Designs PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management technological assessment of firm current designs pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
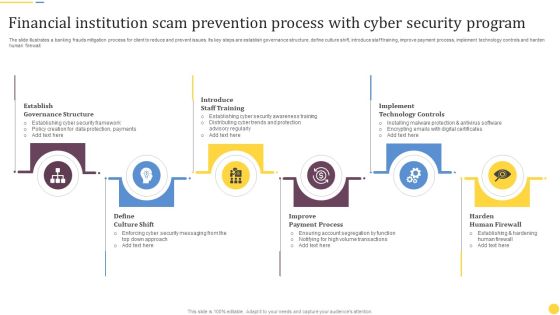
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Certified Information Systems Security Professional CISSP Salary And JOB Details IT Certifications To Enhance Introduction PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Present like a pro with Certified Information Systems Security Professional CISSP Salary And JOB Details IT Certifications To Enhance Introduction PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

KYC Transaction Monitoring System For Business Security Ppt PowerPoint Presentation Complete Deck With Slides
Incorporate this KYC Transaction Monitoring System For Business Security Ppt PowerPoint Presentation Complete Deck With Slides to define the objectives of business performance and how to drive results. List goals and outline a plan to achieve all your enterprise targets using this well crafted complete deck in seventy slides. Walk your audience through the key objectives of your business set-up, especially for customers and inspire them to work with diligence using this predesigned presentation template. Download now with the added assurance of a 100 percent customizable and editable product.

Enhanced Protection Corporate Event Administration How Security Concerns Affect Firm In Present Times Inspiration PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration how security concerns affect firm in present times inspiration pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Prepare A Disaster Recovery Plan IT Security IT Ppt Ideas Graphics Design PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting prepare a disaster recovery plan it security it ppt ideas graphics design pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like make a report of all assets, risk assessment report, identify the importance of assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Picture Of Trade Secret Security Merits Ppt PowerPoint Presentation Model Shapes PDF
Pitch your topic with ease and precision using this picture of trade secret security merits ppt powerpoint presentation model shapes pdf. This layout presents information on trade secret doe not require registration cost, they have immediate effect, they do not require compliance with official procedures such as disclosure of information to any government authority, they are not limited with time unless patents are not revealed to the public. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
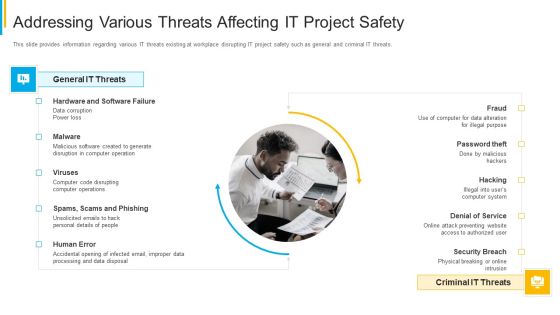
Project Security Administration IT Addressing Various Threats Affecting IT Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Presenting project security administration it addressing various threats affecting it project safety designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like general it threats, criminal it threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Find a pre designed and impeccable CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cloud Computing Security Plan Five Years Roadmap With Key Enablers Designs
Presenting our jaw dropping cloud computing security plan five years roadmap with key enablers designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
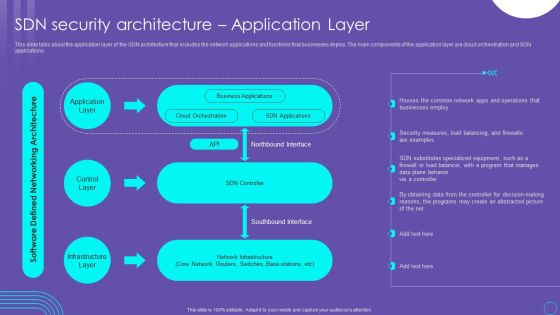
SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF
This slide talks about the application layer of the SDN architecture that includes the network applications and functions that businesses deploy. The main components of the application layer are cloud orchestration and SDN applications. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Computer Security Web Internet Icons PowerPoint Slides And Ppt Diagram Templates
Computer Security Web Internet Icons PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!

