Data Encryption

Mitigation Strategies To Overcome Digital Marketing Tasks Outsourcing Risks Formats PDF
The purpose of this slide is to highlight the multiple strategies that must be followed by the business organizations to overcome digital marketing outsourcing risks. The major solutions are preparation of high level marketing campaigns plans, sharing sensitive data through encrypted channels etc. Create an editable Mitigation Strategies To Overcome Digital Marketing Tasks Outsourcing Risks Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Mitigation Strategies To Overcome Digital Marketing Tasks Outsourcing Risks Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cloud Security Checklist Networking Elements PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting Cloud Security Checklist Networking Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Network, Encrypt Critical Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

ITIL Strategy Service Excellence Client Standards Checklist Contd Ppt PowerPoint Presentation Styles Example PDF
Presenting this set of slides with name itil strategy service excellence client standards checklist contd ppt powerpoint presentation styles example pdf. This is a one stage process. The stages in this process are genuine anti spam solution, vendor supported server, licensed firewall between internal, secured encryption, wireless data traffic, environment, high speed internet access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
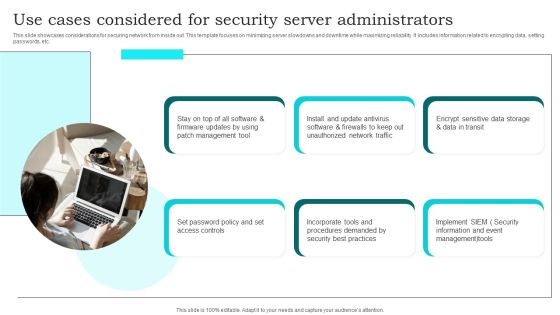
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF
This slide represents e banking security measures and features. It includes login details, encrypted data, account management and two factor authorization. This Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Canva Pro Business Profile Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in app permissions. Presenting Business Profile Canva Security Processes And Systems Elements PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Data Security, Monitoring, Secure Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Picture Editing Company Outline Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in- app permissions. Welcome to our selection of the Picture Editing Company Outline Canva Security Processes And Systems Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

General Outlook Of Ransomware Attack Portrait PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Deliver and pitch your topic in the best possible manner with this General Outlook Of Ransomware Attack Portrait PDF. Use them to share invaluable insights on Tactics Influence, Employees Ransomware, Personal Encrypted and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Increasing Consumer Engagement With Database Solutions To Overcome Database Marketing Template PDF
The purpose of this slide is to showcase multiple solutions which can be undertaken to overcome database marketing challenges. Information covered in this slide is related to updating customer data, using encryption, customer segmentation, etc. Slidegeeks is here to make your presentations a breeze with Increasing Consumer Engagement With Database Solutions To Overcome Database Marketing Template PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Privacy Protection Rankings Of OTT Texting Platforms Template PDF
