Cyber Governance
Incident Response Planning And Reporting Chart With Primary Skills Ppt PowerPoint Presentation Icon Ideas PDF
Pitch your topic with ease and precision using this incident response planning and reporting chart with primary skills ppt powerpoint presentation icon ideas pdf. This layout presents information on management, technical, cyber security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Management Risk And Compliance Model Summary PDF
The following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Showcasing this set of slides titled Cloud Security Management Risk And Compliance Model Summary PDF. The topics addressed in these templates are Governance, Risk, Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Threat Management At Workplace Threat Management Action Plan Responsible Person Template PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

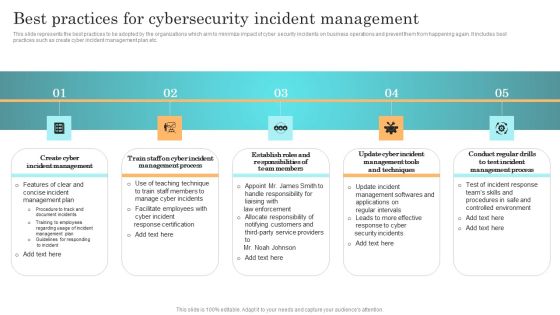
Best Practices For Cybersecurity Incident Management Summary PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Cybersecurity Incident Management Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Cybersecurity Incident Management Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Best Practices For Cybersecurity Incident Management Infographics PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Boost your pitch with our creative Best Practices For Cybersecurity Incident Management Infographics PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Key Competencies For Organization Authorities Ethical Issues In Leadership And Management Download PDF
Presenting key competencies for organization authorities ethical issues in leadership and management download pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like communication, organization, cyber ethics, business, legal liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Leader Vs Administrators Ethical Issues In Leadership And Management Ppt Layouts Graphics Tutorials PDF
Presenting leader vs administrators ethical issues in leadership and management ppt layouts graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like communication, organization, cyber ethics, business, legal liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective Management Styles For Leaders Ethical Issues In Leadership And Management Slides PDF
Presenting effective management styles for leaders ethical issues in leadership and management slides pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like communication, organization, cyber ethics, business, legal liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Leaders Vs Managers Ethical Issues In Leadership And Management Ppt Slides Format Ideas PDF
Presenting leaders vs managers ethical issues in leadership and management ppt slides format ideas pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like communication, organization, cyber ethics, business, legal liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Communication Plan For Cybersecurity Events And Incidents Graphics PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan communication plan for cybersecurity events and incidents graphics pdf bundle. Topics like resources training, department awareness training, approved communication topics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
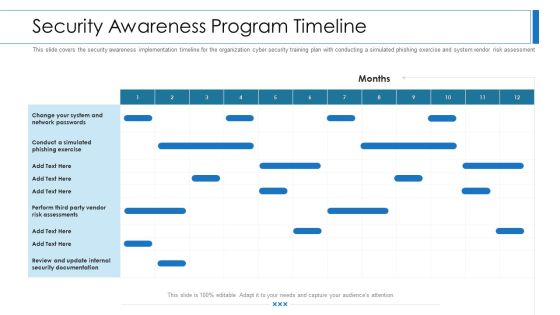
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

API Administration Solution Cost Breakdown To Setup A Company In US Ppt Ideas Summary PDF
The given table shows the number of associated costs to start a company in US. Deliver an awe inspiring pitch with this creative api administration solution cost breakdown to setup a company in us ppt ideas summary pdf bundle. Topics like business, policies, price, cost, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
