Cybersecurity
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
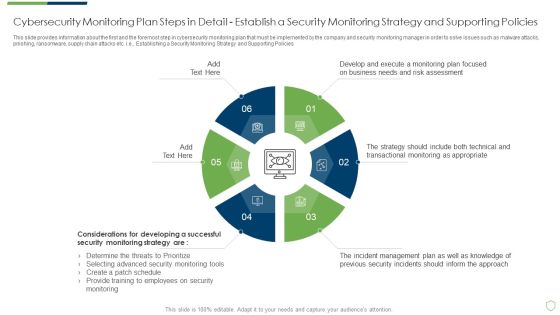
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

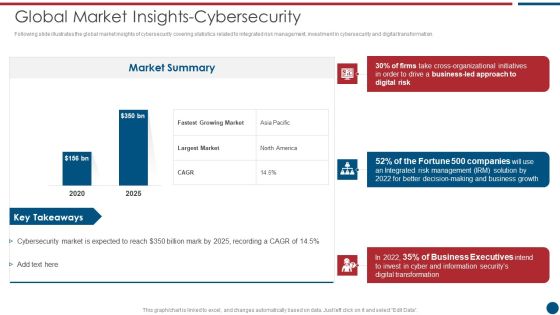
Handling Cyber Threats Digital Era Global Market Insights Cybersecurity Ppt Show Background Image PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative handling cyber threats digital era global market insights cybersecurity ppt show background image pdf bundle. Topics like global market insights cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Costs Incurred To Process Faulty Cybersecurity Transactions Ppt Gallery Influencers PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an awe inspiring pitch with this creative costs incurred to process faulty cybersecurity transactions ppt gallery influencers pdf bundle. Topics like costs incurred to process faulty cybersecurity transactions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

