Cyber Security Operations

Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Boost your pitch with our creative Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Desktop Security Management Common Methods Used To Threaten Computer Security Template PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a desktop security management common methods used to threaten computer security template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, services, network, database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Cloud Security Checklist Backup And Data Recovery Ppt Layouts Infographic Template PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting Cloud Information Security Cloud Security Checklist Backup And Data Recovery Ppt Layouts Infographic Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Plan, Cyber Attacks, Plans Timely. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
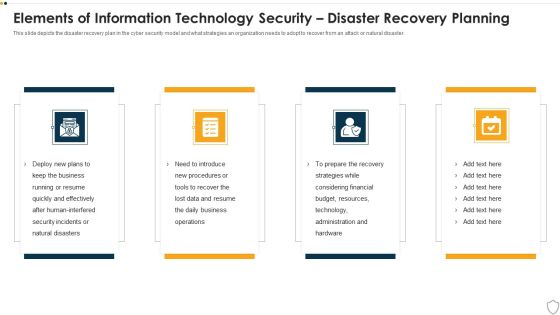
IT Security Elements Of Information Technology Security Disaster Recovery Planning Ppt Infographics Design Ideas PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting it security elements of information technology security disaster recovery planning ppt infographics design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, financial, budget, resources, effectively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Pricing Plan Of Security Awareness Packages Diagrams PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Take your projects to the next level with our ultimate collection of Organizing Security Awareness Pricing Plan Of Security Awareness Packages Diagrams PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Russian Cyber Attacks On Ukraine IT Weaknesses Of Russian Cyber Cell Portrait PDF
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it weaknesses of russian cyber cell portrait pdf bundle. Topics like opportunities, security, outsource, capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
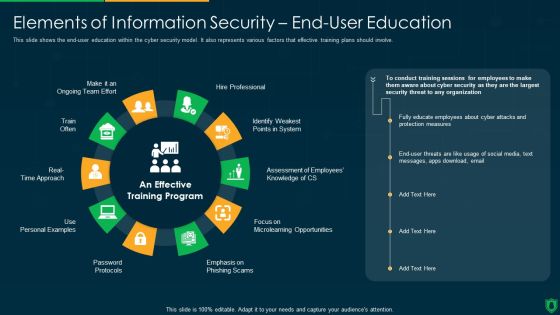
Info Security Elements Of Information Security End User Education Ppt PowerPoint Presentation File Example File PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Presenting info security elements of information security end user education ppt powerpoint presentation file example file pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like hire professional, emphasis on phishing scam, password protocols, train often. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Revenue Losses Cloud Computing Security IT Ppt Ideas Rules PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. This is a cloud security threats revenue losses cloud computing security it ppt ideas rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cyber threats, revenue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cyber Threats, Organizations Could, Drastic Decrease. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
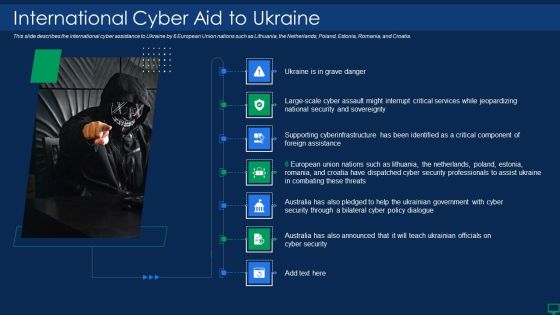
Russian Cyber Attacks On Ukraine IT International Cyber Aid Sample PDF
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it international cyber aid sample pdf bundle. Topics like security, services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
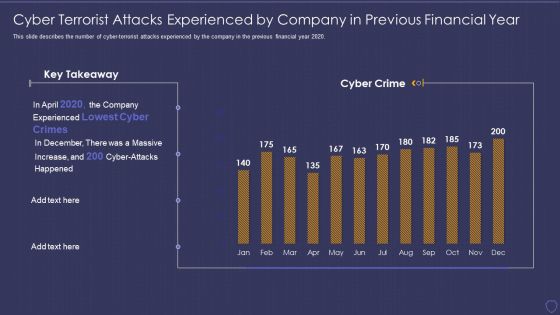
Global Cyber Terrorism Incidents On The Rise IT Cyber Terrorist Attacks Experienced Formats PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2020. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it cyber terrorist attacks experienced formats pdf bundle. Topics like cyber terrorist attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
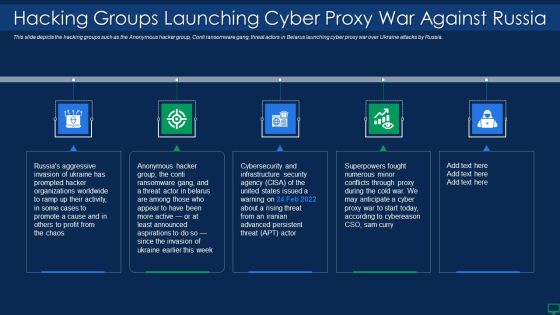