This slide showcase privacy protection rankings of over the top OTT messaging platforms which can be referred by businesses to choose amongst the best and safest texting application for protection of company data. It includes information about end to end encryption, protection of privacy and by default service. It also provides information about features and costs Showcasing this set of slides titled privacy protection rankings of ott texting platforms template pdf The topics addressed in these templates are optional services providing, encryption mechanism, purchases starting All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
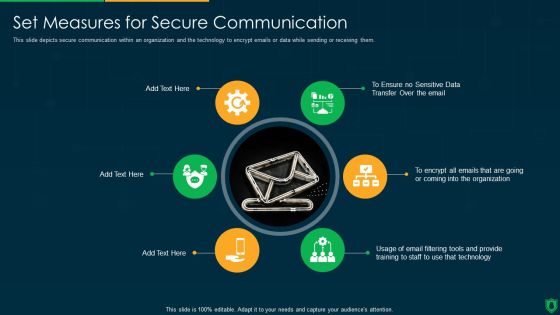
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
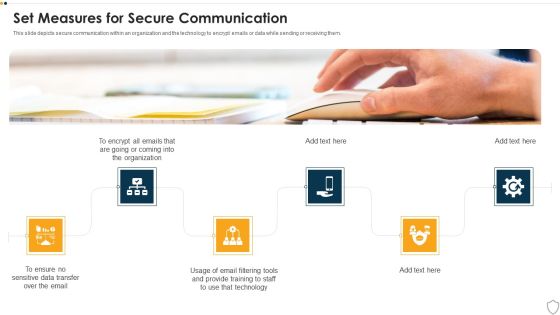
IT Security Set Measures For Secure Communication Ppt Infographic Template Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a it security set measures for secure communication ppt infographic template background designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, training, organization, data transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
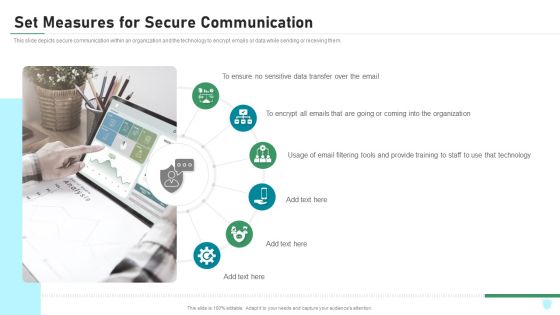
Set Measures For Secure Communication IT Security IT Ppt Styles Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting set measures for secure communication it security it ppt styles background designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data transfer, organization, technology, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Set Measures For Secure Communication Ppt Visual Aids Show PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting cybersecurity set measures for secure communication ppt visual aids show pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like organization, technology, email. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Software Application Layers Used In OSI Model Ppt Inspiration Themes PDF
This slide shows the different software layers that are used in OSI model to encrypt or decrypt the coded data into plain text. It includes session establishment in session layer, translation of data in presentation layer, and network application layer. Persuade your audience using this Software Application Layers Used In OSI Model Ppt Inspiration Themes PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Session Layer, Presentation Layer, Application Layer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Technology Facilities Governance Client Standards Checklist Contd Icons PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a information technology facilities governance client standards checklist contd icons pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect servers, high speed internet access, secured encryption, wireless data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information General Outlook Of Ransomware Attack Summary PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Find highly impressive Prevention Of Information General Outlook Of Ransomware Attack Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Prevention Of Information General Outlook Of Ransomware Attack Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Find highly impressive Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cybersecurity Awareness Program To Prevent Attacks General Outlook Of Ransomware Attack Themes PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF
This slide shows cryptography techniques for phone oriented business data. The purpose of this slide is to highlight main techniques for building phone security policy. It include techniques such as simple codes, symmetric encryption and hashing, etc. Presenting Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Simple Codes, Symmetric Encryption, Asymmetric Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Leverage Strong And Complex Password Management Ppt PowerPoint Presentation File Icon PDF