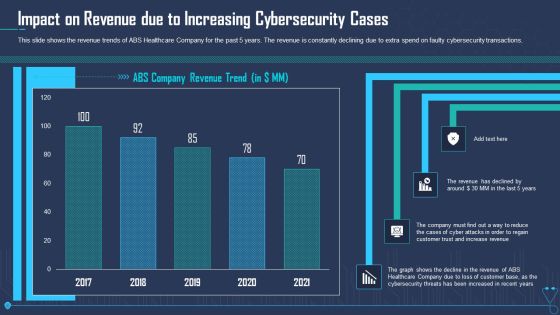
Impact On Revenue Due To Increasing Cybersecurity Cases Ppt Outline Styles PDF
This slide shows the revenue trends of ABS Healthcare Company for the past 5 years. The revenue is constantly declining due to extra spend on faulty cybersecurity transactions. Deliver an awe inspiring pitch with this creative impact on revenue due to increasing cybersecurity cases ppt outline styles pdf bundle. Topics like impact on revenue due to increasing cybersecurity cases can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Costs Incurred To Process Faulty Cybersecurity Transactions Ppt Infographics Smartart PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an awe inspiring pitch with this creative costs incurred to process faulty cybersecurity transactions ppt infographics smartart pdf bundle. Topics like costs incurred to process faulty cybersecurity transactions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Impact On Revenue Due To Increasing Cybersecurity Cases Ppt Inspiration Infographics PDF
This slide shows the revenue trends of ABS Healthcare Company for the past 5 years. The revenue is constantly declining due to extra spend on faulty cybersecurity transactions. Deliver an awe inspiring pitch with this creative impact on revenue due to increasing cybersecurity cases ppt inspiration infographics pdf bundle. Topics like impact on revenue due to increasing cybersecurity cases can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF bundle. Topics like Market Summary, Largest Market, Business Led can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
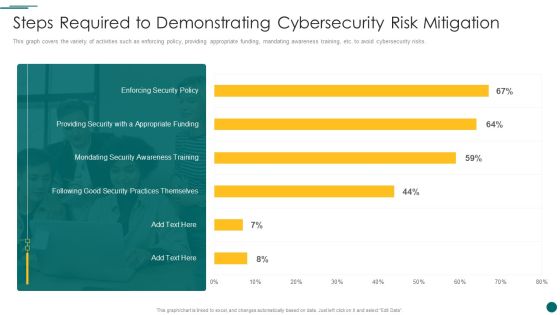
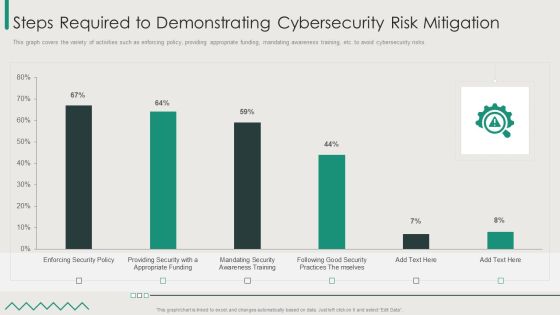
Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF bundle. Topics like Steps Required Demonstrating, Cybersecurity Risk Mitigation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
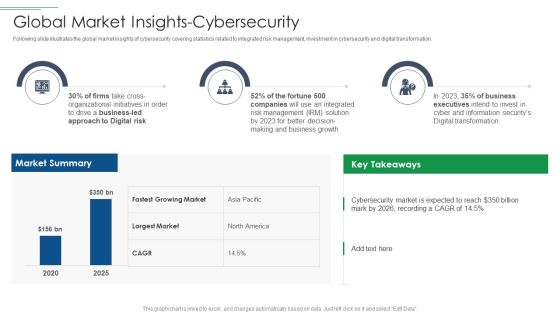
IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF bundle. Topics like Business Growth, Risk Management, Organizational Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity And Hacking Incidents In ABS Healthcare Company Ppt Styles Inspiration PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver and pitch your topic in the best possible manner with this cybersecurity and hacking incidents in ABS healthcare company ppt styles inspiration pdf. Use them to share invaluable insights on protection, data encryption, cybersecurity, 2017 to 2021 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity And Hacking Incidents In ABS Healthcare Company Ppt Information PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver an awe inspiring pitch with this creative cybersecurity and hacking incidents in abs healthcare company ppt information pdf bundle. Topics like cybersecurity and hacking incidents in abs healthcare company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity And Hacking Incidents In ABS Healthcare Company Ppt Infographic Template Graphics Example PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver an awe inspiring pitch with this creative cybersecurity and hacking incidents in abs healthcare company ppt infographic template graphics example pdf bundle. Topics like cybersecurity and hacking incidents in abs healthcare company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity And Hacking Incidents In Abs Healthcare Company Ppt Icon Ideas PDF
This slide shows the graph of total number of Cybersecurity and Hacking Incidents in ABS Healthcare Company from the year 2017 to 2021. Additionally, it provides key insights growth rate, key recommendation, reasons etc. related to growing cybersecurity and hacking incidents. Deliver an awe-inspiring pitch with this creative cybersecurity and hacking incidents in abs healthcare company ppt icon ideas pdf. bundle. Topics like cybersecurity and hacking incidents in abs healthcare company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Distributed Ledger Technology Icon With Cybersecurity Symbol Ppt PowerPoint Presentation Gallery Deck PDF
Presenting distributed ledger technology icon with cybersecurity symbol ppt powerpoint presentation gallery deck pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including distributed ledger technology icon with cybersecurity symbol. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Approaches To Implement Advanced Cybersecurity Monitoring Plan Table Of Contents Information PDF
Deliver an awe inspiring pitch with this creative approaches to implement advanced cybersecurity monitoring plan table of contents information pdf bundle. Topics like essential elements, estimated security monitoring, advanced cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Company Annual Summary Of Cybersecurity Industry One Pager PDF Document PPT Template
Here we present the Company Annual Summary Of Cybersecurity Industry One Pager PDF Document PPT Template. This One-pager template includes everything you require. You can edit this document and make changes according to your needs it offers complete freedom of customization. Grab this Company Annual Summary Of Cybersecurity Industry One Pager PDF Document PPT Template Download now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

