Data Encryption

Cloud Security Checklist Data Encryption Professional PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Presenting Cloud Security Checklist Data Encryption Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protect Keys, Encrypted Data, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Protection Multi Cloud Data Encryption Introduction PDF
This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management. This is a Data Protection Multi Cloud Data Encryption Introduction PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Object Store Appliance, Spectrum Protect, Data Rock Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Encryption And Protection Benchmarks Icon Diagrams PDF
Presenting Data Encryption And Protection Benchmarks Icon Diagrams PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Data Encryption And Protection, Benchmarks Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.This is a Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Encrypted Data, Sensitive Information You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
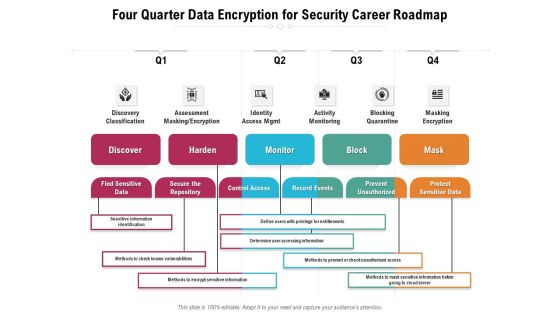
Four Quarter Data Encryption For Security Career Roadmap Sample
We present our four quarter data encryption for security career roadmap sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched four quarter data encryption for security career roadmap sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
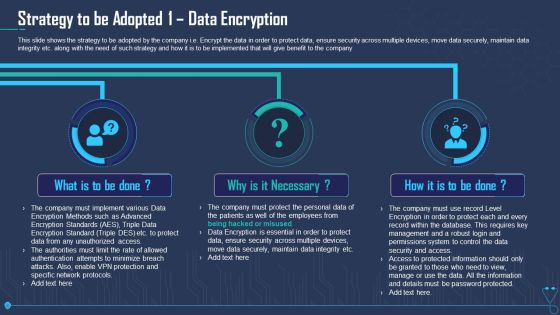
Strategy To Be Adopted 1 Data Encryption Ppt Outline PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt outline pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Year Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured five year data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
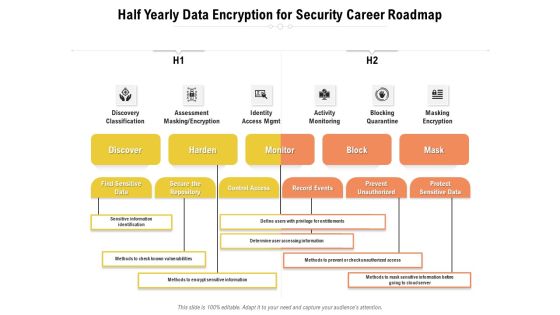
Half Yearly Data Encryption For Security Career Roadmap Structure
Presenting our jaw-dropping half yearly data encryption for security career roadmap structure. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Six Months Data Encryption For Security Career Roadmap Structure
Presenting our innovatively-structured six months data encryption for security career roadmap structure Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Three Months Data Encryption For Security Career Roadmap Summary
Presenting our innovatively-structured three months data encryption for security career roadmap summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Business Data Encryption Security Management Technology Ideas PDF
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting Business Data Encryption Security Management Technology Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authentication, Privacy, Regulatory Compliance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multi Cloud Complexity Management Data Protection Multi Cloud Data Encryption Themes PDF
This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management. Deliver an awe inspiring pitch with this creative Multi Cloud Complexity Management Data Protection Multi Cloud Data Encryption Themes PDF bundle. Topics like Automated Key Management, Spectrum Protect, Cloud Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Scalability Data Protection Multi Cloud Data Encryption Information PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Computing Scalability Data Protection Multi Cloud Data Encryption Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cloud Based Computing Analysis Data Protection Multi Cloud Data Encryption Background PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Based Computing Analysis Data Protection Multi Cloud Data Encryption Background PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Based Computing Analysis Data Protection Multi Cloud Data Encryption Background PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Multi Cloud Infrastructure Management Data Protection Multi Cloud Data Encryption Themes PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management. Find highly impressive Multi Cloud Infrastructure Management Data Protection Multi Cloud Data Encryption Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Multi Cloud Infrastructure Management Data Protection Multi Cloud Data Encryption Themes PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Data Protectionmulticloud Data Encryption Managing Complexity Of Multiple Cloud Platforms Introduction PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management. Find a pre-designed and impeccable Data Protectionmulticloud Data Encryption Managing Complexity Of Multiple Cloud Platforms Introduction PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Data Protectionmulticloud Data Encryption Cloud Computing Complexities And Solutions Structure PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management, This Data Protectionmulticloud Data Encryption Cloud Computing Complexities And Solutions Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Technology Expert Doing Data Encryption For Safety Purpose Ppt PowerPoint Presentation Icon Ideas PDF
Presenting technology expert doing data encryption for safety purpose ppt powerpoint presentation icon ideas pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including technology expert doing data encryption for safety purpose. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analysis Of Various Operating Systems With Data Encryption Ppt PowerPoint Presentation Inspiration Structure PDF