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Physical System To Enhance Concept Map Of Cyber Physical Systems Topics PDF
This slide represents the concept map of the cyber-physical system that includes feedback systems, cyber security, improved design tools, design methodology, and its applications. Present like a pro with Cyber Physical System To Enhance Concept Map Of Cyber Physical Systems Topics PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Physical System To Enhance Cyber Physical Systems In Smart Transportation Systems Icons PDF
This slide depicts the application of CPS in transportation systems, including its benefits such as traffic control, boosting operational efficiency, and safety for road traffic systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Physical System To Enhance Cyber Physical Systems In Smart Transportation Systems Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Assessment Matrix Of Cyber Terrorism Ideas PDF
This slide demonstrates the cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it assessment matrix of cyber terrorism ideas pdf bundle. Topics like financial theft or froud, reputation damage, regulatory, competitors, destruction of critical infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Loss Due To Different Cyber Attacks Designs PDF
This slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Deliver an awe inspiring pitch with this creative cyber exploitation it loss due to different cyber attacks designs pdf bundle. Topics like loss due to different cyber attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
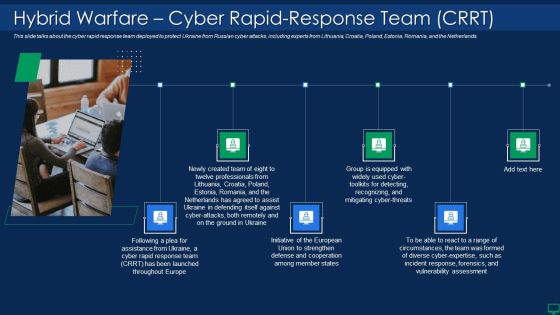
Russian Cyber Attacks On Ukraine IT Hybrid Warfare Cyber Rapid Structure PDF
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyber attacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands. Presenting russian cyber attacks on ukraine it hybrid warfare cyber rapid structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like hybrid warfare cyber rapid response team crrt. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Cyber Terrorist Experienced By Company In Previous Financial Year Sample PDF
This slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2022.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorist experienced by company in previous financial year sample pdf bundle. Topics like Increased Costs, Reputational Damage, Intellectual Property Theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Terrorism Assault Cyber Terrorism Attacks Awareness Programme For Employees Clipart PDF
This slide depicts the cyber terrorism attacks awareness programm for employees, including the name of the participants and what modules would be covered under training.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorism attacks awareness programme for employees clipart pdf bundle. Topics like Unanticipated Occurrence, Multiple Copies Of Data, Malicious Assaults can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
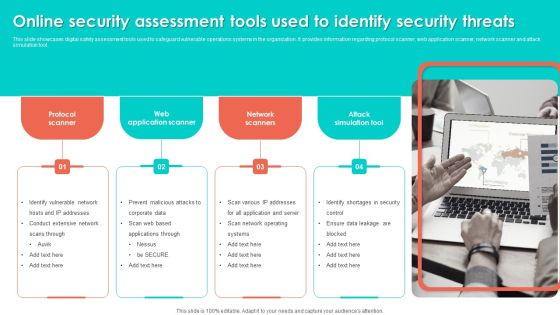
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Terrorism Assault Cyber Terrorism Faced By Various Industries Pictures PDF
This slide describes the cyber terrorism attacks various industries face, including health, finance, media, transportation and education.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorism faced by various industries pictures pdf bundle. Topics like Cyber Terrorism Faced By Companies In US can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Terrorism Assault Dashboard For Threat Tracking Of Cyber Terrorism Themes PDF
This slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault dashboard for threat tracking of cyber terrorism themes pdf Use them to share invaluable insights on Massive Increase, Cyber Attacks Happened, Company Experienced and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
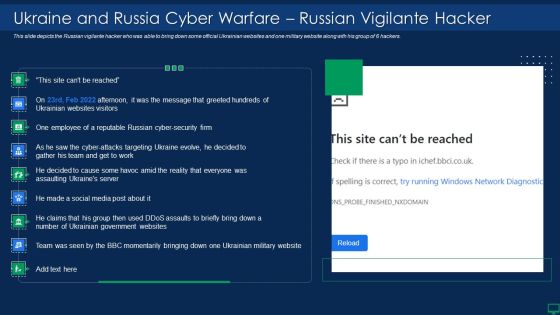
Russian Cyber Attacks On Ukraine IT Ukraine And Russia Cyber Warfare Elements PDF
This slide represents the Ukraine and Russia cyber warfare impact on western countries such as the United States, United Kingdom, and Estonia. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it ukraine and russia cyber warfare elements pdf bundle. Topics like businesses, networks, internet, cybersecurity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Russian Cyber Attacks On Ukraine IT Shuckworm Continues Cyber Espionage Ideas PDF
Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it shuckworm continues cyber espionage ideas pdf bundle. Topics like organization, devices, emails can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Does Ukraine And Russia Cyber Diagrams PDF
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it does ukraine and russia cyber diagrams pdf bundle. Topics like does ukraine and russia cyber warfare kill people can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
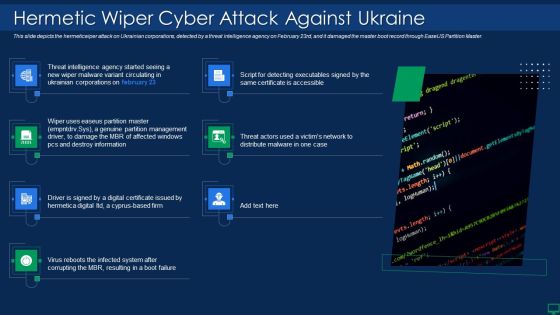
Russian Cyber Attacks On Ukraine IT Hermetic Wiper Cyber Attack Infographics PDF
Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it hermetic wiper cyber attack infographics pdf bundle. Topics like information, management, system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
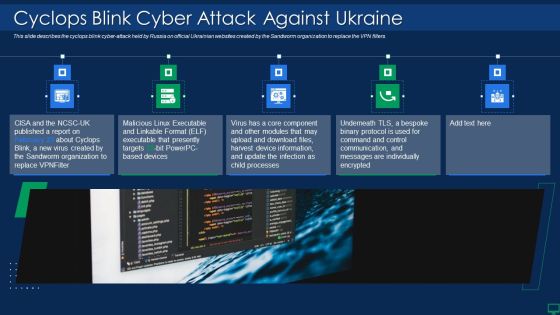
Russian Cyber Attacks On Ukraine IT Cyclops Blink Cyber Attack Mockup PDF
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters. This is a russian cyber attacks on ukraine it cyclops blink cyber attack mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device, processes, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Cyber Terrorism Faced By Companies In US Mockup PDF
This slide depicts the cyber terrorism attacks faced by the companies in the US, and the graph represents the financial losses in the last five years. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault cyber terrorism faced by companies in us mockup pdf Use them to share invaluable insights on Consequences Of Cyber Attacks, Response Planning, Recovery Strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Russian Cyber Attacks On Ukraine IT Cyber Attacks On Ukraine Information PDF
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. Presenting russian cyber attacks on ukraine it cyber attacks on ukraine information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like social media, systems, networks, services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT Ukraine And Russia Cyber Warfare Impact Information PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it ukraine and russia cyber warfare impact information pdf bundle. Topics like ukraine and russia cyber warfare russian vigilante hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Systems Security And Risk Management Plan Financial Impact Of Information Security Attacks Microsoft PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Create an editable Information Systems Security And Risk Management Plan Financial Impact Of Information Security Attacks Microsoft PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Information Systems Security And Risk Management Plan Financial Impact Of Information Security Attacks Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Create an editable Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF today and make your presentation stand out from the rest.
