Cybersecurity

Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF
This slide highlights scorecard related to security breaches in gaming field. The purpose of this template is to rate the incidents based on severity. It includes elements such as account taken over, personal details posting on web, spyware, data breaches and cyber bullying. Showcasing this set of slides titled Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF. The topics addressed in these templates are Incident, Score, Data Breaches, Low, High. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Make sure to capture your audiences attention in your business displays with our gratis customizable Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
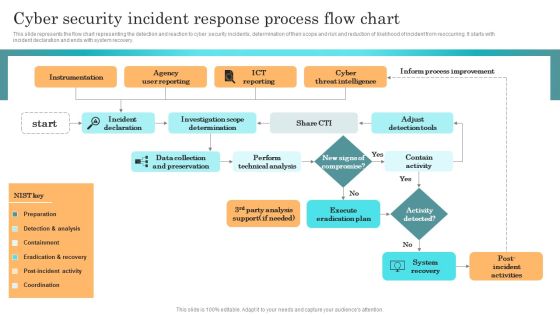
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.
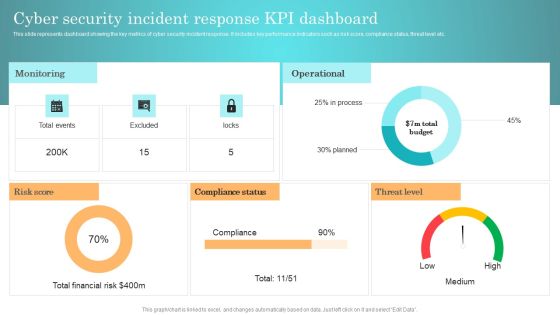
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF
The following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Want to ace your presentation in front of a live audience Our Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Three Lines Of Defense Border Model For Cyber Security Designs PDF
This slide represents the model of lines of defense for products and services quality assurance. It includes activities performed in first, second and third line of defense for quality assurance such as risk management, monitor and support in risk related matters, internal quality audits etc. Presenting Three Lines Of Defense Border Model For Cyber Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security, Three Lines, Border Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Terrorism Assault Managing Cyber Terrorism 60 Days Plan Clipart PDF
This slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault managing cyber terrorism 60 days plan clipart pdf Use them to share invaluable insights on time to detect an incident, data loss incidents, infected computers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF
Mentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Showcasing this set of slides titled Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF. The topics addressed in these templates are Endpoint Protection, Firewall, Email Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF
This slide exhibits the different types of managed security services such as risk management, virtual CISO and security awareness education. It also provides information about the multiple offerings of each service. Persuade your audience using this Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Offerings, Security Awareness Education, Virtual CISO. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF
This slide exhibits the various application security approaches which can be implemented by organization to manage their IT services. The key approaches are design review, code review and application security audit Showcasing this set of slides titled Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF. The topics addressed in these templates are Design Review, Code Review, Approaches, Application Security Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF
This slide highlights security risks occurred in the company. The purpose of this template is to report the severity of security threats. It also includes action steps taken in prevention or resolution of security incidents along with risk categories. Showcasing this set of slides titled Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF. The topics addressed in these templates are Incidents, Category, Severity, Response Action Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management.. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. This Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well arranged Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Incident Response Techniques Deployement Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. This Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
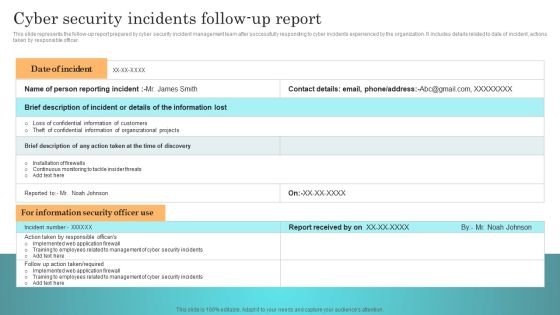
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF
The following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Slidegeeks has constructed Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
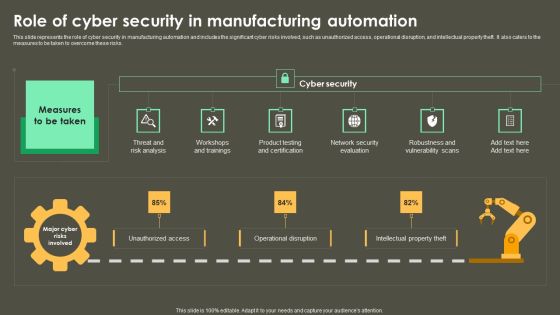
Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well-arranged Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Rules And Regulations With Accuracy Ppt PowerPoint Presentation Slides Outfit
Presenting this set of slides with name cyber security rules and regulations with accuracy ppt powerpoint presentation slides outfit. This is a six stage process. The stages in this process are purpose and manner of collection, accuracy and duration of retention, use of personal data, security of personal data, information to be generally available, access to personal data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Determining Roles And Responsibilities For Risk Handling Ppt Outline Example PDF
