Construction Safety Plan

Data Security Benefits Of Adopting Tokenization PPT Sample
This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. Find a pre-designed and impeccable Data Security Benefits Of Adopting Tokenization PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Three Customer Relationship Management Strategies To Build Effective Customer In Banking Sector Summary PDF
This slide outlines three CRM techniques to build effective customer strategy in banking industry. It involves strategies such as customer segmentation, provide effective customer service and get banking data secured.Persuade your audience using this Three Customer Relationship Management Strategies To Build Effective Customer In Banking Sector Summary PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Communication, Segmentation, Organizer Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest

Table Of Contents For Security Control Techniques For Real Estate Project Download PDF
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Security Control Techniques For Real Estate Project Download PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
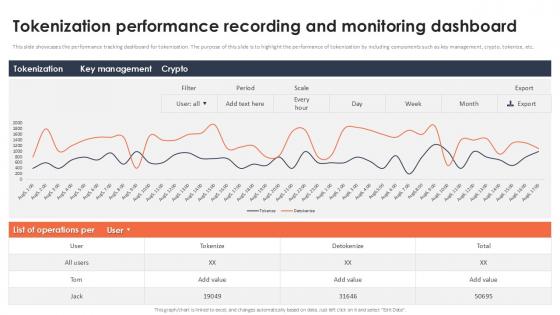
Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide
This slide showcases the performance tracking dashboard for tokenization. The purpose of this slide is to highlight the performance of tokenization by including components such as key management, crypto, tokenize, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide today and make your presentation stand out from the rest

Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in eighty nine slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
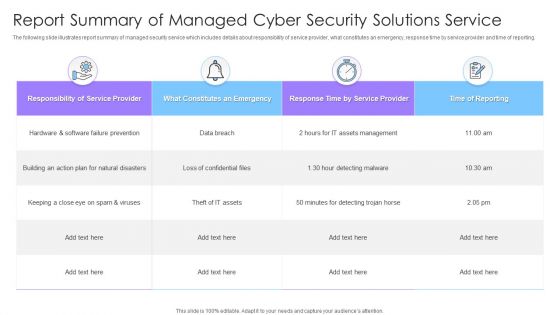
Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides
The following slide illustrates report summary of managed security service which includes details about responsibility of service provider, what constitutes an emergency, response time by service provider and time of reporting. Showcasing this set of slides titled Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides. The topics addressed in these templates are Responsibility Of Service Provider, Time Of Reporting, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Ten Key Considerations Of Building A Data Governance Strategy Ppt PowerPoint Presentation File Pictures
Presenting this set of slides with nameten key considerations of building a data governance strategy ppt powerpoint presentation file pictures. This is a ten stage process. The stages in this process are architecture, data modeling, data storage, data security, interoperability, business intelligence, data quality. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
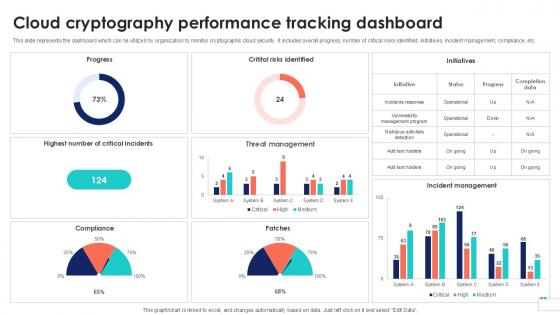
Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
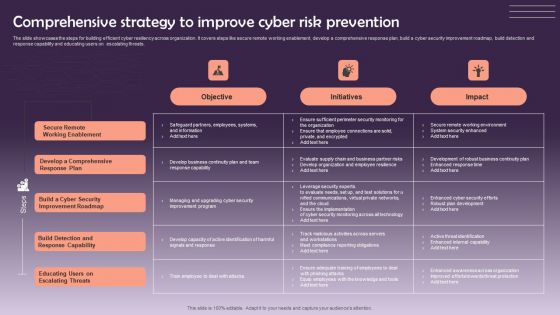
Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF
The slide showcases the steps for building efficient cyber resiliency across organization. It covers steps like secure remote working enablement, develop a comprehensive response plan, build a cyber security improvement roadmap, build detection and response capability and educating users on escalating threats. Pitch your topic with ease and precision using this Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF. This layout presents information on Objective, Initiatives, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Tips For Real Estate Investors PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Key Tips For Real Estate Investors PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Download and present our Sales PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Present our Shapes PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need.Use these PowerPoint slides for presentations relating to Rendering of a key with HOME security, signs, sales, business, shapes. The prominent colors used in the PowerPoint template are Yellow, Brown, Black.
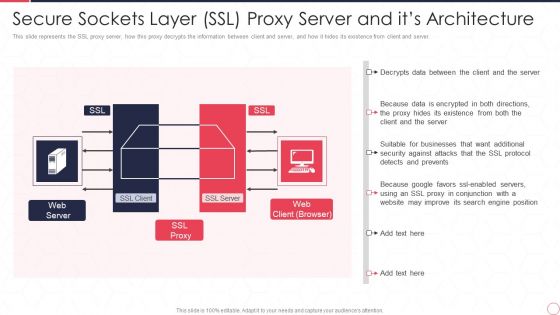
Reverse Proxy Server IT Secure Sockets Layer Ssl Proxy Server And Its Architecture Ppt Inspiration Outline PDF
This slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. This is a reverse proxy server it secure sockets layer ssl proxy server and its architecture ppt inspiration outline pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like web server, ssl proxy, web client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
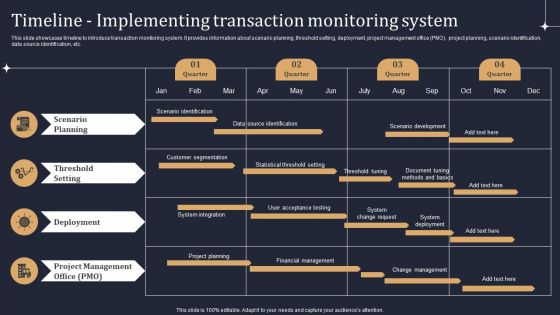
KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
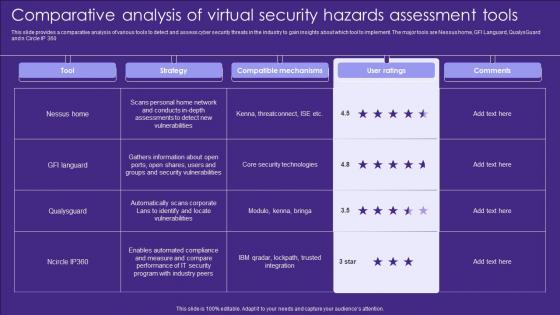
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Application Services Company Outline Information Technology Services Ideas PDF
The slide showcases range of information technology services offered by company for customers. It depicts managed services, intelligent business services, digital experience, solution engineering, innovation services and technology and security advisory. Presenting IT Application Services Company Outline Information Technology Services Ideas PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security Advisory, Managed Services, Intelligent Business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
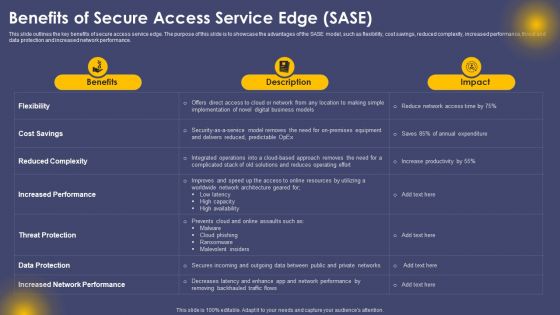
Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF
This slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. This Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
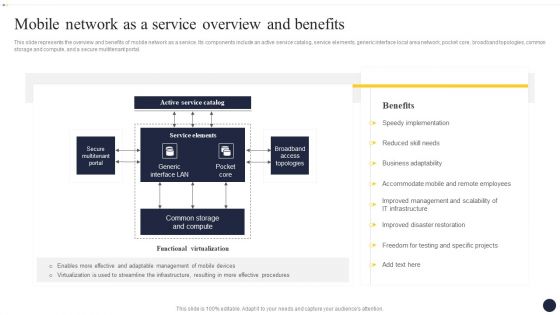
Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. If you are looking for a format to display your unique thoughts, then the professionally designed Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Risk Assessment Dashboard For Securing Supply Chain System Graphics PDF
This slide demonstrates risk assessment matrix for improving the efficiency of industrial supply chain system. It includes supplier risks, service type and service health etc.Showcasing this set of slides titled Risk Assessment Dashboard For Securing Supply Chain System Graphics PDF The topics addressed in these templates are Operation Compliance, Privacy Compilation, External Score All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.This modern and well-arranged Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
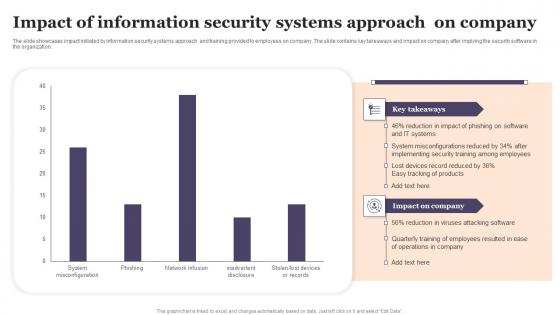
Impact Of Information Security Systems Approach On Company Designs Pdf
The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Showcasing this set of slides titled Impact Of Information Security Systems Approach On Company Designs Pdf The topics addressed in these templates are Impact Of Information, Security Systems, Approach On Company All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.

Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF
The following slide highlights components of managed security service along with the expected cost. Software, antivirus and security monitoring are some of the components which will assist the organization in improving its IT security. Showcasing this set of slides titled Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF. The topics addressed in these templates are Security Monitoring, Antivirus, Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Technologies Used To Protect Data In Use Secure Multi Party Template Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Technologies Used To Protect Data In Use Secure Multi Party Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Technologies Used To Protect Data In Use Secure Multi Party Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Take your projects to the next level with our ultimate collection of IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Cyber Security Implementation Framework Agenda For Cyber Security Management Ppt PowerPoint Presentation Gallery Ideas PDF
Presenting this set of slides with name cyber security implementation framework agenda for cyber security management ppt powerpoint presentation gallery ideas pdf. This is a one stage process. The stages in this process are determining roles and responsibilities, risk management, executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document
Presenting you an exemplary Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
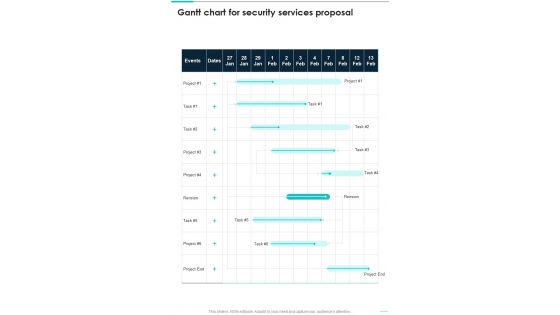
Gantt Chart For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Security Services Proposal One Pager Sample Example Document brilliant piece now.

