Cybersecurity

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
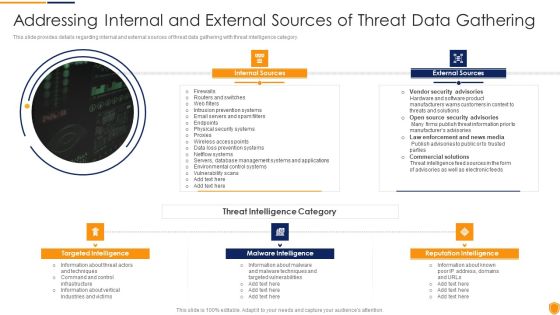
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Internal And External Clipart PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a mitigating cybersecurity threats and vulnerabilities addressing internal and external clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal sources, external sources, targeted intelligence, malware intelligence, reputation intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
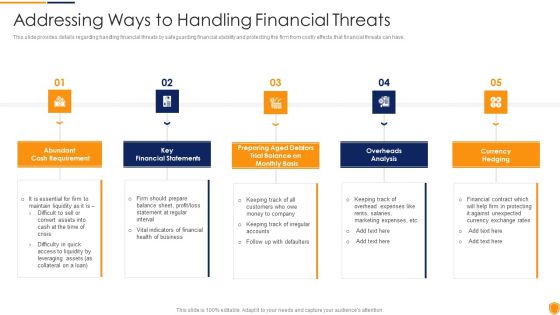
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Ways To Handling Professional PDF
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Presenting mitigating cybersecurity threats and vulnerabilities addressing ways to handling professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cash requirement, key financial statements, overheads analysis, currency hedging. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Different Kinds Of Insider Information PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a mitigating cybersecurity threats and vulnerabilities different kinds of insider information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like different kinds of insider digital threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis For Effective Threat Graphics PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. This is a mitigating cybersecurity threats and vulnerabilities impact analysis for effective threat graphics pdf template with various stages. Focus and dispense information one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis for effective threat management in securing workplace. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis Of Successful Threat Slides PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Presenting mitigating cybersecurity threats and vulnerabilities impact analysis of successful threat slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like focus area, past state, present state, benefit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Threat Management Action Plan Mockup PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities threat management action plan mockup pdf. Use them to share invaluable insights on threat identification, threat treatment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Various Types Of Workplace Download PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a mitigating cybersecurity threats and vulnerabilities various types of workplace download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threatening behavior, stalking, assault harassment, property damage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Methods To Develop Cybersecurity Monitoring Best Practices To Be Followed By The Company Demonstration PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Presenting methods to develop cybersecurity monitoring best practices to be followed by the company demonstration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like practice description, gather monitoring data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role Of Technical Competence In Organizational It Professional Upskilling For Cybersecurity Guidelines PDF
The following slide provides information about the key roles of the ML Architect along with the role description. Major roles included in the slide are Data Scientist Citizen Data Scientist, ML architect, AI Architect, and AI Engineer This is a Role Of Technical Competence In Organizational It Professional Upskilling For Cybersecurity Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Scientist Or Citizen, Data Scientist Extracting Knowledge, Functions To Operationalize You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Presenting Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Incident Management, Asset Management, Risk Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.This is a Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disaster, Environmental Control Failures, Deliberate Software Attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF Use them to share invaluable insights on Resources Required, Responsible Person, Expected Resolution Time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Role And Responsibilities Of QA In Devops Diagrams PDF
This slide provides information regarding role and responsibilities of QA in DevOps for quality management. This is a Cybersecurity Risk Administration Plan Role And Responsibilities Of QA In Devops Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development And Implementation, Asset Classification And Control, Development Of Organizational You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
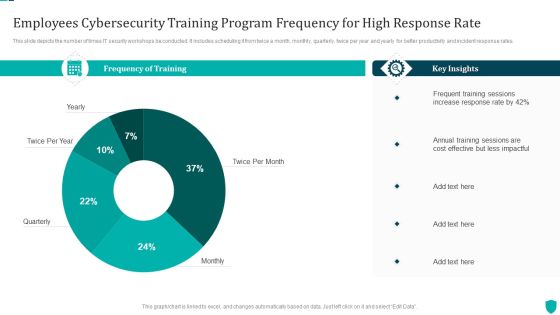
Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF
This slide depicts the number of times IT security workshops be conducted. It includes scheduling it from twice a month, monthly, quarterly, twice per year and yearly for better productivity and incident response rates.Showcasing this set of slides titled Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF. The topics addressed in these templates are Frequency Of Training, Key Insights, Frequent Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
