Data Privacy

Freemium Business Pricing Flow Model Themes PDF
This slide covers freemium revenue generation diagram for ABC company. It includes diagram based on two customers having free and premium product respectively with revenue paid to the company by premium user and multiple features locked for free users.Pitch your topic with ease and precision using this Freemium Business Pricing Flow Model Themes PDF. This layout presents information on Premium Service, Customers Freemium Service, Advanced Features. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF
The following slide highlights key responsibilities of the digitization of security systems team with the position level and requirements. The various positions mentioned in the slide are security engineer, senior security engineer, distinguished security engineer and digitization of security systems manager. Showcasing this set of slides titled Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF. The topics addressed in these templates are Security Engineer, Senior Security Engineer, Security Automation Manager. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
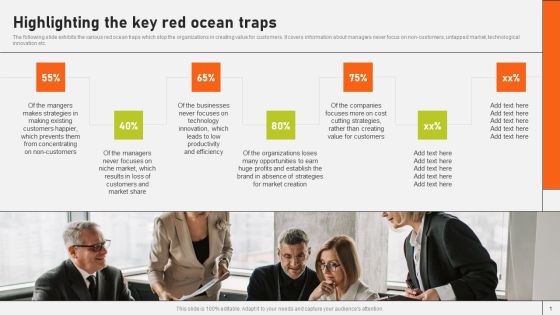
Securing Market Leadership Through Competitive Excellence Highlighting The Key Red Ocean Traps Guidelines PDF
The following slide exhibits the various red ocean traps which stop the organizations in creating value for customers. It covers information about managers never focus on non-customers, untapped market, technological innovation etc. Present like a pro with Securing Market Leadership Through Competitive Excellence Highlighting The Key Red Ocean Traps Guidelines PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Methods To Develop Advanced Essential Elements Of Security Monitoring Plan Formats PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver and pitch your topic in the best possible manner with this methods to develop advanced essential elements of security monitoring plan formats pdf. Use them to share invaluable insights on network security, critical infrastructure, cloud security, application security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Tracking Mobile Device Activities At Workplace Business Mobile Device Security Management Icons PDF
This slide covers information regarding the tracking mobile device activities at workplace with details about MDM managed mobile summary, MDM users, vulnerabilities and severity summary. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Tracking Mobile Device Activities At Workplace Business Mobile Device Security Management Icons PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
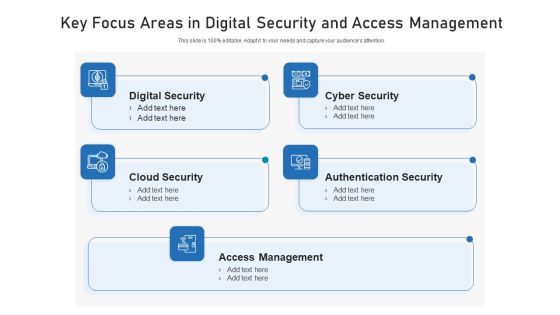
Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF.

Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF
This slide provides information regarding security objectives such as confidentiality, integrity and availability and their role in IoT security compliance. Boost your pitch with our creative Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. Retrieve professionally designed KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

