Data Privacy

App Design Model Icon For Security Optimization Ppt PowerPoint Presentation Inspiration PDF
Showcasing this set of slides titled app design model icon for security optimization ppt powerpoint presentation inspiration pdf. The topics addressed in these templates are app design model icon for security optimization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Construction Project Plan With Secure Financing Ppt PowerPoint Presentation Gallery Gridlines PDF
Showcasing this set of slides titled construction project plan with secure financing ppt powerpoint presentation gallery gridlines pdf. The topics addressed in these templates are project tasks, contract writing, contract signing, secure financing, obtain permits, site work. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Guard For Surveillance Vector Icon Ppt PowerPoint Presentation File Inspiration PDF
Showcasing this set of slides titled security guard for surveillance vector icon ppt powerpoint presentation file inspiration pdf. The topics addressed in these templates are security guard for surveillance vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Surveillance Security Camera With Dual Lens Ppt PowerPoint Presentation Gallery Examples PDF
Showcasing this set of slides titled surveillance security camera with dual lens ppt powerpoint presentation gallery examples pdf. The topics addressed in these templates are surveillance security camera with dual lens. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Risk Prevention And Security Management Vector Icon Ppt PowerPoint Presentation File Background Images PDF
Showcasing this set of slides titled risk prevention and security management vector icon ppt powerpoint presentation file background images pdf. The topics addressed in these templates are risk prevention and security management vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Control Strategy With Key Rules Ppt PowerPoint Presentation Gallery Clipart PDF
Showcasing this set of slides titled security control strategy with key rules ppt powerpoint presentation gallery clipart pdf. The topics addressed in these templates are security control, guideline, comments or status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
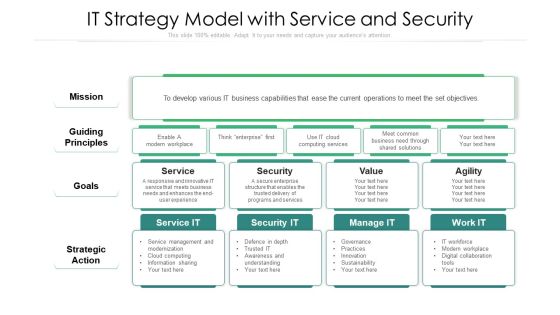
IT Strategy Model With Service And Security Ppt Professional Aids PDF
Showcasing this set of slides titled it strategy model with service and security ppt professional aids pdf. The topics addressed in these templates are strategic action, mission, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud App Security KPI Dashboard For An Enterprise Ppt Model Template PDF
Showcasing this set of slides titled Cloud App Security KPI Dashboard For An Enterprise Ppt Model Template PDF. The topics addressed in these templates are Cloud App Security, KPI Dashboard, Enterprise. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF
Showcasing this set of slides titled Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF. The topics addressed in these templates are Cyber Security, KPI Dashboard, Average Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security KPI Dashboard For Cyberthreats And Anomalies Ppt Professional Gridlines PDF
Showcasing this set of slides titled Security KPI Dashboard For Cyberthreats And Anomalies Ppt Professional Gridlines PDF. The topics addressed in these templates are Security KPI Dashboard, Cyberthreats And Anomalies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security KPI Dashboard To Identify The Risk Of Application Ppt Icon Show PDF
Showcasing this set of slides titled Security KPI Dashboard To Identify The Risk Of Application Ppt Icon Show PDF. The topics addressed in these templates are Risk Levels, Security KPI Dashboard, Risk Of Application. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
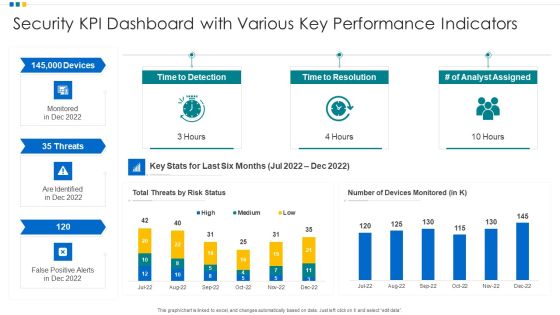
Security KPI Dashboard With Various Key Performance Indicators Ppt Portfolio Objects PDF
Showcasing this set of slides titled Security KPI Dashboard With Various Key Performance Indicators Ppt Portfolio Objects PDF. The topics addressed in these templates are Security Kpi Dashboard, Performance Indicators, Analyst Assigned. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Saas Cloud Security Action Plan Icon Ppt PowerPoint Presentation File Templates PDF
Showcasing this set of slides titled Saas Cloud Security Action Plan Icon Ppt PowerPoint Presentation File Templates PDF. The topics addressed in these templates are Saas Cloud Security, Action Plan, Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Introduction To Secure Access Service Edge SASE Ppt Infographics Demonstration PDF
This slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Want to ace your presentation in front of a live audience Our Introduction To Secure Access Service Edge SASE Ppt Infographics Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Factors To Be Considered Before Selecting Information Technology Process Automation Brochure PDF
This slide showcases elements to think about before choosing automation solution. This template aims on deploying IT services in systematic manner and improving efficiency throughout organization. It covers aspects such as security, user-interface, etc. Persuade your audience using this Factors To Be Considered Before Selecting Information Technology Process Automation Brochure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Understanding Organizational Needs, User Friendly Interface Design, Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Technology Facility Maintenance And Provider Client Standards Checklist Contd Clipart PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a technology facility maintenance and provider client standards checklist contd clipart pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secured encryption, protect servers, internal network, high speed internet access . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF.

Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF
This slide represents the ongoing onslaught of russia on ukraine from december 2015 to jan 2022. Russia has attacked ukraine and other countries in many ways. If you are looking for a format to display your unique thoughts, then the professionally designed Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF
This slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business owned devices, and installation maintenance of operating systems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF
This slide showcases areas where the funds that are collected in series C funding round will be allocated like- marketing, sales and research and development. If you are looking for a format to display your unique thoughts, then the professionally designed Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
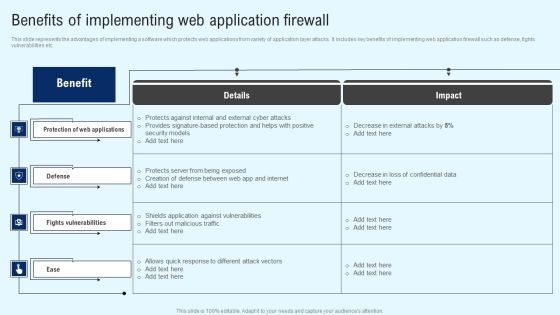
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Boost your pitch with our creative Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF
This slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Showcasing this set of slides titled ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF. The topics addressed in these templates are Customer Expectations, Industry Norms, Internal Business Demands. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computing Technology Industry Association Certification Career Roadmap Professional PDF
The following slide showcases certification roadmap for computing technology industry. It shows accreditations in information security, network and cloud technologies, hardware services infrastructure and IT management and strategy for beginner, intermediate, advanced and expert levels. Persuade your audience using this Computing Technology Industry Association Certification Career Roadmap Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Network And Cloud Technologies, IT Management And Strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF
The following slide highlights components of managed security service along with the expected cost. Software, antivirus and security monitoring are some of the components which will assist the organization in improving its IT security. Showcasing this set of slides titled Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF. The topics addressed in these templates are Security Monitoring, Antivirus, Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computing Technology Prior And Current Comparison Demonstration PDF
The slide showcases before and after scenario of cloud computing. It compares traditional and cloud computing on the basis of various parameters. Pitch your topic with ease and precision using this Computing Technology Prior And Current Comparison Demonstration PDF. This layout presents information on Security, Database, Operating System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF
This slide shows comparison of different managed security service packages like silver, gold, platinum and diamond offered by service providers to the companies. It provides information about malware protection, security awareness, ransomware prevention etc. Pitch your topic with ease and precision using this Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF. This layout presents information on Email Security, Phishing Awareness, Security Awareness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
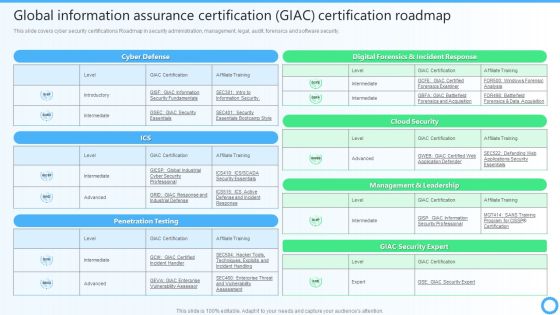
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Robotic Armor IT Types Of Robotic Exoskeleton Passive Exoskeleton Rules PDF
This slide describes the passive type of robotic exoskeletons that boost a users mobility with springs or other sources of motor force. It also includes the areas where they could be used, such as capturing energy, re-distributing weight, locking, and dampening. This is a Robotic Armor IT Types Of Robotic Exoskeleton Passive Exoskeleton Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Energy Capture, Components Redistribute Loads, Boost Persons Mobility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
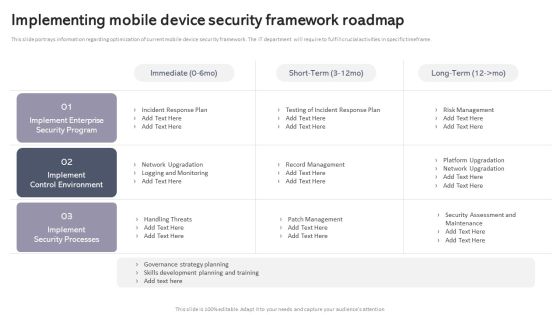
Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Explore a selection of the finest Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Comparison Of Cyber Risk Security Vendors With Pricing And Use Case Formats PDF
Mentioned slide highlights the cyber threat security vendors with uses cases, metrics, intelligence , cyber security and pricing. Pitch your topic with ease and precision using this comparison of cyber risk security vendors with pricing and use case formats pdf. This layout presents information on financial services, cyber security, intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF bundle. Topics like Traditional It Security, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
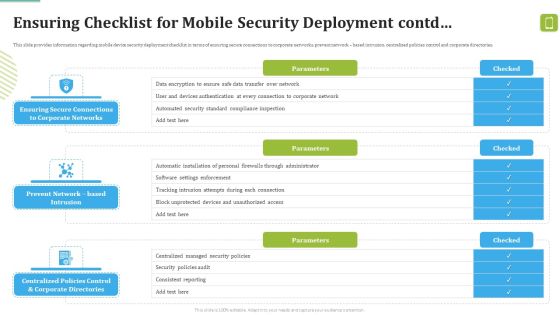
MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF. Use them to share invaluable insights on Against Malicious, Device Security, Automatic Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
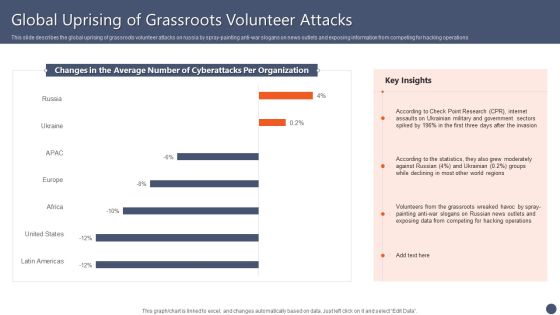
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF
This slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Boost your pitch with our creative Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Role Of Management In Effective Governance Mobile Device Security Management Background PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver and pitch your topic in the best possible manner with this Role Of Management In Effective Governance Mobile Device Security Management Background PDF. Use them to share invaluable insights on Senior Executives, Steering Committees, Effectiveness Reporting and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF

Cyber Security Kpis To Measure Phishing Scams And Attacks Topics PDF
Mentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Showcasing this set of slides titled cyber security kpis to measure phishing scams and attacks topics pdf. The topics addressed in these templates are cyber security kpis to measure phishing scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF
The following slide showcases the impact of software as a service SaaS security in developing business. It includes key elements such as scalability, security, customization, maintenance, availability, IT cost etc. Showcasing this set of slides titled Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF. The topics addressed in these templates are Scalability, Security, Customization, Maintenance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF
This slide highlights security risks occurred in the company. The purpose of this template is to report the severity of security threats. It also includes action steps taken in prevention or resolution of security incidents along with risk categories. Showcasing this set of slides titled Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF. The topics addressed in these templates are Incidents, Category, Severity, Response Action Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Operations Certifications And Training Courses For IT Professionals Topics PDF
This slide exhibits training courses for security operations administrators to enhance their cyber threat management skills. It includes elements such as course, course outline, rating, pricing, frequency, and mode of training. Showcasing this set of slides titled Security Operations Certifications And Training Courses For IT Professionals Topics PDF. The topics addressed in these templates are Security Operations, Fundamental, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.Presenting ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Asset Management, Operational Security, Physical And Environmental. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Google Cloud Services Identity And Security Google Cloud Computing System Themes PDF
This slide describes the identity and security service of Google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security.Presenting Google Cloud Services Identity And Security Google Cloud Computing System Themes PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Resource Manager, Security Scanner, Platform Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
 Home
Home