Effective Digital Security Metrics And Metrics Categories Microsoft Pdf
Pitch your topic with ease and precision using this Effective Digital Security Metrics And Metrics Categories Microsoft Pdf This layout presents information on Security Program Maturity, Metric Category, Sensitive Data Scanning It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
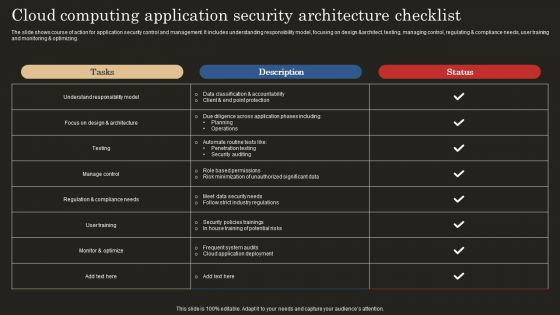
Cloud Computing Application Security Architecture Checklist Template PDF
The slide shows course of action for application security control and management. It includes understanding responsibility model, focusing on design andarchitect, testing, managing control, regulating and compliance needs, user training and monitoring and optimizing. Showcasing this set of slides titled Cloud Computing Application Security Architecture Checklist Template PDF. The topics addressed in these templates are Data Classification Accountability, Client Point Protection, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Bring Your Own Device Security Policies For Device Protection Icon Designs PDF
Presenting Bring Your Own Device Security Policies For Device Protection Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Bring Your Own, Device Security Policies, Device Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
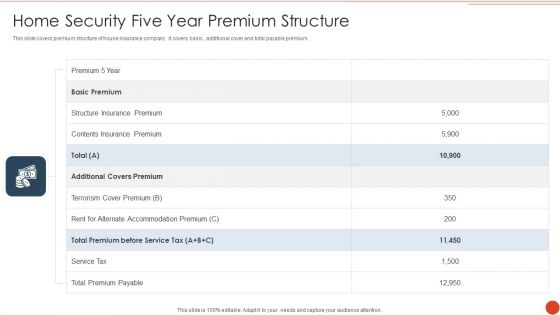
Home Security Five Year Premium Structure Graphics PDF
This slide covers premium structure of house insurance company . it covers basic , additional cover and total payable premium. Showcasing this set of slides titled Home Security Five Year Premium Structure Graphics PDF. The topics addressed in these templates are Additional Covers Premium, Service Tax, Total Premium Payable. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Services Offered Camera Management Platform Investor Funding Elevator Pitch Deck
This slide mentions various features offered by security platform to its users. Key features include cloud recording, snapshotting, object counting, movement heatmaps, sudden light alert, counting people etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Services Offered Camera Management Platform Investor Funding Elevator Pitch Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Internet Security Kpis And Metrics Ppt PowerPoint Presentation Gallery Outline PDF
Showcasing this set of slides titled internet security kpis and metrics ppt powerpoint presentation gallery outline pdf. The topics addressed in these templates are threat detection, risk and compliance, services compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Architecture Blockchain System Blockchain Use Cases Ppt Layouts Icons PDF
The slide shows Blockchain use cases. This is a architecture blockchain system blockchain use cases ppt layouts icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like smart contracts, digital currency, record keeping, securities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Guidelines IT Security Awareness And Training Policy Overview Portrait PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Guidelines IT Security Awareness And Training Policy Overview Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Guidelines IT Security Awareness And Training Policy Overview Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of twenty three slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.
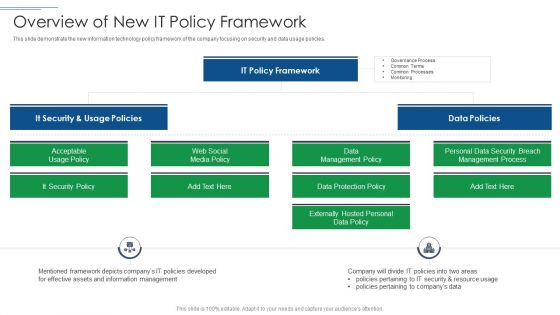
IT Security Risk Management Approach Introduction Overview Of New It Policy Framework Ideas PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting IT Security Risk Management Approach Introduction Overview Of New It Policy Framework Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like It Security, It Policy Framework, Data Policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Tactic For Process Management For IT Roadmap Five Year Designs
We present our cyber security tactic for process management for it roadmap five year designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security tactic for process management for it roadmap five year designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Comparative Analysis Of Internet Security Models Slides Pdf
This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST Pitch your topic with ease and precision using this Comparative Analysis Of Internet Security Models Slides Pdf This layout presents information on Operative Techniques, Development Stage, Benchmark Configuration It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Secure Web Gateway Implementation Methodology Inline Web Access Control Solution
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Create an editable Secure Web Gateway Implementation Methodology Inline Web Access Control Solution that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Secure Web Gateway Implementation Methodology Inline Web Access Control Solution is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
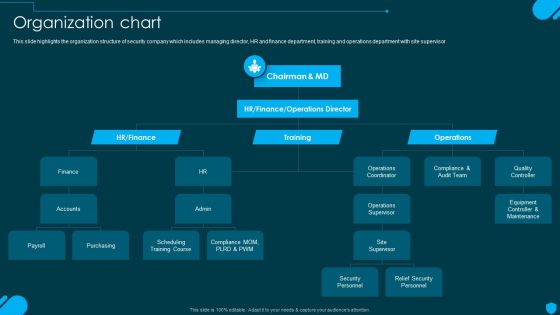
Security And Human Resource Services Business Profile Organization Chart Elements PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security And Human Resource Services Business Profile Organization Chart Elements PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
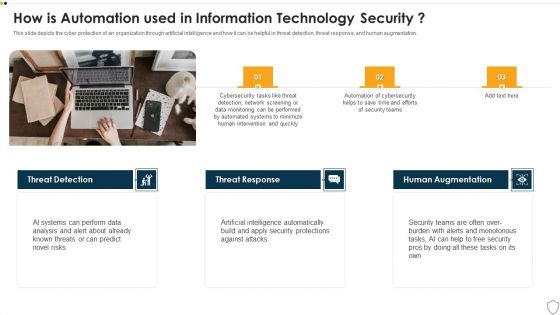
IT Security How Is Automation Used In Information Technology Security Ppt Diagram Lists PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting it security how is automation used in information technology security ppt diagram lists pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
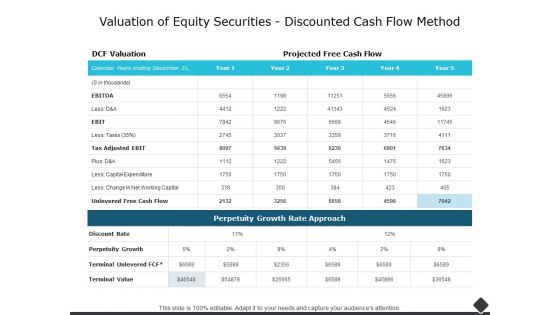
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Outline Designs
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation outline designs. The topics discussed in this diagram are business, management, marketing, compare. This is a completely editable PowerPoint presentation, and is available for immediate download.
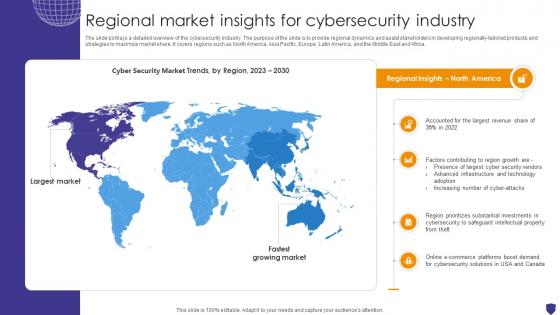
Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V
The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa. Explore a selection of the finest Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Audit System Events Ppt PowerPoint Presentation Model
This is a audit system events ppt powerpoint presentation model. This is a five stage process. The stages in this process are computer configuration, windows settings , security settings , local policies, audit policy.

Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf
The purpose of this slide is to outline the tasks performed by serverless computing. The services provided by serverless computing are monitoring services, integration services, security, support and maintenance, API management services, etc. Do you know about Slidesgeeks Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

ITIL Service Design Overview Professional PDF
This slide depicts the overview of ITIL service design, including easytouse services, to obtain ROI, balanced functionality, cost and performance, dependable and predictable IT service, etc.This is a ITIL Service Design Overview Professional PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Attacks, Management Architectures, Dependable And Predictable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Communicate Your Csr Values To Team Ppt PowerPoint Presentation Good
This is a communicate your csr values to team ppt powerpoint presentation good. This is a six stage process. The stages in this process are passion, agility, innovation, diversity, security, promotion.

Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF.

Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
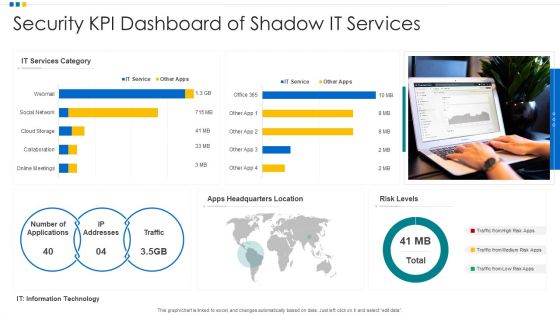
Security KPI Dashboard Of Shadow It Services Ppt Ideas Deck PDF
Pitch your topic with ease and precision using this Security KPI Dashboard Of Shadow It Services Ppt Ideas Deck PDF. This layout presents information on Security KPI Dashboard, Shadow It Services, Risk Levels. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Challenges And Related Solutions In Utility Tokens Securing Your Data Ppt Presentation
This slide outlines the issues faced by utility tokens in data security. The purpose of this slide is to showcase utility token challenges which include absence of inherent mechanism, inadequate promotion, etc. Get a simple yet stunning designed Challenges And Related Solutions In Utility Tokens Securing Your Data Ppt Presentation It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Challenges And Related Solutions In Utility Tokens Securing Your Data Ppt Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home