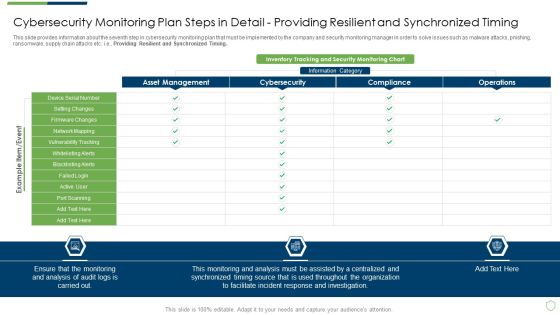
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Russian Cyber Attacks On Ukraine IT Cybersecurity Risks Of An Escalating Icons PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. This is a russian cyber attacks on ukraine it cybersecurity risks of an escalating icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like capabilities, economic, measures, severe, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Intelligence Framework For Application Consumption Major Cybersecurity Challenges With Required Actions Mockup PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption major cybersecurity challenges with required actions mockup pdf. Use them to share invaluable insights on cybersecurity strategy, performing effective oversight, protecting cyber critical infrastructure, telecommunications, management challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Major Cybersecurity Challenges With Required Actions Ppt Pictures Background Designs PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges This is a major cybersecurity challenges with required actions ppt pictures background designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, cybersecurity strategy, performing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

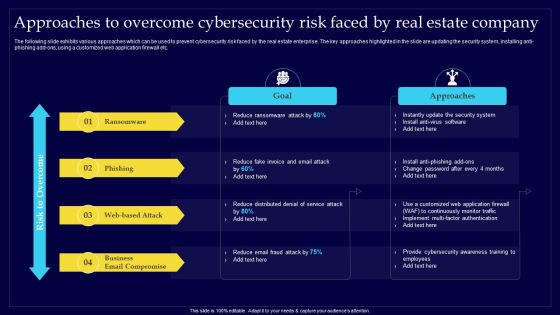
Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Latest Trends Existing In Cybersecurity Industry Template 261 One Pager Documents
This one pager covers details regarding the latest industry trends that are existing in the Cybersecurity industry and will prevail in upcoming future. Presenting you a fantastic Latest Trends Existing In Cybersecurity Industry Template 261 One Pager Documents. This piece is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this Latest Trends Existing In Cybersecurity Industry Template 261 One Pager Documents A4 One-pager now.

One Page Annual Summary Of Firm In Cybersecurity Industry Template 262 One Pager Documents
This one pager shows the detailed summary of a firm in cybersecurity industry such as company name and overview, segment information, revenue split, key financials, key performance indicators, business strategy, major competitors etc. Presenting you an exemplary One Page Annual Summary Of Firm In Cybersecurity Industry Template 262 One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Annual Summary Of Firm In Cybersecurity Industry Template 262 One Pager Documents brilliant piece now.

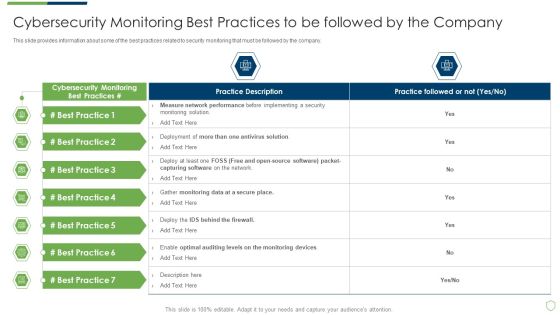
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Best Mockup PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring best mockup pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
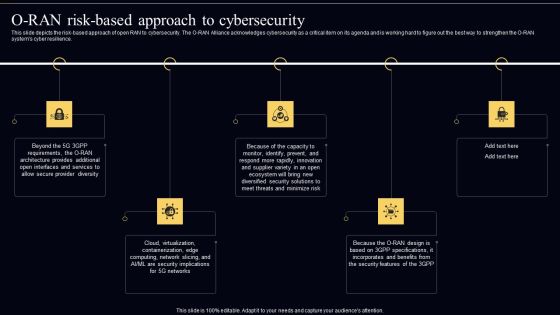
Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF
This slide depicts the risk based approach of open RAN to cybersecurity. The O RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O RAN systems cyber resilience. Get a simple yet stunning designed Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Open Radio Access Network IT O RAN Risk Based Approach To Cybersecurity Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF
This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF today and make your presentation stand out from the rest.

Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Communication Plan For Cybersecurity Events And Incidents Hacking Prevention Awareness Training For IT Security Background PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents hacking prevention awareness training for it security background pdf. Use them to share invaluable insights on development, security, management, cybersecurity, communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Communication Plan For Cybersecurity Events And Incidents Pictures PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition communication plan for cybersecurity events and incidents pictures pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Communication Plan For Cybersecurity Events And Incidents Ppt Icon Good PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents ppt icon good pdf. Use them to share invaluable insights on resources training, awareness training, cybersecurity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Communication Plan For Cybersecurity Events And Incidents Ppt Inspiration Graphic Images PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents ppt inspiration graphic images pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Difference Cybersecurity Information Security Ppt PowerPoint Presentation Summary Slide Download Cpb
Presenting this set of slides with name difference cybersecurity information security ppt powerpoint presentation summary slide download cpb. This is an editable Powerpoint five stages graphic that deals with topics like difference cybersecurity information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cybersecurity Incident Response Workflow System Ppt PowerPoint Presentation Gallery Examples Cpb
Presenting this set of slides with name cybersecurity incident response workflow system ppt powerpoint presentation gallery examples cpb. This is an editable Powerpoint four stages graphic that deals with topics like cybersecurity incident response workflow system to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Shield Icon On Computer Monitor For Cybersecurity Ppt PowerPoint Presentation Gallery Show PDF
Persuade your audience using this shield icon on computer monitor for cybersecurity ppt powerpoint presentation gallery show pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including shield icon on computer monitor for cybersecurity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Costs Incurred To Process Faulty Cybersecurity Transactions Ppt Portfolio Graphic Tips PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an awe inspiring pitch with this creative costs incurred to process faulty cybersecurity transactions ppt portfolio graphic tips pdf bundle. Topics like costs incurred, process faulty, 2017 to 2021 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Costs Incurred To Process Faulty Cybersecurity Transactions Ppt File Format PDF
This slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver and pitch your topic in the best possible manner with this costs incurred to process faulty cybersecurity transactions ppt file format pdf. Use them to share invaluable insights on cost, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Agenda For Effective Cybersecurity Training To Raise Awareness Ppt Summary Templates PDF
This is a agenda for effective cybersecurity training to raise awareness ppt summary templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for effective cybersecurity training to raise awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5 Phase Procedure Infographics For Cybersecurity In Financial Services Ppt PowerPoint Presentation File Smartart PDF
Persuade your audience using this 5 phase procedure infographics for cybersecurity in financial services ppt powerpoint presentation file smartart pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 phase procedure infographics for cybersecurity in financial services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comprehensive Business Digitization Deck Steps Required To Demonstrating Cybersecurity Risk Mitigation Microsoft PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative comprehensive business digitization deck steps required to demonstrating cybersecurity risk mitigation microsoft pdf bundle. Topics like enforcing policy, providing appropriate funding, mandating awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Budget For Effective Threat Ideas PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities budget for effective threat ideas pdf bundle. Topics like incident management, risk management, client onboarding process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Agenda For Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
This is a agenda for modern security observation plan to eradicate cybersecurity risk and data breach information pdf template with various stages. Focus and dispense information on senen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for modern security observation plan to eradicate cybersecurity risk and data breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver and pitch your topic in the best possible manner with this Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF Use them to share invaluable insights on Practices Themselves, Awareness Training, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
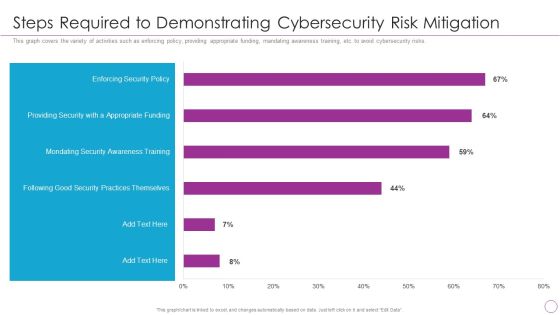
Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver an awe inspiring pitch with this creative Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF bundle. Topics like Practices Themselves, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
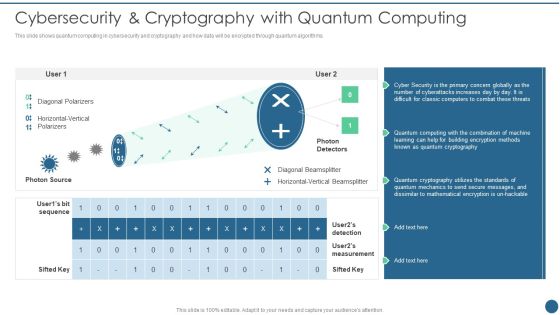
Quantum Key Distribution Cybersecurity And Cryptography With Quantum Computing Designs PDF
This slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms. Deliver and pitch your topic in the best possible manner with this Quantum Key Distribution Cybersecurity And Cryptography With Quantum Computing Designs PDF Use them to share invaluable insights on Diagonal Polarizers, Diagonal Beamsplitter, Horizontal Vertical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF. Use them to share invaluable insights on Enforcing Security Policy, Good Security Practices, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF
This graph covers the variety of activities such as enforcing Policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF bundle. Topics like Enforcing Security Policy, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