The following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Do you know about Slidesgeeks Leverage Strong And Complex Password Management Ppt PowerPoint Presentation File Icon PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
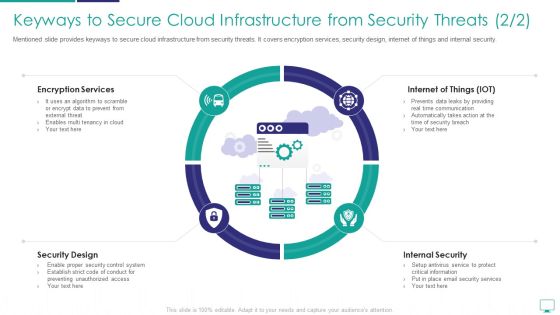
Keyways To Secure Cloud Infrastructure From Security Threats Formats PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a keyways to secure cloud infrastructure from security threats formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encryption services, internet of things, security design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
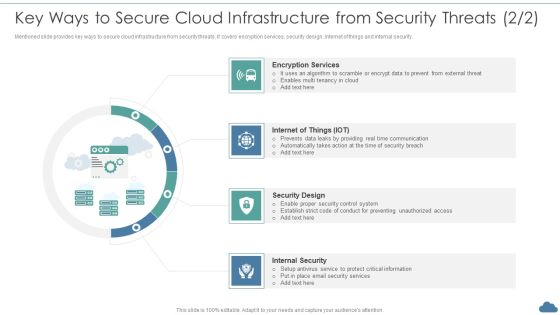
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
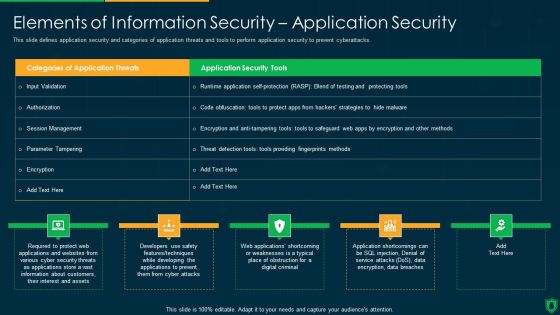
Info Security Elements Of Information Security Application Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Deliver and pitch your topic in the best possible manner with this info security elements of information security application security ppt powerpoint presentation file graphics download pdf. Use them to share invaluable insights on application security tools, parameter tampering, encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
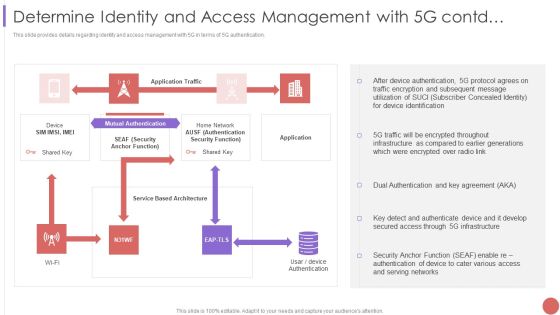
Determine Identity And Access Management With 5G Contd Structure PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Determine Identity And Access Management With 5G Contd Structure PDF Use them to share invaluable insights on Mutual Authentication, Device Authentication, Traffic Encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reverse Proxy Server IT Secure Client Connection To Proxy And Secure Proxy Connection Ppt Infographic Template Design Inspiration PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. This is a reverse proxy server it secure client connection to proxy and secure proxy connection ppt infographic template design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server outside firewall, encrypted, secure, proxy, client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Dashboard Showing IT Risk Control Strategies Risk Management Portrait PDF
This slide shows the dashboard that depicts the information technology risk management which focuses on the percentage of potential risks, risk analysis progress, response progress, risk rating breakdown with vulnerabilities such as encryption vulnerabilities, physical security , etc. Showcasing this set of slides titled Dashboard Showing IT Risk Control Strategies Risk Management Portrait PDF. The topics addressed in these templates are Risk Analysis Progress, Risk Heat Map, Action Plan Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
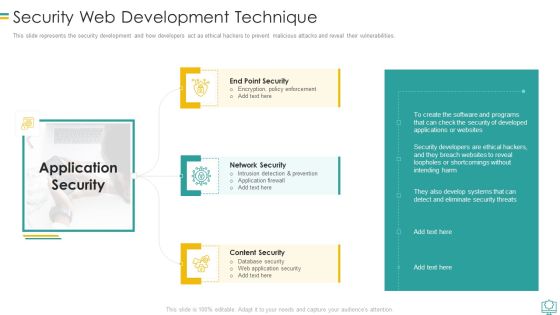
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Methods To Develop Advanced Cybersecurity Monitoring Tools To Be Implemented Guidelines PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative methods to develop advanced cybersecurity monitoring tools to be implemented guidelines pdf bundle. Topics like network security monitoring, encryption tool, web vulnerability scanning tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Welcome to our selection of the 1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
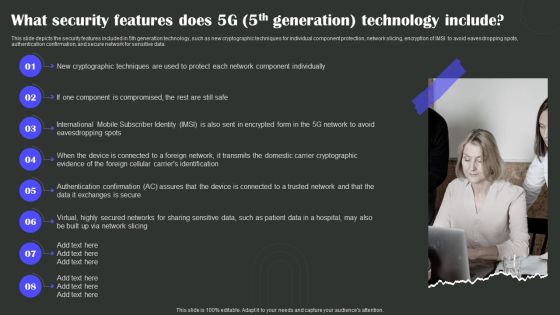
