Cyber Governance

KPI Dashboard To Track IT Protection Performance Elements PDF
This slide shows the dashboard of cyber protection with incident and threat management. It includes overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Pitch your topic with ease and precision using this KPI Dashboard To Track IT Protection Performance Elements PDF. This layout presents information on Incident Management, Threat Management, Critital Risks Identified. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Risk Assessment On Effective IT Service Excellence Designs PDF
This slide signifies the bar graph comparison on growth and benefits provided by IT services. It includes various assistance like cost control, cyber security risk, data analytics and anti virus protection. Showcasing this set of slides titled Comparative Risk Assessment On Effective IT Service Excellence Designs PDF. The topics addressed in these templates are Software Management, Incident Management, Release Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
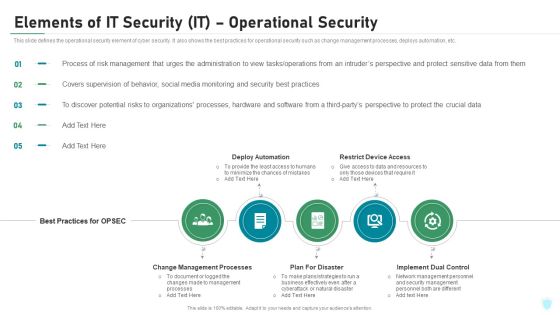
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
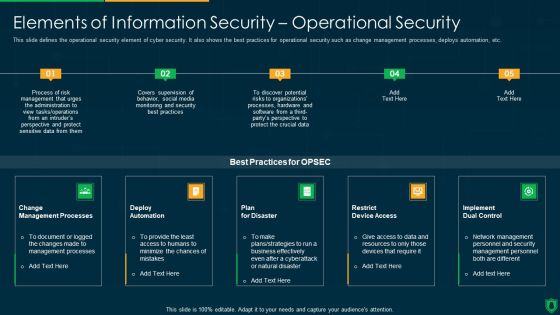
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
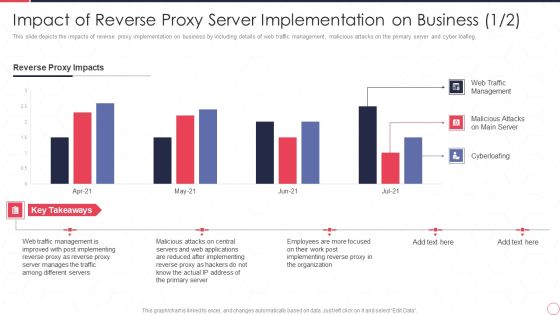
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy Server IT Ppt Professional Slides PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing. Deliver an awe inspiring pitch with this creative impact of reverse proxy server implementation on business reverse proxy server it ppt professional slides pdf bundle. Topics like reverse proxy impacts, web traffic management, malicious attacks on main server, cyberloafing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Anti Scam Playbook Effective Communication Plan To Address Fraud Event Appropriately Sample PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible. This is a Anti Scam Playbook Effective Communication Plan To Address Fraud Event Appropriately Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management, Information, System, Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Defence Protection Strategy Roadmap For Organizational Growth Demonstration PDF
This slide depicts cybersecurity strategy roadmap illustrating surface cyber attack management, process and data optimization and stakeholder engagement for organizational growth.Persuade your audience using this Internet Defence Protection Strategy Roadmap For Organizational Growth Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Optimization Processes, Engaging Stakeholders, Vulnerability Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Fraud Avoidance Playbook Effective Communication Plan To Address Fraud Event Appropriately Clipart PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible. Presenting Fraud Avoidance Playbook Effective Communication Plan To Address Fraud Event Appropriately Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Delivery Method, Finance Department, Management Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

The ROI Of Security Awareness Training Ppt Slides Background PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyberconscious workforce.This is a the roi of security awareness training ppt slides background pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs from routine security practices, costs from productivity loss. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Intelligence Framework For Application Consumption Major Cybersecurity Challenges With Required Actions Mockup PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption major cybersecurity challenges with required actions mockup pdf. Use them to share invaluable insights on cybersecurity strategy, performing effective oversight, protecting cyber critical infrastructure, telecommunications, management challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
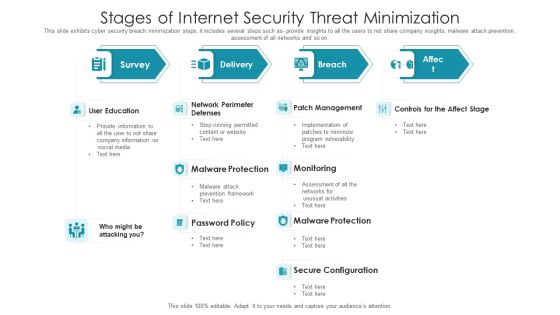
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
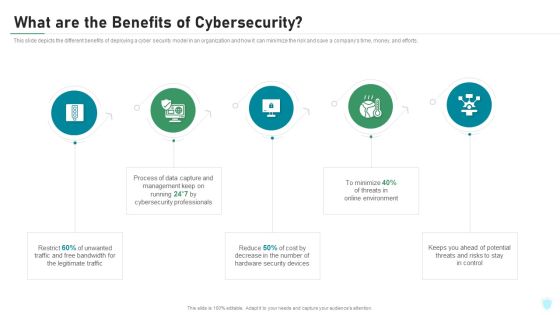
What Are The Benefits Of Cybersecurity IT Security IT Ppt Summary Professional PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a what are the benefits of cybersecurity it security it ppt summary professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like legitimate traffic, cybersecurity, management, process, potential. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