Investment Banking Security Underwriting Pitchbook Services Offered By Investment Bank Designs PDF
The slide comprises key services of the company which includes underwriting, general advisory, merger and acquisition advisory, asset management and sales trading solutions. Presenting Investment Banking Security Underwriting Pitchbook Services Offered By Investment Bank Designs PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Advisory Services, Merger And Acquisition, Assets Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Strategies To Manage Cyber Risks Ppt Icon Gallery PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting it security strategies to manage cyber risks ppt icon gallery pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like conduct awareness sessions, prioritize cyber risk as strategic issue, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF
This slide shows plan for managing insider risk with case status. It provides information about users, alert, status, severity, time detected, action plan, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF. This layout presents information on Requires Review, Action Plan, Case Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
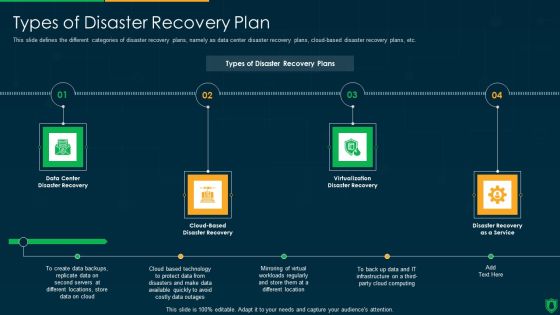
Info Security Types Of Disaster Recovery Plan Ppt PowerPoint Presentation File Clipart PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a info security types of disaster recovery plan ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data center, disaster recovery, cloud based, disaster recovery, virtualization disaster recovery, disaster recovery as a service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

IT Security Awareness Training Program Process To Ensure Effectiveness Diagrams PDF
This slide covers cybersecurity awareness training program process to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Persuade your audience using this IT Security Awareness Training Program Process To Ensure Effectiveness Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Implement Training, Determine Type Training, Identify Training Need. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF
This slide provides information regarding risk response plan for firms in terms of employee safety, development of cross functional team, ensuring liquidity and developing contingency plan, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Corporate Security And Risk Management Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Presenting corporate security and risk management various types of workplace violence and threats designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like threats or threatening behavior, physical assault, property damage, stalking, harassment or intimidation . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. The Information Security Monitor Access To Sensitive And Regulated Data Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Systems Security And Risk Management Plan For Table Of Contents Mockup PDF
Welcome to our selection of the Information Systems Security And Risk Management Plan For Table Of Contents Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
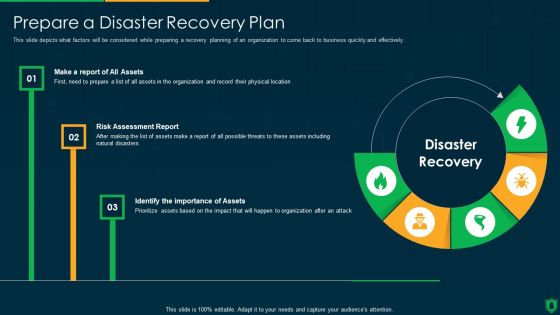
Info Security Prepare A Disaster Recovery Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a info security prepare a disaster recovery plan ppt powerpoint presentation file portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disaster recovery, risk assessment report, identify importance assets, disaster recovery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