What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Present like a pro with What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Explore a selection of the finest Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
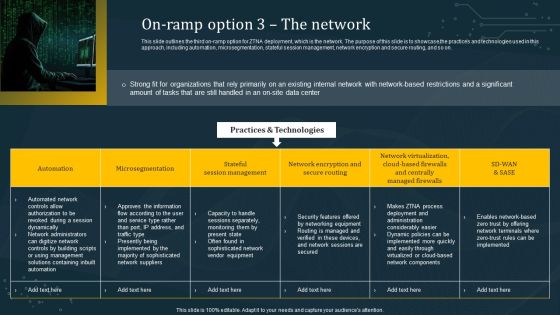
On Ramp Option 3 The Network Structure PDF
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you know about Slidesgeeks On Ramp Option 3 The Network Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
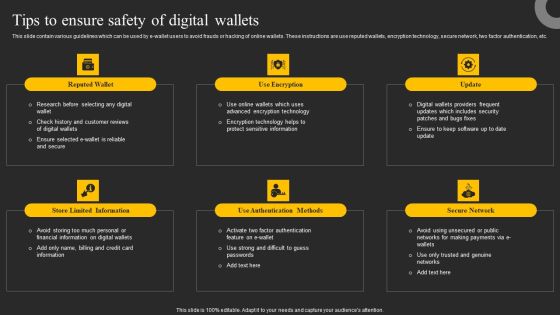
Tips To Ensure Safety Of Digital Wallets Ppt Summary Slide Download PDF
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc. Welcome to our selection of the Tips To Ensure Safety Of Digital Wallets Ppt Summary Slide Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
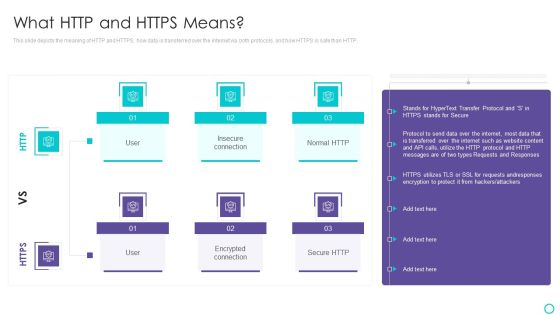
Website Designing And Development Service What HTTP And HTTPS Means Information PDF
This slide depicts the meaning of HTTP and HTTPS, how data is transferred over the internet via both protocols, and how HTTPS is safe than HTTP.Deliver an awe inspiring pitch with this creative Website Designing And Development Service What HTTP And HTTPS Means Information PDF bundle. Topics like Encrypted Connection, Transferred Over The Internet, Hackers Or Attackers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Website Programming IT What HTTP And HTTPS Means Ppt PowerPoint Presentation File Model PDF
This slide depicts the meaning of HTTP and HTTPS, how data is transferred over the internet via both protocols, and how HTTPS is safe than HTTP. Deliver and pitch your topic in the best possible manner with this website programming it what http and https means ppt powerpoint presentation file model pdf. Use them to share invaluable insights on insecure connection, encrypted connection, secure http and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
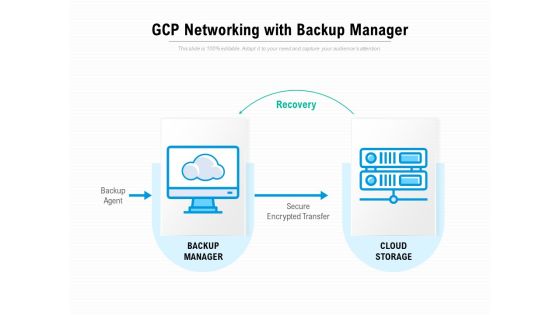
Gcp Networking With Backup Manager Ppt PowerPoint Presentation Portfolio Model
Presenting this set of slides with name gcp networking with backup manager ppt powerpoint presentation portfolio model. This is a one stage process. The stages in this process are recovery, backup agent, backup manager, cloud storage, secure encrypted transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Analyzing 5G Impact Over 4G Difference Between 4G And 5G Based On Ofdm Encoding Graphics PDF
This slide talks about another factor of difference between 4G and 5G, which is orthogonal frequency-division multiplexing, and is used in 5G technology. Deliver and pitch your topic in the best possible manner with this Analyzing 5G Impact Over 4G Difference Between 4G And 5G Based On Ofdm Encoding Graphics PDF. Use them to share invaluable insights on Orthogonal Frequency, Division Multiplexing, Encrypts Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Exploitation IT Backup Of Sensitive Information Elements PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a cyber exploitation it backup of sensitive information elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like services, manipulation, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Forensic Fraud Accounting Flow And Blockchain Integration Clipart PDF
This slide covers flow of financial fraud investigation and use of blockchain technology. It includes blockchain to store the entire case documents with evidences and reports in an encrypted form. Presenting Forensic Fraud Accounting Flow And Blockchain Integration Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Analysis Tools, Blockchain Technology, Process Initiated. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
