Cyber Security Operations

Optimizing Tasks Team Collaboration Agile Operations Prioritizing Agile Software Development Tasks Guidelines PDF
Presenting this set of slides with name optimizing tasks team collaboration agile operations prioritizing agile software development tasks guidelines pdf. This is a five stage process. The stages in this process are quick delivery of project deliverables, enhancing team communication, customer collaboration, minimize cyber security risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Terrorism Assault How To Prevent Ddos Attacks In The Company Inspiration PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc.Presenting cyber terrorism assault how to prevent ddos attacks in the company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like service providers bandwidth capacity, network monitoring, update security components In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF
This slide illustrates the roles and responsibilities of the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Explore a selection of the finest Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF
This slide talks about the various advantages of SOC-as-a-Service for organizations. The purpose of this slide is to highlight the main pros of security operations centers, including lowering the risk of data breaches, quick detection and remediation, ability to scale, resource optimization, enhanced maturity, and lowering costs. Find highly impressive Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF
This slide outlines the overview of dedicated SOC, including its goal and advantages and disadvantages. The purpose of this slide is to showcase the dedicated security operations center covering its benefits and drawbacks. The goal of this SOC center is to monitor information systems around the clock. Create an editable Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF
This slide represents the overview, benefits and disadvantages of virtual security operation center model. The purpose of this slide is to highlight the advantage, disadvantages and alternative approaches for VSOC such as outsourcing of virtual SOC model. This modern and well arranged Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF
This slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti-phishing, data discovery, and packet-level visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Development And Operations KPI Dashboard For Determining Active Bugs Portrait PDF
This slide template covers about determining email and voice bugs during production line. Further, it covers about active bugs on weekly basis.Showcasing this set of slides titled Development And Operations KPI Dashboard For Determining Active Bugs Portrait PDF The topics addressed in these templates are Development Operations, Dashboard Determining, Active Bugs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

E Commerce Operations In B2b Email Marketing Strategies To Enhance Professional PDF
This slide represents email marketing tactics used by marketers to increase conversion rate and engagement level on ecommerce website. It includes automated welcome emails, deliver lead magnet etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give E Commerce Operations In B2b Email Marketing Strategies To Enhance Professional PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable E Commerce Operations In B2b Email Marketing Strategies To Enhance Professional PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Streamlining Operations Through Clothing Business Strategy Email Marketing To Restore Lost Portrait PDF
This slide showcases cart abandonment email marketing to re-target customers. The slide includes impact which are attract more customers, enhance brand recognition and improve sales. Welcome to our selection of the Streamlining Operations Through Clothing Business Strategy Email Marketing To Restore Lost Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Developing Implementing Organization Marketing Promotional Strategies Marketing Operations Strategy Summary PDF
Deliver an awe inspiring pitch with this creative developing implementing organization marketing promotional strategies marketing operations strategy summary pdf bundle. Topics like website, email, content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
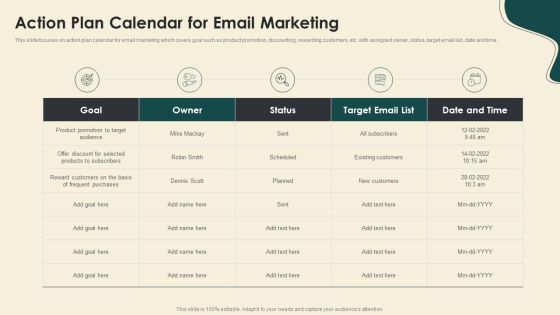
Digitally Streamline Automation Sales Operations Action Plan Calendar For Email Marketing Infographics PDF
This slide focuses on action plan calendar for email marketing which covers goal such as product promotion, discounting, rewarding customers, etc. with assigned owner, status, target email list, date and time. Deliver and pitch your topic in the best possible manner with this Digitally Streamline Automation Sales Operations Action Plan Calendar For Email Marketing Infographics PDF. Use them to share invaluable insights on Goal, Owner, Target Email List and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Sales Automation Process To Streamline Workflow Digitally Streamline Automation Sales Operations Professional PDF
This slide shows the sales automation process to streamline workflow which includes lead capturing, assigning duty, lead calling, showing demo, email scheduling and following up. Deliver an awe inspiring pitch with this creative Sales Automation Process To Streamline Workflow Digitally Streamline Automation Sales Operations Professional PDF bundle. Topics like Optimize Contact Management, Sales Information, Sales Executive can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Optimizing The Marketing Operations To Drive Efficiencies Marketing Reach By Channels Sources Infographics Guidelines PDF
Deliver an awe inspiring pitch with this creative optimizing the marketing operations to drive efficiencies marketing reach by channels sources infographics guidelines pdf bundle. Topics like marketing, sources, online media, emails can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
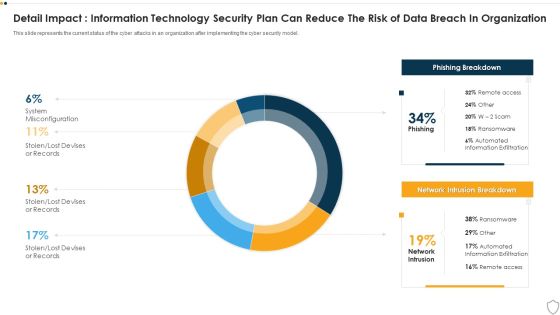
IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF
