Construction Safety Plan
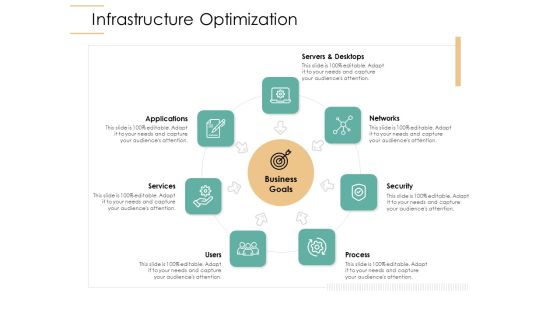
Infrastructure Strategies Infrastructure Optimization Ppt Layouts Slides PDF
Presenting infrastructure strategies infrastructure optimization ppt layouts slides pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like services, networks, servers and desktops, security, process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
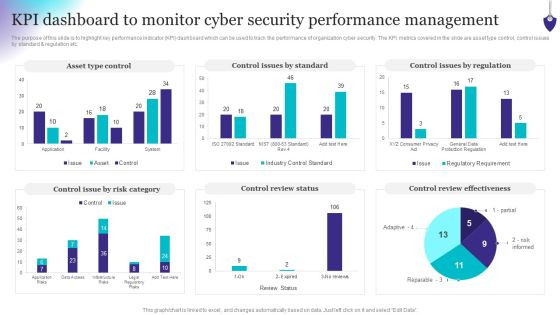
Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This modern and well-arranged Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating. This modern and well-arranged Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Categories Of Load Balancer What Kind Of Traffic Can Load Balancers Handle Ideas PDF
This slide describes the kinds of traffic that a load balancer can handle such as hypertext transfer protocol, hypertext transfer protocol secure, transmission control protocol and user datagram protocol. Presenting categories of load balancer what kind of traffic can load balancers handle ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like some load balancers have recently introduced functionality, https balancing is similar to http balancing, requests are routed using normal http methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phases Of Information IT Security Awareness Training Program Mockup PDF
This slide covers phases of information cybersecurity awareness training program. It involves four phases such as design, development, execution and continual improvement. Persuade your audience using this Phases Of Information IT Security Awareness Training Program Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Design, Development, Execution, Continual Improvement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Security Incident Handling Analyzing IT Department On Nist Cybersecurity Framework Introduction PDF
Presenting this set of slides with name computer security incident handling analyzing it department on nist cybersecurity framework introduction pdf. The topics discussed in these slides are identify, detect, protect, respond, recover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Stock Photo 3d Globe Inside The Chain Security PowerPoint Slide
3d globe is covered with chain in this business image. This image is specially designed for displaying global security issues. Use this image for business and defense related presentations and create a good impact on viewers.

IT Security Information Technology Security Awareness Training For Staff Ppt Slide PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Presenting it security information technology security awareness training for staff ppt slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like senior executives, developers, front line staff, it teams, project managers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Create an editable CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Major Advantages Of Banking Industry Revolution Challenges And Solutions Regarding Diagrams PDF
This slide shows the benefits of mobile banking that improves and enhances the banking services and leads to a positive digital banking transformation such as 24 7 service availability, paperless transactions, facilitation of location-based services, increased efficiency and compliance etc. Presenting major advantages of banking industry revolution challenges and solutions regarding diagrams pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like securing media communications, drifting away from legacy applications, security issues In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
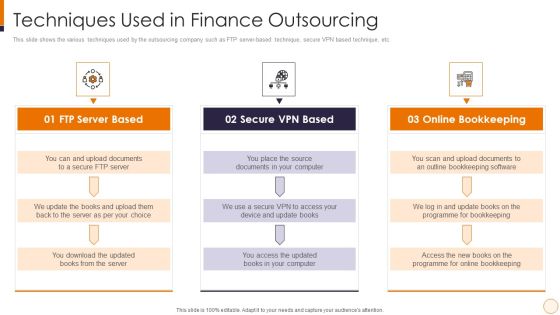
SME And Startups Financing Services Techniques Used In Finance Outsourcing Microsoft PDF
This slide shows the various techniques used by the outsourcing company such as FTP server-based technique, secure VPN based technique, etc. Presenting sme and startups financing services techniques used in finance outsourcing microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ftp server based, secure vpn based, online bookkeeping. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Actual Time Transaction Monitoring Software And Strategies Key Members Of Financial Security Department Diagrams PDF
The following slide highlights key members of financial security department. It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Actual Time Transaction Monitoring Software And Strategies Key Members Of Financial Security Department Diagrams PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Security KPI Dashboard Content Ppt PowerPoint Presentation Complete With Slides
Improve your presentation delivery using this Security KPI Dashboard Content Ppt PowerPoint Presentation Complete With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising tweleve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
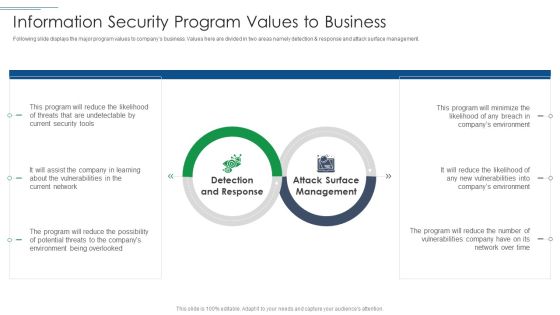