Showcasing this set of slides titled analysis of various operating systems with data encryption ppt powerpoint presentation inspiration structure pdf. The topics addressed in these templates are analysis of various operating systems with data encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Checklist Data Encryption Cloud Computing Security IT Ppt Summary Tips PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a cloud security checklist data encryption cloud computing security it ppt summary tips pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safeguard, data servers, network, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Protect Keys, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF
This slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Strategy To Be Adopted 1 Data Encryption Ppt Gallery Skills PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt gallery skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
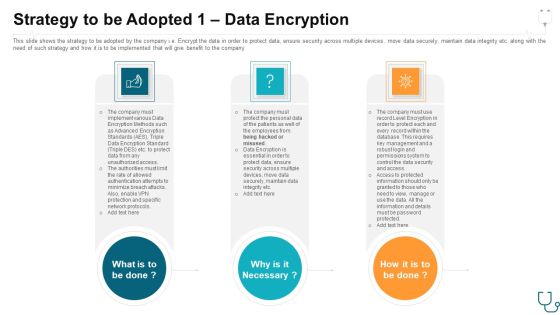
Strategy To Be Adopted 1 Data Encryption Ppt Model Deck PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt model deck pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Characteristics Of Technology Data Encryption Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this characteristics of technology data encryption ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Data Rest Encryption Solutions Ppt PowerPoint Presentation Gallery Rules Cpb
Presenting this set of slides with name data rest encryption solutions ppt powerpoint presentation gallery rules cpb. This is an editable Powerpoint eight stages graphic that deals with topics like data rest encryption solutions to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 1 Data Encryption Microsoft PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting minimize cloud risks medical care business case competition strategy to be adopted 1 data encryption microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protection And Specific Network Protocols, Protect Data, Permissions System, Key Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Email Security Encryption And Data Loss Prevention Roadmap Icons PDF
This is a email security encryption and data loss prevention roadmap icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap, 2017 to 2020. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Encryption And Data Loss Prevention Timeline Template PDF
This is a email security encryption and data loss prevention timeline template pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2013 to 2020. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Scrambling Vs Encryption Ppt PowerPoint Presentation Professional Graphics Download Cpb
Presenting this set of slides with name data scrambling vs encryption ppt powerpoint presentation professional graphics download cpb. This is an editable Powerpoint four stages graphic that deals with topics like data scrambling vs encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cloud Computing Service Framework Encryption Data Integrity Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this cloud computing service framework encryption data integrity ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Email Security Encryption And Data Loss Prevention Proposal Icons Slide Summary PDF
Download our innovative and attention-grabbing email security encryption and data loss prevention proposal icons slide summary pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Email Security Encryption And Data Loss Prevention Table Of Content Slides PDF
Presenting email security encryption and data loss prevention table of content slides pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like project context, our services, action plan, investment, about us, case study, our team, client testimonials, terms and conditions. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Email Security Encryption And Data Loss Prevention 30 60 90 Days Plan Diagrams PDF
This is a email security encryption and data loss prevention 30 60 90 days plan diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Email Security Encryption And Data Loss Prevention Client Testimonial Guidelines PDF
This Slide shows the testimonials of the previous clients who have worked with you. Presenting email security encryption and data loss prevention client testimonial guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like client testimonial. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Email Security Encryption And Data Loss Prevention Your Investment For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed investment of your client into various security softwares. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention your investment for e mail security proposal diagrams pdf bundle. Topics like product, free version, starting price, frequency, per user can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Email Security Encryption And Data Loss Prevention Gantt Chart Information PDF
Your complex projects can be managed and organized simultaneously using this detailed email security encryption and data loss prevention gantt chart information pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well-crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.