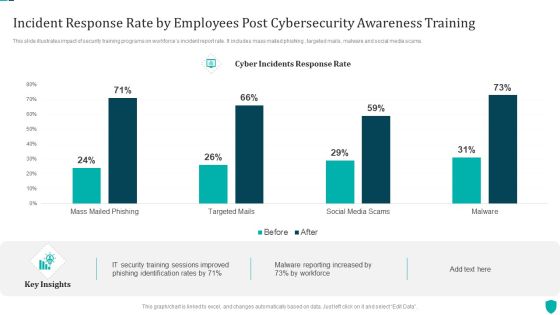
Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF
This slide illustrates impact of security training programs on workforces incident report rate. It includes mass mailed phishing , targeted mails, malware and social media scams.Pitch your topic with ease and precision using this Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF. This layout presents information on Training Sessions, Phishing Identification, Malware Reporting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Want to ace your presentation in front of a live audience Our Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Roles And Responsibilities Of Risk Management Team Cybersecurity Risk Assessment Infographics PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roles And Responsibilities Of Risk Management Team Cybersecurity Risk Assessment Infographics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF
Retrieve professionally designed Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Assigning Criticality Rating To Information Assets Cybersecurity Risk Assessment Template PDF
This slide showcases criticality rating that can be allocation to assets for identifying critical assets. Its key elements are asst, failure cost, failure impact and criticality rating. Take your projects to the next level with our ultimate collection of Assigning Criticality Rating To Information Assets Cybersecurity Risk Assessment Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Improving Cybersecurity With Incident Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides
Grab this Improving Cybersecurity With Incident Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides to craft a unique and engaging business proposal for your clients. This PowerPoint complete Deck of fivtyslides covers essentials points all essential points that makes it an excellent choice for exhibiting an idea to the stakeholders. You can use this presentation template, even, to give a product demo to highlight its credibility and usage. The presentation template is also equipped to do this with its 100 precent editable and customizable capability. Download now.

Asset Criticality Of Identified System Improving Cybersecurity With Incident Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Asset Criticality Of Identified System Improving Cybersecurity With Incident Themes PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Asset Maintenance Cost Assessment Sheet Improving Cybersecurity With Incident Download PDF
Following slide displays assessment sheet that can be used by members to record overall asset maintenance cost for further analysis. Sections covered in the sheet are onsite solution, initial, monthly and annual cost.Want to ace your presentation in front of a live audience Our Asset Maintenance Cost Assessment Sheet Improving Cybersecurity With Incident Download PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Make sure to capture your audiences attention in your business displays with our gratis customizable Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
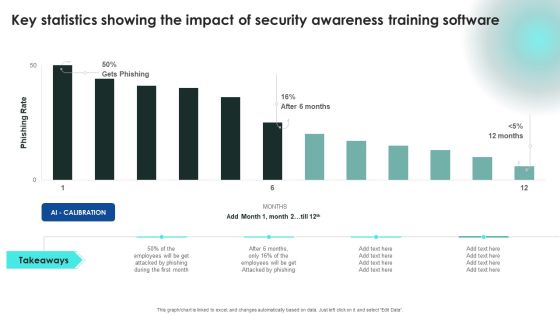
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF
This modern and well arranged Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Implementing Cybersecurity Awareness Program To Prevent Attacks Social Engineering Attack Prevention Techniques Topics PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. There are so many reasons you need a Implementing Cybersecurity Awareness Program To Prevent Attacks Social Engineering Attack Prevention Techniques Topics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF
Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Various Techniques Designs PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Find a pre-designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Various Techniques Designs PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cybersecurity Guidelines IT Acceptable Use Of Equipment Policy Overview Slides PDF
This slide outlines the acceptable use policy, and it includes how official computers should be used, risks associated with improper usage, and appropriate behavior while handling sensitive information. Find a pre-designed and impeccable Cybersecurity Guidelines IT Acceptable Use Of Equipment Policy Overview Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF
This slide represents the access authorization, modification, and identity access management based on polp, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Guidelines IT Byod Procedure Device Protocols For Workers Guidelines PDF
This slide represents the device protocols that are the first step in the BYOD procedure. It also includes the software information that should be installed on the employees personal devices. Want to ace your presentation in front of a live audience Our Cybersecurity Guidelines IT Byod Procedure Device Protocols For Workers Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Cybersecurity Guidelines IT Byod Restrictions On Authorized Use Personal Devices Professional PDF