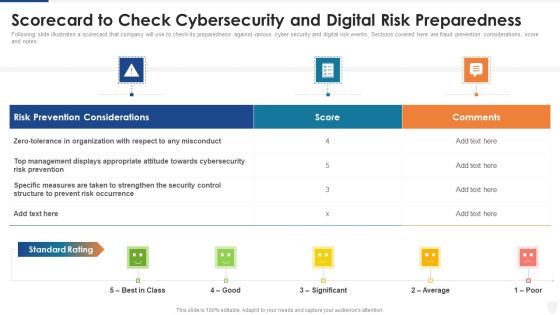
Scorecard To Check Cybersecurity And Digital Risk Preparedness Ppt Layouts Brochure PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this scorecard to check cybersecurity and digital risk preparedness ppt layouts brochure pdf. Use them to share invaluable insights on organization, management, measures, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Setting Scenario For Cybersecurity Control Ppt Pictures Graphics Tutorials PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting setting scenario for cybersecurity control ppt pictures graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like management controls, technical controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Initiatives To Produce Effective Concept For Logistic Firm Risks Involved In Technology Formats PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies or Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this initiatives to produce effective concept for logistic firm risks involved in technology formats pdf. Use them to share invaluable insights on connectivity risk, cyber security risk, inventory management risk, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity What Are The Benefits Of Electronic Information Security Ppt Infographics Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting cybersecurity what are the benefits of electronic information security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, process, cybersecurity, environment, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
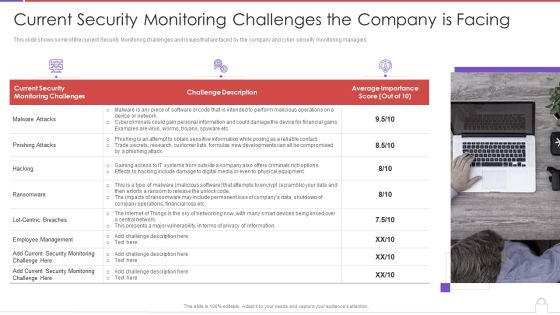
Methods To Develop Advanced Current Security Monitoring Challenges The Company Is Facing Professional PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a methods to develop advanced current security monitoring challenges the company is facing professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current security, monitoring challenges, challenge description, average importance score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives Scorecard To Check Cybersecurity And Digital Risk Preparedness Rules PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative data safety initiatives scorecard to check cybersecurity and digital risk preparedness rules pdf bundle. Topics like risk prevention considerations, score, standard rating, top management displays can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
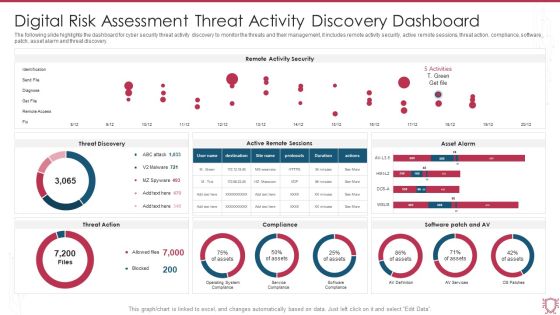
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digitalization Of Operative Enterprises IT OT Organizational Structure Based On Target And Culture Sharing Sample PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Deliver an awe inspiring pitch with this creative Digitalization Of Operative Enterprises IT OT Organizational Structure Based On Target And Culture Sharing Sample PDF bundle. Topics like Business Continuity, Crisis Management, Design can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. This is a Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise CIO, Product Heads, Crisis Management, IT Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Safety Breach Response Playbook Communication Plan For Effective Incident Guidelines PDF
This slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person. Slidegeeks has constructed Safety Breach Response Playbook Communication Plan For Effective Incident Guidelines PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
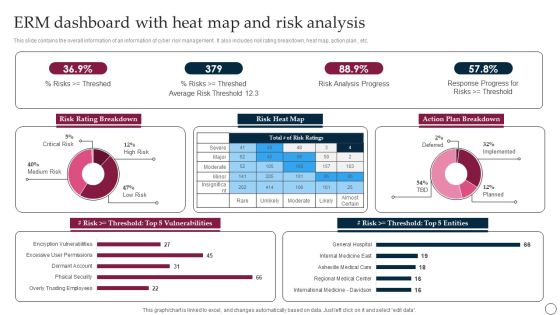
ERM Dashboard With Heat Map And Risk Analysis Ppt PowerPoint Presentation File Backgrounds PDF
This slide contains the overall information of an information of cyber risk management . It also includes risk rating breakdown, heat map, action plan , etc. Showcasing this set of slides titled ERM Dashboard With Heat Map And Risk Analysis Ppt PowerPoint Presentation File Backgrounds PDF. The topics addressed in these templates are Risk Rating Breakdown, Average Risk, Risk Analysis Progress. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Trends On Effective Information Technology Service Excellence Themes PDF