KPI Dashboard To Track Security Risk Events Ppt Pictures Deck PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this kpi dashboard to track security risk events ppt pictures deck pdf. Use them to share invaluable insights on technology risk, system, financial risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
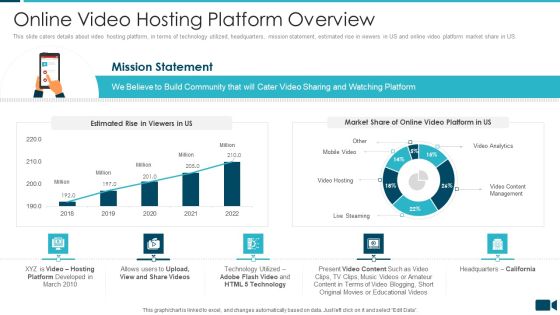
Secured Video Hosting Platform Investor Capital Funding Online Video Hosting Platform Overview Sample PDF
This slide caters details about video hosting platform, in terms of technology utilized, headquarters, mission statement, estimated rise in viewers in US and online video platform market share in US. Deliver and pitch your topic in the best possible manner with this secured video hosting platform investor capital funding online video hosting platform overview sample pdf. Use them to share invaluable insights on online video hosting platform overview and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Food Process Tracking With Control Chart Food Security Excellence Ppt Inspiration Graphics Example PDF
The quality team will use control chart as food quality management tool. It will help in determining the food processes are stable and capable under provided conditions. Deliver an awe inspiring pitch with this creative food process tracking with control chart food security excellence ppt inspiration graphics example pdf bundle. Topics like action plan, resources, chart analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Solutions Business Profile Client Reviews And Testimonials Information PDF
This slides focuses on client testimonials post using our products and services which helps to build credibility and reliability to business and helps in decision making process. Presenting Information Technology Solutions Business Profile Client Reviews And Testimonials Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Been Connected, Evolving Moving, Excellent Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF
This slide depicts the hacking groups such as the anonymous hacker group, conti ransomware gang, threat actors in belarus launching cyber proxy war over ukraine attacks by russia. Find highly impressive Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.Slidegeeks has constructed Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
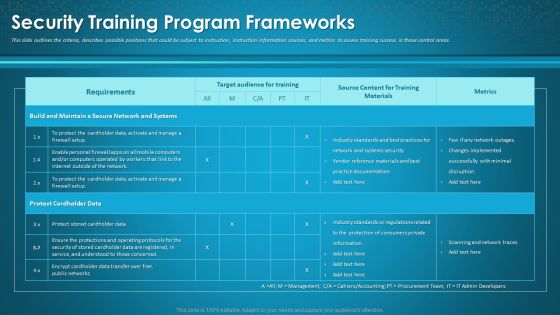
Organizational Network Awareness Staff Learning Security Training Program Frameworks Sample PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this organizational network awareness staff learning security training program frameworks sample pdf. Use them to share invaluable insights on target audience for training, source content, metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Communication Plan For Insider Threat In Cyber Security Awareness Background PDF
This slide shows insider threat awareness communication plan. It provides information about discussions, description, frequency, communication method, etc. Showcasing this set of slides titled Communication Plan For Insider Threat In Cyber Security Awareness Background PDF. The topics addressed in these templates are Discussions, Threat Prevention, Industrial News. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF
This slide defines the web tools to prevent from cyber attacks. It includes information related to different softwares, features and description. Showcasing this set of slides titled Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF. The topics addressed in these templates are Software Tools, Solarwinds Identity Monitor, Free Tool. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Virtual WAN Architecture Secure Access Service Edge Vs SD WAN Ideas PDF
This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. This modern and well-arranged Virtual WAN Architecture Secure Access Service Edge Vs SD WAN Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF
The following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Create an editable Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.

Businesses Digital Technologies E Business Infrastructure Scope Topics PDF
This is a businesses digital technologies e business infrastructure scope topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like services and cloud management, it security and compliance, flexibility, costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF.

Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF.

Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF.

Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. If you are looking for a format to display your unique thoughts, then the professionally designed Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security And Human Resource Services Business Profile Executive Leadership And Management Sample PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security And Human Resource Services Business Profile Executive Leadership And Management Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Amrs In Autonomous Security Robots Asrs Ppt PowerPoint Presentation File Outline PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Amrs In Autonomous Security Robots Asrs Ppt PowerPoint Presentation File Outline PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Chief Information Officers Guide On Technology Plan IT Risk Management Framework Infographics PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Chief Information Officers Guide On Technology Plan IT Risk Management Framework Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
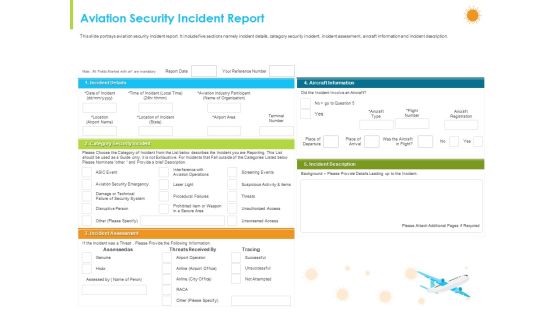
How Aviation Industry Coping With COVID 19 Pandemic Aviation Security Incident Report Template PDF
This slide portrays aviation security incident report. It include five sections namely incident details, category security incident, incident assessment, aircraft information and incident description.Deliver an awe inspiring pitch with this creative how aviation industry coping with COVID 19 pandemic aviation security incident report template pdf. bundle. Topics like suspicious activity and items, aircraft information, category security incident, incident assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Website Audit To Increase Conversion Rate Website Security Auditing And Testing Background PDF
This slide highlights the website security audit which includes host discovery, services inspection, services fingerprinting, site structure, web application analysis, and code assessment. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Website Audit To Increase Conversion Rate Website Security Auditing And Testing Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Business Analysis Non Functional Requirements Ppt Slides
This is a business analysis non functional requirements ppt slides. This is a seven stage process. The stages in this process are reliability, availability, maintainability, safety, security, scalability, usability.