Presenting this set of slides with name cyber security for your organization determining roles and responsibilities for risk handling ppt outline example pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management, executive, line management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Determining Roles And Responsibilities For Risk Handling Ideas PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining roles and responsibilities for risk handling ideas pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Risk Management Plan System Management Checklist With Key Activities Structure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative cyber security risk management plan system management checklist with key activities structure pdf bundle. Topics like system monitoring, data backup, security patches, virus scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Using System Categorization Sheet For Asset Identification Template PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information. Deliver an awe inspiring pitch with this creative cyber security risk management plan using system categorization sheet for asset identification template pdf bundle. Topics like location, accessibility, organization, access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Information And Event Dashboard Enhancing Cyber Safety With Vulnerability Administration Formats PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this security information and event dashboard enhancing cyber safety with vulnerability administration formats pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Security Lifecycle Ppt Summary Brochure PDF
This is a handling cyber threats digital era security lifecycle ppt summary brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Icon For Managed Cyber Cloud Security Service Ppt Outline Graphic Tips PDF
Persuade your audience using this Icon For Managed Cyber Cloud Security Service Ppt Outline Graphic Tips PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon, Cloud Security, Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF bundle. Topics like Gap Analysis, Environmental Trends, Business Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF
The following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy,disaster recovery, password encryption, tasks, reviews etc. There are so many reasons you need a Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Wireless Network Security System Icon Of Cloud Servers To Secure Data Clipart PDF
Persuade your audience using this wireless network security system icon of cloud servers to secure data clipart pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon of cloud servers to secure data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Information Security Cloud Security Checklist Networking Ppt Infographics Deck PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. This is a Cloud Information Security Cloud Security Checklist Networking Ppt Infographics Deck PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ensure Security, Data Supposed, Encrypt Critical. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Five Stages Circular Process Business Cyber Security Ppt PowerPoint Presentation Icon Tips
Presenting this set of slides with name five stages circular process business cyber security ppt powerpoint presentation icon tips. This is a five stage process. The stages in this process are technology, strategy, steps approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Testing Process With Icons Ppt PowerPoint Presentation Infographic Template Demonstration
Presenting this set of slides with name cyber security testing process with icons ppt powerpoint presentation infographic template demonstration. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Five Techniques Of Cyber Security Testing Ppt PowerPoint Presentation Layouts Model
Presenting this set of slides with name five techniques of cyber security testing ppt powerpoint presentation layouts model. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Process Steps With Icons Ppt PowerPoint Presentation Summary Slide
Presenting this set of slides with name cyber security process steps with icons ppt powerpoint presentation summary slide. This is a four stage process. The stages in this process are assess, evaluate, build, execute. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security for your organization ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are risk management, business, analysis, goal, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Backup Maintenance Recovery Budget Planning Ppt Inspiration Slide Portrait PDF
Presenting this set of slides with name cyber security for your organization backup maintenance recovery budget planning ppt inspiration slide portrait pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, travel shipping costs, labor contractor costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Critical Business Functions Recovery Priorities Ppt Inspiration Slide PDF
Presenting this set of slides with name cyber security for your organization critical business functions recovery priorities ppt inspiration slide pdf. This is a one stage process. The stages in this process are priorities, maximum allowable downtime, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Essential Contingency Plan Strategies Ppt Layouts Vector PDF
Presenting this set of slides with name cyber security for your organization essential contingency plan strategies ppt layouts vector pdf. This is a one stage process. The stages in this process are contingency considerations, contingency solutions, server, vendor information, critical components, technologies integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Mission Ppt Infographics Model PDF