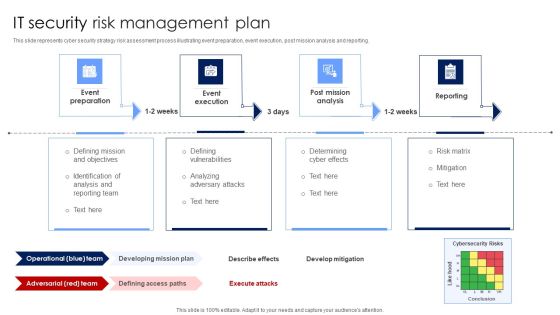
IT Security Risk Management Plan Mockup PDF
This slide represents cyber security strategy risk assessment process illustrating event preparation, event execution, post mission analysis and reporting. Presenting IT Security Risk Management Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Post Mission Analysis, Reporting, Event Execution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Capital Expenditure Budget Performance Report Ppt Inspiration Graphics PDF
This slide shows present typical reports showing the comparison of budgeted expenditures to actual expenditures of a company. It includes authorized and cumulative amounts with variance. Showcasing this set of slides titled Capital Expenditure Budget Performance Report Ppt Inspiration Graphics PDF. The topics addressed in these templates are Network Infrastructure, Maintenance, Cyber Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Leadership And Management Ethical Issues In Leadership And Management Formats PDF
Presenting leadership and management ethical issues in leadership and management formats pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like communication, organization, cyber ethics, business, legal liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Desktop Security Management Managing Computer Security 30 Days Plan Designs PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 30 days plan designs pdf bundle. Topics like awareness, measured, risk, security, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Managing Computer Security 90 Days Plan Professional PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 90 days plan professional pdf bundle. Topics like awareness, security, information, resources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Roadmap For Computer Security Training Graphics PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting desktop security management roadmap for computer security training graphics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
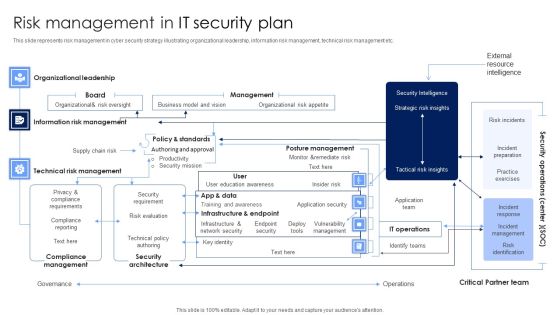
Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

International Organization Standardization 270001 Mapping Of Risk Events Slides PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative international organization standardization 270001 mapping of risk events slides pdf bundle. Topics like financial risk, technology risk, unauthorized activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Multi Cloud Complexity Management Multi Cloud Offerings Inspiration PDF
This slide covers the services offered by the consulting firm for multi cloud solutions covering cloud strategy and readiness SaaS implementation, custom implementation, cloud migration and many more. Deliver and pitch your topic in the best possible manner with this Multi Cloud Complexity Management Multi Cloud Offerings Inspiration PDF. Use them to share invaluable insights on Cloud Strategy, Organizational Change Management, Cyber Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
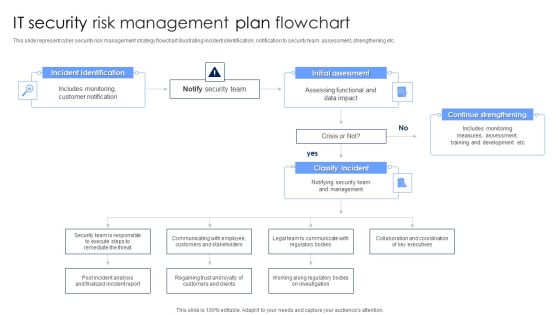
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Risk Management Process For Organization Template PDF
This slide displays flow diagram to illustrate cybersecurity risk management process to ensure continuous monitoring. It includes components such as threats, vulnerabilities, impacts, intelligence, etc. Showcasing this set of slides titled IT Security Risk Management Process For Organization Template PDF. The topics addressed in these templates are Organization, Cyber Intelligence, Continuous Monitoring, Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