Table Of Contents For Blockchain Technology Framework IT Key Microsoft PDF
Deliver an awe inspiring pitch with this creative table of contents for blockchain technology framework it key microsoft pdf bundle. Topics like technology, security, plans, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Infrastructure Library Permission Administration ITIL Access Management Objectives Template PDF
This is a it infrastructure library permission administration itil access management objectives template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like manage access to services based on policies and actions elaborated in information security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Safety Breach Response Playbook Cyber Security Awareness Training Program Diagrams PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience. Find a pre-designed and impeccable Safety Breach Response Playbook Cyber Security Awareness Training Program Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Find highly impressive Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
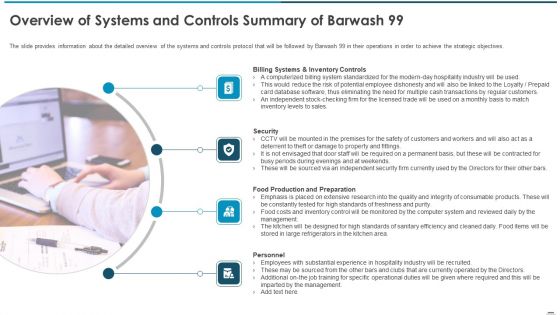
Sell Side Confidential Information Memorandum CIM Pitch Book Overview Of Systems And Controls Summary Brochure PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. This is a sell side confidential information memorandum cim pitch book overview of systems and controls summary brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like billing systems and inventory controls, security, food production and preparation, personnel. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Convergence Strategy Information IT OT Roles And Competencies Ppt Guide PDF
In this slide we have Listed a variety of IT or OT integration competencies that suited certain types of roles. This is a Convergence Strategy Information IT OT Roles And Competencies Ppt Guide PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IT Roles, OT Competencies, Developer, Technical Applications Architect, Information Security Officer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
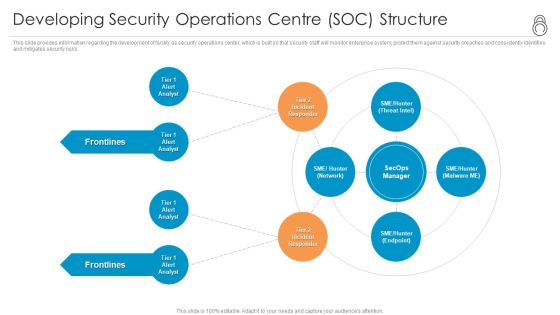
Enhanced Protection Corporate Event Administration Developing Security Operations Centre SOC Structure Formats PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting enhanced protection corporate event administration developing security operations centre soc structure formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Need Of IT Risk Management Professional PDF
The following slide highlights the importance of information risk management which includes safer environment, reduce unexpected events, financial benefits, saves time and effort, and improves security. Presenting Information Technology Threat Mitigation Methods Need Of IT Risk Management Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Financial Benefits, Saves Time And Effort, Improves Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
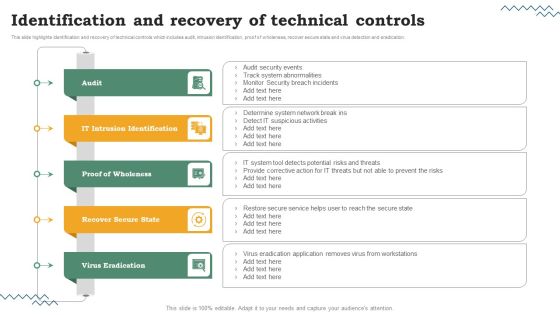
Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Slidegeeks is here to make your presentations a breeze with Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Audit Demanded, Enable Collaboration, Industrialize Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
SIEM Sim Vs Sem Vs SIEM Ppt Icon Format Ideas PDF
This is a siem sim vs sem vs siem ppt icon format ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information management, security event management, security information and event management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Sample Information Management System Powerpoint Guide
This is a sample information management system powerpoint guide. This is a five stage process. The stages in this process are collection and processing, integration , information security , analysis , interface and display.
Server Room Layout Icon With Security Key Ppt PowerPoint Presentation File Slide Portrait PDF
Showcasing this set of slides titled server room layout icon with security key ppt powerpoint presentation file slide portrait pdf. The topics addressed in these templates are server room layout icon with security key. All the content presented in this PPT design is completely editable. Download it and make ajustments in color, background, font etc. as per your unique business setting.

Picture Of Buckingham Palace London With Security Guards Ppt PowerPoint Presentation File Structure PDF
Showcasing this set of slides titled picture of buckingham palace london with security guards ppt powerpoint presentation file structure pdf. The topics addressed in these templates are picture of buckingham palace london with security guards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Protection Vector Showing Secured Bitcoin With Dollar Symbol Ppt PowerPoint Presentation Infographic Template Icon PDF
Showcasing this set of slides titled protection vector showing secured bitcoin with dollar symbol ppt powerpoint presentation infographic template icon pdf. The topics addressed in these templates are protection vector showing secured bitcoin with dollar symbol. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Online Security Theft And Threats Vector Icon Ppt PowerPoint Presentation Ideas Files PDF
Showcasing this set of slides titled online security theft and threats vector icon ppt powerpoint presentation ideas files pdf. The topics addressed in these templates are online security theft and threats vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Of Business Website Vector Icon Ppt PowerPoint Presentation Pictures Infographics PDF
Showcasing this set of slides titled security of business website vector icon ppt powerpoint presentation pictures infographics pdf. The topics addressed in these templates are security of business website vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Measures To Prevent Accident At Workplace Ppt PowerPoint Presentation Pictures Display PDF
Showcasing this set of slides titled security measures to prevent accident at workplace ppt powerpoint presentation pictures display pdf. The topics addressed in these templates are security measures to prevent accident at workplace. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
 Home
Home