Presenting this set of slides with name cyber security for your organization our mission ppt infographics model pdf. This is a one stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Team Ppt Ideas Infographic Template PDF
Presenting this set of slides with name cyber security for your organization our team ppt ideas infographic template pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Recovery Task List Maintenance Ppt Layouts Designs Download PDF
Presenting this set of slides with name cyber security for your organization recovery task list maintenance ppt layouts designs download pdf. This is a one stage process. The stages in this process are estimated time, actual time, assigned, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Risk Assessment Matrix Ppt Ideas PDF
Presenting this set of slides with name cyber security for your organization risk assessment matrix ppt ideas pdf. This is a one stage process. The stages in this process are insignificant, minor, severity, risk, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Staff Training Schedule With Cost Ppt Visual Aids Slides PDF
Presenting this set of slides with name cyber security for your organization staff training schedule with cost ppt visual aids slides pdf. This is a one stage process. The stages in this process are advanced software training, advanced skills train, training module. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Thank You Ppt Portfolio Clipart PDF
Presenting this set of slides with name cyber security for your organization thank you ppt portfolio clipart pdf. The topics discussed in these slide is thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Timeframe For Incident Management Ppt Icon Graphics Design PDF
Presenting this set of slides with name cyber security for your organization timeframe for incident management ppt icon graphics design pdf. This is a one stage process. The stages in this process are incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Weekly Timeline With Task Name Ppt Outline Ideas PDF
Presenting this set of slides with name cyber security for your organization weekly timeline with task name ppt outline ideas pdf. The topics discussed in these slide is organization weekly timeline. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Amount Spent On Cyber Fraud Settlements Portrait PDF
Presenting this set of slides with name computer security incident handling amount spent on cyber fraud settlements portrait pdf. The topics discussed in these slides are settlements, amount, average. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Categorization Of Cyber Risks Ppt Gallery Template PDF
Presenting this set of slides with name computer security incident handling categorization of cyber risks ppt gallery template pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Incident Reporting By Different Cyber Departments Brochure PDF
Presenting this set of slides with name computer security incident handling incident reporting by different cyber departments brochure pdf. The topics discussed in these slides are description, department a, department b, department c, department d. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Strategies To Mitigate Cyber Security Risks Ppt Icon Themes PDF
Presenting this set of slides containing editable icons for topic icons slide for strategies to mitigate cyber security risks ppt icon themes pdf. All icons in this slide are 100 percent editable. You can replace icons in your deck with any of these icons. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks 30 60 90 Days Plan Ppt Icon Picture PDF
Presenting this set of slides with name strategies to mitigate cyber security risks 30 60 90 days plan ppt icon picture pdf. This is a three stage process. The stages in this process are 30 60 90 days. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
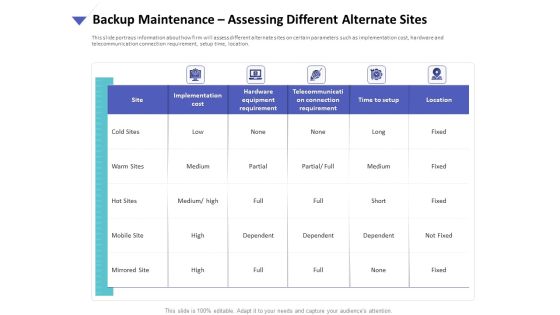
Strategies To Mitigate Cyber Security Risks Backup Maintenance Assessing Different Alternate Sites Ppt Portfolio Background PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance assessing different alternate sites ppt portfolio background pdf. The topics discussed in these slides are implementation cost, hardware equipment requirement, telecommunication connection requirement, time setup, location. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Developing Alternate Sites Ppt Templates PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance developing alternate sites ppt templates pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Recovery Budget Planning Ppt Ideas Graphic Images
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance recovery budget planning ppt ideas graphic images. This is a one stage process. The stages in this process are vendor costs, hardware costs, software costs, equipment replacement, testing costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
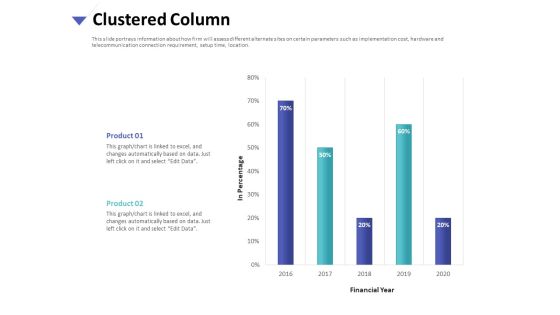
Strategies To Mitigate Cyber Security Risks Clustered Column Ppt Inspiration Example PDF
Presenting this set of slides with name strategies to mitigate cyber security risks clustered column ppt inspiration example pdf. The topics discussed in these slide is clustered column. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home