This slide covers the restrictions on the authorized use of personal devices in corporate buildings or property. It also includes that employees should inform their friends and family about the policy to avoid personal concerns at work. There are so many reasons you need a Cybersecurity Guidelines IT Byod Restrictions On Authorized Use Personal Devices Professional PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cybersecurity Guidelines IT Checklist For Writing An Effective IT Policy Rules PDF
This slide describes the checklist for an effective information technology policy, and it includes all the best practices that should be considered while writing an IT policy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cybersecurity Guidelines IT Checklist For Writing An Effective IT Policy Rules PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cybersecurity Guidelines IT Importance Of IT Policies And Procedures Rules PDF
This slide talks about the importance of information technology policies and procedures. It also includes how organizations could experience outages due to the lack of inadequate IT management. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Guidelines IT Importance Of IT Policies And Procedures Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Guidelines IT Internet Usage Policy Objective And General Guidelines Elements PDF
This slide describes the objective and general guidelines of internet usage policy, and it also includes the internet login guidelines for employees. Welcome to our selection of the Cybersecurity Guidelines IT Internet Usage Policy Objective And General Guidelines Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Guidelines IT Overview Of Information Retention Policy For Employees Microsoft PDF
This slide talks about the data retention policy, including the involved data types such as documents, customer records, transactional information, email communication, and contracts. Find a pre-designed and impeccable Cybersecurity Guidelines IT Overview Of Information Retention Policy For Employees Microsoft PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF
This slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Want to ace your presentation in front of a live audience Our Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Cybersecurity Guidelines IT Termination Of Employment And Violation Of Byod Policy Themes PDF
This slide talks about the termination of employment and violation of BYOD policy. Both include the actions to be performed if any employee leaves or violates the BYOD policy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cybersecurity Guidelines IT Termination Of Employment And Violation Of Byod Policy Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cybersecurity Guidelines IT Timeline To Develop An Information Technology Policy Introduction PDF
This slide represents the timeline to develop an information technology policy and it includes all the steps to be performed while developing an IT policy. Present like a pro with Cybersecurity Guidelines IT Timeline To Develop An Information Technology Policy Introduction PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Guidelines IT Column Chart Ppt PowerPoint Presentation Icon Show PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cybersecurity Guidelines IT Column Chart Ppt PowerPoint Presentation Icon Show PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Cybersecurity Guidelines IT Our Target Ppt PowerPoint Presentation Gallery Visual Aids PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Our Target Ppt PowerPoint Presentation Gallery Visual Aids PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Guidelines IT SWOT Analysis Ppt PowerPoint Presentation File Background Images PDF
This modern and well-arranged Cybersecurity Guidelines IT SWOT Analysis Ppt PowerPoint Presentation File Background Images PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF
Welcome to our selection of the Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
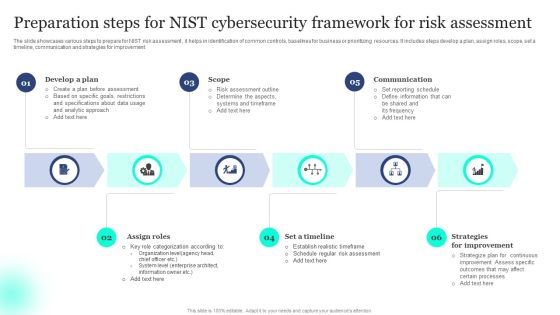
Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF
The slide showcases various steps to prepare for NIST risk assessment , it helps in identification of common controls, baselines for business or prioritizing resources. It includes steps develop a plan, assign roles, scope, set a timeline, communication and strategies for improvement. Presenting Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Scope, Communication, Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides
Arouses curiosity in the audience is the USP of this Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides. The image shown compliments the text provided. The holistic image conveys the message that we are on to something important, the deep world of business communication training. Download it now, and as always customize and edit each of the sixty five slides as per convenience and the data and the experience you are comfortable sharing with your audience.