This slide signifies the effective information technology recent and future trends. It includes stages like artificial intelligence, block chain, cyber security and customer data platform. Persuade your audience using this Key Trends On Effective Information Technology Service Excellence Themes PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analytics, Distributed Enterprise, Enterprise Service Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Effective Communication Plan To Address Fraud One Pager Sample Example Document
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible. Presenting you an exemplary Effective Communication Plan To Address Fraud One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Effective Communication Plan To Address Fraud One Pager Sample Example Document brilliant piece now.

IT Security Incident Escalation Communication Plan Flowchart Structure PDF
This slide illustrates a flow chart of the cyber security incident escalation communication plan to manage an attack and minimize the impact. It includes elements such as security team, incident identifier vendor notification etc. Presenting IT Security Incident Escalation Communication Plan Flowchart Structure PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Identifier, Vendor Notification, Website Gets Crashed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Communication Plan For Information Technology Asset Security Threats Pictures PDF
This slide consists of a communication plan that can be implemented by managers to safeguard information technology assets from cyber threats and create an effective response plan. Major elements covered are IT security assets, risk, threat, risk impact, etc. Showcasing this set of slides titled Communication Plan For Information Technology Asset Security Threats Pictures PDF. The topics addressed in these templates are ZZZZZZZZZZZZZZZZZZZZIT Servers, Network Systems, ModemZZZZZZZZZZZZZ. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
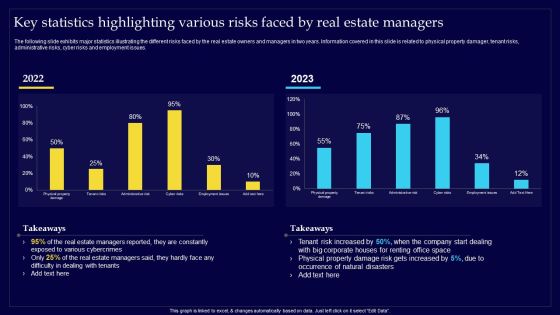
Executing Risk Mitigation Key Statistics Highlighting Various Risks Faced By Real Estate Elements PDF
The following slide exhibits major statistics illustrating the different risks faced by the real estate owners and managers in two years. Information covered in this slide is related to physical property damager, tenant risks, administrative risks, cyber risks and employment issues. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Executing Risk Mitigation Key Statistics Highlighting Various Risks Faced By Real Estate Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Executing Risk Mitigation Key Statistics Highlighting Various Risks Faced By Real Estate Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Slidegeeks has constructed Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Successful Risk Administration Key Statistics Highlighting Various Risks Faced By Real Estate Summary PDF
The following slide exhibits major statistics illustrating the different risks faced by the real estate owners and managers in two years. Information covered in this slide is related to physical property damager, tenant risks, administrative risks, cyber risks and employment issues. Find highly impressive Successful Risk Administration Key Statistics Highlighting Various Risks Faced By Real Estate Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Successful Risk Administration Key Statistics Highlighting Various Risks Faced By Real Estate Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
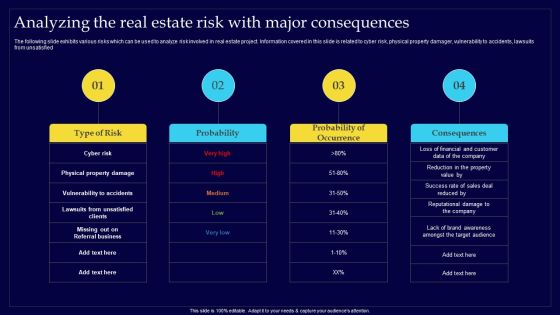
Executing Risk Mitigation Analyzing The Real Estate Risk With Major Consequences Introduction PDF
The following slide exhibits various risks which can be used to analyze risk involved in real estate project. Information covered in this slide is related to cyber risk, physical property damager, vulnerability to accidents, lawsuits from unsatisfied. Boost your pitch with our creative Executing Risk Mitigation Analyzing The Real Estate Risk With Major Consequences Introduction PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF today and make your presentation stand out from the rest.