This slide outlines the timeline to implement SecOps in an organization. The purpose of this slide is to demonstrate the various steps businesses will follow while implementing SecOps, including collecting needs, defining scope, building repeatable workflows, conducting red-blue team training, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cybersecurity Operations Cybersecops Roadmap To Implement Secops In Business Background PDF
This slide represents the roadmap to implement SecOps in an organization. The purpose of this slide is to demonstrate the various steps businesses will follow while implementing SecOps, including collecting needs, defining scope, building repeatable workflows, conducting red-blue team training, etc. This Cybersecurity Operations Cybersecops Roadmap To Implement Secops In Business Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cybersecurity Operations Cybersecops Roadmap To Implement Secops In Business Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cybersecurity Operations Cybersecops Metrics To Track Secops Impact On Business Icons PDF
This slide refers to the key metrics to track the impact of SecOps implementation on business. The purpose of this slide is to highlight the key metrics for SecOps tracking, including mean time to acknowledge, mean time to resolve, incidents remediated and escalations between each tier. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Metrics To Track Secops Impact On Business Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Metrics To Track Secops Impact On Business Icons PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Business Operations Assessment Developing Marketing Strategies Optimization Ppt Icon Infographics PDF
Presenting business operations assessment developing marketing strategies optimization ppt icon infographics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like search engine optimization, content marketing, email marketing, pay per click advertising, social media marketing, optimization. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Operations Assessment Developing Marketing Strategies Technologies Ppt Layouts Graphics Pictures PDF
This is a business operations assessment developing marketing strategies technologies ppt layouts graphics pictures pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital technologies, content marketing, social media, email marketing, seo, campaign. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
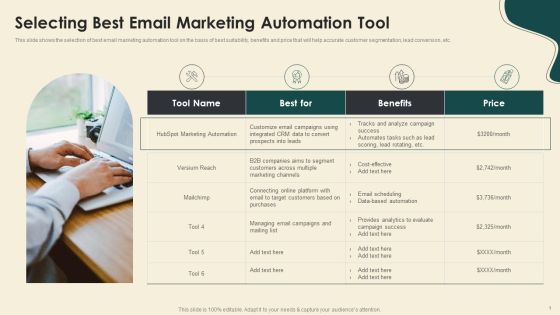
Digitally Streamline Automation Sales Operations Selecting Best Email Marketing Automation Tool Structure PDF
This slide shows the selection of best email marketing automation tool on the basis of best suitability, benefits and price that will help accurate customer segmentation, lead conversion, etc. Presenting Digitally Streamline Automation Sales Operations Selecting Best Email Marketing Automation Tool Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Marketing Automation, Marketing Channels, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digitally Streamline Automation Sales Operations Choose Successful Email Marketing Campaign Pictures PDF
This slide shows the comparison of email marketing campaign on the basis of open and click rates. It also includes customer segments, campaign goal, schedule and campaign tracking metrics. Deliver and pitch your topic in the best possible manner with this Digitally Streamline Automation Sales Operations Choose Successful Email Marketing Campaign Pictures PDF. Use them to share invaluable insights on Campaign Goal, Customer Segment, Target and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
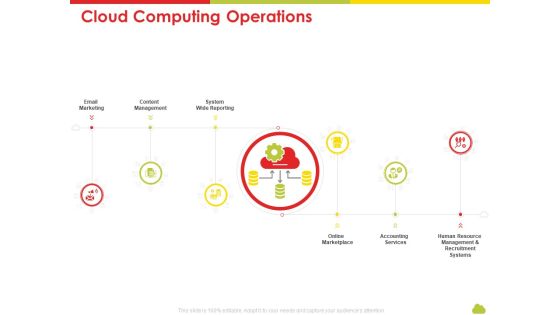
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Operations Slides PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan cloud computing operations slides pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email marketing, content management, accounting services, system wide reporting. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Optimizing The Marketing Operations To Drive Efficiencies Manage Channel Partner Program Information PDF
This is a optimizing the marketing operations to drive efficiencies manage channel partner program information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like face to face and webex training, channel flash email newsletter, video library. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management For Improving IT Operations Determine Various Configuration Profiles Portrait PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Mobile Device Management For Improving IT Operations Determine Various Configuration Profiles Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Mobile Device Management For Improving IT Operations Determine Various Configuration Profiles Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Applications Of Claude Ai For Sales And Marketing Operations Elements PDF
This slide showcases key use cases of Claud.ai large language model applications available to sales and marketing teams. It provides details about sales pitch, angry customers, email, virtual representative, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Applications Of Claude Ai For Sales And Marketing Operations Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Business Operations Assessment Developing Marketing Strategies Ppt Icon Background Designs PDF
This is a business operations assessment developing marketing strategies ppt icon background designs pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like use social media, create video tutorials, start blogging now, understand search engine optimization, leverage influencers, use email marketing sequences, create affiliate program, use linkedin right way, use facebook ads with re targeting, build great lead magnet. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Streamlining Operations Through Clothing Business Strategy Ecommerce Clothing Retail Download PDF