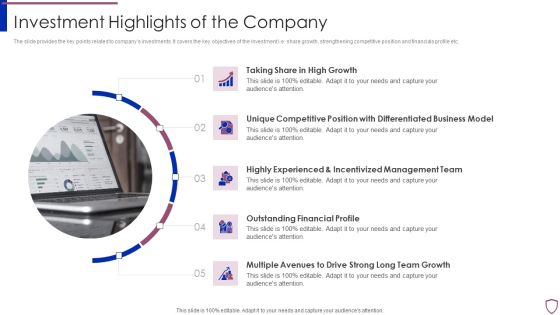
Financing Catalogue For Security Underwriting Agreement Investment Highlights Of The Company Sample PDF
The slide provides the key points related to companys investments. It covers the key objectives of the investment i.e. share growth, strengthening competitive position and financials profile etc. Presenting financing catalogue for security underwriting agreement investment highlights of the company sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like growth, business, management, financial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
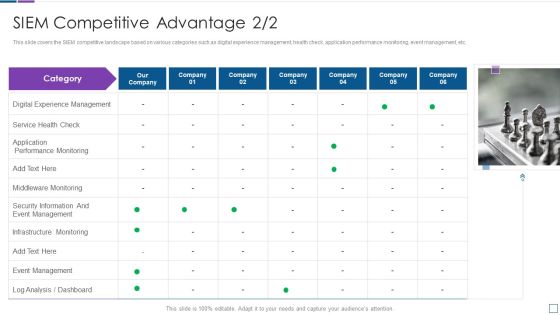
Real Time Assessment Of Security Threats SIEM Competitive Advantage Service Structure PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Presenting real time assessment of security threats siem competitive advantage service structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital experience management, service health check, application performance monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
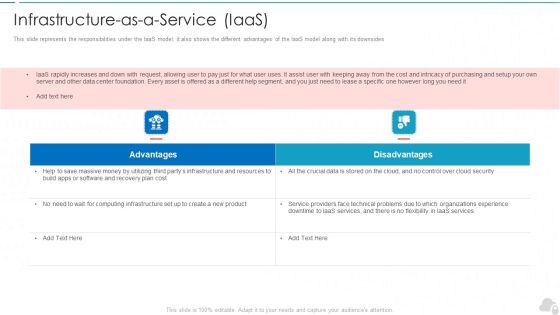
Infrastructure As A Service Iaas Cloud Computing Security IT Ppt Layouts Background Image PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a infrastructure as a service iaas cloud computing security it ppt layouts background image pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advantages, disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
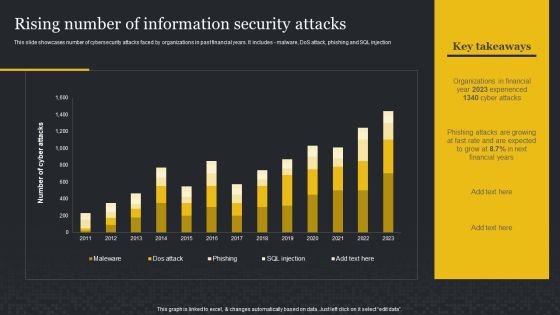
Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Boost your pitch with our creative Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Key Services Analysis For IT Security Risk Management Company Mockup PDF
The following slide explains various services provided by cybersecurity risk management company. It further includes details such as capability assessment, regulatory response and compliance, etc. Presenting Key Services Analysis For IT Security Risk Management Company Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Capability Assessments, Risk Management, Regulatory Response And Compliance, Strategy And Program Design. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Skills Required To Become An Ethical Hacker Security Ppt Layouts Guide PDF
This slide depicts the skills required to become an ethical hacker, such as programming knowledge, scripting languages, networking skills, and understanding databases and servers. Presenting skills required to become an ethical hacker security ppt layouts guide pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like networking, technologies, management, database. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Find a pre-designed and impeccable Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Information Systems Security And Risk Management Plan Swot Analysis Topics PDF
Retrieve professionally designed Information Systems Security And Risk Management Plan Swot Analysis Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cloud Security Assessment Methods Framework Ppt PowerPoint Presentation File Clipart PDF
The slide illustrates a framework for cloud audit methods to describe client responsibility and CSP responsibility. Various methods included are infrastructure, platform and software. Pitch your topic with ease and precision using this Cloud Security Assessment Methods Framework Ppt PowerPoint Presentation File Clipart PDF. This layout presents information on Methods, Infrastructure Iaas, Platform Paas, Client Responsibility. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home