Successful Risk Administration Analyzing The Real Estate Risk With Major Consequences Summary PDF
The following slide exhibits various risks which can be used to analyze risk involved in real estate project. Information covered in this slide is related to cyber risk, physical property damager, vulnerability to accidents, lawsuits from unsatisfied clients, etc. Create an editable Successful Risk Administration Analyzing The Real Estate Risk With Major Consequences Summary PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Successful Risk Administration Analyzing The Real Estate Risk With Major Consequences Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
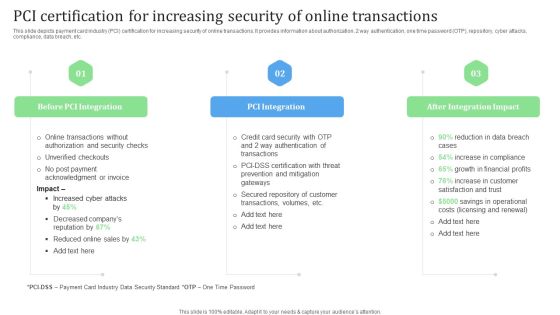
PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Transform Management Instruction Schedule Technological Change Management Designs PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Find highly impressive Transform Management Instruction Schedule Technological Change Management Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Transform Management Instruction Schedule Technological Change Management Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Ukraine Cyberwarfare Us Is Unmasking Russian Hackers Faster Than Ever Rules Pdf
This slide represents the rapid announcements made by the United States about Russian cyberattacks against Ukraine within the 48 hours of the cyberwar. This is a ukraine cyberwarfare us is unmasking russian hackers faster than ever rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like demonstrates how attribution has become a critical tactic of cyber warfare, quickness with which us and uk authorities, cyberattack has been staged to cause fear in ukraine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF
This slide depicts the risk-based approach of open RAN to cybersecurity. The O-RAN Alliance acknowledges cybersecurity as a critical item on its agenda and is working hard to figure out the best way to strengthen the O-RAN systems cyber resilience. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab O RAN Architecture O Ran Risk Based Approach To Cybersecurity Rules PDF today and make your presentation stand out from the rest.

Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF
This slide showcases software that can help organization to monitor and information security risk. It provides information about Cyber Risk Quantification, vulnerability management, Centralized repository for assets etc. Get a simple yet stunning designed Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
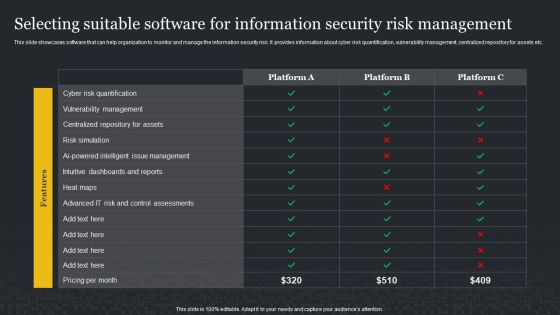
Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. If you are looking for a format to display your unique thoughts, then the professionally designed Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Impact Of Financial Risks On Online Store Metrics Financial Management Strategies Professional PDF
This slide depicts impact of financial risks on online store metrics. It provides information about online fraud, frequent chargebacks, high volume of transactions, lengthy delivery time, merchant risk, cyber hacking, customer satisfaction, etc.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Financial Risks On Online Store Metrics Financial Management Strategies Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Financial Risks On Online Store Metrics Financial Management Strategies Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Managing E Commerce Business Accounting Impact Of Financial Risks On Online Store Metrics Formats PDF
This slide depicts impact of financial risks on online store metrics. It provides information about online fraud, frequent chargebacks, high volume of transactions, lengthy delivery time, merchant risk, cyber hacking, customer satisfaction, etc. Find highly impressive Managing E Commerce Business Accounting Impact Of Financial Risks On Online Store Metrics Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Managing E Commerce Business Accounting Impact Of Financial Risks On Online Store Metrics Formats PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
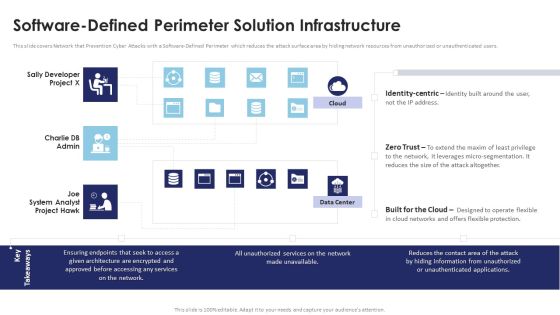
Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Are you searching for a Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF from Slidegeeks today.
 Home
Home