IT Security Risk Management Approach Introduction Information Security Program Values To Business Sample PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting IT Security Risk Management Approach Introduction Information Security Program Values To Business Sample PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Detection And Response, Attack Surface Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF bundle. Topics like OT Security Functions, Security Architecture And Engineering, Primary Responsibility, Shared Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Risk Mitigation Strategy Model Icon With Security Shield Symbol Ppt PowerPoint Presentation Icon Inspiration PDF
Persuade your audience using this risk mitigation strategy model icon with security shield symbol ppt powerpoint presentation icon inspiration pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including risk mitigation strategy model icon with security shield symbol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Security Implementation Framework Determining Roles And Responsibilities For Risk Handling Icons PDF
Presenting this set of slides with name cyber security implementation framework determining roles and responsibilities for risk handling icons pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Risk Based Procedures To IT Security Risk Governance Structure Ppt PowerPoint Presentation Icon Gallery PDF
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Risk Governance Structure Ppt PowerPoint Presentation Icon Gallery PDF. Use them to share invaluable insights on Risk Management, Board Directors, Strategy Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Half Yearly Information Technology Security Program Maturity Roadmap Microsoft
Introducing our half yearly information technology security program maturity roadmap microsoft. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Quarterly Information Technology Security Program Maturity Roadmap Ideas
Introducing our quarterly information technology security program maturity roadmap ideas. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Six Months Information Technology Security Program Maturity Roadmap Infographics
Introducing our six months information technology security program maturity roadmap infographics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Three Months Information Technology Security Program Maturity Roadmap Pictures
Introducing our three months information technology security program maturity roadmap pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetxary penalty and operational disruption. If you are looking for a format to display your unique thoughts, then the professionally designed Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Service Desk Incident Management Framework Ppt PowerPoint Presentation File Pictures PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Service Desk Incident Management Framework Ppt PowerPoint Presentation File Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Service Desk Incident Management Framework Ppt PowerPoint Presentation File Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Steps Included In Data Retention Security Mechanism Introduction PDF
This slide depicts the steps covered in data retention policy. The steps included are determine applicable regulations, catalogue data, decision making, policy documentation and implementation.Persuade your audience using this Steps Included In Data Retention Security Mechanism Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Catalogue Data, Decision Making, Document Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Online Settlement Revolution Digital Payment System Deployment Services Summary PDF
Listed Solutions provides centralized, secure storage of analytical assets, and advanced capabilities for management and control of predictive analytic processes. Presenting online settlement revolution digital payment system deployment services summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like automate process, analytics, infrastructure, data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Information Technology Infrastructure Model With Service Provider Graphics PDF
The following slide outlines comprehensive technology infrastructure framework. It provides information about client governance, service provider governance, client service desk, security levels etc. Presenting Information Technology Infrastructure Model With Service Provider Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Datacenter, Monitoring And Management, Data Management, Client Service Desk, Service Provider. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Executing Risk Mitigation Key Benefits Post Implementing Risk Mitigation Strategies Structure PDF
The following slide exhibits the positive impact of implementing risk management strategies in real estate business. Customer satisfaction, improved data security, operational process improvement and reduced catastrophic events are some of the major benefits which are outlined in the slide. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Executing Risk Mitigation Key Benefits Post Implementing Risk Mitigation Strategies Structure PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Executing Risk Mitigation Key Benefits Post Implementing Risk Mitigation Strategies Structure PDF today and make your presentation stand out from the rest.