One Page Annual Summary Of Firm In Cybersecurity Industry One Pager Documents
Presenting you an exemplary One Page Annual Summary Of Firm In Cybersecurity Industry One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Annual Summary Of Firm In Cybersecurity Industry One Pager Documents brilliant piece now.

Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents
Looking for a predesigned Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents. Here is the perfect piece for you It has everything that a well-structured Annual Report PowerPoint Deck should have. Besides, it is 100 percent editable, which offers you the cushion to make adjustments according to your preferences. Grab this Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents A4 One-pager now.

Table Of Contents For Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents
Presenting you an exemplary Table Of Contents For Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents For Cybersecurity Annual Report Of The Company 2021 2022 One Pager Documents brilliant piece now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Policies Inspiration PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Presenting continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring policies inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

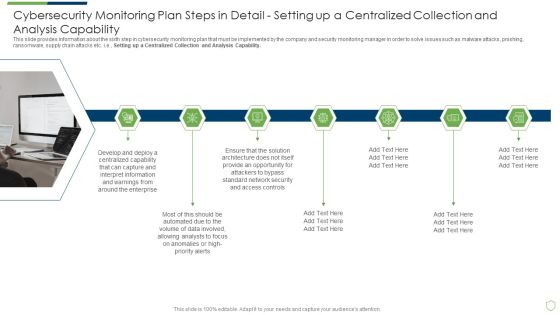
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF
The following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber-attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Get a simple yet stunning designed Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF
Explore a selection of the finest Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Create an editable Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Executing Risk Mitigation Approaches To Overcome Cybersecurity Risk Faced By Real Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

IT Policies And Procedures Cybersecurity Awareness Training For Staff Structure PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IT Policies And Procedures Cybersecurity Awareness Training For Staff Structure PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IT Policies And Procedures Cybersecurity Awareness Training For Staff Structure PDF today and make your presentation stand out from the rest.
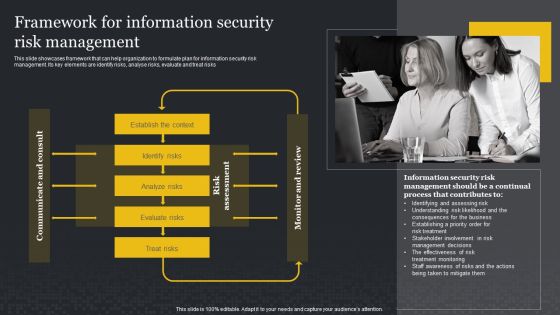
Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Presenting this PowerPoint presentation, titled Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add-ons, using a customized web application firewall etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Approaches To Overcome Cybersecurity Risk Faced By Real Estate Enhancing Process Improvement By Regularly Elements PDF today and make your presentation stand out from the rest.

Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Brochure PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Implementing Cybersecurity Awareness Program To Prevent Attacks Outlook Of Social Engineering Attack Sample PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Presenting this PowerPoint presentation, titled Implementing Cybersecurity Awareness Program To Prevent Attacks Outlook Of Social Engineering Attack Sample PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Implementing Cybersecurity Awareness Program To Prevent Attacks Outlook Of Social Engineering Attack Sample PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Implementing Cybersecurity Awareness Program To Prevent Attacks Outlook Of Social Engineering Attack Sample PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Themes PDF

Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Portrait PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Are you searching for a Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Portrait PDF from Slidegeeks today.

Information Technology Policy And Processes Cybersecurity Awareness Training For Staff Themes PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Technology Policy And Processes Cybersecurity Awareness Training For Staff Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Information Technology Policy And Processes Cybersecurity Awareness Training For Staff Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Clipart PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Get a simple yet stunning designed Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Clipart PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Clipart PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

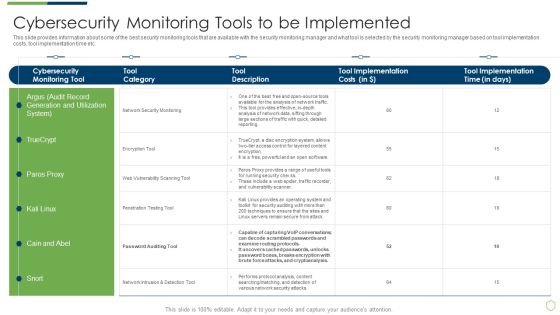
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Wiper Spyware Attack Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Background PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions.This is a data wiper spyware attack cybersecurity risks of an escalating russia ukraine conflict background pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extensive cyber capabilities, russian invasion would, measures as economic warfare You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps like identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Persuade your audience using this Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Recover, Respond, Detect, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
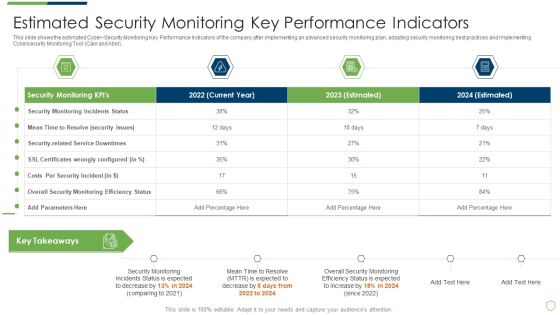
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
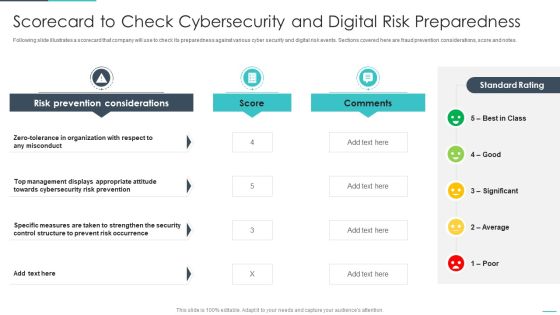
Handling Cyber Threats Digital Era Scorecard To Check Cybersecurity Ppt Model Information PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative dling cyber threats digital era scorecard to check cybersecurity ppt model information pdf bundle. Topics like scorecard to check cybersecurity and digital risk preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
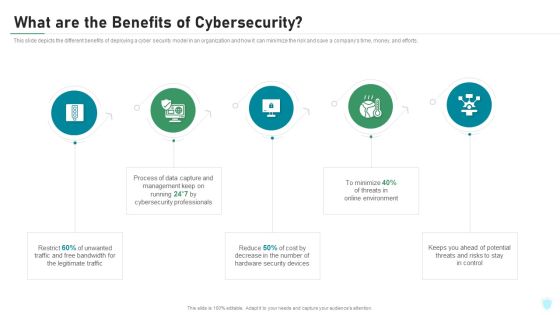
What Are The Benefits Of Cybersecurity IT Security IT Ppt Summary Professional PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a what are the benefits of cybersecurity it security it ppt summary professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like legitimate traffic, cybersecurity, management, process, potential. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity What Are The Benefits Of Electronic Information Security Ppt Infographics Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting cybersecurity what are the benefits of electronic information security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, process, cybersecurity, environment, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