Email Security Encryption And Data Loss Prevention Proposal Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought-provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the twenty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
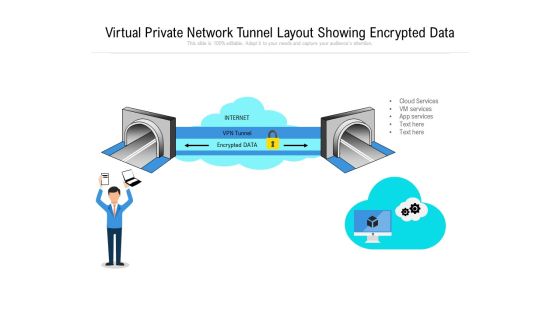
Virtual Private Network Tunnel Layout Showing Encrypted Data Ppt PowerPoint Presentation File Summary PDF
Persuade your audience using this virtual private network tunnel layout showing encrypted data ppt powerpoint presentation file summary pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network tunnel layout showing encrypted data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Redis Cache Data Structure IT Encrypted Password For Securing Redis Settings Formats PDF
This slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. This is a redis cache data structure it encrypted password for securing redis settings formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypted password for securing redis settings. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Encrypt And Create Backup Of Useful Data Ppt PowerPoint Presentation File Icon PDF
The following slide illustrates various methods to encrypt and back-up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Explore a selection of the finest Encrypt And Create Backup Of Useful Data Ppt PowerPoint Presentation File Icon PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Encrypt And Create Backup Of Useful Data Ppt PowerPoint Presentation File Icon PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
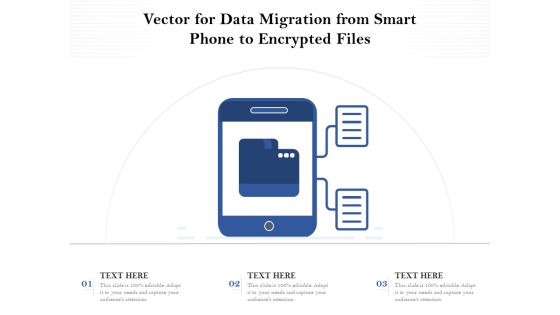
Vector For Data Migration From Smart Phone To Encrypted Files Ppt PowerPoint Presentation Outline Background Images PDF
Presenting vector for data migration from smart phone to encrypted files ppt powerpoint presentation outline background images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vector for data migration from smart phone to encrypted files. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Document Encryption Vector Icon Ppt PowerPoint Presentation Styles Clipart Images
Presenting this set of slides with name document encryption vector icon ppt powerpoint presentation styles clipart images. This is a one stage process. The stage in this process is document encryption vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
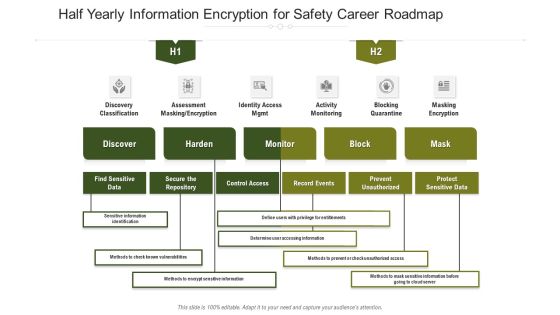
Half Yearly Information Encryption For Safety Career Roadmap Infographics
We present our half yearly information encryption for safety career roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly information encryption for safety career roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
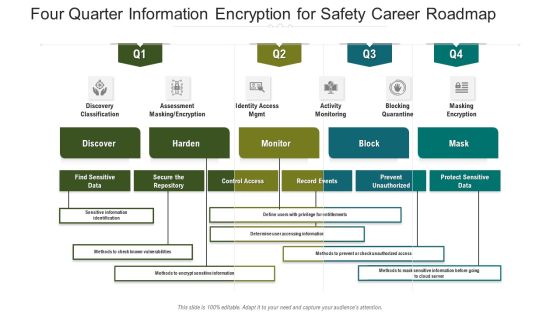
Four Quarter Information Encryption For Safety Career Roadmap Introduction
Presenting our innovatively structured four quarter information encryption for safety career roadmap introduction Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Five Year Information Encryption For Safety Career Roadmap Icons
Introducing our five year information encryption for safety career roadmap icons. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Six Months Information Encryption For Safety Career Roadmap Structure
Introducing our six months information encryption for safety career roadmap structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Three Months Information Encryption For Safety Career Roadmap Structure
Introducing our three months information encryption for safety career roadmap structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Business Information And Application Layers With Protection And Encryption Brochure PDF
This slide covers business application layers with security and encryption with data access logic, presentation logic and business logic.Pitch your topic with ease and precision using this Business Information And Application Layers With Protection And Encryption Brochure PDF. This layout presents information on Organizational Service, Components Duration, Operating System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