Blockchain And DLT Framework Blockchain Technology In Government Sector Inspiration PDF
This slide represents the use case of blockchain in the government sector how it would benefit voting, data security, budgeting and corruption. This is a Blockchain And DLT Framework Blockchain Technology In Government Sector Inspiration PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like National, Digital Currency, Data Security, Fighting corruption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ESO System Center Framework Ppt PowerPoint Presentation Gallery Brochure PDF
This slide covers enterprise security operations center framework. It involves five stages such as discovery, preliminary investigation, triage, extended investigation and respond. Persuade your audience using this ESO System Center Framework Ppt PowerPoint Presentation Gallery Brochure PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Discovery, Preliminary Investigation, Triage, Extended Investigation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Securities Risk Assessment In Investment Topics PDF
This slide shows the risk percentage of three securities purchased by an investor. It includes risk level during four quarters of all three securities. Pitch your topic with ease and precision using this Securities Risk Assessment In Investment Topics PDF. This layout presents information on Investment, Key Takeaways, Continuous Increase. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
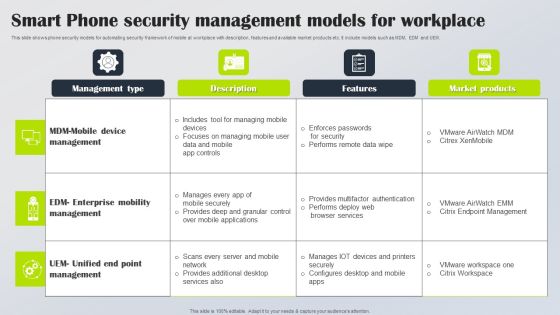
Smart Phone Security Management Models For Workplace Rules PDF
This slide shows phone security models for automating security framework of mobile at workplace with description, features and available market products etc. It include models such as MDM, EDM and UEM. Showcasing this set of slides titled Smart Phone Security Management Models For Workplace Rules PDF. The topics addressed in these templates are Management Type, Description, Features. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF
This slide describes the establishment of cyber policies by international laws, including the budapest convention on cybercrime and the united nations group of governmental experts. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Create an editable Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Comparative Analysis Of Scrum Service Management Tools Clipart PDF
The following slide depicts the comparison of information service management tools to select the best option based on its features. It includes elements such as price, maintenance, flexibility, security, mobility, integration, etc. Showcasing this set of slides titled Comparative Analysis Of Scrum Service Management Tools Clipart PDF. The topics addressed in these templates are Comparative Analysis, Scrum Service, Management Tools. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Iot Security Lock For Safe Fleet Management Sample PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot Security Lock For Safe Fleet Management Mockup PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Mockup PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Network Access User Flow Overview Mockup PDF
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Create an editable Zero Trust Network Access User Flow Overview Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access User Flow Overview Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
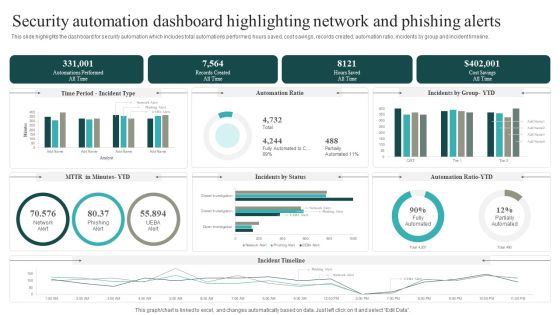
Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. This modern and well arranged Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Create an editable Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Securities Allocation Dashboard For Project Metrics Information PDF
This slide shows the securities allocation dashboard for project management which focuses on expenses incurred on project which includes cash, commends, revenues and inventory with total allocation of securities with the percentage. Showcasing this set of slides titled Securities Allocation Dashboard For Project Metrics Information PDF. The topics addressed in these templates are Inventory, Project, Revenues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
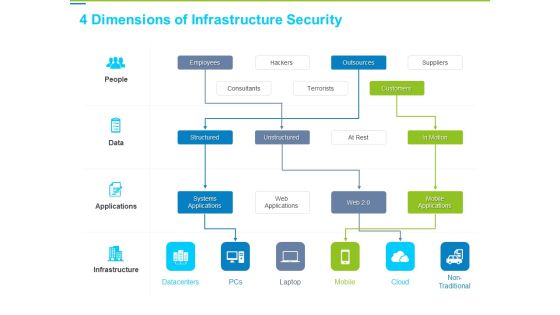
Framework Administration 4 Dimensions Of Infrastructure Security Ppt Infographic Template Slide Download PDF
This is a framework administration 4 dimensions of infrastructure security ppt infographic template slide download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. Find a pre-designed and impeccable Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
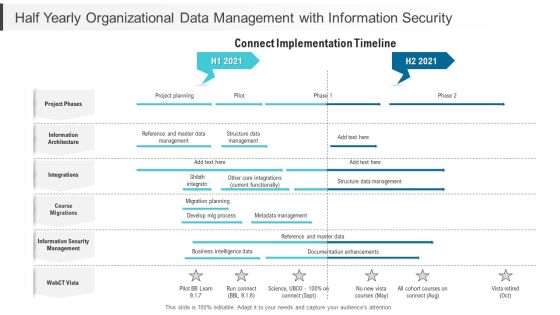
Half Yearly Organizational Data Management With Information Security Designs
Presenting our jaw dropping half yearly organizational data management with information security designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Implement Electronic Health Records Techniques Brochure PDF
This slide showcases the strategies to implement electronic health records EHRs. It includes strategies such as integrate reliable EHR system, secure patient data, use data analytics and train staff. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implement Electronic Health Records Techniques Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implement Electronic Health Records Techniques Brochure PDF

Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF
This slide provides information regarding ITIL process areas in terms of service strategy and service design and associated sequential activities. Deliver an awe inspiring pitch with this creative Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF bundle. Topics like Sequential Activities Processes, Strategy Management Execution, Sequential Activities Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determine Right Pricing Strategy New Product Three Tier Pricing Strategy Designs PDF
Presenting this set of slides with name determine right pricing strategy new product three tier pricing strategy designs pdf. This is a three stage process. The stages in this process are basic security, advanced security, unlimited websites, super advanced security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Dashboard Depicting Security Problem Management Metrics Ppt Gallery Designs PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Showcasing this set of slides titled Dashboard Depicting Security Problem Management Metrics Ppt Gallery Designs PDF. The topics addressed in these templates are Percentage, New Critical, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

 Home
Home