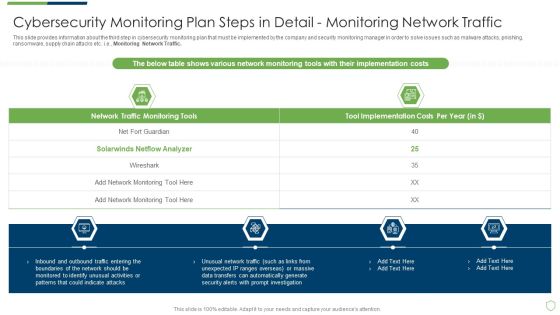
Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF
This slide represents the identified cyber security risks to help the organizations in identifying and prioritizing areas to improve cybersecurity program. It includes details related to cyber security threats, risks, risk priority, mitigation plan, risk owner and risk deduction timeline. Showcasing this set of slides titled Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF. The topics addressed in these templates are Threat, Risk, Risk Priority, Risk Mitigation Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
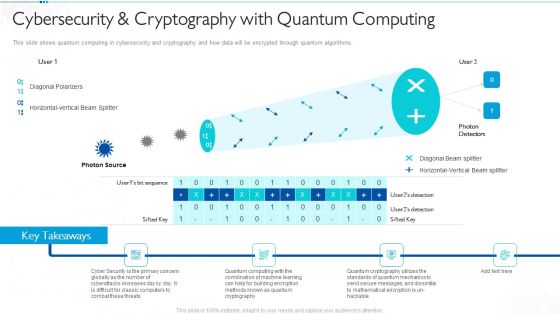
Quantum Computing For Everyone IT Cybersecurity And Cryptography With Quantum Computing Ideas PDF
This slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms. Presenting quantum computing for everyone it cybersecurity and cryptography with quantum computing ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cryptography, quantum computing, cyberattacks, globally. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Threat Status In Project Management Dashboard With Reported Incidents Introduction PDF
This slide represents open and closed cybersecurity risk incidents in areas such as 2 factor authentication, daily backup data etc. Showcasing this set of slides titled cybersecurity threat status in project management dashboard with reported incidents introduction pdf. The topics addressed in these templates are application control, application patch, operating system patch, restricted admin privileges, untrusted application alert. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System Slides PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine-Tune Monitoring System. Presenting cybersecurity monitoring plan steps in detail fine tune monitoring system slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like inappropriate collection, monitoring information, investigative resources needed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Guidelines PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring user activity guidelines pdf bundle. Topics like action information, user information, monitoring capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing Background PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail providing resilient and synchronized timing background pdf. Use them to share invaluable insights on monitoring and analysis, incident response, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
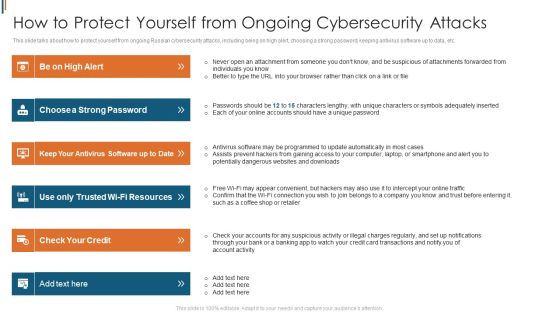
Ukraine Cyberwarfare How To Protect Yourself From Ongoing Cybersecurity Attacks Themes Pdf
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. This is a ukraine cyberwarfare how to protect yourself from ongoing cybersecurity attacks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like choose a strong password, keep your antivirus software up to date, use only trusted wi fi resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack How To Protect Yourself From Ongoing Cybersecurity Attacks Download PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc.Presenting data wiper spyware attack how to protect yourself from ongoing cybersecurity attacks download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like choose a strong password, keep your antivirus, software up to date In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
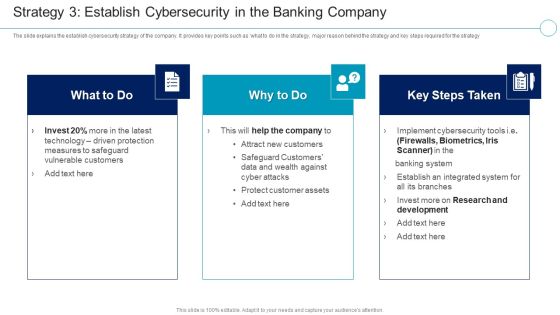