End To End Encryption Vector Icon Ppt PowerPoint Presentation Gallery Show PDF
Presenting this set of slides with name end to end encryption vector icon ppt powerpoint presentation gallery show pdf. This is a three stage process. The stages in this process are end to end encryption vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Distributed Ledger Technology Icon With Encryption Symbol Ppt PowerPoint Presentation Gallery Visuals PDF
Persuade your audience using this distributed ledger technology icon with encryption symbol ppt powerpoint presentation gallery visuals pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including distributed ledger technology icon with encryption symbol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Dashboard With Encryption Status Ppt PowerPoint Presentation Gallery Pictures PDF
Presenting this set of slides with name information security dashboard with encryption status ppt powerpoint presentation gallery pictures pdf. The topics discussed in these slides are devices, cost, malware. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe Slides PDF
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Data Mining Implementation Tools For Data Science SAS Template PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption.This is a data mining implementation tools for data science sas template pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong data analysis abilities, report output format, data encryption algorithms You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Organization Cyber Security Dashboard Pictures PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative companys data safety recognition organization cyber security dashboard pictures pdf bundle. Topics like application health, operating systems, encryption status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Technologies To Ensure Data Protection And Privacy Background PDF
The following slide showcases some technologies to administer organizational data privacy and security concerns. It includes elements such as data encryption, change management and auditing, user and behavior analytics UEBA, backup and recovery etc. Presenting Technologies To Ensure Data Protection And Privacy Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Encryption, Change Management And Auditing, Backup And Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Saving Practices Of Disaster Recovery Plan Professional PDF
This slide shows five cloud disaster recovery approaches that every organization should adopt to prevent the loss of crucial data. It includes suitable disaster recovery service provider, data encryption, small and large scale recovery plans, updated disaster recovery plan and proper testing procedure. Presenting Data Saving Practices Of Disaster Recovery Plan Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Encryption, Proper Testing Procedure, Service Provider. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Recognition Organization Cyber Security Dashboard Demonstration PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization cyber security dashboard demonstration pdf. Use them to share invaluable insights on cyber security, key performance, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Analytics IT Tools For Data Science SAS Ppt Ideas Templates PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption. This is a data analytics it tools for data science sas ppt ideas templates pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, data format, sas studio, generation programming language, analysis abilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
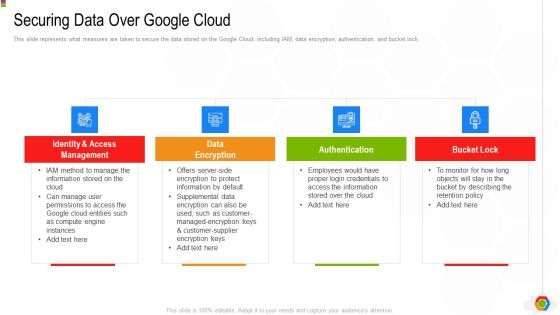