OP Risk Management Operational Risk Assessment Worksheet Microsoft PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative op risk management operational risk assessment worksheet microsoft pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Project Scope Management Plan For Agile Implementation Formats PDF
This slide shows the scope of Agile Implementation such as major objectives behind the project, priority tasks to be done, estimated budget for task, project inputs, estimated completion time for task etc. Deliver an awe inspiring pitch with this creative project scope management plan for agile implementation formats pdf bundle. Topics like overloading and enhance, minimizing cyber security, project deliverables can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Security Of Employees Devices Microsoft PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Deliver an awe inspiring pitch with this creative desktop security management security of employees devices microsoft pdf bundle. Topics like security of employees devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Motivation Theories And Leadership Ethical Issues In Leadership And Management Demonstration PDF
Presenting motivation theories and leadership ethical issues in leadership and management demonstration pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like communication, organization, cyber ethics, business, legal liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF
This slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF bundle. Topics like Conference Meeting, Incident Information, Various Departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
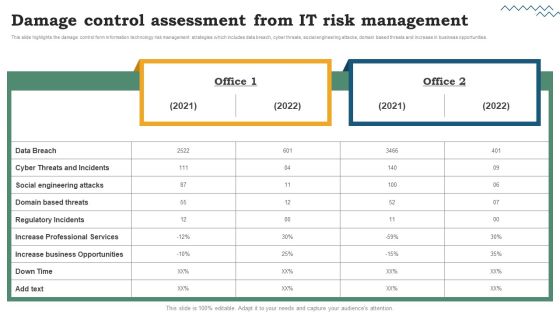
Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Initiating Hazard Managing Structure Firm Operational Risk Assessment Worksheet Rules PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe-inspiring pitch with this creative initiating hazard managing structure firm operational risk assessment worksheet rules pdf bundle. Topics like business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing IT Security IT 30 Days Plan Ppt Gallery Graphics Download PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing it security it 30 days plan ppt gallery graphics download pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
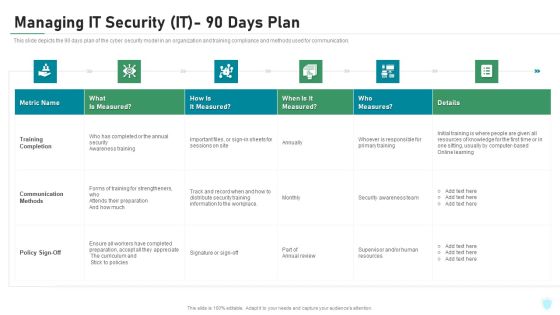
Managing IT Security IT 90 Days Plan Ppt Layouts Picture PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this managing it security it 90 days plan ppt layouts picture pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Risk Management Structure In Financial Companies Operational Risk Assessment Worksheet Introduction PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risk assessment worksheet introduction pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
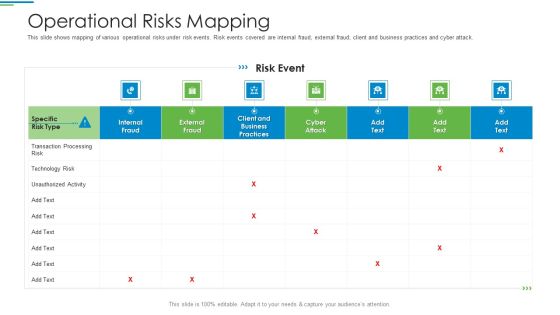
Operational Risk Management Structure In Financial Companies Operational Risks Mapping Summary PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risks mapping summary pdf bundle. Topics like transaction processing risk, technology risk, unauthorized activity, business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management For Organization Essential Assets Determine Several Threat Actors Profile Inspiration PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative risk management for organization essential assets determine several threat actors profile inspiration pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Iot Digital Twin Technology Post Covid Expenditure Management Optimize Digitalize Supply Template PDF
