Cybersecurity

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Table Of Contents Guidelines PDF
Deliver an awe inspiring pitch with this creative case competition overpower the obstacle of cyber security in medicare table of contents guidelines pdf bundle. Topics like swot analysis of abs healthcare company, abs healthcare company competitive analysis, abs healthcare company challenges and their solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Timeline Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare timeline sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Management Plan Addressing The Incidents Logging Process Diagrams PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an awe inspiring pitch with this creative cyber security risk management plan addressing the incidents logging process diagrams pdf bundle. Topics like process id, procedure, description, responsible person can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Defining The Severity Levels Of Risk Template PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan defining the severity levels of risk template pdf. Use them to share invaluable insights on risk level, risk score, description and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Defining Vulnerability Rating With Criteria Summary PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
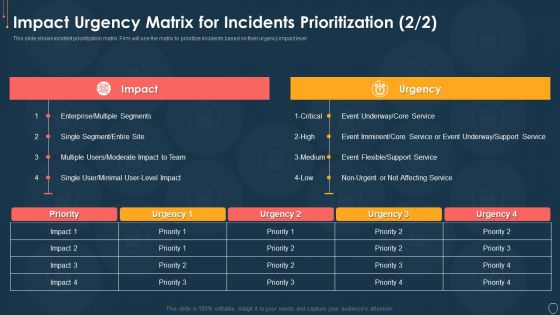
Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Event Topics PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative cyber security risk management plan impact urgency matrix for incidents prioritization event topics pdf bundle. Topics like impact urgency matrix for incidents prioritization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Location Information PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact urgency matrix for incidents prioritization location information pdf. Use them to share invaluable insights on business, location, inconvenient, moderate, preform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Incident Management Tool We Will Use Mockup PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative cyber security risk management plan incident management tool we will use mockup pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan 30 60 90 Days Plan Infographics PDF
This is a cyber security risk management plan 30 60 90 days plan infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Multitiered Risk Management Framework Diagram Inspiration PDF
This is a cyber security risk management plan multitiered risk management framework diagram inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like orgnization, mission or business processes, information systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Online And Onsite Training Schedule For Employee Elements PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative cyber security risk management plan online and onsite training schedule for employee elements pdf bundle. Topics like position, software name, course type, training mode, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Threat And Vulnerability Management Dashboard Portrait PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat and vulnerability management dashboard portrait pdf. Use them to share invaluable insights on exposure score, configuration score, severity distribution, vulnerable software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Cyber Security Administration In Organization Assets Background PDF
Presenting table of contents cyber security administration in organization assets background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like handling, assets, digital, workplace, violence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Addressing Natural Calamities Posing Threat Sample PDF
This slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an awe inspiring pitch with this creative cyber security administration in organization addressing natural calamities posing threat sample pdf bundle. Topics like sources, evacuation, environmental, contamination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Incident Reporting By Different Departments Download PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Deliver an awe inspiring pitch with this creative cyber security administration in organization incident reporting by different departments download pdf bundle. Topics like incident reporting by different departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Addressing Cyber Threats In Various Industries Brochure PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management addressing cyber threats in various industries brochure pdf. Use them to share invaluable insights on healthcare, manufacturing, government, energy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
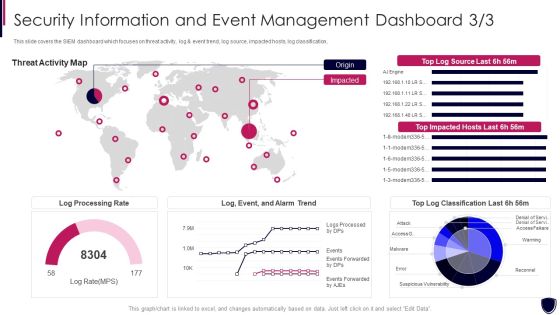
Security Information And Event Enhancing Cyber Safety With Vulnerability Administration Portrait PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event enhancing cyber safety with vulnerability administration portrait pdf bundle. Topics like log processing rate, threat activity map can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF
This is a Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Communication Plan For Insider Threat In Cyber Security Awareness Background PDF
This slide shows insider threat awareness communication plan. It provides information about discussions, description, frequency, communication method, etc. Showcasing this set of slides titled Communication Plan For Insider Threat In Cyber Security Awareness Background PDF. The topics addressed in these templates are Discussions, Threat Prevention, Industrial News. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF
This slide shows timeline depicting insider threat user logs. It contains information about archived activities, user event, policy violation trigger, capture continuation, etc. Pitch your topic with ease and precision using this Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF. This layout presents information on User Event, Policy Violation Trigger, Archived Logs. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF
This slide shows program for insider threat awareness training. It provides information such as program, details, system requirements, duration, fee or charge, etc. Showcasing this set of slides titled Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF. The topics addressed in these templates are Indicators Insider Threat, Protection Confidential Data, Insider Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. There are so many reasons you need a Prevention Of Information Major Statistics Of Cyber Security Awareness Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF
Want to ace your presentation in front of a live audience Our Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
Table Of Contents For Cyber Security Breache Response Strategy Formats PDF