Google Cloud Console IT Securing Data Over Google Cloud Ppt Pictures Slides PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. This is a google cloud console it securing data over google cloud ppt pictures slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identity and access management, data encryption, authentication, bucket lock. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. Presenting Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Data Encryption, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Using Data Science Technologies For Business Transformation Tools For Data Science SAS Introduction PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Using Data Science Technologies For Business Transformation Tools For Data Science SAS Introduction PDF from Slidegeeks and deliver a wonderful presentation.

Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
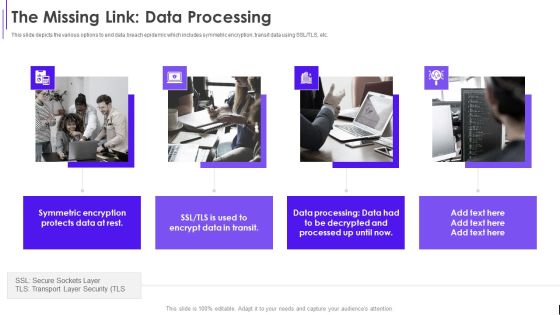
Fundraising Pitch Deck For Evervault The Missing Link Data Processing Ppt Model Summary PDF
This slide depicts the various options to end data breach epidemic which includes symmetric encryption, transit data using SSL or TLS, etc. Presenting Fundraising Pitch Deck For Evervault The Missing Link Data Processing Ppt Model Summary PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Symmetric Encryption, Protects Data, Encrypt Data, Data Processing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
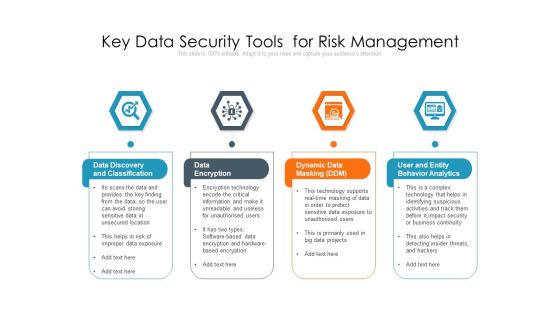
Key Data Security Tools For Risk Management Ppt PowerPoint Presentation Outline Guide PDF
Persuade your audience using this key data security tools for risk management ppt powerpoint presentation outline guide pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including data discovery and classification, data encryption, dynamic data masking ddm, user and entity behavior analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Studies Tools For Data Science SAS Designs PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption. Presenting Information Studies Tools For Data Science SAS Designs PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Strong Data Analysis, Data Format, Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
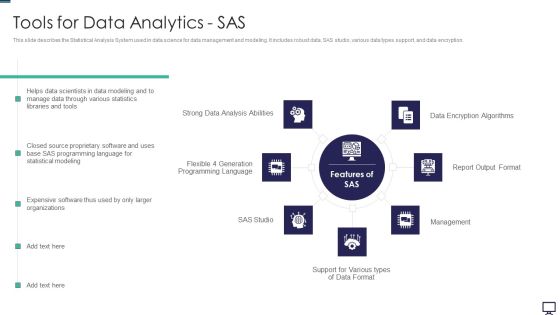
Tools For Data Analytics SAS Ppt Styles Guidelines PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption. This is a tools for data analytics sas ppt styles guidelines pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tools for data analytics sas. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Big Data Architect Tool Selection For Big Data Management Icons PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.This is a Big Data Architect Tool Selection For Big Data Management Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Businesses Frequently, Straight Forward, Either Providing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
VPN Encrypted Connection Vector Icon Ppt PowerPoint Presentation Model Introduction PDF
Presenting vpn encrypted connection vector icon ppt powerpoint presentation model introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including VPN encrypted connection vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
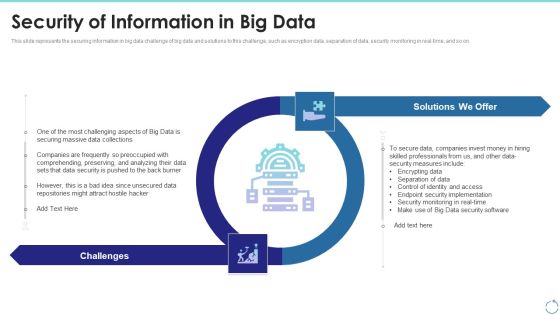
Security Of Information In Big Data Ppt Infographics Layout PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. This is a security of information in big data ppt infographics layout pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, implementation, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Securing Data Over Google Cloud Google Cloud Computing System Professional PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock.Presenting Securing Data Over Google Cloud Google Cloud Computing System Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Protect Information, Compute Engine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
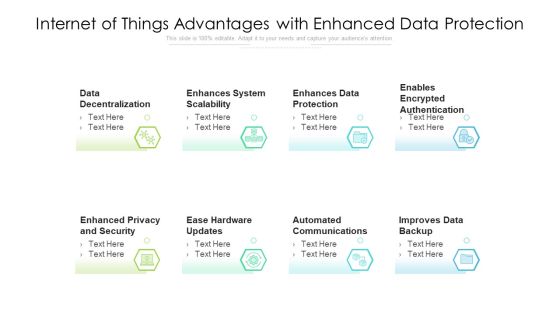
Internet Of Things Advantages With Enhanced Data Protection Ppt PowerPoint Presentation File Background Designs PDF
