Data Encryption

Four Safest Texting Platforms And Applications Infographics PDF
This slide illustrates four safest messaging platforms and applications useful for businesses to have private conversations within the organization. It also includes information about safety features like end-to-end encryption, vanishing messages, chat backups, transparency reports, group chat security, etc.Showcasing this set of slides titled four safest texting platforms and applications infographics pdf The topics addressed in these templates are four safest texting platforms and applications All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Technology Facility Maintenance And Provider Client Standards Checklist Contd Clipart PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a technology facility maintenance and provider client standards checklist contd clipart pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secured encryption, protect servers, internal network, high speed internet access . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
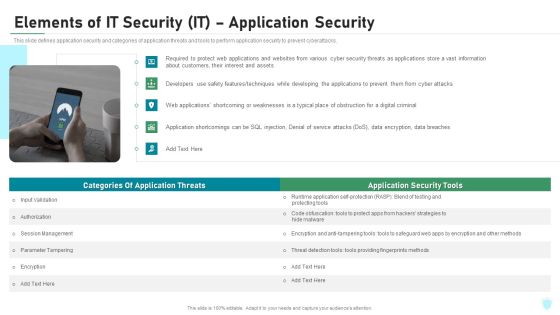
Elements Of IT Security IT Application Security Ppt Layouts Ideas PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a elements of it security it application security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, encryption, authorization, techniques, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Flowchart Depicting Vendor Verification System Assessment Infographics PDF
This slide focuses on the flowchart that depicts the vendor due diligence assessment which covers document submission for security review, vendor shortlisting, compliance, monitoring encryption, ensuring supportive features, evaluating capacity, approval and making final decision, etc. Presenting Flowchart Depicting Vendor Verification System Assessment Infographics PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Required Resources, Conducting Internal Process, Security Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Benefits Of Using A Reverse Proxy Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the benefits of using a reverse proxy server, and it includes load balancing, enhanced security, powerful caching, superior compression, optimized SSL encryption, and monitoring and logging traffic.This is a Benefits Of Using A Reverse Proxy Server Reverse Proxy For Load Balancing Designs PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Load Balancing, Powerful Caching, Superior Compression. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
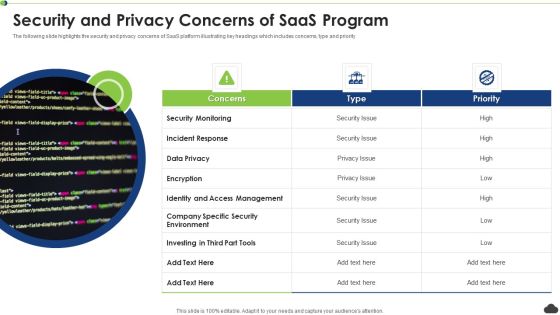
Security And Privacy Concerns Of Saas Program Ppt PowerPoint Presentation File Background PDF
The following slide highlights the security and privacy concerns of SaaS platform illustrating key headings which includes concerns, type and priority. Persuade your audience using this security and privacy concerns of saas program ppt powerpoint presentation file background pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security monitoring, incident response, encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Project Management Software Capital Raising Deck Why Invest With Us Download PDF
Following slide showcases benefits that are offered by company to assure business safety. It include pointers such as consistent backups, development processes, encryption, code review etc. Slidegeeks has constructed Project Management Software Capital Raising Deck Why Invest With Us Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Cloud Computing Application Security Architecture Audit Checklist Structure PDF
The slide shows a checklist containing number of tasks needed to be done while performing application security audit. It includes tasks like developing password policies, making multi factor confirmation mandatory, supervising SaaS license, etc. Showcasing this set of slides titled Cloud Computing Application Security Architecture Audit Checklist Structure PDF. The topics addressed in these templates are Develop Password Policies, Validate Anti Attacking Protections, Set Message Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
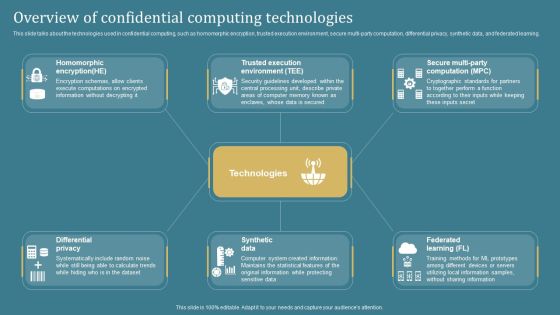
Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Welcome to our selection of the Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
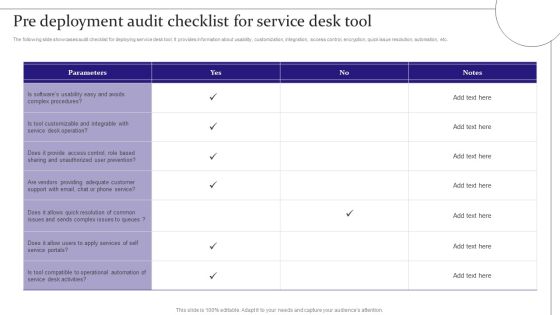
Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. This Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Pre Deployment Audit Checklist For Service Desk Tool Sample PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
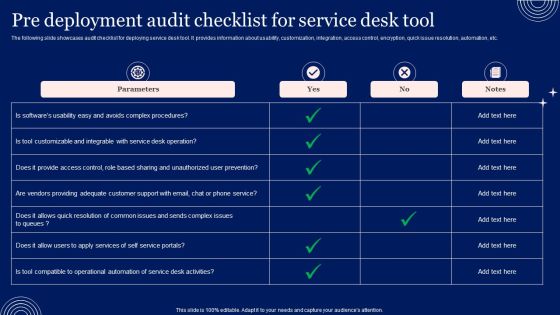
Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc.This Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheImplementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
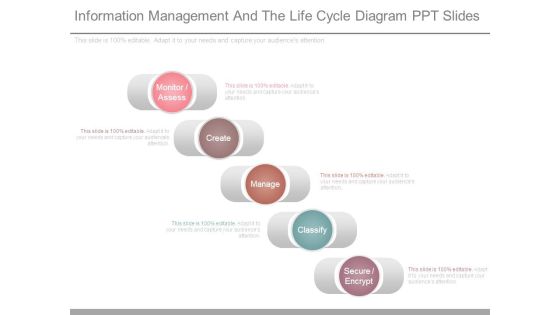
Information Management And The Life Cycle Diagram Ppt Slides
This is a information management and the life cycle diagram ppt slides. This is a five stage process. The stages in this process are monitor assess, create, manage, classify, secure encrypt.

Key Properties Of Blockchain And Distributed Ledger Technology Mockup PDF
Following slide exhibits blockchain technology properties which shows the complete overview of this technology. Programmable, secure, anonymous, time-stamped, verification and transparency are the core properties covered in this slide. Persuade your audience using this Key Properties Of Blockchain And Distributed Ledger Technology Mockup PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Technology, Individually Encrypted, Kept Anonymous. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home