Want to ace your presentation in front of a live audience Our Table Of Contents For Cyber Security Breache Response Strategy Formats PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Management Inspiration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting enhancing cyber safety with vulnerability administration security information and event management inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data retention, forensic analysis, dashboards, data correlation, data aggregation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
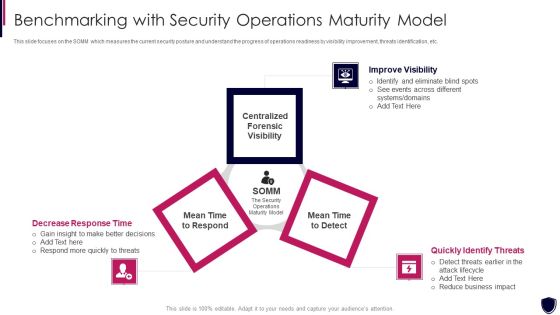
Enhancing Cyber Safety With Vulnerability Administration Benchmarking With Security Inspiration PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. This is a enhancing cyber safety with vulnerability administration benchmarking with security inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like improve visibility, quickly identify threats, decrease response time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era KPI Dashboard To Track Security Risk Events Ppt Inspiration PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era kpi dashboard to track security risk events ppt inspiration pdf. Use them to share invaluable insights on kpi dashboard to track security risk events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF
The following slide indicates key features of cloud managed security service. The features covered in the slide are low cost, data loss prevention, customized solutions and proactive maintenance and support. Presenting Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Low Cost, Customized Solutions, Additional Benefits. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides
The following slide illustrates report summary of managed security service which includes details about responsibility of service provider, what constitutes an emergency, response time by service provider and time of reporting. Showcasing this set of slides titled Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides. The topics addressed in these templates are Responsibility Of Service Provider, Time Of Reporting, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF
This slide outlines the different challenges faced by the companies with managed security service providers. The key challenges are lack of skilled staff, too many alerts and support experience. Presenting Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Too Many Alerts, Support Experience, Lack Skilled Staff. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF. Use them to share invaluable insights on Gap Analysis, Protect Resources, Communicate Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
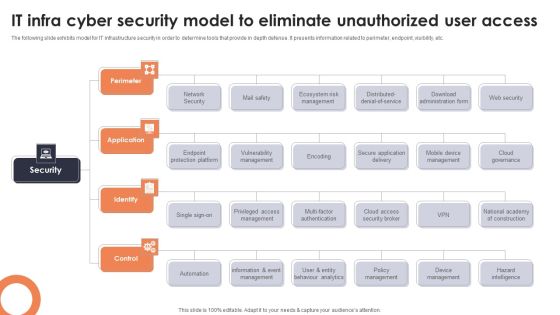
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Small Business Network Diagram 3d Man With Key Puzzle PowerPoint Slides
We present our small business network diagram 3d man with key puzzle PowerPoint Slides.Download and present our People PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Use our Security PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Present our Puzzles or Jigsaws PowerPoint Templates because You will get more than you ever bargained for. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use our Business PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless.Use these PowerPoint slides for presentations relating to 3d, Access, Art, Attached, Business, Choice, Community, Concept, Connection, Creativity, Cut, Decision, Defense, Human, Idea, Illustration, Integration, Isolated, Jigsaw, Join, Key, Latch, Link, Lock, Man, Part, People, Person, Piece, Privacy, Protect, Protection, Puzzle, Safeguard, Safety, Security, Solution, Solve, Strategy, Toy, United\n. The prominent colors used in the PowerPoint template are Red, White, Gray. PowerPoint presentation experts tell us our small business network diagram 3d man with key puzzle PowerPoint Slides are incredible easy to use. Professionals tell us our Business PowerPoint templates and PPT Slides look good visually. People tell us our small business network diagram 3d man with key puzzle PowerPoint Slides are designed by a team of presentation professionals. Presenters tell us our Concept PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Professionals tell us our small business network diagram 3d man with key puzzle PowerPoint Slides are readymade to fit into any presentation structure. We assure you our Concept PowerPoint templates and PPT Slides will save the presenter time.

Building Cyber Risk Prevention In Financial Services Sector Elements PDF
The slide showcases the steps to develop the cyber resiliency of financial services industry. It covers steps like secure by design, zero trust, third party cyber risk assessment, security awareness training and cyber insurance. Persuade your audience using this Building Cyber Risk Prevention In Financial Services Sector Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Secure By Design, Zero Trust, Security Awareness Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF
This slide highlights tracking sheet of security incidents occurred in several departments in an organization. The purpose of this template is to provide information to the management about security breaches in the company. It includes elements such as number of incidents, cost per incident, team responsiveness rates, status of action taken, etc. Pitch your topic with ease and precision using this Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF. This layout presents information on Key Components, Cost Per Incident, Team Responsiveness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
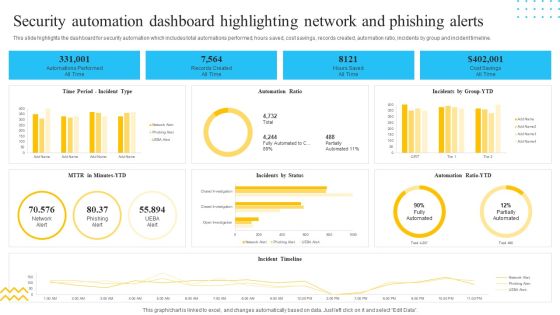
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF bundle. Topics like Records Created, All Time, Hours Saved, Cost Savings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Disaster Recuperation Six Months Roadmap To Eradicate Intrusion Icons
Presenting the cyber security disaster recuperation six months roadmap to eradicate intrusion icons. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Security Tactic For Process Management For IT Roadmap Three Months Demonstration
Presenting our jaw dropping cyber security tactic for process management for it roadmap three months demonstration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Cyber Security Risk Management Plan Asset Criticality Of Identified System Components Mockup PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan asset criticality of identified system components mockup pdf. Use them to share invaluable insights on system name, component used, impact rating, criticality rating, failure cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Management Plan Mitigation Plan For Resolving Encountered Threat Pictures PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an awe inspiring pitch with this creative cyber security risk management plan mitigation plan for resolving encountered threat pictures pdf bundle. Topics like threat encountered, mitigation plan, responsible person, communication mode, risk level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home