Presenting internet of things advantages with enhanced data protection ppt powerpoint presentation file background designs pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including system scalability, data protection, encrypted authentication. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF
The purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Create an editable Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Electronic Footprint And Data Privacy Management Tools Professional PDF
This slide mention tools used to manage digital footprint and data privacy. It includes Anti-tracking tools, Private search engines, virtual private networks and website encryption tools. Presenting Electronic Footprint And Data Privacy Management Tools Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Virtual Private Networks, Website Encryption Tools, Private Search Engines. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Security Methods With Disaster Recovery Ppt PowerPoint Presentation Pictures Vector
Presenting this set of slides with name data security methods with disaster recovery ppt powerpoint presentation pictures vector. This is a five stage process. The stages in this process are data deduplication, disaster recovery, the encryption algorithm, disk mirroring and storage replication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
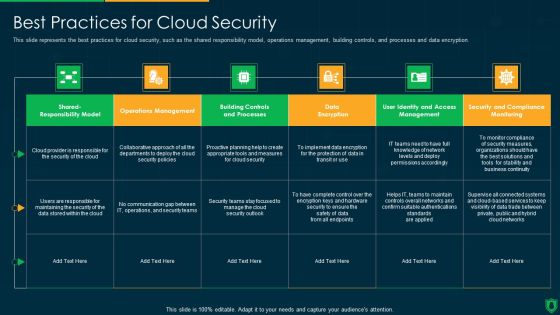
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Evervault Capital Investment Elevator Pitch Deck The Missing Link Data Processing Portrait PDF
This slide depicts the various options to end data breach epidemic which includes symmetric encryption, transit data using SSL or TLS, etc. This is a evervault capital investment elevator pitch deck the missing link data processing portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like the missing link data processing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Online Risk Mitigation Procedure In Cloud Migration Mockup PDF
The purpose of this slide is to represent process for mitigating digital risk while migrating data to cloud platform. It includes various steps such as understand shared responsibility model, migrating data in various stages, understanding regulatory requirements, encrypting data and centralizing management and monitoring. Presenting Online Risk Mitigation Procedure In Cloud Migration Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Migrate Data, Encrypt Data, Centralize Management Monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Optimizing Digital Marketing Strategy Use Cloud Technology To Manage Data While Slides PDF
This template covers the process of using cloud technology for managing data. It also includes the benefits of cloud technology, such as encrypting all data and defining who has access. Slidegeeks is here to make your presentations a breeze with Optimizing Digital Marketing Strategy Use Cloud Technology To Manage Data While Slides PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Best Practices For Cloud Security Ppt Infographics Show PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. This is a best practices for cloud security ppt infographics show pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processes, management, monitoring, data encryption, implement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Best Practices For Cloud Security Ppt Icon Pictures PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting it security best practices for cloud security ppt icon pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operations management, security and compliance monitoring, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cost Estimation For Strategy Implementation Ppt Model Icon PDF