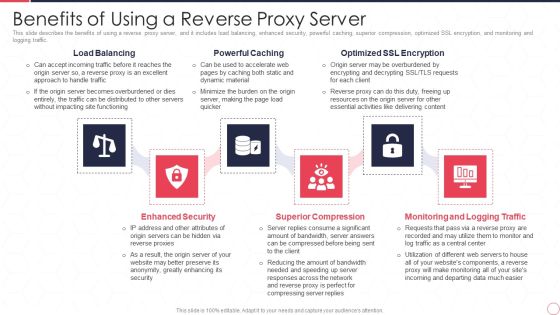
Reverse Proxy Server IT Benefits Of Using A Reverse Proxy Server Ppt Model Designs PDF
This slide describes the benefits of using a reverse proxy server, and it includes load balancing, enhanced security, powerful caching, superior compression, optimized SSL encryption, and monitoring and logging traffic. This is a reverse proxy server it benefits of using a reverse proxy server ppt model designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like load balancing, powerful caching, optimized ssl encryption, enhanced security, superior compression, monitoring and logging traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF
The following slide depicts the minimum security standards to protect software and platform as a service SaaS and PaaS. It includes elements such as encryption, authentication, security and privacy etc. along with high, medium and low risk level. Pitch your topic with ease and precision using this Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF. This layout presents information on Required Actions, Encryption, Security And Privacy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Technology Update With Air Cloud Servers Ppt Styles Inspiration PDF
Presenting technology update with air cloud servers ppt styles inspiration pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including firmware control, upgradation encryption, electronic control, management, cloud servers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Operational Technology Safety Network Model With Threat Forensics Ppt PowerPoint Presentation Example File PDF
Presenting operational technology safety network model with threat forensics ppt powerpoint presentation example file pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including threat forensics, e2ee encryption, change management, usb sheepdip. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Ppt Continual Way To Prevent Manufacture Losses Seven Steps PowerPoint Templates
PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-This PowerPoint Diagram shows you the continual way to prevent manufacture losses in any Business related Activities. It is shown by different shades of Brown color. -PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words
Ppt Successive Representation Of 7 Stages An Arrow PowerPoint Templates
PPT successive representation of 7 stages an arrow PowerPoint Templates-This PowerPoint Diagram shows you the Successive Representation of five approaches on the Arrow. It shows the successive concepts used in a procedure. You can change color, size and orientation of any icon to your liking.-PPT successive representation of 7 stages an arrow PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words
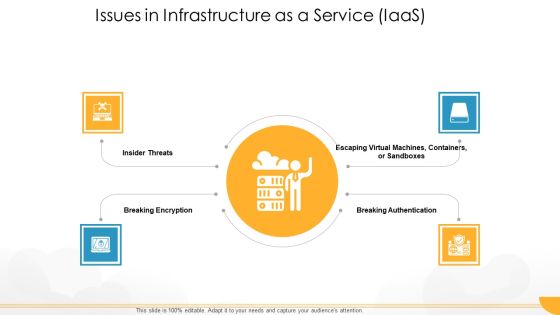
Technology Guide For Serverless Computing Issues In Infrastructure As A Service Iaas Diagrams PDF
This is a technology guide for serverless computing issues in infrastructure as a service iaas diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insider threats, breaking encryption, breaking authentication, virtual machines. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Issues In Infrastructure As A Service Iaas Ideas PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan issues in infrastructure as a service iaas ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insider threats, breaking encryption, escaping virtual machines, containers, or sandboxes, breaking authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
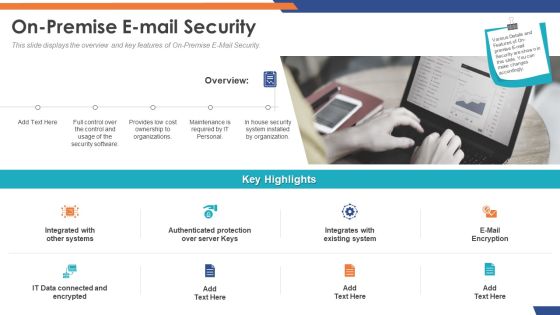