This slide provides an overview of the apparel firm. It includes companys mission, vision, principles and highlights that covers headquarter, employees, valuation, business model, website, email, etc. This Streamlining Operations Through Clothing Business Strategy Ecommerce Clothing Retail Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

30 60 90 Days Digital Marketing Operations Training Department Program Plan Information PDF
This slide covers 3 month schedule to train new digital marketing interns. It includes training based on marketing introduction, soft skill development, paid advertising, email marketing, SEO, social media, content and influencer marketing, public relations, etc. Presenting 30 60 90 Days Digital Marketing Operations Training Department Program Plan Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Introduction To Marketing, Paid Advertising, Digital Marketing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF
This slide represents the overview and primary functions of SOC-as-a-Service. The purpose of this slide is to demonstrate the various critical functions and key features, and it also covers the reasons for organizations to adopt the subscription-based model. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Streamlining Operations Through Clothing Business Strategy Budgeted And Actual Cost Information PDF
This slide showcases the budget and actual cost spend on marketing channels for brand marketing. The channels covered are PPC, affiliate, influencer, video and email marketing, Facebook ads and search engine optimization. This Streamlining Operations Through Clothing Business Strategy Budgeted And Actual Cost Information PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Attacks Experienced By The Company In Previous Financial Year Download PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this cyber attacks experienced by the company in previous financial year download pdf. Use them to share invaluable insights on cyber attacks experienced by the company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Infographics PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year ppt infographics pdf bundle. Topics like cyber attacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Summary PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative cyber stacks experienced by the company in previous financial year ppt summary pdf bundle. Topics like cyber stacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Setting Scenario For Cybersecurity Control Ppt Infographics Brochure PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting handling cyber threats digital era setting scenario for cybersecurity control ppt infographics brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
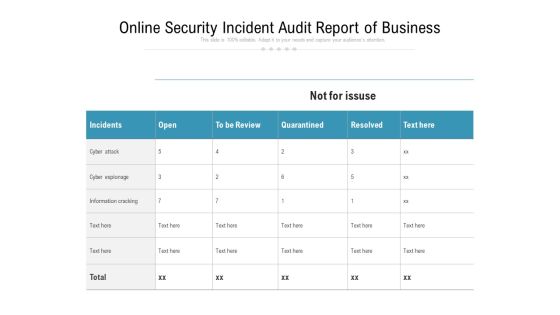
Online Security Incident Audit Report Of Business Ppt PowerPoint Presentation Inspiration Layout Ideas PDF
Pitch your topic with ease and precision using this online security incident audit report of business ppt powerpoint presentation inspiration layout ideas pdf. This layout presents information on incidents, cyber attack, cyber espionage, information cracking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Other Cyber Strategies Of KPMG For Client Data Protection Structure PDF
This slide covers introduction to KPMG strategy related to operations for business transformation. The purpose of this template is to provide an overview based on benefits of KPMG operational strategies along with insights and key operations at KPMG. It includes operations such as advisory, tax and legal services, audit, etc. This modern and well-arranged Other Cyber Strategies Of KPMG For Client Data Protection Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Terrorism Assault Updating Hardware And Software In Company Infographics PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems.Deliver an awe inspiring pitch with this creative cyber terrorism assault updating hardware and software in company infographics pdf bundle. Topics like peripheral devices, security necessitates, traditional ways to data transport can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Companys Data Safety Recognition Cyber Attacks Experienced By The Company In Previous Financial Year Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. This is a companys data safety recognition cyber attacks experienced by the company in previous financial year sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system misconfiguration, inadvertent disclosure, network intrusion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

What Is IT Security IT And How Does IT Work Ppt Slides Gridlines PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a what is it security it and how does it work ppt slides gridlines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like techniques, computer systems, networks, servers, mobile devices, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF
The following slide highlights insurance sales cycle for cyber security to improve market penetration and reduce security risks and data thefts. It includes components such as attractive price offers or buyers, improve value proposition, training and development and upgrade agent or broker support. Presenting Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Broker Support, Development, Proposition. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Policies Inspiration PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Presenting continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring policies inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF
This slide covers plan related to workplace security awareness training program. It includes elements such as training providers, target employees and training topics related to BYOD, phishing, social engineering, data handling, privacy, security engineering, insider threat, etc. Pitch your topic with ease and precision using this Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF. This layout presents information on Employee, Target, Developer. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
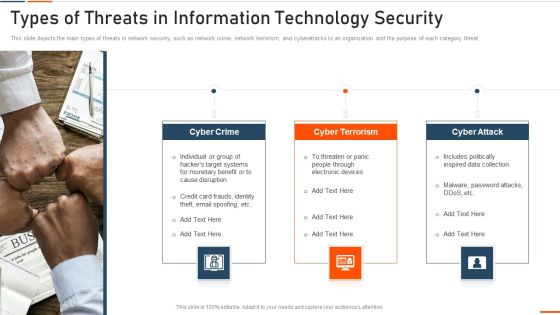
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home