This slide focuses on the optimization and digitalization of supply chain operations which covers cyber supply chain, risk analytics and physical supply chain. Deliver an awe inspiring pitch with this creative iot digital twin technology post covid expenditure management optimize digitalize supply template pdf bundle. Topics like supply chain, promotion, risk, analytics, optimization, procurement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Managing Electronic Information Security 30 Days Plan Ppt Layouts Design Ideas PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 30 days plan ppt layouts design ideas pdf. Use them to share invaluable insights on measured, metric, awareness, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Managing Electronic Information Security 90 Days Plan Ppt Pictures Example Introduction PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 90 days plan ppt pictures example introduction pdf. Use them to share invaluable insights on measured, awareness, security, communication methods and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management What Is Computer Security And How Does It Work Template PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Deliver an awe inspiring pitch with this creative desktop security management what is computer security and how does it work template pdf bundle. Topics like networks, systems, protect data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management It Infrastructure Computer Security Budget For Fy2022 Slides PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative desktop security management it infrastructure computer security budget for fy2022 slides pdf bundle. Topics like it infrastructure computer security budget for fy2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Timeline For The Implementation Of Computer Security Sample PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this desktop security management timeline for the implementation of computer security sample pdf. Use them to share invaluable insights on security documentation, system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Determine Several Threat Actors Profile Clipart PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management determine several threat actors profile clipart pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Statistics Associated To Workplace Threats Template PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. . Deliver an awe inspiring pitch with this creative corporate security and risk management statistics associated to workplace threats template pdf bundle. Topics like cyber attacks costs, organizations, organizations have, organizations face, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
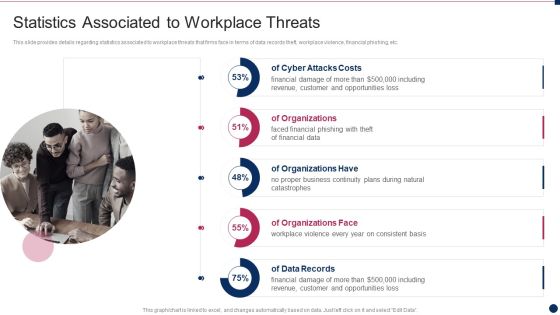
Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
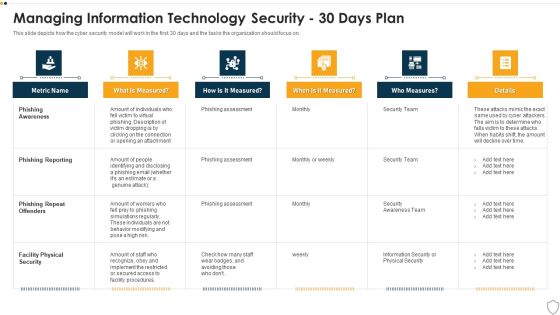
IT Security Managing Information Technology Security 30 Days Plan Themes PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

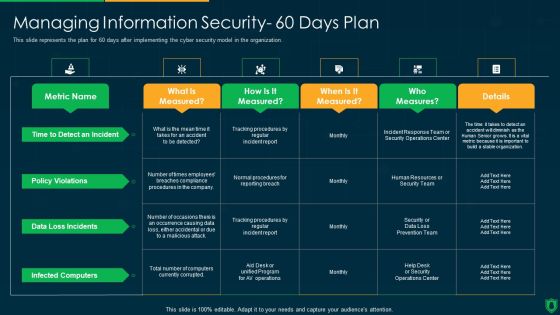
IT Security Managing Information Technology Security 60 Days Plan Professional PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative it security managing information technology security 60 days plan professional pdf bundle. Topics like time to detect an incident, policy violations, data loss incidents, infected computers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
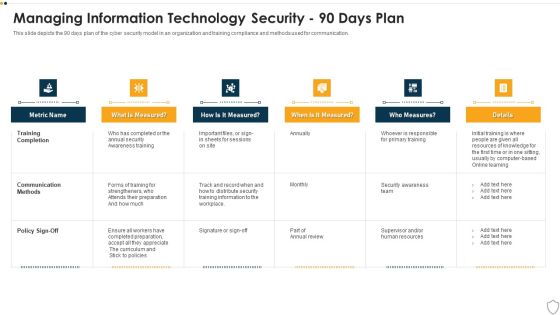
IT Security Managing Information Technology Security 90 Days Plan Sample PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 90 days plan sample pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Managing Information Security 60 Days Plan Ppt PowerPoint Presentation File Graphics Example PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this info security managing information security 60 days plan ppt powerpoint presentation file graphics example pdf. Use them to share invaluable insights on policy violations, data loss incidents, infected computers, time to detect an incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
 Home
Home