Email Security Market Research Report On Premise E Mail Security Mockup PDF
Presenting this set of slides with name email security market research report on premise e mail security mockup pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market On Premise E Mail Security Topics PDF
Presenting this set of slides with name global cloud based email security market on premise e mail security topics pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Tech Update With Over The Air Gateway Management Ppt PowerPoint Presentation Gallery Themes PDF
Persuade your audience using this tech update with over the air gateway management ppt powerpoint presentation gallery themes pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including firmware control, upgradation encryption, electronic control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF
The following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy,disaster recovery, password encryption, tasks, reviews etc. There are so many reasons you need a Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

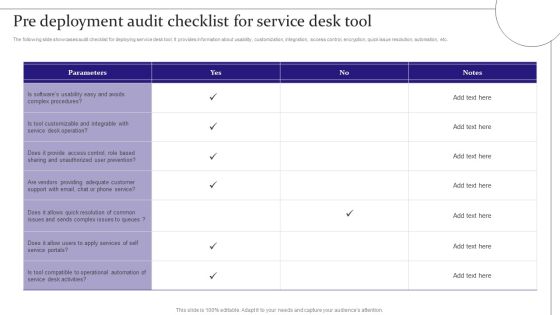
Improve IT Service Desk Pre Deployment Audit Checklist For Service Desk Tool Icons PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc.Deliver and pitch your topic in the best possible manner with this Improve IT Service Desk Pre Deployment Audit Checklist For Service Desk Tool Icons PDF. Use them to share invaluable insights on Customizable Integrable, Operational Automation, Service Desk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Four Safest Texting Platforms And Applications Infographics PDF
This slide illustrates four safest messaging platforms and applications useful for businesses to have private conversations within the organization. It also includes information about safety features like end-to-end encryption, vanishing messages, chat backups, transparency reports, group chat security, etc.Showcasing this set of slides titled four safest texting platforms and applications infographics pdf The topics addressed in these templates are four safest texting platforms and applications All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Technology Facility Maintenance And Provider Client Standards Checklist Contd Clipart PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a technology facility maintenance and provider client standards checklist contd clipart pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secured encryption, protect servers, internal network, high speed internet access . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
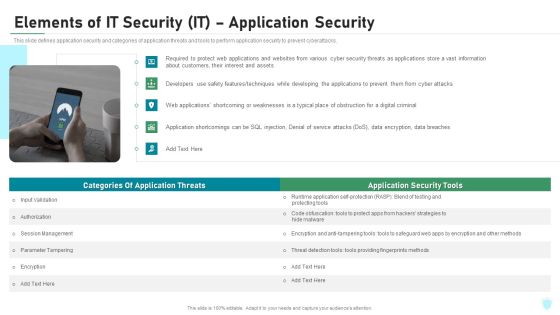
Elements Of IT Security IT Application Security Ppt Layouts Ideas PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a elements of it security it application security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, encryption, authorization, techniques, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Flowchart Depicting Vendor Verification System Assessment Infographics PDF