The slide shows the estimation of major cost involved in the next four years 2021 to 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Deliver an awe inspiring pitch with this creative cost estimation for strategy implementation ppt model icon pdf bundle. Topics like data encryption, increasing employee awareness, restricted access to physical devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Assessment Of Data Loss Prevention Software Structure PDF
Following slide illustrates comparison of various data loss prevention softwares used in the retail industry. The comparison is drawn on the features such as detecting suspicious activity, endpoint protection platform, enforced encryption etc. Showcasing this set of slides titled Comparative Assessment Of Data Loss Prevention Software Structure PDF. The topics addressed in these templates are System Audit, Pricing, Enforced Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Software Services Business Profile Digital Products And Solutions Ppt PowerPoint Presentation File Infographics PDF
This slide depicts four product categories which include software, products, platforms, and others. Key solutions under these categories are remote meeting software, data encryption tool, operating system, simulation software, antivirus protection, surveillance infrastructure, engineering design tool, and source code development platform. This is a Software Services Business Profile Digital Products And Solutions Ppt PowerPoint Presentation File Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Remote Meeting Software, Data Encryption Tool, Operating System. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Organization Cyber Security Dashboard Ppt Icon Sample PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard ppt icon sample pdf. Use them to share invaluable insights on makes and models, application health, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
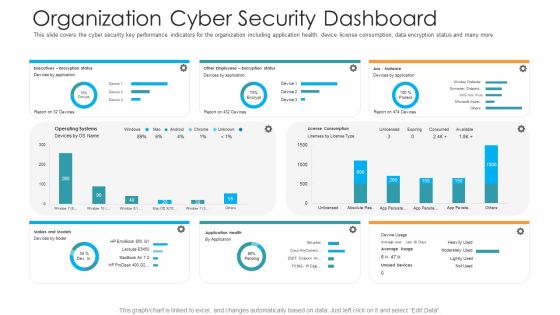
Organization Cyber Security Dashboard Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on executives, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Network Security Awareness Staff Learning Organization Cyber Security Dashboard Elements PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization cyber security dashboard elements pdf. Use them to share invaluable insights on organization cyber security dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organization Cyber Security Dashboard Ppt Show Outfit PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe inspiring pitch with this creative organization cyber security dashboard ppt show outfit pdf bundle. Topics like operating systems, license consumption, makes and models, other employees can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Five Phases Of Data Project Lifecycle Management Formats PDF
This slide covers five phases of data lifecycle management. It involves generate and collect data, manage, use and share, archive and destroy data.Persuade your audience using this Five Phases Of Data Project Lifecycle Management Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Constantly Producing, Encryption Cleansed, Protection Regulations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
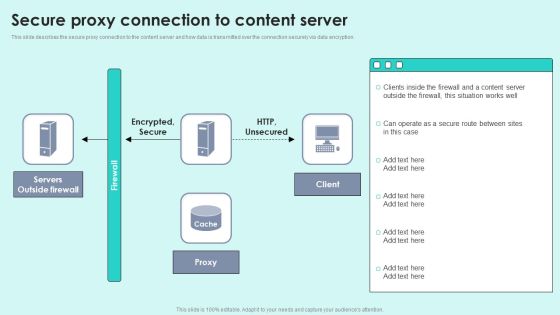
Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Configuration Management Audit Checklist Professional PDF
This slide covers cloud infrastructure management audit checklist. It involves data encryption, security controls, tested visibility, fully independent data centres, customer penetration and vulnerability.Presenting Cloud Computing Configuration Management Audit Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Management, Customer, Data Centres. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Challenge And Solutions 2 Cloud Threats And Security Ppt Outline Design Inspiration PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt outline design inspiration pdf bundle. Topics like implement data encryption techniques to eliminate risk of infiltration, security and compliance risks are major considerations for the company, professional business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Gallery Background Images PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Deliver an awe inspiring pitch with this creative strategies for reducing cybersecurity risks in abs healthcare company ppt gallery background images pdf bundle. Topics like set strong passwords and use data encryption, ensure proper data management and use updated software, proper employee training, protect devices that can be physically accessed, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Rules PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Presenting strategies for reducing cybersecurity risks in abs healthcare company rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like set strong passwords and use data encryption, proper employee training, protect devices that can be physically accessed, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF bundle. Topics like Implement Information, Data Encryption, Implement Advanced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Best Practices For Cloud Security Ppt Gallery Visuals PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this information technology security best practices for cloud security ppt inspiration example file pdf. Use them to share invaluable insights on best practices for cloud security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Timeline Deploying Iot Into Logistics Department Introduction PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver an awe inspiring pitch with this creative Timeline Deploying Iot Into Logistics Department Introduction PDF bundle. Topics like Preparing Secondary Layer, Planning And Research, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline Deploying Iot Into Logistics Department Clipart PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver an awe inspiring pitch with this creative Timeline Deploying Iot Into Logistics Department Clipart PDF bundle. Topics like Planning And Research, Preparing Secondary Layer, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. This Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today

Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
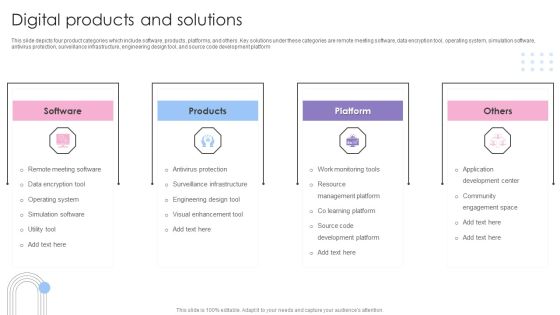
Software Products And Solutions Firm Details Digital Products And Solutions Slides PDF
This slide depicts four product categories which include software, products, platforms, and others. Key solutions under these categories are remote meeting software, data encryption tool, operating system, simulation software, antivirus protection, surveillance infrastructure, engineering design tool, and source code development platform. This is a Software Products And Solutions Firm Details Digital Products And Solutions Slides PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Software, Products, Platform, Others. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Secure Application Layer In Platform Services Topics PDF
This slide showcases ways to secure the application layer in platform services to the attainment of protection against security risks. It also includes vendor lock-in, threat modeling, mapping, testing, etc. Presenting Strategies To Secure Application Layer In Platform Services Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Probability, Threat Modeling, Data Encryption Rest Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF
The following slide highlights cloud implementation key challenges and solutions to monitor business costs, improve security and manage capacity requirements. It includes challenges such as mounting costs, technology drag, concerns of cloud security and solutions such as regular accounting, budgeting, data encryption etc. Pitch your topic with ease and precision using this Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF. This layout presents information on Challenges, Description, Solutions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home