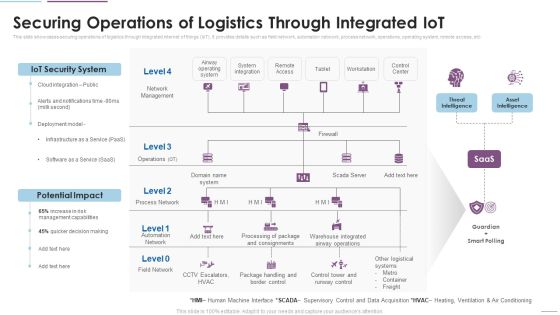
Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. This is a Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IoT Security System, Potential Impact, Network Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Employee Awareness Training Budget Against Cyber Terrorism FY2020 Inspiration PDF
This slide demonstrates the employee awareness training budget against cyber-terrorism by a graph that includes the training date, and the degree of capacity. Deliver an awe inspiring pitch with this creative cyber terrorism assault employee awareness training budget against cyber terrorism fy2020 inspiration pdf bundle. Topics like Protect Cardholder Data, Maintain A Vulnerability, Management Program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
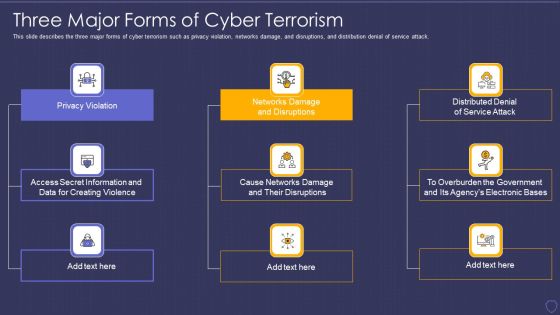
Global Cyber Terrorism Incidents On The Rise IT Three Major Forms Of Cyber Terrorism Topics PDF
This slide describes the three major forms of cyber terrorism such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Presenting global cyber terrorism incidents on the rise it three major forms of cyber terrorism topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like privacy violation, networks damage and disruptions, distributed denial of service attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Three Major Forms Of Cyber Terrorism Brochure PDF
This slide describes the three major forms of cyber terrorism attacks such as privacy violation, networks damage, and disruptions, and distribution denial of service attack.This is a cyber terrorism assault three major forms of cyber terrorism brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privacy violation, networks damage and disruptions, distributed denial You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Intelligent Computing System Cyber Physical Systems In Water Distribution Systems Portrait PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Cyber Physical Systems In Water Distribution Systems Portrait PDF bundle. Topics like Network, Data Acquisition Systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Global Cyber Terrorism Incidents On The Rise IT Phishing Cyber Terrorism Tool Rules PDF
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Presenting global cyber terrorism incidents on the rise it phishing cyber terrorism tool rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like phishing cyber terrorism tool. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Phishing Techniques Misused For Cyber Assault Ideas PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Presenting global cyber terrorism incidents on the rise it phishing techniques misused for cyber assault ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like spear phishing, smishing and vishing, whaling, email phishing scams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Malicious Code Malware Misused For Cyber Terrorism Pictures PDF
This slide depicts the malicious code or malware misused for cyber terrorism attacks to hijack or access information from computers.Presenting cyber terrorism assault malicious code malware misused for cyber terrorism pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like broad spectrum, executed by changing, programmer by stopping In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT What Is Cyber Terrorism Infographics PDF
This slide describes cyber-terrorism and how it is used to access sensitive information and political or psychological aimed attacks. This is a global cyber terrorism incidents on the rise it what is cyber terrorism infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like political, ideological gain, networks, violating privacy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Distributed Denial Of Service DDOS As Cyber Terrorism Tool Slides PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault distributed denial of service ddos as cyber terrorism tool slides pdf Use them to share invaluable insights on Make A Risk Assessment, Determine The Importance Of Assets, Make A Complete Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Phishing Techniques Misused For Cyber Assault Slides PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. This is a cyber terrorism assault phishing techniques misused for cyber assault slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like smishing and vishing, spear phishing, contact information through You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Simple Advanced And Complex Types Of Cyber Terrorism Structure PDF
This slide explains the simple advanced and complex types of cyber terrorism attacks i.e. simple structure, advanced structure, and complex coordinated around the 128 countries of the world.This is a cyber terrorism assault simple advanced and complex types of cyber terrorism structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simple structured, advanced structured, complex coordinated You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Types Of Trojans Misused In Cyber Terrorism Background PDF
This slide describes the types of trojans misused in cyber terrorism attacks such as downloader trojan, spyware, backdoor trojan, and rootkit trojans. Presenting cyber terrorism assault types of trojans misused in cyber terrorism background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like backdoor trojan, downloader trojan, rootkit trojans In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cyber Intelligent Computing System Cyber Physical Systems Architecture Physical Layer Designs PDF
This slide represents the physical layer of cyber physical system architecture, including the devices used at this level, such as sensor units and actuator units and their tasks. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Cyber Physical Systems Architecture Physical Layer Designs PDF. Use them to share invaluable insights on Physical Infrastructures, Communication Networks, Global Positioning Systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. This Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Slidegeeks has constructed Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cybersecurity Operations Cybersecops Secops Effective Implementation Impact Summary PDF
This slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Operations Cybersecops Secops Effective Implementation Impact Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF
This slide depicts the RACI matrix for implementing SecOps in the organization. The purpose of this slide is to showcase the various tasks and the responsible persons for those tasks. The leading roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Present like a pro with Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard Sample PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard sample pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

 Home
Home