This slide focuses on the flowchart that depicts the vendor due diligence assessment which covers document submission for security review, vendor shortlisting, compliance, monitoring encryption, ensuring supportive features, evaluating capacity, approval and making final decision, etc. Presenting Flowchart Depicting Vendor Verification System Assessment Infographics PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Required Resources, Conducting Internal Process, Security Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Benefits Of Using A Reverse Proxy Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the benefits of using a reverse proxy server, and it includes load balancing, enhanced security, powerful caching, superior compression, optimized SSL encryption, and monitoring and logging traffic.This is a Benefits Of Using A Reverse Proxy Server Reverse Proxy For Load Balancing Designs PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Load Balancing, Powerful Caching, Superior Compression. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
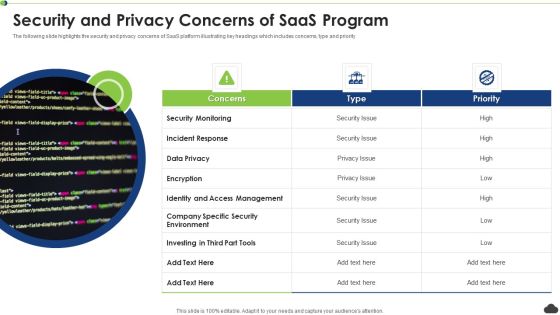
Security And Privacy Concerns Of Saas Program Ppt PowerPoint Presentation File Background PDF
The following slide highlights the security and privacy concerns of SaaS platform illustrating key headings which includes concerns, type and priority. Persuade your audience using this security and privacy concerns of saas program ppt powerpoint presentation file background pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security monitoring, incident response, encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Project Management Software Capital Raising Deck Why Invest With Us Download PDF
Following slide showcases benefits that are offered by company to assure business safety. It include pointers such as consistent backups, development processes, encryption, code review etc. Slidegeeks has constructed Project Management Software Capital Raising Deck Why Invest With Us Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Cloud Computing Application Security Architecture Audit Checklist Structure PDF
The slide shows a checklist containing number of tasks needed to be done while performing application security audit. It includes tasks like developing password policies, making multi factor confirmation mandatory, supervising SaaS license, etc. Showcasing this set of slides titled Cloud Computing Application Security Architecture Audit Checklist Structure PDF. The topics addressed in these templates are Develop Password Policies, Validate Anti Attacking Protections, Set Message Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
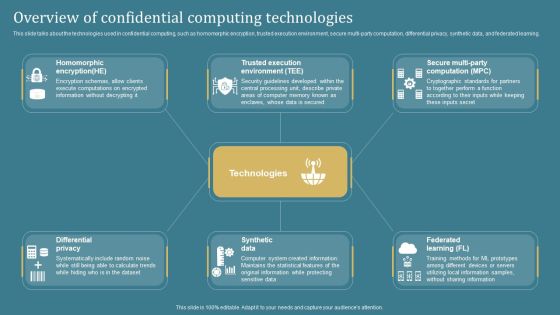
Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Welcome to our selection of the Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. This Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Pre Deployment Audit Checklist For Service Desk Tool Sample PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
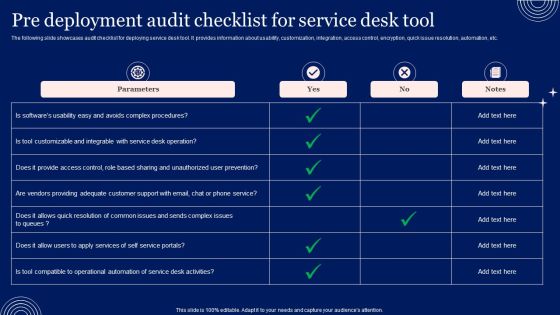
Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc.This Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheImplementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
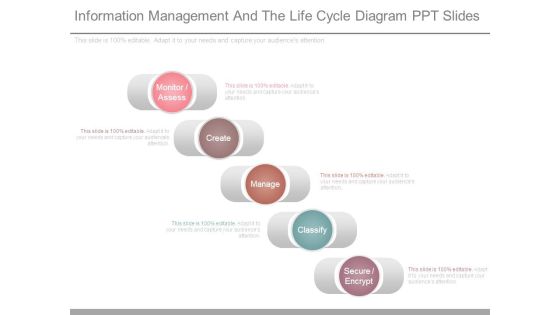
Information Management And The Life Cycle Diagram Ppt Slides
This is a information management and the life cycle diagram ppt slides. This is a five stage process. The stages in this process are monitor assess, create, manage, classify, secure encrypt.

Key Properties Of Blockchain And Distributed Ledger Technology Mockup PDF
Following slide exhibits blockchain technology properties which shows the complete overview of this technology. Programmable, secure, anonymous, time-stamped, verification and transparency are the core properties covered in this slide. Persuade your audience using this Key Properties Of Blockchain And Distributed Ledger Technology Mockup PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Technology, Individually Encrypted, Kept Anonymous. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home