Financial Services Enterprise Transformation Strategy 3 Cybersecurity In The Banking Company Mockup PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy This is a Financial Services Enterprise Transformation Strategy 3 Cybersecurity In The Banking Company Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Research And Development, Measures To Safeguard, Technology Driven Protection You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF
This slide represents risk assessment software dashboard for cybersecurity. It includes risk percentage, number of risks, risk analysis progress, risk response progress, risk rating etc. Showcasing this set of slides titled Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF. The topics addressed in these templates are Risk Rating Breakdown, Action Plan Breakdown, Top 5 Entities Prone To Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Digital Technology Adoption In Banking Industry Case Competition Strategy 3 Establish Cybersecurity Guidelines PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy Presenting Digital Technology Adoption In Banking Industry Case Competition Strategy 3 Establish Cybersecurity Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Technology Driven Protection Measures, Safeguard Vulnerable Customers, Establish An Integrated System In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Management Architect, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
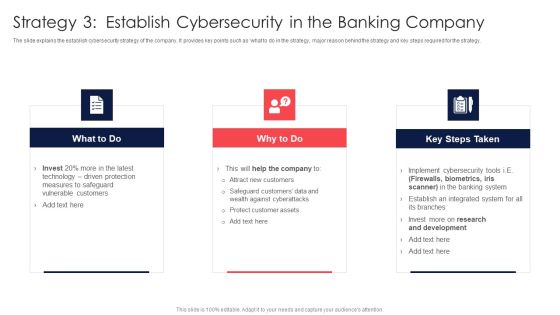
Digital Transformation Of Consumer Strategy 3 Establish Cybersecurity In The Banking Company Ideas PDF
The slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy. Presenting Digital Transformation Of Consumer Strategy 3 Establish Cybersecurity In The Banking Company Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Driven Protection, Vulnerable Customers, Against Cyberattack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF. Use them to share invaluable insights on Goal, Security System, Reduce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF. Use them to share invaluable insights on Reduce Ransomware, Reduce Distributed, Approaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF
This slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing, Malware, Blackmail Hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. Find a pre-designed and impeccable Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
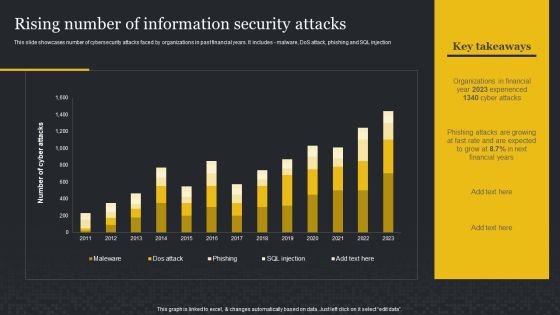
Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Boost your pitch with our creative Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF

Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF
This Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF
Are you searching for a Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF from Slidegeeks today.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF
Find highly impressive Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.

Agenda For Implementing Cybersecurity Awareness Program To Prevent Attacks Designs PDF
Create an editable Agenda For Implementing Cybersecurity Awareness Program To Prevent Attacks Designs PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Agenda For Implementing Cybersecurity Awareness Program To Prevent Attacks Designs PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity Guidelines IT Employee Awareness Training Budget For FY2022 Structure PDF
This slide describes the employee awareness training budget for FY2022. It includes provider, training date, duration, budget, qualification, capability level, and frequency. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Guidelines IT Employee Awareness Training Budget For FY2022 Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Guidelines IT Employee Awareness Training Budget For FY2022 Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

 Home
Home