Cybersecurity Operations Cybersecops Best Tools For Security Operations Secops Graphics PDF
This slide represents the best security operations tools for the year 2023. The purpose of this slide is to showcase the various prominent tools for SecOps, including Grafana, StackStorm, GRR Rapid Response, Chef Inspec, Find a pre designed and impeccable Cybersecurity Operations Cybersecops Best Tools For Security Operations Secops Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF
This slide represents the main steps to developing a security operations center. The purpose of this slide is to highlight the main building steps involved in a SecOps creation. These steps include selecting a service model, location, technology, people and processes. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Boost your pitch with our creative Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. Increase malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Slidegeeks has constructed Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Slidegeeks has constructed Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
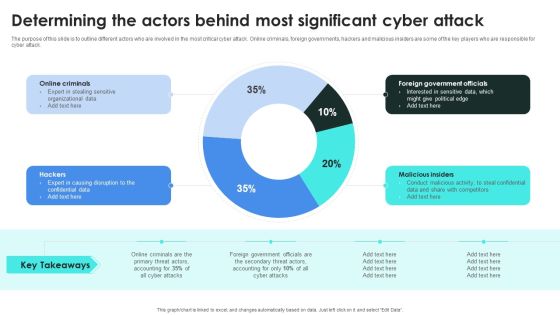
Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
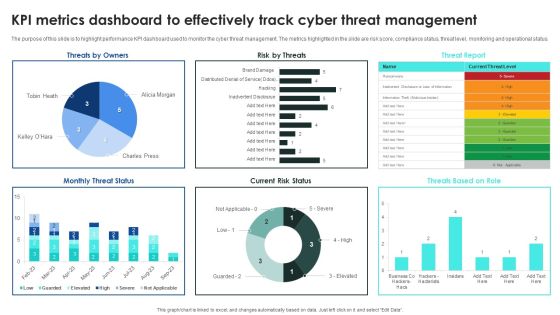
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Welcome to our selection of the Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Slidegeeks is here to make your presentations a breeze with Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc.Welcome to our selection of the Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF
This slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Audit Commission Strengthening Cybersecurity Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured audit commission strengthening cybersecurity ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twenty seven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Take advantage of this well-researched and professionally-designed Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the seventy two slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.
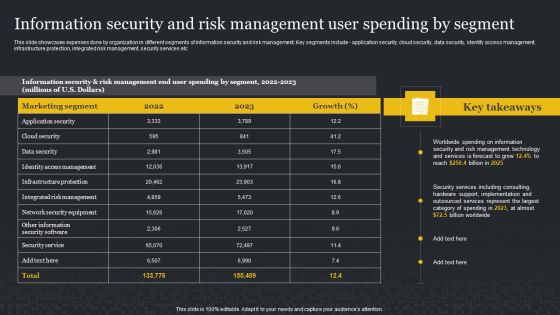
Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
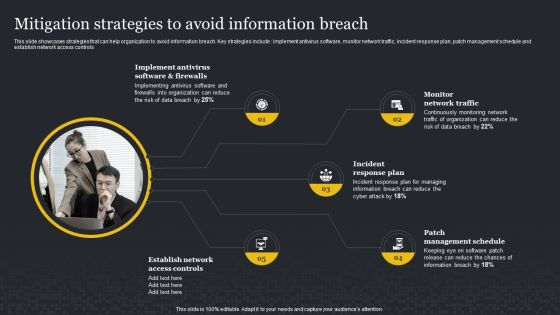
Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
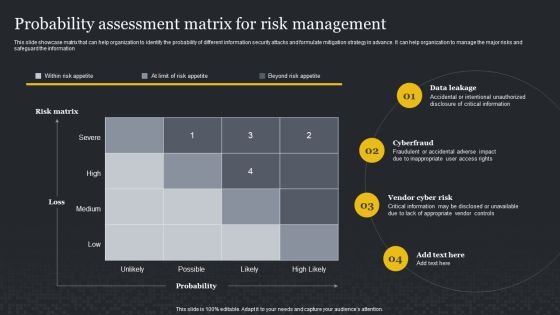
Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Slidegeeks is here to make your presentations a breeze with Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
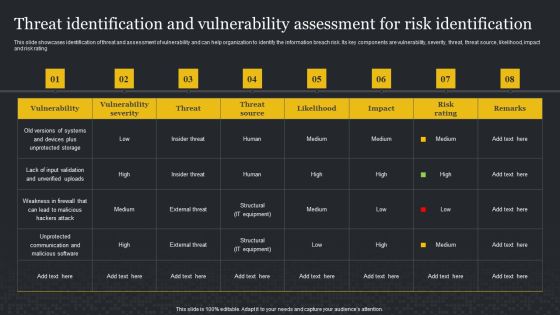
Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. This modern and well-arranged Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
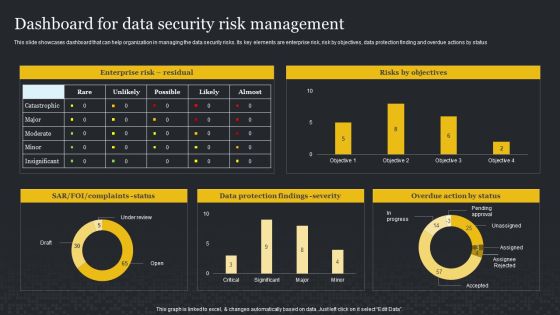
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
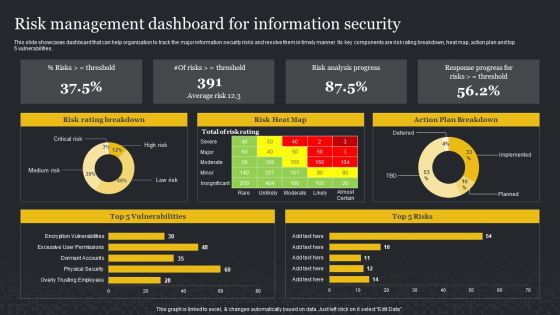
Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Implementing Cybersecurity Awareness Program To Prevent Attacks Ppt PowerPoint Presentation Complete Deck With Slides
This Implementing Cybersecurity Awareness Program To Prevent Attacks Ppt PowerPoint Presentation Complete Deck With Slides is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This seventy five slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF
The purpose of this slide is to showcase the Does and do nots of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF
This slide depicts the critical components of information technology policy, and it includes integrity, confidentiality, and availability, including how these components work. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF
This slide represents the vendor management policy, and it also includes points to be considered when choosing a vendor. This policy is about the vendor with whom organizations share their critical information. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF
This slide represents the company stipend for BYOD policy, including the stats for 2022, such as percent the age of employees using their personal devices, BYOD generated value of each worker per year, and so on. Present like a pro with Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF
This slide represents the overview and primary functions of SOC-as-a-Service. The purpose of this slide is to demonstrate the various critical functions and key features, and it also covers the reasons for organizations to adopt the subscription-based model. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF
This slide represents the overview, benefits and disadvantages of virtual security operation center model. The purpose of this slide is to highlight the advantage, disadvantages and alternative approaches for VSOC such as outsourcing of virtual SOC model. This modern and well arranged Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF
This slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Welcome to our selection of the Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cybersecurity Operations Cybersecops RACI Matrix For SOC As A Service Security Model Microsoft PDF
This slide outlines the RACI matrix for the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops RACI Matrix For SOC As A Service Security Model Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF
This slide depicts the career opportunities in cybersecurity, including various job roles such as chief information security officer, chief security office, security engineers, architects, analysts and penetration testers. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Incident Response Techniques Deployement Five Phases Of Cybersecurity Incident Management Formats PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Want to ace your presentation in front of a live audience Our Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Incident Response Techniques Deployement Impact Of Cybersecurity Incidents On Organization Clipart PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Approaches To Implement Advanced Cybersecurity Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fortyfour slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of seventy slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Cybersecurity Risk Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fifty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF
This slide represents the cybersecurity risks associated with russia and ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Strategies To Mitigate Cyber Security Risks Analyzing IT Department On NIST Cybersecurity Framework Ppt Slides Background Designs PDF
Presenting this set of slides with name strategies to mitigate cyber security risks analyzing it department on nist cybersecurity framework ppt slides background designs pdf. The topics discussed in these are performance, nist core functions, identify, protect, detect, recover, respond. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF
This slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

COVID 19 Mitigating Impact On High Tech Industry Cybersecurity Checklist During Remote Working For Employees Demonstration PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry cybersecurity checklist during remote working for employees demonstration pdf. This is a eleven stage process. The stages in this process are ensuring secure, removable storage, continuously record nearby conversations, social media approval. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home